
Google Cloud
Google Cloud
Attack surface management ~Understanding of unrecognized assets published on the Internet~
Remote work has increased due to changes in work styles, and network connections via VPN have increased. Attackers are targeting vulnerabilities in assets exposed to the Internet that are poorly managed, such as VPNs, as the next attack point for Web/mail.
Attack surface management (ASM) provided by Mandiant can identify your company's public assets on the Internet, visualize the risks of cyber attacks hidden in them, and use them for your company's security measures.
Mandiant Attack surface management
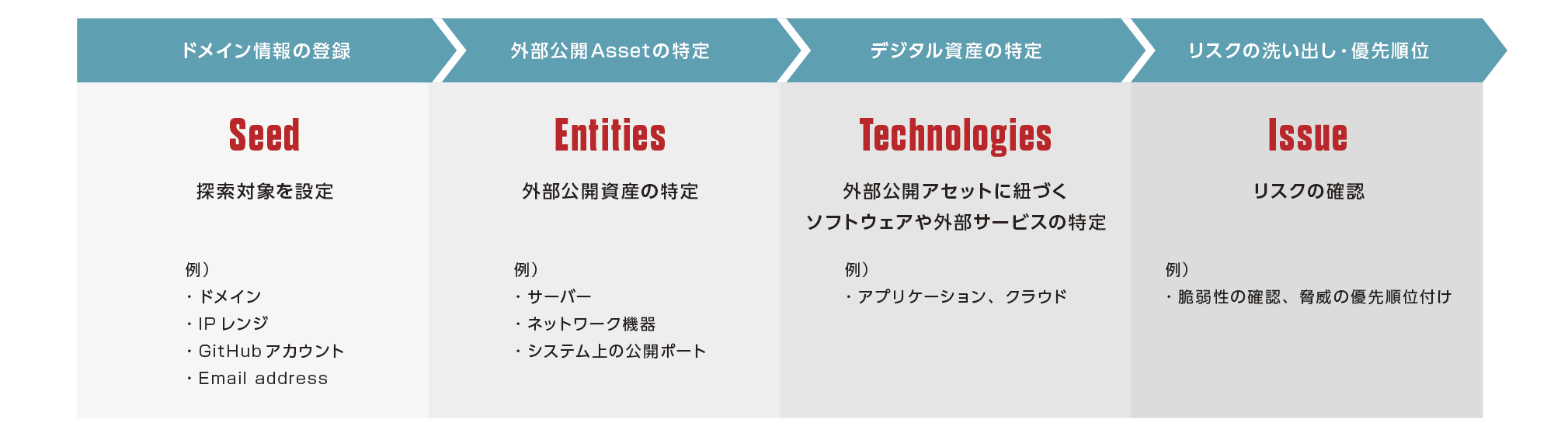
From the domain registered in the ASM tool, identify externally published assets and system information connected to the outside, and visualize risks such as vulnerabilities hidden in them
- Understand the company's Internet-published assets and visualize the risks of cyberattacks hidden therein
- Execute active and passive type scans for the identified vulnerabilities of your company's public assets on the Internet, and search deeper for vulnerability information.
- For discovered vulnerabilities, risk prioritization based on Mandiant's years of experience in cyberattacks
Flow from external public asset search to discovery
Feature (1) Detection of highly accurate vulnerability information
Vulnerability scans are performed in the following ways:
- Passive scan
Points out vulnerabilities based on information such as the application being used and its version
*Passive scanning alone may result in false positives and vulnerabilities that cannot be found.
-Vulnerability is judged even if a patch is applied by WAF/IPS, etc. - Active scan
Run real vulnerability attacks to check for security holes
If it is protected or patched, it will not react because the vulnerability cannot be exploited.
Newly disclosed vulnerability information is quickly updated to tools and reflected in active scans
Reduces tool operation load by displaying results only for highly accurate vulnerability information
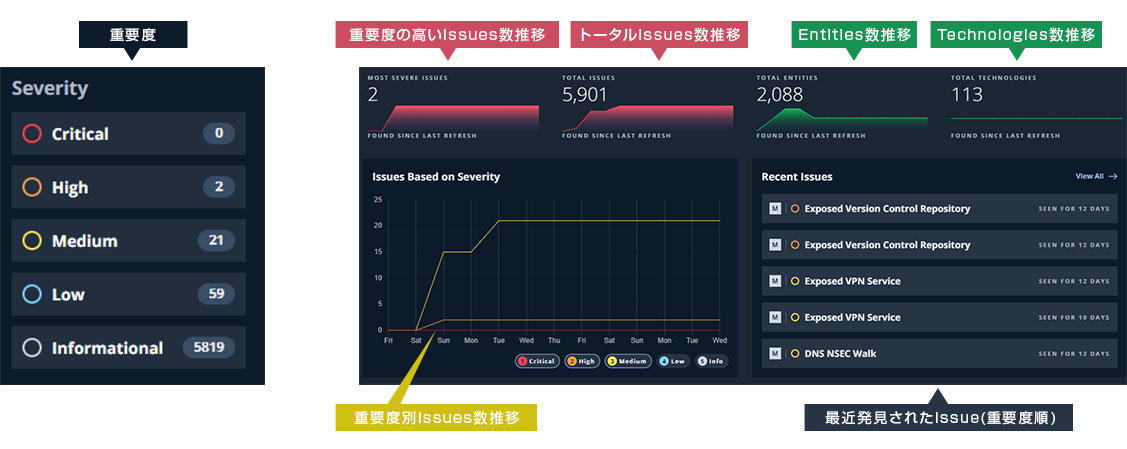
Feature 2 Prioritization of vulnerability information
Mandiant prioritizes the risks of vulnerability information based on the knowledge gained in the field of cyber attack countermeasures
Prioritize vulnerability information that really poses a risk to your company in 5 levels
It is possible to respond to high-priority vulnerabilities
Inquiry/Document request
Macnica Google Cloud
- TEL:045-476-2010
- E-mail:google-sales@reseller.macnica.co.jp
Weekdays: 9:00-17:00