product
- Why choose Splunk
- Installation record
- price
- Splunk Enterprise Security
- Splunk Phantom (SOAR)
- Splunk ITSI (Next Generation IT Operations)
- Splunk Observability Cloud
- Splunk UBA
- Macnica CSIRT App Basic
- App for Splunk for Financial Institutions
- Splunk Analytics for Hadoop
- About Apps
- Splunk Edge Hub
- What is Splunk
service
- Dashboard/SPL Creation Pack [Implementation/Building Support]
- Version upgrade service [implementation and construction support]
- Smart Security Monitoring App [Original App/Service]
- Splunk × LANSCOPE Original App [Original App/Service]
- Security Monitoring App for Box [Original App/Service]
- Cloud Security Monitoring App [Original App/Service]
- List of services
Specifications/Technical Information
Application for evaluation machine
- FAQ

Splunk
Splunk
Why are SIEM and Splunk indispensable for security measures in the new era?
Compared to a few years ago, corporate security measures are placing more emphasis on the endpoint side, and more and more customers are choosing to outsource their security functions. At this Splunk Circle Spring 2022 panel discussion, Mr. Katsuaki Shimadera from Recruit and Mr. Shintaro Watanabe from JCOM discussed "Why SIEM? Why Splunk?" We will deliver the pattern in digest.

Mr. Katsuaki Shimadera
Recruit Co., Ltd.
security operations center
Log analysis platform team leader

Mr. Shintaro Watanabe
JCOM Co., Ltd.
Cyber Security Promotion Office
manager

Masayuki Yoshida
Macnica
2nd Technology Department 1st Technology Department 1st Section
(Splunk Technology) Deputy Manager
Is SIEM unnecessary for modern security measures?
"SIEM (Security Information and Event Management)" is a product that supports "detection," "response," and "recovery" in the Cyber Security Framework (CSF) of NIST (National Institute of Standards and Technology). Centrally manage logs from various security and network devices and generate alerts for activities identified as potential security incidents through correlation analysis.
As cyberattacks have become more sophisticated and sophisticated in recent years, investigations using SIEM in companies have become commonplace. On the other hand, products called XDR (EDR/NDR, etc.) are now equipped with functions similar to SIEM, and some people have started to hear the opinion that SIEM is unnecessary.
On top of that, first of all, we discussed why SIEM is necessary again.

