Products/Services
product
service
- Simple Security Consulting [Consulting]
- Splunk SOAR Automation Assessment Service [Consulting]
- Dashboard/SPL Creation Pack [Implementation/Building Support]
- Version upgrade service [implementation and construction support]
- Splunk Premium Apps construction support service [implementation and construction support]
- Splunk Security Log Analysis Start Package [Original App/Service]
- Splunk × CrowdStrike Falcon Insight, Macnica Original App [Original App/Service]
- Government uniform standard compatible App [Original App/Service]
- Smart Security Monitoring App [Original App/Service]
- Splunk × LANSCOPE Original App [Original App/Service]
- Security Monitoring App for Box [Original App/Service]
- Cloud Security Monitoring App [Original App/Service]
- SIEM Operation Monitoring Service [Original App/Service]
- List of services
- Macnica Premium Support for Splunk (utilization support, version upgrade monitoring)
- Macnica Premium Support for Splunk Skill Up Package
Specifications/Technical Information
Specifications/Technical Information
Evaluation machine application/FAQ
Application for evaluation machine
- FAQ

Splunk
Splunk
What is an app that supports uniform government standards?
- The uniform government standards apply to national public servants, independent administrative agencies, and designated corporations engaged in administrative work in government agencies, and have been formulated with the aim of uniformly raising the information security level of government agencies. Compliance is now required.
- Macnica Splunk, which enables detection, investigation, and analysis of security incidents based on machine data, and Tanium, which is responsible for endpoint configuration management, are combined to develop an App that is compatible with the guideline items listed in "Part 5 to Part 7 of the Guidelines for Establishing Countermeasure Standards for Fiscal Year 2008" of the Unified Government Standards. The App for the Unified Government Criteria was developed independently.
- The Government Uniform Standard App can implement the following measures
- Check whether your organization complies with the guidelines of the uniform government standards
