McAfee
マカフィー
McAfee Endpoint Security
McAfee Endpoint Securityの概要
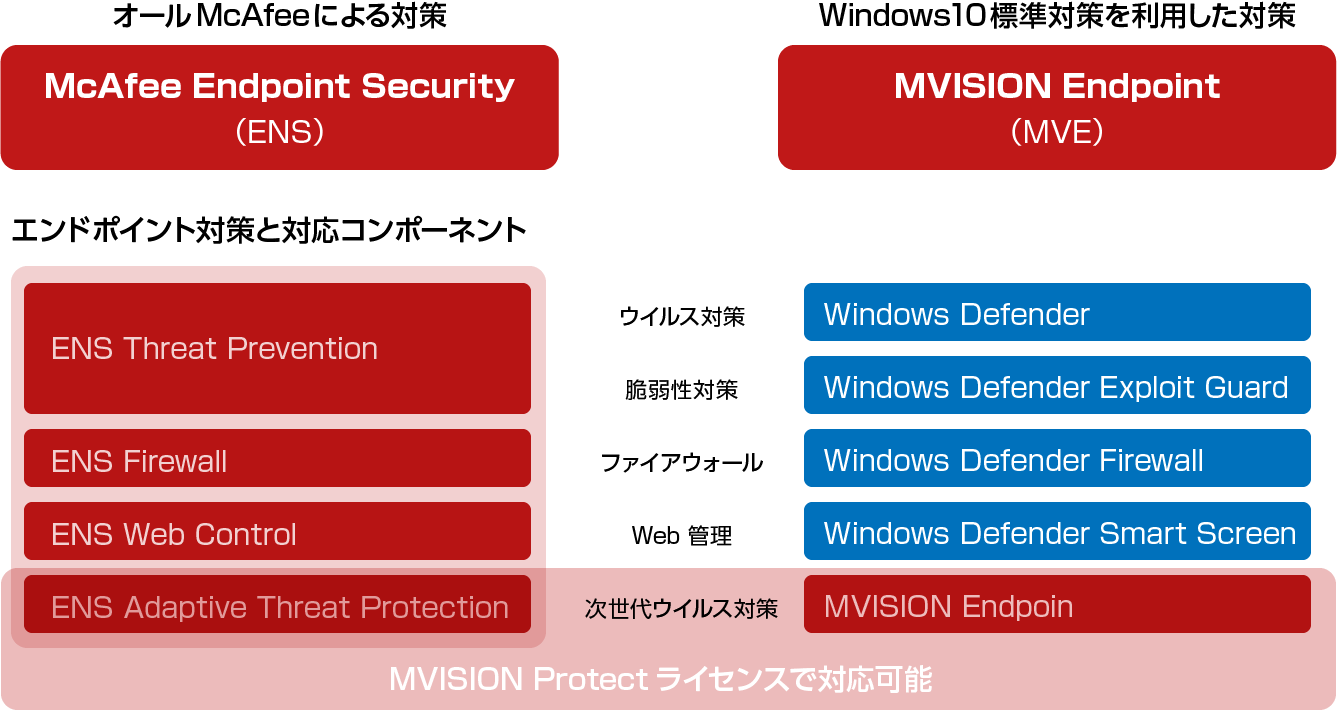
Windows向けエンドポイントセキュリティは 2つの選択肢があります。
ウィルス対策
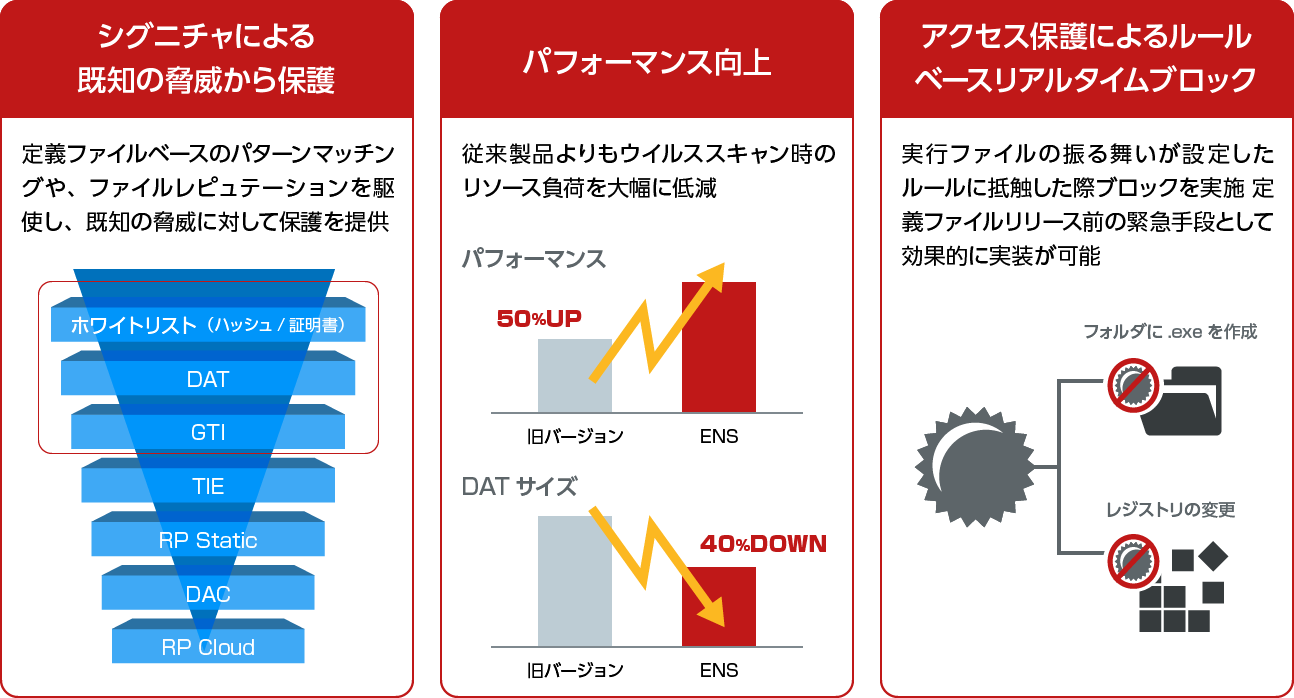
- 既知のマルウェア対策を効率よく実現
- ルールベースブロックも実施
- 高度なスクリプトスキャン(AMSI連携)
- Windows10では、パソコンにインストールされているウイルス対策ソフトのスキャン機能を別のプログラムから呼び出せるようにするための新たな仕組みが実装されることになった。