product
- Why choose Splunk
- Installation record
- price
- Splunk Enterprise Security
- Splunk Phantom (SOAR)
- Splunk ITSI (Next Generation IT Operations)
- Splunk Observability Cloud
- Splunk UBA
- Macnica CSIRT App Basic
- App for Splunk for Financial Institutions
- Splunk Analytics for Hadoop
- About Apps
- Splunk Edge Hub
- What is Splunk
service
- Dashboard/SPL Creation Pack [Implementation/Building Support]
- Version upgrade service [implementation and construction support]
- Smart Security Monitoring App [Original App/Service]
- Splunk × LANSCOPE Original App [Original App/Service]
- Security Monitoring App for Box [Original App/Service]
- Cloud Security Monitoring App [Original App/Service]
- List of services
Specifications/Technical Information
Application for evaluation machine
- FAQ

Splunk
Splunk
Splunk into a modern SIEM
"Smart Security Monitoring App"
With the rapid spread of telework in recent years, the number of entry routes for attackers has increased, making it easier for attackers to infiltrate companies. In addition, due to the sophistication of attack methods, it is becoming extremely difficult to deal with all infringements with perimeter security alone. Under these circumstances, "security operations centered on SIEM", which analyzes a wide range of data sources, is gaining importance as one of the most effective countermeasures.