- Visualization of information systems, software, and Windows patch application status
- Check vulnerability information
- Additional information collection and handling using the function of the linked configuration management product from Splunk
- Statistical comparison with historical data
- Based on the results obtained from the App screen, it is possible to collect additional information and take action from Splunk by using the API of the configuration management product (Tanium).
Main implementation contents
| function | Overview | Purpose of use |
|---|---|---|
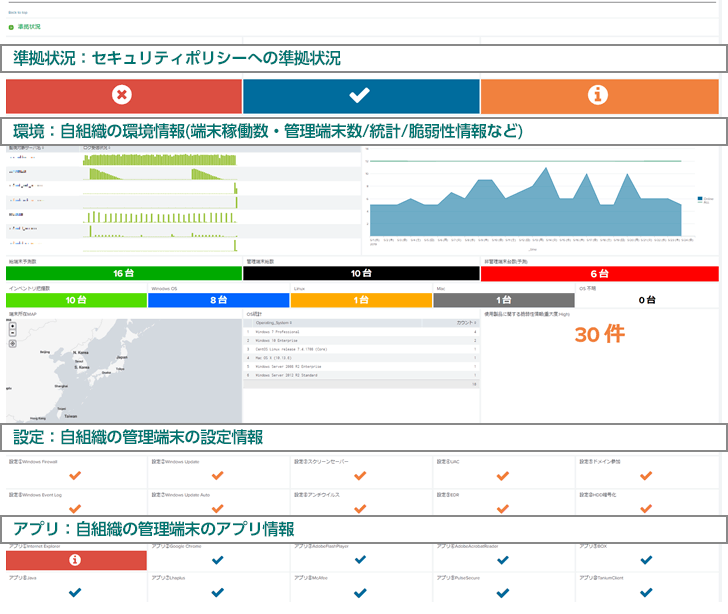
| Government uniform standard summary | A function that visualizes the status of compliance with guidelines within the uniform government standards and displays items that deviate from the guidelines as errors (abnormalities). | It is used to detect anomalies (outside the policy) in the organization in accordance with the guidelines of uniform government standards. |
| List of information systems | A function to display detailed information of information systems (endpoints) in lists and statistics, and to visualize the existence of unmanaged information systems. | It is used as a hardware ledger for checking information of each information system when cyber attack damage occurs or during maintenance/maintenance. |
| software search | A function that displays software information installed in information systems (endpoints) in lists and statistics, and can also identify terminals. | It is used as a software ledger for checking information on information systems when obtaining vulnerability information or managing licenses. |
| Windows patch search | A function that displays the Windows patch information of the information system as a list and statistical information, and visualizes the application status. | It is used to check the application status of the information system when obtaining vulnerability information or reporting the patch application status. |
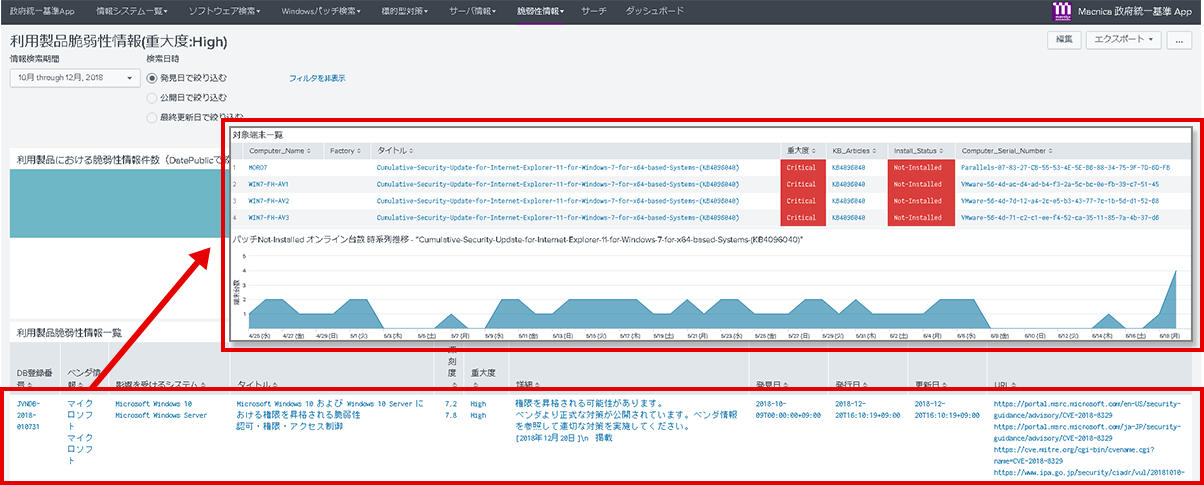
| Vulnerability information | A function that automatically collects the latest vulnerability information on the vulnerability disclosure site (JVN) and creates a list of detailed information such as vendor names, affected systems, and CVE numbers. | It is used to obtain the latest vulnerability information and confirm whether or not it affects your organization. |