「Antimalware Scan Interface(AMSI)」というインターフェースを使って、プログラムの中からウイルス対策ソフトにコンテンツを引き渡し、マルウェアではないかどうかをチェックできる。
- 悪質なスクリプトは何重もの難読化が施してあったとしても、最終的には可読化され、明白なコードがスクリプト処理エンジンに引き渡される。その段階で、スクリプト処理エンジンはWindows AMSIの新しいAPIを呼び出して、可読化された内容のスキャンを要求できる。
- Powershell、VB Script、Java ScriptのコードをAMSIがNESに引き渡してスキャンが可能。
脆弱性対策
Endpoint Security Threat Prevention
- エクスプロイト防止
ファイアウォール
Endpoint Security Firewall
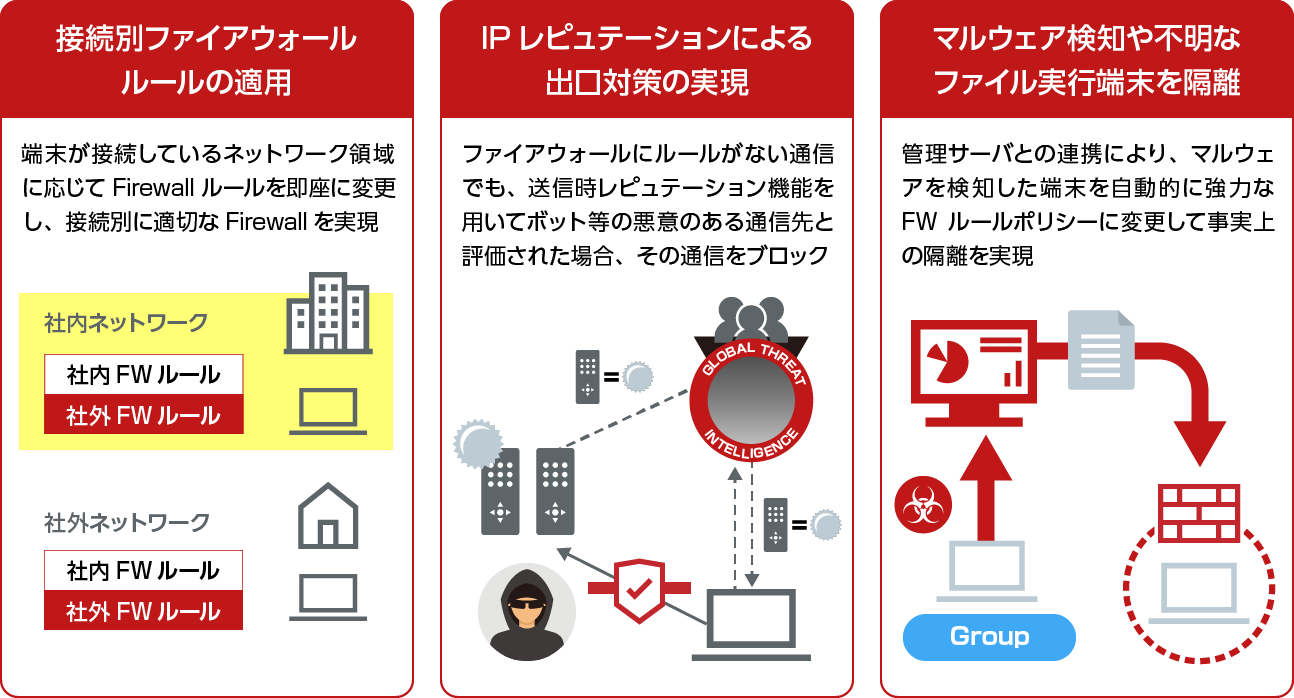
- 柔軟性と堅牢性を備えた Firewall機能
- ネットワーク隔離も実現
Web管理
Endpoint Security Web Control
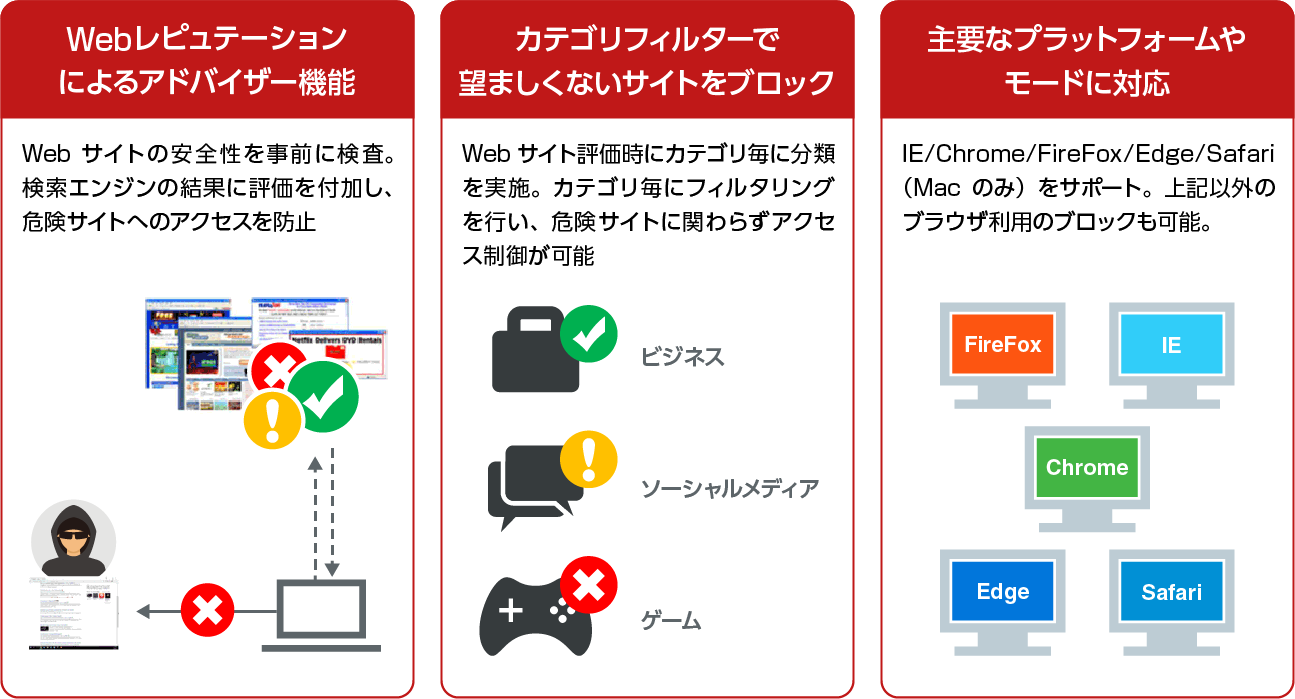
- 感染ルートの多い Webサイトはマルウェア着弾前に検査を実施
次世代ウィルス対策
Endpoint Security Adaptive Threat Protection
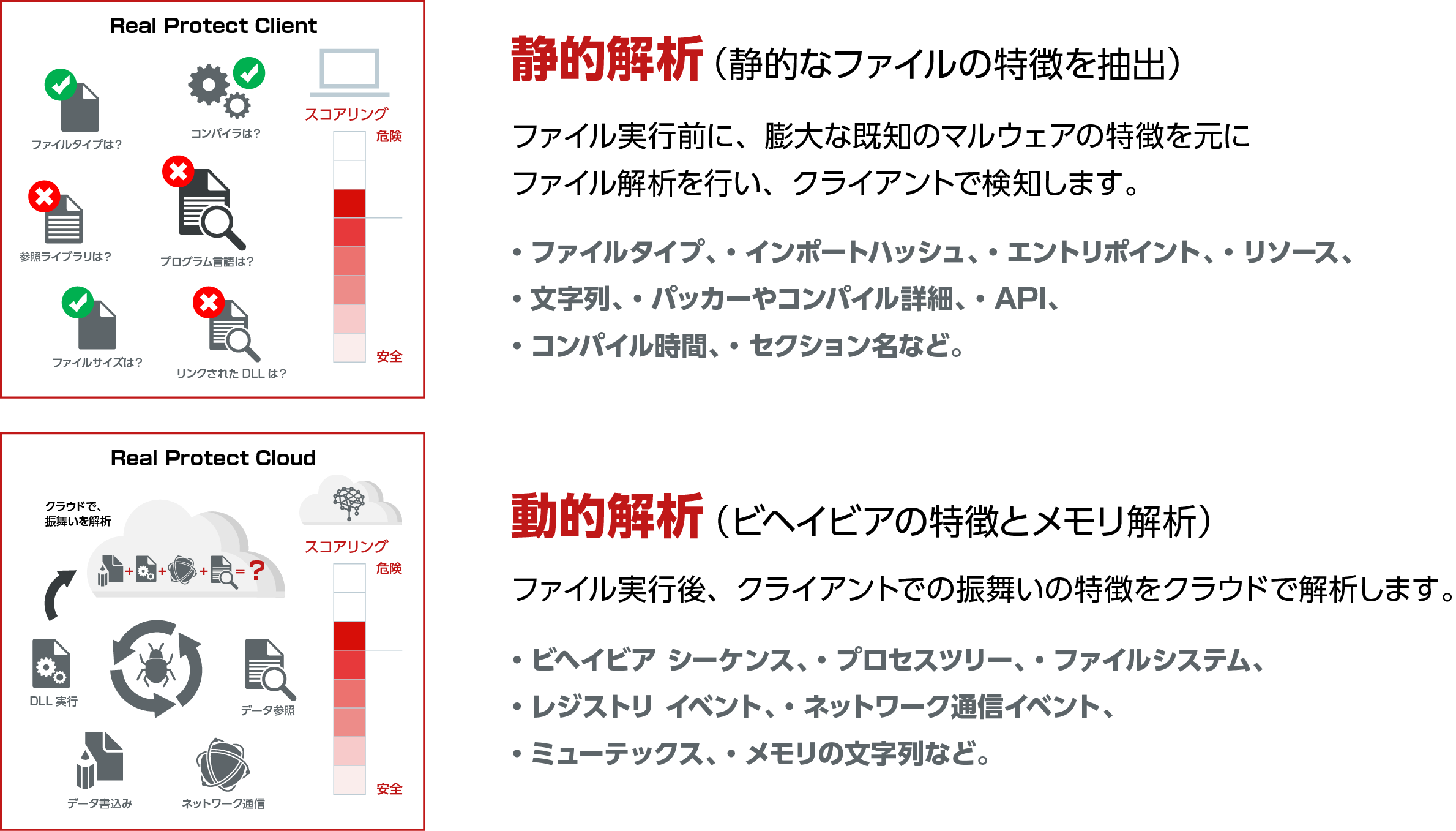
- 機械学習
- Dynamic Application Containment(DAC)