Smart Security Monitoring App (SSMA) is our original SIEM-App exclusively for Splunk Enterprise designed and developed under the concept of "providing necessary and sufficient functions for modern enterprise security".
Main function
Equipped with three function groups initially
- Detection function by extensive log correlation analysis
- Detection function by IoC*1 matching using threat intelligence
- A collection of dashboards for efficient and lean alert management/tracking/dive-in
Quickly launch detection operations to deal with advanced cyberattacks and improve the efficiency of post-detection operations in responding to alerts. This will upgrade your Splunk to a "modern SIEM" at once.
*1: The basic idea of IoC is to quickly detect attacks and minimize the scope of their impact by creating a database of cyber-attack traces and using them as technical specifications.
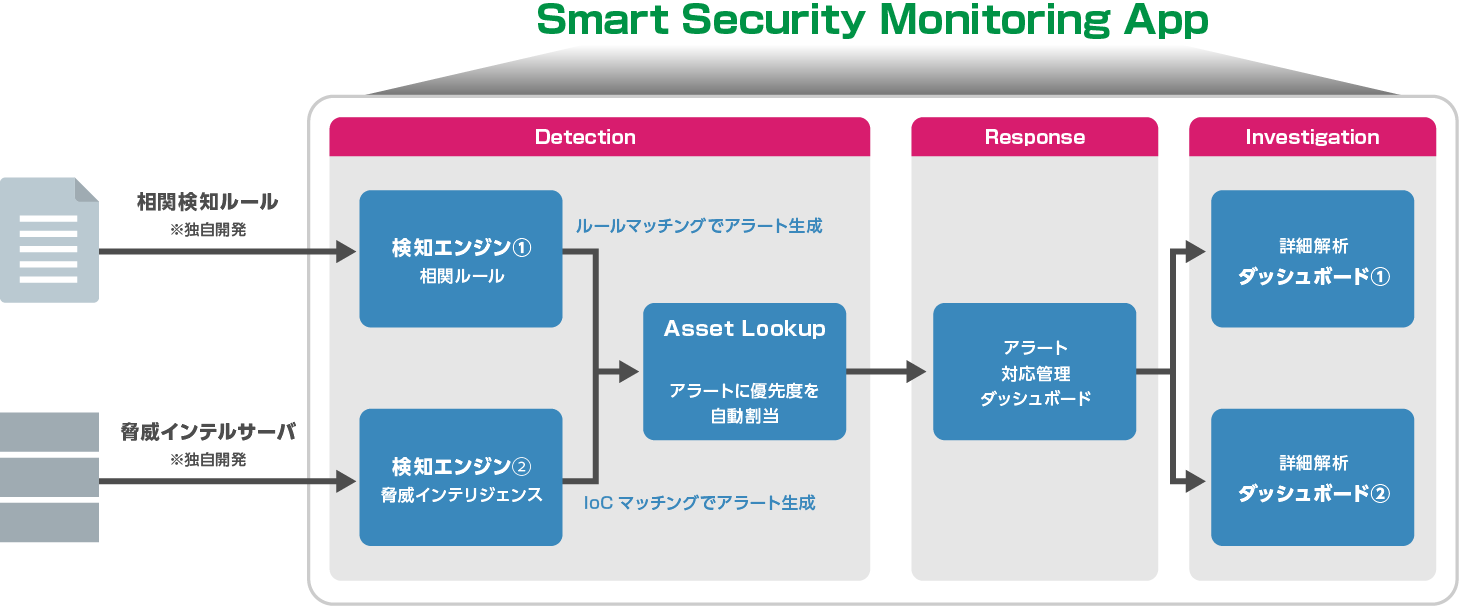
Detection①
Log-based correlation detection rules
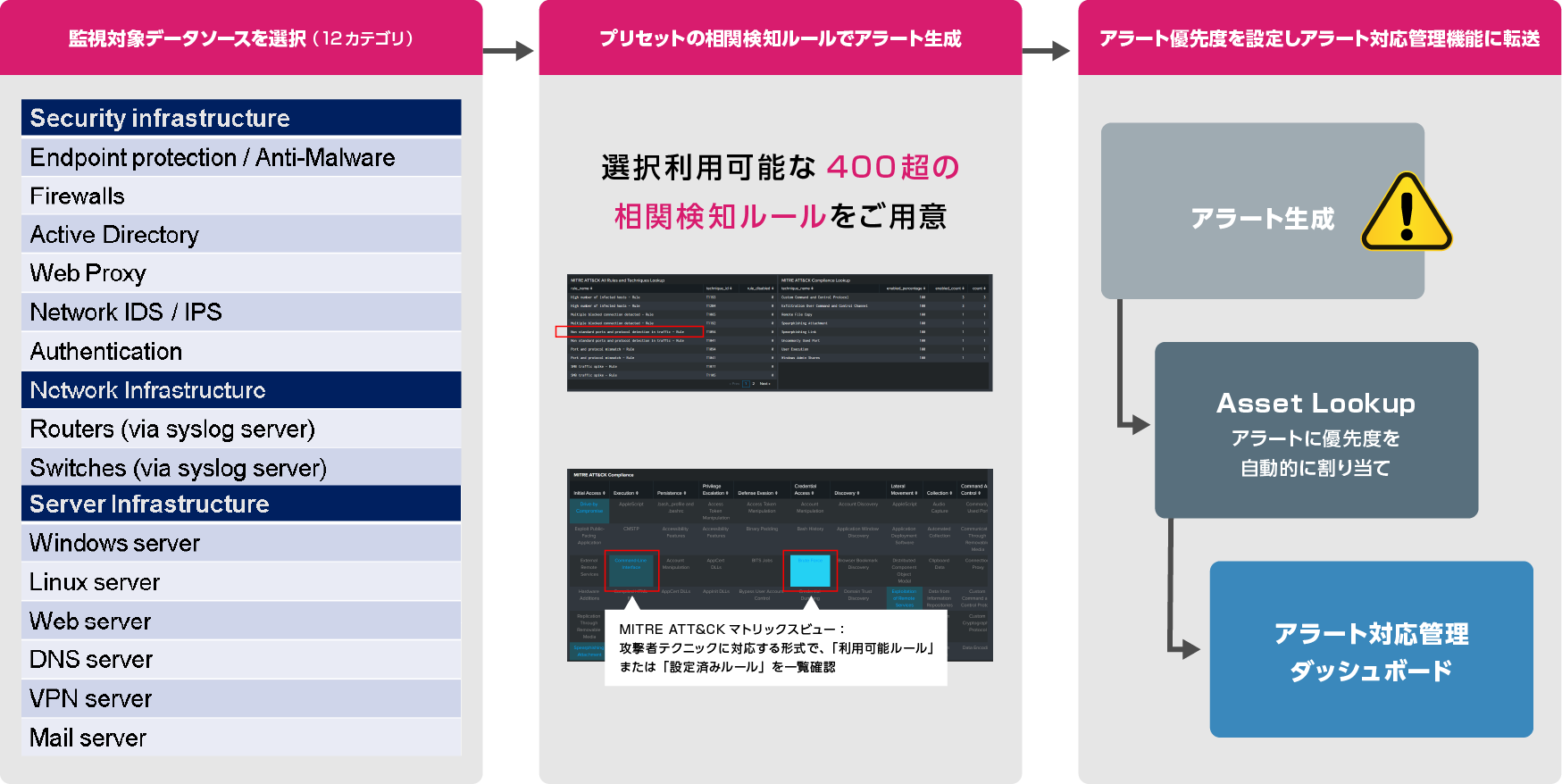
- Over 400 correlation detection rules developed independently by Positka (choose and implement from preset rules)
- Correlation detection using a wide range of data sources in 12 categories (AD, endpoints, server logs, etc.)
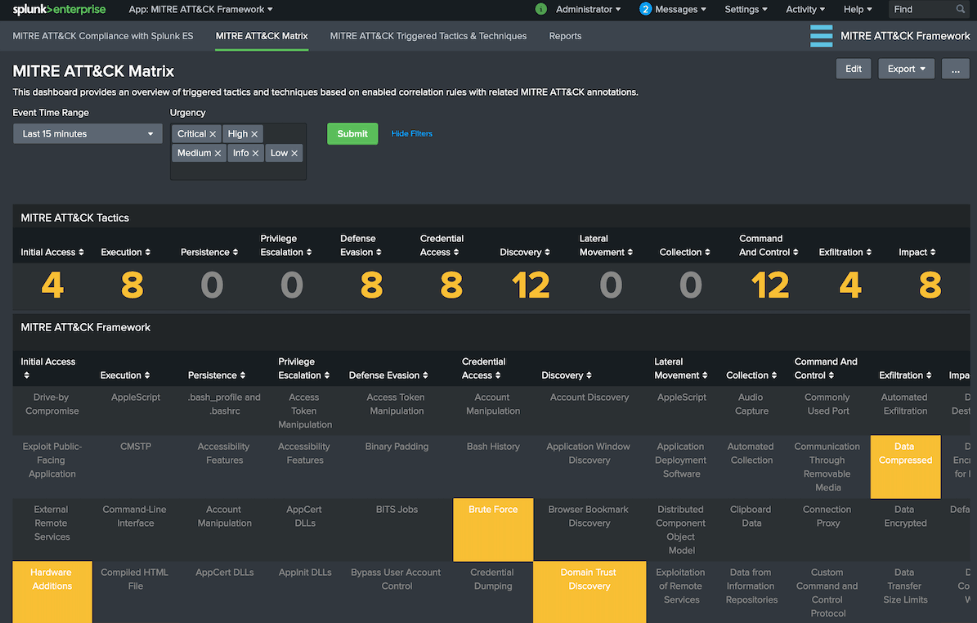
- Designed based on the MITER ATT&CK framework to detect ATT&CK-defined "attacker techniques"
Detection②
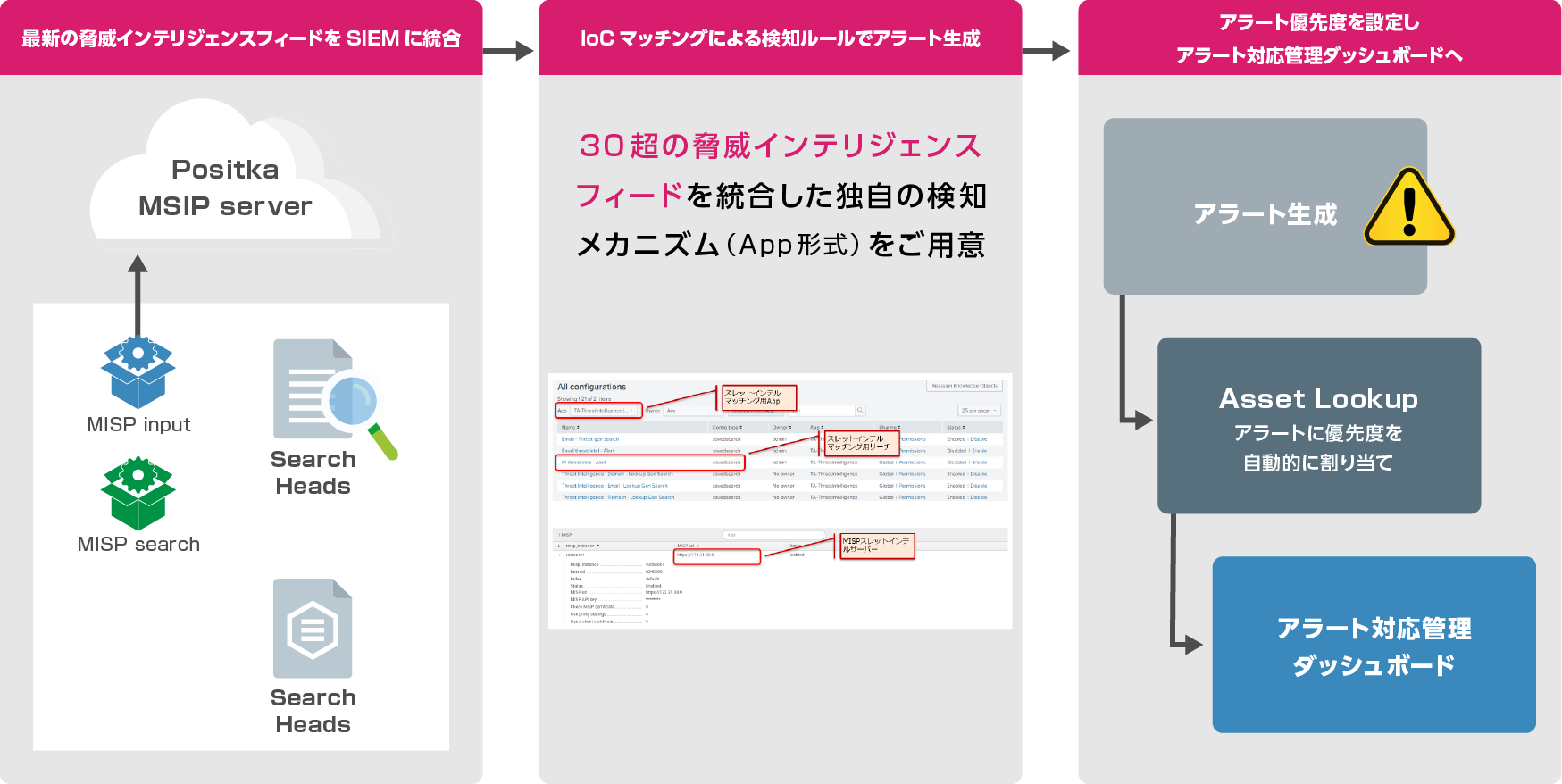
IoC matching

- Integrate IoC information from proprietary threat intelligence (MISP-based) into SIEM
