Splunk
スプランク
SIEM機能について
Splunkが提供するSIEM機能とは?
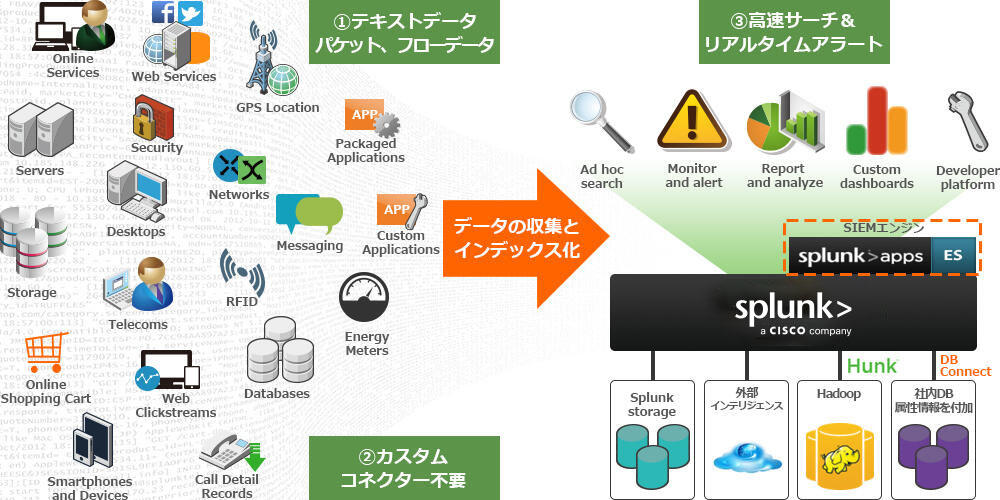
Splunkはテキスト化されていればあらゆるデバイス、システムのデータを取込むことができ、検索・分析をかけることが可能です。
SIEMとして利用するには2通りあり、Splunkのみで検知ルールを作成しSIEMとして利用する、または相関ルールを持つEnterprise Securityという有償Add-onを実装しSIEMとして利用する、いずれかの方法があります。
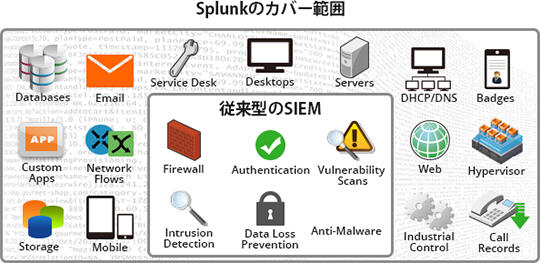
セキュリティ用に開発された専用Apps
SIEM用に開発された有償AppsであるEnterprise Securityと、個別デバイス用の無償Appsを組み合わせることでお客様環境、用途に合わせてSplunkを活用いただくことが可能です。
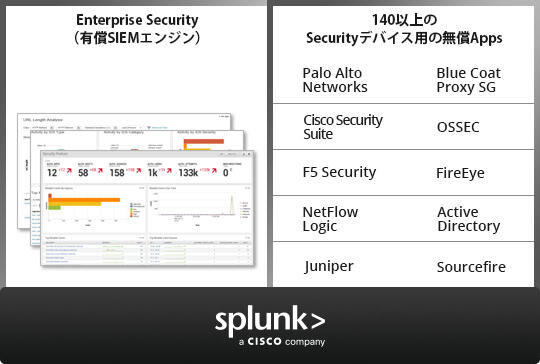
SIEM機能としての実績は?
SIEMとしてのSplunk
Gartner Magic QuadrantのSIEMカテゴリにてリーダーとしてポジショニングされており、SplunkをSIEMとして採用するケースが増えています。
Splunkはセキュリティ専門製品ではないにもかかわらず、SIEM製品と同格の評価を受けております。さらにワールドワイドで9000社以上の導入実績があるなか、2800社以上がセキュリティ用途でSplunkを導入しています。
セキュリティ専門製品ではないのにこれだけSplunkが"SIEM"機能として評価される理由
SIEM
- セキュリティに特化した相関分析やアラートのルール
- 多数のセキュリティ機器のログに対応
- 豊富なレポートテンプレート
- セキュリティ機器からでるアラートの重要性にプライオリティづけ
- 調査の担当を割り振り、調査状況を共有するチケッティングシステム

課題
- 未対応のデータソース、スキーマ定義
- 問題特定の為のサーチ機能、解析スピード、拡張性

Splunkの解決策
- 一製品でデータ収集・保存・検索・アラートを実現
- 高いスケーラビリティ (200TB/日)
- 一般的なハードウェア上で動作
- 同じデータをセキュリティ以外の目的でも利用可能、高いROI実績
- テキストであればどんなデータも取り込み可能
- 高速な検索・データ抽出に強み
- 過去データを利用し統計分析
| 一般的なSIEM製品 | Splunk ES | |
|---|---|---|
| 相関分析 | ルールベース(既知・定義済パターン) | ルールベース統計ベース(未知、疑わしい) |
| 相関分析処理 | リアルタイム | リアルタイム・クエリー(アドホックに即応) |
| 相関ベース | ルールベース | 統計ベース |
| 利用シーン | SOCオペレーション (エスカレーション・ワークフロー) |
SOCアナリスト、 事後調査デバイス/アプリケーション管理者 |
| 実装と スケールコストメリット |
多様なデバイス・ルール対応 ソフトウェア/アプライアンスモデルによる制限 (イベント量・ハードウェアスペック) 大規模・定期的なメンテナンスによるコスト |
データフォーマット・デバイス依存なし ソフトウェア上の制限なし (コモディティハードウェア増設) 短期間での構築 オンデマンドでのメンテナンス(カスタマイズ)に対応 |
| アーキテクチャ |
従来SIEMのアーキテクチャ
 |
Splunkのアーキテクチャ
 |
お問い合わせ・資料請求
株式会社マクニカ Splunk 担当
- TEL:045-476-2010
- E-mail:splunk-sales@macnica.co.jp
平日 9:00~17:00