- ロールバック機能
Dynamic Application Containment(DAC)
- 脅威判定できなかったプロセスを監視し、悪意のある動作のみをブロック(封じ込め)
- ファイルレピュテーションでは「信頼」「脅威」の判定ができなかったプロセスが対象
- プロセスはシステム上で動作しているが、ルールで禁止されている危険な動作はできないためシステムに影響を与えることはほぼ不可能
- DACによる動作の制限例
- ランサムウェアの特徴的な動作
- NWや外部媒体を使った拡散
- 他のプロセスに対する不正なアクセス(インジェクション)
- 別の実行可能な形式のファイルの作成(ダウンローダー、ドロッパーの動作)
ロールバック機能
- 脅威が行った変更をロールバックし、脅威実行前の元の状態に可能な限り復元します。
- レピュテーションが「不明」以下のプロセスとその子プロセスの動作を監視します。
- 監視対象のプロセスが不正な挙動を示すと、プロセスを停止させるとともに、実行前の状態に復元します。
次世代ウィルス対策(MVISION Endpoint)
MVISION Endpoint
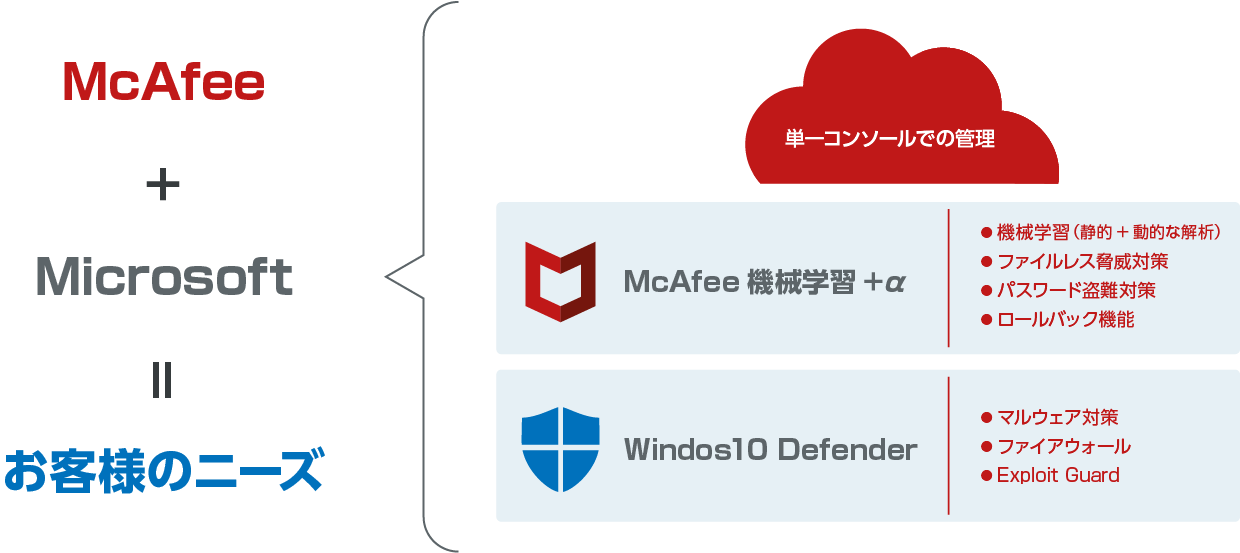
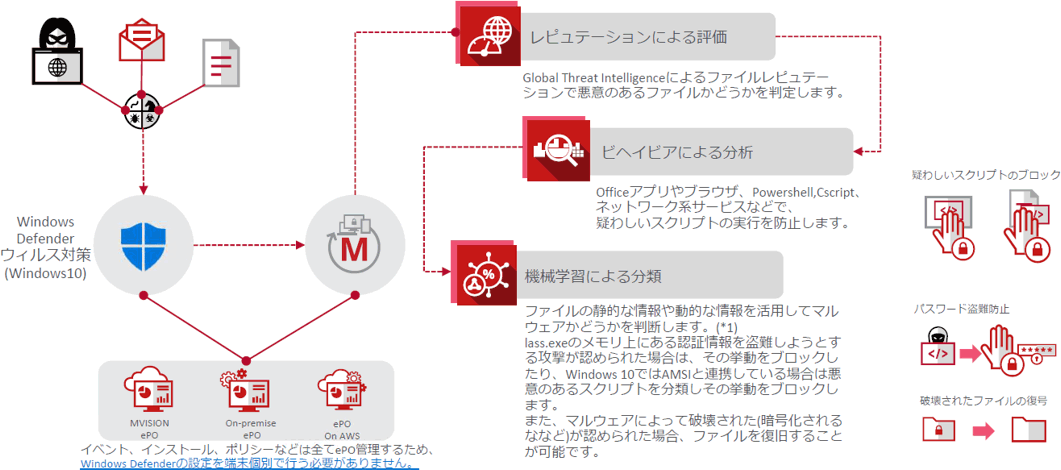
- Windows Defender と連携する次世代ウイルス対策
- Windows Defender との連携イメージ
- 機械学習機能
- MVISION Endpoint のその他機能
MVISION Endpointには、機械学習の他に、+αの機能として以下の新しい機能が含まれます。
- ロールバック機能:ランサムウェア等に万が一感染した場合、感染前の状態に戻すことが出来る機能
- パスワード盗難対策:認証情報(ログイン パスワード)の盗難を防御する機能(Credential Theft Protection)
- ファイルレス脅威対策:Windowsの「PowerShell」や「WMI」を悪用したファイルレスマルウェアによる攻撃を防御

評価版申込み
- 無償で30日間ご評価いただけます。
- 以下のフォームよりお申し込みください。
ENS テクニカルチェックのススメ
- VSEからENSへの円滑なバージョンアップのために、現環境の利用バージョン、ポリシーの状況把握を実施させていただきます。
- バージョンアップ作業についてお気軽にご相談ください。