- Implement detection rules that can deal with the latest threats with IoC matching App
Response
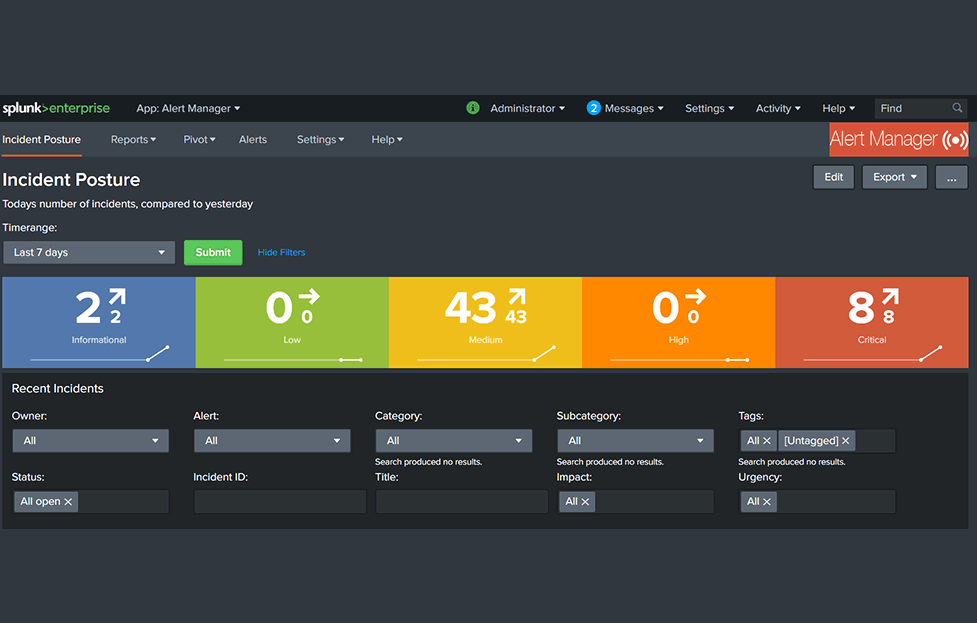
Alert response management
- Equipped with alert response management mechanisms such as alert status management and owner assignment
- Automatically assign alert priority to generated alerts according to Asset type
- Necessary and sufficient various alert filter functions
Solution image
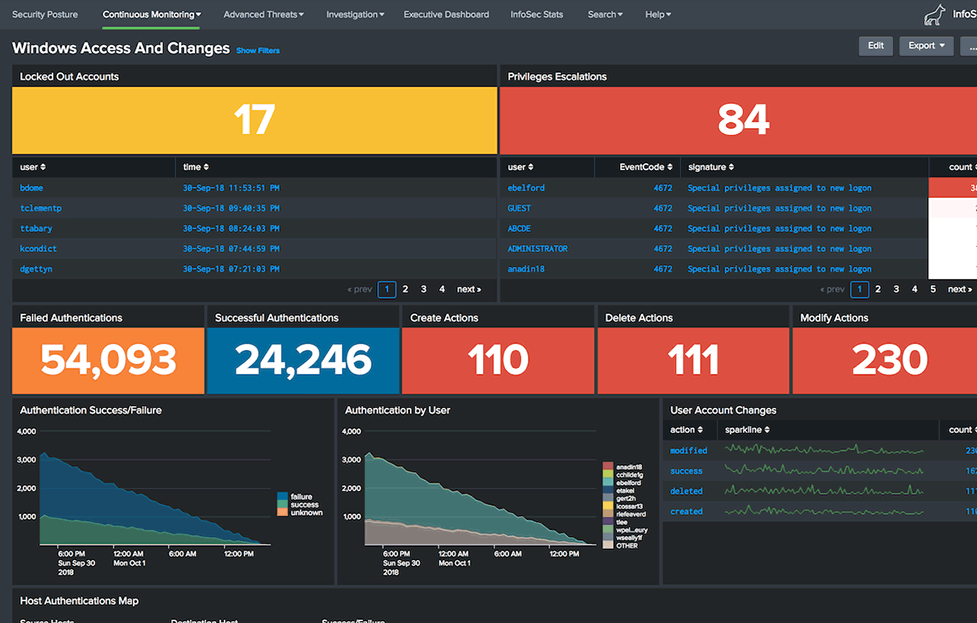
Seamlessly provide a set of functions required for daily operations of SOC
This App integrates the functions and mechanisms required for the actual operation of SIEM, and is designed to cover a series of SOC routine tasks from "detection to alert response management to detailed investigation".