Types of security measures and status of functional expansion
What are the benefits of using SIEM?
First, we asked Mr. Shimadera about Recruit's security efforts.
"At Recruit, we consider security threats in four quadrants: commercial environment, work environment, external actors, and internal actors. I think SIEM is effective in all four quadrants. In other words, we monitor with various sensors and logs for malware and account infringement.
Keeping track of all these things can be a pain, so a SIEM can be very useful. Looking at the phases, there are some overlapping solutions such as EDR, but SIEM does not work on its own, but collects various sensors and logs for centralized management and correlation analysis. We use them while complementing each other.” (Mr. Shimadera)
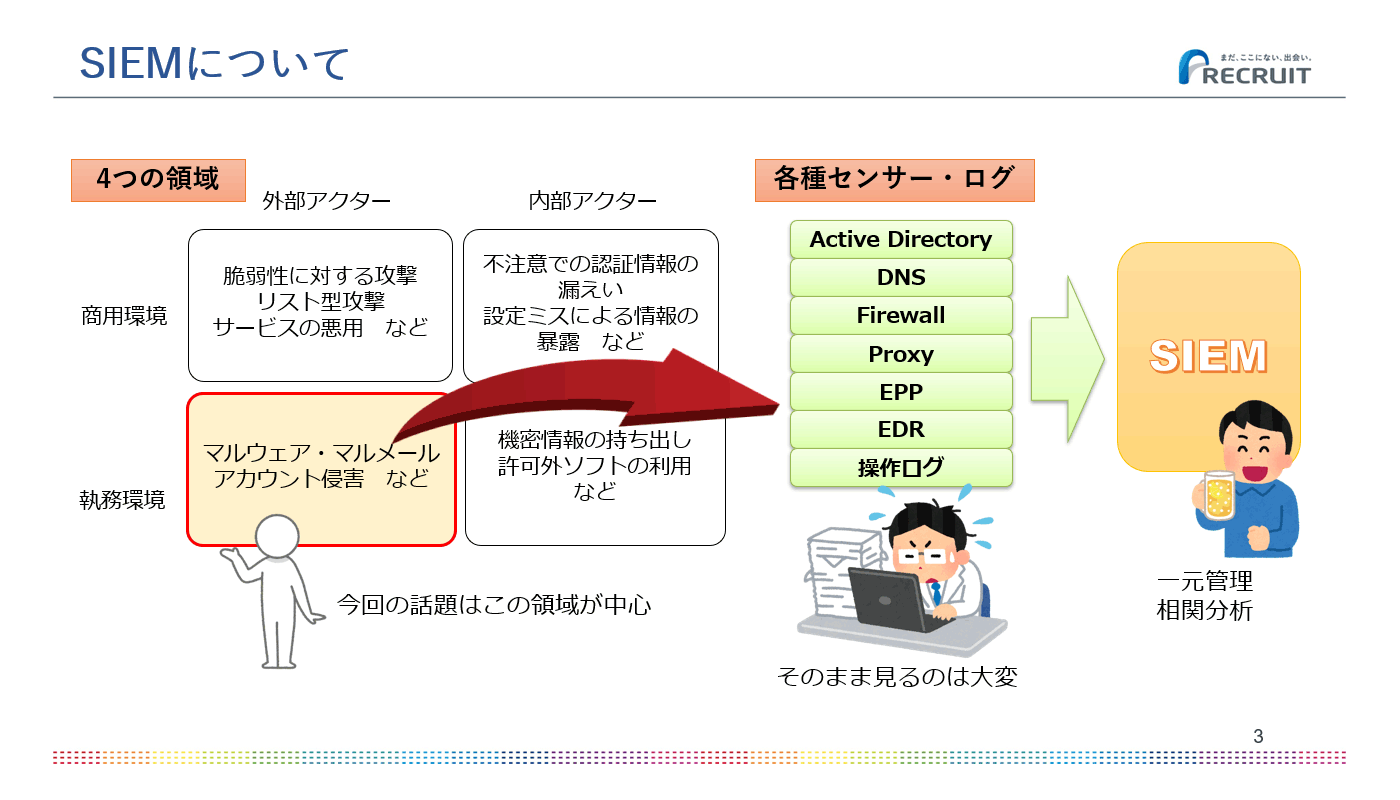
SIEM Utilization in Recruitment
Next, we asked Mr. Watanabe of JCOM about the usefulness of SIEM.
“Mr. Recruit talked about external threats, so I will focus on internal fraud. Detection of internal fraud, represented by the taking of confidential information, is not complete with a single sensor log. Malicious The insider first needs to obtain the data, then process it, etc. And finally, the act of taking it out occurs, and these are basically acts with authority That's it.
Identifying candidates for suspicious behavior requires considering the context over time. This requires taking in and analyzing information from multiple sources. A SIEM is effective in achieving this.
JCOM sends information to Splunk Cloud, including information from various internal systems, authentication infrastructure for customers, and applications such as member pages. For fraud detection, we have also introduced Exabeam, a UEBA product, and only use the Advanced Analytics function. (Mr. Watanabe)
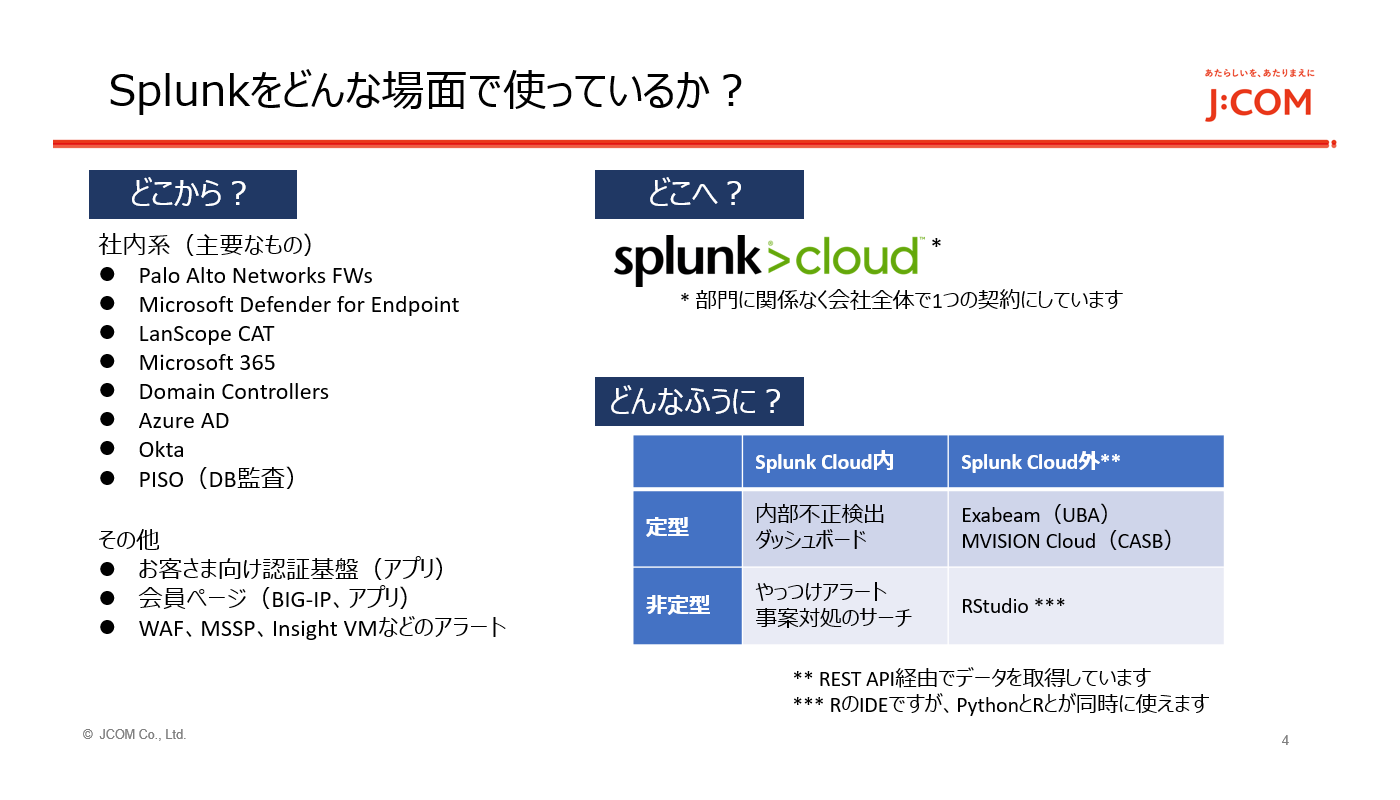
Utilization of SIEM in JCOM
Differences in actual operation that cannot be seen in catalog specifications
Besides Splunk, there are many other SIEM products on the market. So, where is the point of differentiation unique to Splunk? Mr. Shimadera explained the specific Splunk usage environment in Recruit.
“At Recruit, we use Splunk for malware countermeasures. There are two types of VDI: secure VDI, which handles customers’ personal information, and standard VDI, which does not handle personal information. Management is handled by another internal system department, so we asked them to install Forwarder so that the SOC can receive logs, and the received logs are put into the log analysis infrastructure for security monitoring.
In addition, when comparing Splunk and other companies' products, Splunk is "handling various logs", "enrichment (*)", "correlation analysis", "long-term log storage", and "agent provision" in all request categories. We were able to confirm its superiority." (Mr. Shimadera)
*Enrichment: Refers to adding information from a csv file, etc. to the imported data. This process makes it easier for Splunk users to understand the data.
Also, when compared at the actual operation level, which cannot be seen from the catalog specs alone, a big difference appeared.
