product
- Why choose Splunk
- Installation record
- price
- Splunk Enterprise Security
- Splunk Phantom (SOAR)
- Splunk ITSI (Next Generation IT Operations)
- Splunk Observability Cloud
- Splunk UBA
- Macnica CSIRT App Basic
- App for Splunk for Financial Institutions
- Splunk Analytics for Hadoop
- About Apps
- Splunk Edge Hub
- What is Splunk
service
- Dashboard/SPL Creation Pack [Implementation/Building Support]
- Version upgrade service [implementation and construction support]
- Smart Security Monitoring App [Original App/Service]
- Splunk × LANSCOPE Original App [Original App/Service]
- Security Monitoring App for Box [Original App/Service]
- Cloud Security Monitoring App [Original App/Service]
- List of services
Specifications/Technical Information
Application for evaluation machine
- FAQ

Splunk
Splunk
Splunk for Security
Why is log analysis important for targeted attack countermeasures? This is to quickly identify traces of attacks and minimize damage when an incident occurs.
The advantages of having an environment in which log analysis can be performed quickly are as follows.
- Reduced time to identify scope of impact (improved incident response)
- Reduces the man-hours required for manually comparing various suspicious logs when an incident occurs
上記のように、Splunkでログを集めて可視化、分析する重要性を理解しつつも、取込むべきログの選定が難しい、ということが昨今多くのお客様で課題になっています。
Many people may not be able to use Splunk as expected because they do not know which logs to analyze and what to look at.
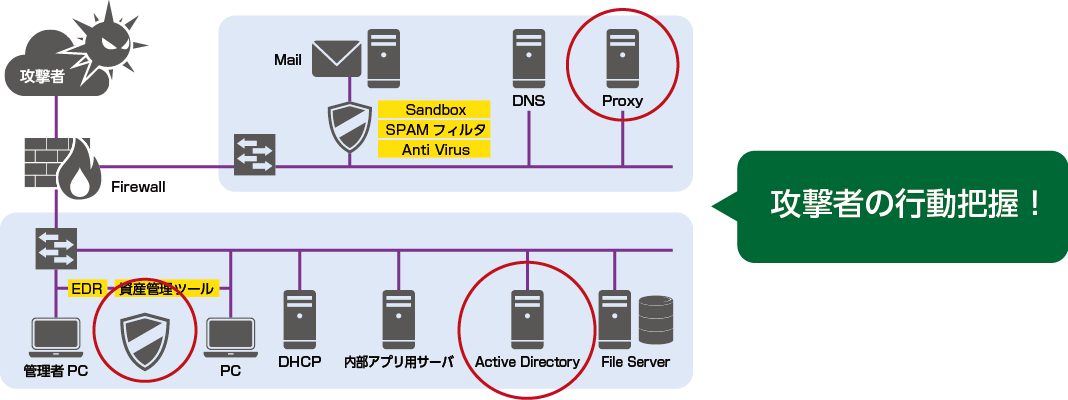
Important log sources to be analyzed for targeted attack countermeasures are:
Proxy/Active Directory/EDR/Asset management tool
There are three types of
The reason is?
Splunk for Networks
Strengthen IT infrastructure management by leveraging the strengths of Splunk
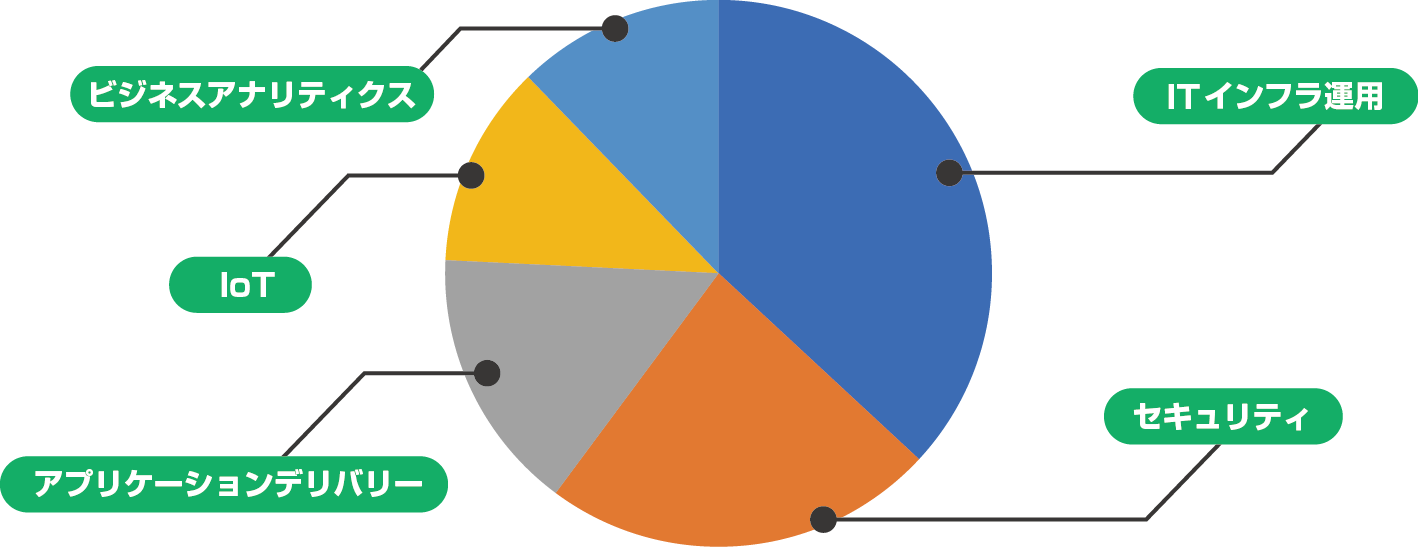
In Japan, 80% of Splunk use cases are security applications. Splunk can be used in all fields, so it would be a waste to limit it to one use.
Would you like to expand the application area of Splunk in the field of IT infrastructure operation, which is a large market in the world and is used by customers on a daily basis?
Percentage of Splunk target market size globally
- Target customer
- Customers already using Splunk for security
- Customers dissatisfied with existing IT infrastructure monitoring tools
- Customers interested in keywords such as AI, machine learning, DX, and automation
- merit
- Changed the way of looking at proxy logs that have been imported into Splunk for security purposes, and can also be used from the perspective of IT infrastructure operation
- "Associating logs and metrics information", "long-term log storage", and "correlation/trend analysis" enable monitoring from a medium- to long-term perspective instead of instantaneous monitoring.
- "ITSI (Splunk IT Service Intelligence)" enables predictive detection of network anomalies using machine learning
What are the specific steps to strengthen IT infrastructure operations?
Weekdays: 9:00-17:00
Inquiry/Document request
In charge of Macnica Splunk Co., Ltd.
- TEL:045-476-2010
- E-mail:splunk-sales@macnica.co.jp
Weekdays: 9:00-17:00