Products/Services
product
service
- Simple Security Consulting [Consulting]
- Splunk SOAR Automation Assessment Service [Consulting]
- Dashboard/SPL Creation Pack [Implementation/Building Support]
- Version upgrade service [implementation and construction support]
- Splunk Premium Apps construction support service [implementation and construction support]
- Splunk Security Log Analysis Start Package [Original App/Service]
- Splunk × CrowdStrike Falcon Insight, Macnica Original App [Original App/Service]
- Government uniform standard compatible App [Original App/Service]
- Smart Security Monitoring App [Original App/Service]
- Splunk × LANSCOPE Original App [Original App/Service]
- Security Monitoring App for Box [Original App/Service]
- Cloud Security Monitoring App [Original App/Service]
- SIEM Operation Monitoring Service [Original App/Service]
- List of services
- Macnica Premium Support for Splunk (utilization support, version upgrade monitoring)
- Macnica Premium Support for Splunk Skill Up Package
Specifications/Technical Information
Specifications/Technical Information
Evaluation machine application/FAQ
Application for evaluation machine
- FAQ

Splunk
Splunk

Simplified operation with automatic quarantine function
Device auto-quarantine
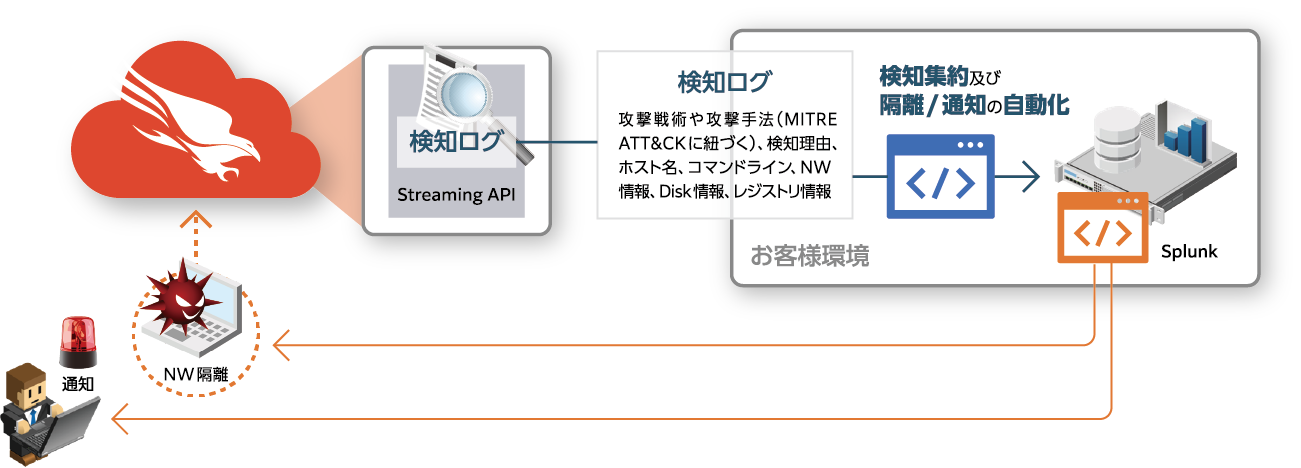
In response to alerts fired from CrowdStrike Falcon-installed terminals, Falcon's API (Streaming API) is used to aggregate detection information → Direct the automatic isolation of terminals
In response to alerts fired from CrowdStrike Falcon-installed terminals, Falcon's API (Streaming API) is used to aggregate detection information → Direct the automatic isolation of terminals
Powerful backup for security operations
Automatic terminal isolation reduces on-site man-hours for security operation teams and strongly backs up security operations after hours such as late night hours on holidays.
Automatic terminal isolation reduces on-site man-hours for security operation teams and strongly backs up security operations after hours such as late night hours on holidays.