It includes a function that automatically assigns "alert priority according to related assets" to all generated alerts, and has a mechanism to streamline alert handling after detection.
detection mechanism
Two Detection Mechanisms to Deal with Sophisticated Cyberattacks
Detection Mechanism ①: Correlation Detection Rule
A rule library of over 400 correlation detection rules for monitoring various data sources. Detection rules are designed as a set of rules for detecting "attacker techniques" defined by MITER ATT&CK *2, making it possible to detect sophisticated attacker techniques and behaviors.
For example, a rule that detects from authentication logs the brute force *3 behavior often used by attackers to elevate privileges (taking Active Directory administrator privileges, etc.) after intrusion, and lateral movement within the target company by attackers. Over 400 rule libraries are available, such as rules for detecting abuse of remote services (SMB *4, RDP *5, etc.) that are frequently used when planning for security.
*2: The flow and methods of cyberattacks have been systematized by MITER (USA), a not-for-profit organization that implements CVE numbering.
©2020 The MITER Corporation.
*3: One of the methods of deciphering passwords by "brute force attack".
*4: Abbreviation for Server Message Block. A protocol (communication protocol) and communication service for sharing files and printers among multiple Windows computers on a local network (LAN)
*5: Abbreviation for Remote Desktop Protocol.
Detection Mechanism ②: Threat Intelligence
In conjunction with our own threat intelligence service, it is possible to detect suspicious behavior and communications as early as possible from the latest IoC (Indicator of Compromise) *1. It works in conjunction with an intelligence service that integrates over 30 threat intelligence feeds, integrates IoC into SIEM, and performs various detections by matching with IoC.
For example, based on IoC, we have prepared a number of searches that detect accesses to domains frequently used by attackers and communications to IPs that are recognized as C&C servers. This makes it possible to apply the latest threat intelligence that integrates information from around the world to SIEM operations and improve the level of security response.
Price/Service
This App will be provided as a package service that bundles initial installation work and first year support. The pricing model has the following characteristics:
(1) Pricing system that does not depend on the captured log volume
It is determined based on the number of types of imported data sources and the number of correlation detection rules to be implemented. Therefore, the log volume ingested is not linked to the price.
(2) A price that bundles the introduction work at the time of launch
迅速なSIEM運用立ち上げのため、以下の導入/実装作業を弊社にて代行します。上記金額には各種作業代行費用が含まれています。
| menu | Base package
|
Standard package
|
|---|---|---|
| standard price | 11.6 million yen *Includes first-year support and implementation agency fees *Requires remote work. |
15 million yen *Includes first-year support and implementation agency fees *Requires remote work. |
Service contents included in the above price
|
||
*The prices shown above do not include tax.
*The above prices are based on the premise of implementation for remote work (using VPN or remote desktop). (If on-site work is required, individual quotations will be provided.)
*App/solution customization is not included in the above services. (If necessary, please purchase the "Dashboard Creation Pack" separately.)
* Tuning of detection rules after completion of initial implementation and initial tuning is not included in the above service range. (If necessary, please purchase the "Dashboard Maintenance Pack" separately.)
Weekdays: 9:00-17:00
Inquiry/Document request
In charge of Macnica Splunk Co., Ltd.
- TEL:045-476-2010
- E-mail:splunk-sales@macnica.co.jp
Weekdays: 9:00-17:00