| Targeted attack countermeasures | A function that can collect additional information and take action from Splunk by using the API of the configuration management product. | It is used to identify and restore information systems in the event of a cyber-attack, and to assess the risks of other information systems. |
main dashboard
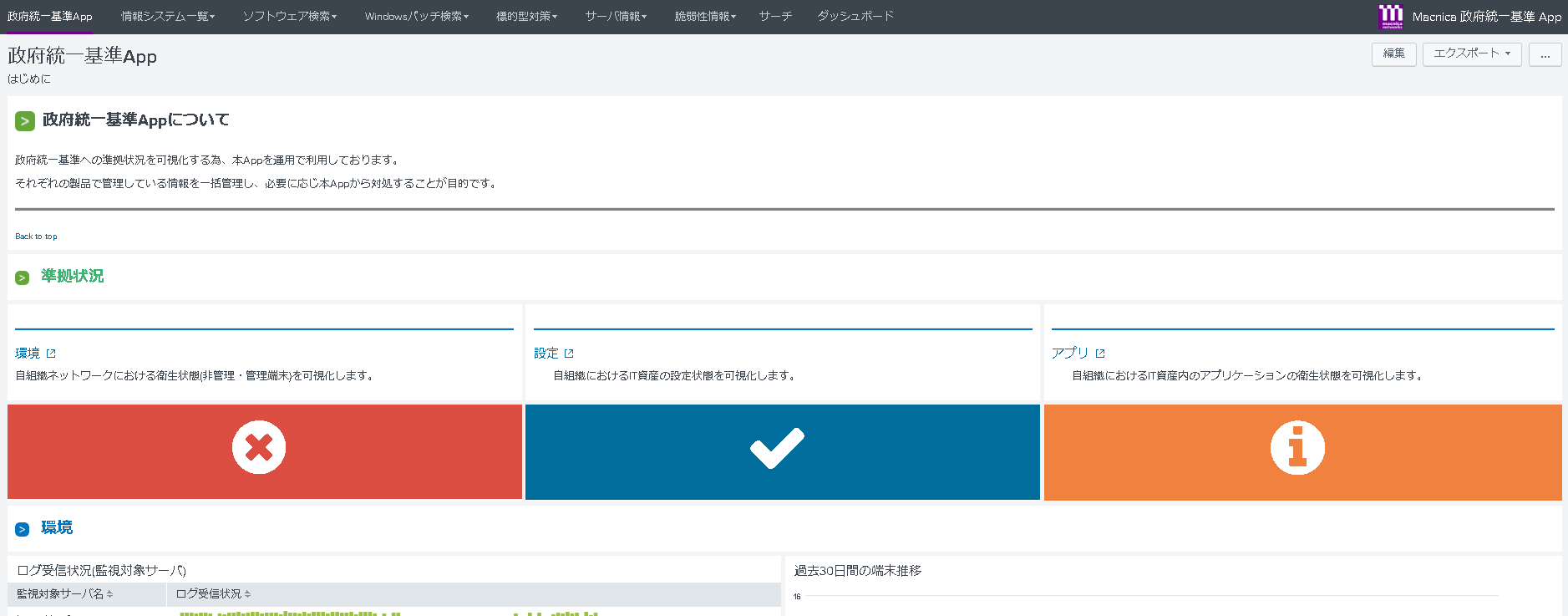
Dashboard for configuration management
Aggregate information of all terminals by ledger automation, save and visualize with Splunk
Dashboard for configuration management
Investigate“unsanitary” terminals that are detached from the security policy
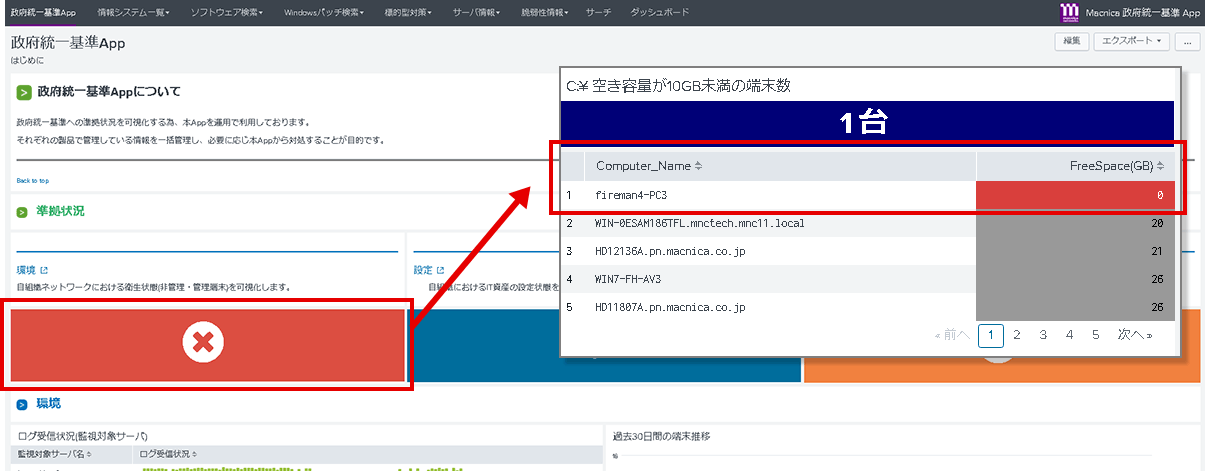
Security dashboard
Centralized management by Splunk completes everything from investigation to response (process blocking/quarantine)
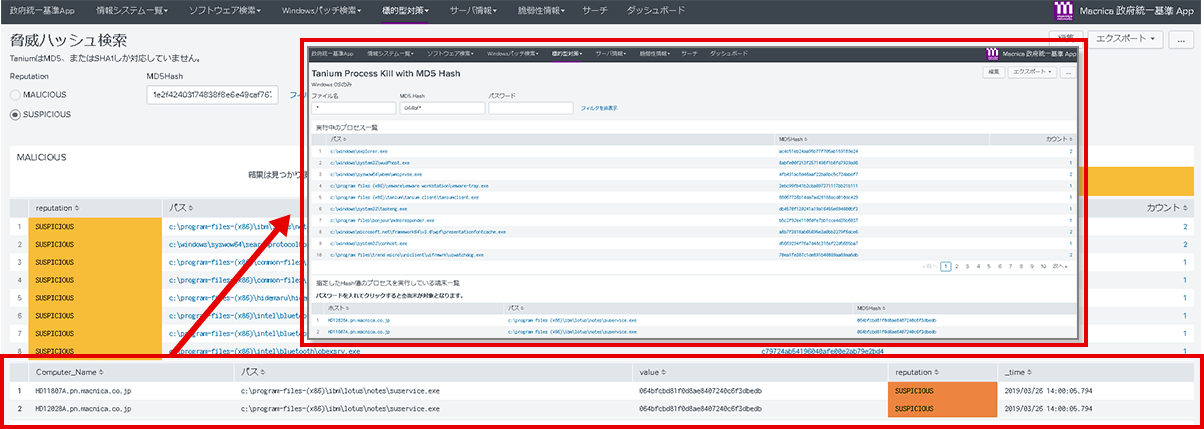
Security dashboard
Centralized management by Splunk enables everything from checking the latest vulnerability information to identifying devices
Precautions for using App that supports unified government standards
- This App is provided as a sample for customization to customers who have purchased or are considering purchasing Splunk and Tanium products through our company.
- We reserve the right to change the content of this App as appropriate due to version upgrades of Splunk products.
- The copyright of this App and other intellectual property rights belong to our company.
- It is prohibited to provide this App, search queries of this App, implementation contents such as visualization logic, etc. to anyone other than the end user who notified us.
- In addition, the terms and conditions that stipulate the contents and conditions of this App shall take precedence over other valid agreements between our company and the customer, and it is assumed that you agree to all terms before using this App.
Media introduction
An app that supports uniform government standards was introduced to the media.
Inquiry/Document request
In charge of Macnica Splunk Co., Ltd.
- TEL:045-476-2010
- E-mail:splunk-sales@macnica.co.jp
Mon-Fri 8:45-17:30