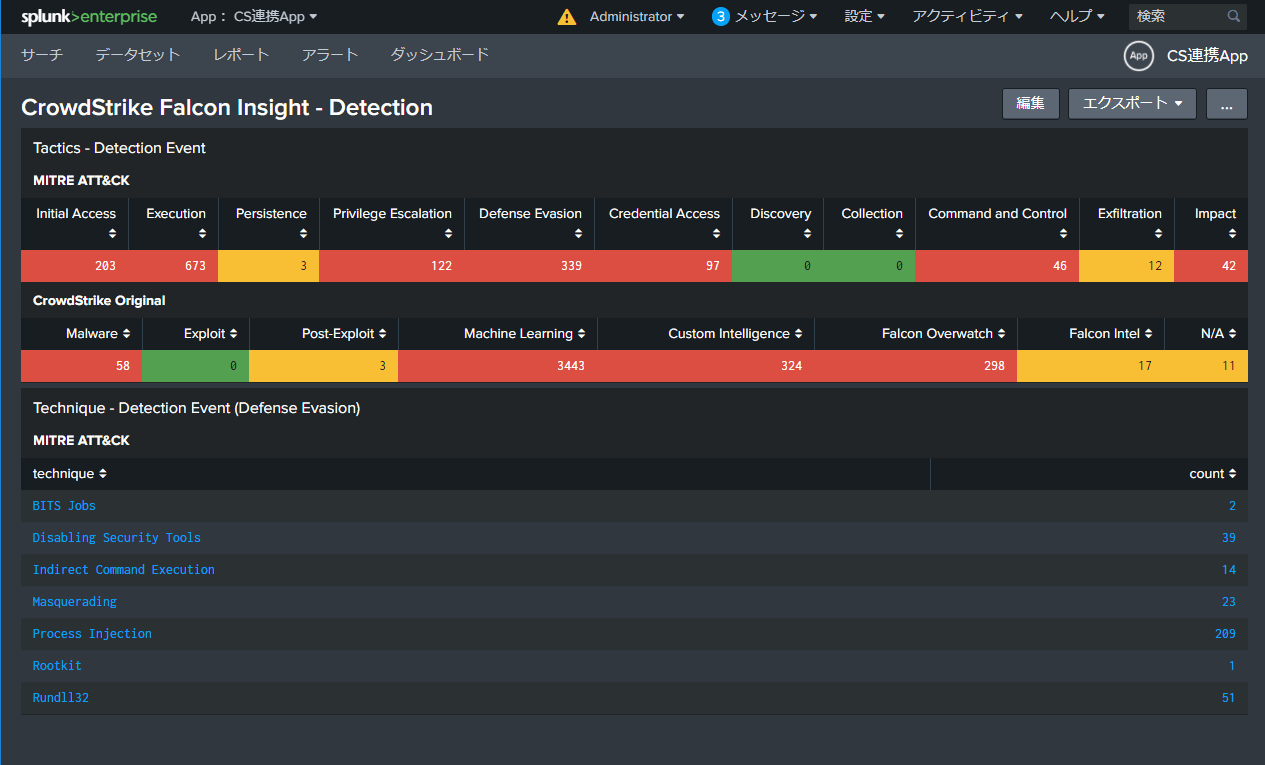
Analysis of detection status by dashboard reporting
Visualize endpoint detection status
Visualization of endpoints exposed to threats from statistics and analysis of detection logs, and creation of customized dashboards according to customer-specific requests
Visualization of endpoints exposed to threats from statistics and analysis of detection logs, and creation of customized dashboards according to customer-specific requests
Centralized management of all logs
By importing other security and network logs you already have into Splunk, you can centrally manage the overall log operation with Splunk.
By importing other security and network logs you already have into Splunk, you can centrally manage the overall log operation with Splunk.
Auto-quarantine function
- Automate initial response
After collecting detection information in Splunk, when specific conditions (Severity: High or higher, other than specific terminals) are met, CrowdStrike's NW isolation API is executed to logically isolate, enabling automatic initial response. - CrowdStrike detection information can be viewed on Splunk
Primary information detected by CrowdStrike can be viewed on Splunk. In addition, it is possible to automate network isolation operations for terminals from the management console. - Real-time notification
Quarantine/detection notifications are sent via Slack (default setting). In addition to Slack, it is also possible to customize the notification method by email and Teams.
Splunk requirements: [Version] Splunk Enterprise v8.0 or higher (Splunk Cloud not applicable) [Installed OS] Linux OS only
CrowdStrike Requirements: [License] Falcon insight, Threat Graph
Dashboard reporting
- Seamless analysis - change settings
It is possible to manage the detection status of endpoints exposed to threats on Splunk and analyze them using detection logs. You can also centralize all your CrowdStrike logs in Splunk. (FDR (Falcon Data Replicator) is required on the CrowdStrike Falcon Insight side for some activity log captures.) It is also possible to go to the CrowdStrike console by drilling down from the dashboard, and seamlessly perform everything from analysis to setting changes. can do. - Saving and viewing logs
For example, even after the detection log retention period on CrowdStrike, you can store and view logs according to your security policy by linking with Splunk and storing them.
Form of provision
Via sales partners or direct sales by user companies are also possible
* Prices are fixed prices for user companies * Partitions are provided for sales partners
Offer price
| trial plan | standard plan | Premium plan | |
|---|---|---|---|
| Price (annual) |
free of charge |
¥660,000~ |
¥1,980,000~ |
| support |
× |
○ |
○ |
| App implementation/customization |
× |
× |
○※1 |
*1 Please consult us separately regarding implementation details and customization details.
Inquiry/Document request
In charge of Macnica Splunk Co., Ltd.
- TEL:045-476-2010
- E-mail:splunk-sales@macnica.co.jp
Mon-Fri 8:45-17:30