For example, in the case of "supporting various logs", in the case of Splunk, it is possible to flexibly define fields after importing logs, and in addition, even if the log format changes slightly, it can be handled without re-importing. Splunk calls this "schema-on-the-fly". On the other hand, other companies' products cannot import logs unless the fields are defined in advance, and if the log format changes, it will be necessary to import them again.
As for "enrichment", since it can be enriched by lookup after log import, there is almost no need to import logs again. By the way, in other companies' products, it is necessary to enrich before log import, and if you want to change it, you need to import it again.
“To sum up, I think the main points of differentiation of Splunk are that there is little difficulty in importing logs, that it can be operated without problems even if the field changes slightly, and that enrichment can be done after importing.” (Shimadera) Mr)
Reasons for continuing to use Splunk as a CSIRT
Mr. Watanabe then gave two reasons for continuing to use Splunk from the standpoint of a CSIRT that performs digital forensics and incident response.
First, the SPL query language is very practical. Case-insensitive searches are efficient, and enrichment is essential for digital forensics.
Second, you can get data in CSV format via REST API. Other SIEM products can output data via REST APIs, but they are often limited to JSON format. In order to use it in statistical analysis software, it is necessary to convert the nested JSON format into tidy data that is easy to parse. This task consumes a lot of memory. However, Splunk can output data in CSV format immediately, so there is no stress.
"It's easy to get started with Splunk. If you get a job with it, that's a success. Then you can look deeper into the structure, and you can broaden it. It's a tool that makes the user smarter along with it." (Mr. Watanabe)
Meet modern security needs with Splunk
“Why SIEM?”
Security operations require many functions such as monitoring, detection, analysis, and response. By using SIEM, it is possible to respond quickly to incidents through centralized management and correlation analysis of logs. In addition, by complementing each other with SIEM and other security products, it is possible to achieve further threat protection while reducing management man-hours.
“Why Splunk?”
It is also attractive that there is no need for prior schema definition and there is a large difference in enrichment after importing. In addition, while other companies' products are limited in the types of logs that can be handled, Splunk can handle a wide variety of logs, making it possible to improve detection accuracy through correlation analysis of multiple logs. In other companies' products, collation work with other logs occurs in the analysis phase after detection, but Splunk can handle it with one consistent common analysis platform. Therefore, Splunk can be said to be the most suitable SIEM product in today's world, where the burden of responding to incidents is low and countermeasures against the latest ransomware and malware are required on a daily basis.
Inquiry/Document request
In charge of Macnica Splunk Co., Ltd.
- TEL:045-476-2010
- E-mail:splunk-sales@macnica.co.jp
Weekdays: 9:00-17:00




