product
- Why choose Splunk
- Installation record
- price
- Splunk Enterprise Security
- Splunk Phantom (SOAR)
- Splunk ITSI (Next Generation IT Operations)
- Splunk Observability Cloud
- Splunk UBA
- Macnica CSIRT App Basic
- App for Splunk for Financial Institutions
- Splunk Analytics for Hadoop
- About Apps
- Splunk Edge Hub
- What is Splunk
service
- Dashboard/SPL Creation Pack [Implementation/Building Support]
- Version upgrade service [implementation and construction support]
- Smart Security Monitoring App [Original App/Service]
- Splunk × LANSCOPE Original App [Original App/Service]
- Security Monitoring App for Box [Original App/Service]
- Cloud Security Monitoring App [Original App/Service]
- List of services
Specifications/Technical Information
Application for evaluation machine
- FAQ

Splunk
Splunk
Effective ways to promote zero trust as seen in Splunk use cases [Splunk Circle 2021 Fall]
Triggered by the rapid increase in remote work and the spread of cloud services, the new security framework "Zero Trust" has begun to attract attention. So what are the challenges for companies to tackle Zero Trust? In this article, we will explore Zero Trust initiatives and challenges from the case studies of Taisei Corporation and Sega Sammy Holdings.

TAISEI CORPORATION
President's Office Information Planning Department
Platform Planning Office Manager
Mr. Tetsuya Yamada

TAISEI CORPORATION
President's Office Information Planning Department
Platform Planning Office Manager
Mr. Masatoshi Ueno

SEGA SAMMY HOLDINGS INC.
IT Solution Headquarters
Global Security Office
specialist
Mr. Masahiro Sato
What is Macnica 's definition of zero trust?
Currently, the use of cloud services has become indispensable for conducting business activities, and the momentum is increasing at an accelerating pace. Furthermore, due to the recent corona pandemic, the number of opportunities to work outside the company has increased, such as the rapid increase in the introduction of remote work by companies. As a result, the conventional perimeter defense, which blocks threats at the boundary between the internal network and the external network, centering on firewalls, is no longer able to protect internal systems.
Therefore, "zero trust" is attracting attention, which verifies the safety of all communications without trusting them. At Macnica, we aim to achieve Zero Trust by connecting users and apps and allowing access with minimal privileges, and by continuously monitoring the premise that threats are being infiltrated.

So how can we promote Zero Trust by utilizing Splunk? From here, we will look at the points in promoting Zero Trust, using Taisei Corporation and Sega Sammy Holdings as examples.
Taisei Corporation's Zero Trust Efforts
Until now, Taisei Corporation has implemented security measures based on the premise that company-loaned PCs will not be taken out of the company network or connected. However, in the future, with the aim of improving the work efficiency of employees and on-site workers, it is necessary to safely use company-issued PCs even if they are taken outside the company network.
As a result of examining various security measures, Taisei Corporation came to the conclusion that only the Zero Trust model can meet this security requirement, and is proceeding with the study of SDP (Software Defined Perimeter), which is implemented in principle even in Zero Trust. increase. SDP is a mechanism that enables protection by supporting centralized access control with software. Mr. Yamada of Taisei Corporation talks about the initial consideration as follows.
"As a step in our consideration, we first evaluated what kind of risks remained against threats by undergoing an assessment by Macnica. We identified issues by taking into account our company's unique network requirements, and implemented Zero Trust. We proceeded with verification and selection of security products.As we move forward with micro-segmentation, we are unable to gain acceptance from system administrators by simply "strengthening security," so we also need to improve convenience for users. I was conscious of that.'' (Mr. Yamada)

A major feature of Macnica 's assessment is that it uses a framework called "MITRE ATT&CK" for evaluation. The previously adopted cyber kill chain is a model of an attacker's behavioral process, but MITER ATT&CK is a framework of an attacker's tactics. This will clarify what can and cannot be addressed with current measures.
Mr. Yamada explains the identification of requirements for Zero Trust as follows.
“From about five years ago, Taisei Corporation has been aiming for a world where we can realize a full Internet in-house network, in other words, a network without LANs and WANs, with the aim of improving work efficiency.
We also wanted to solve issues such as micro-segmentation and control the flow of communication with people and devices. Therefore, we proceeded with the verification of products such as SD-WAN and SASE, and had Macnica perform an assessment, and ultimately settled on SDP, which is a zero trust network.
Also, if a threat is detected by NDR (network detection and response) or targeted attack countermeasures, add it to the blacklist of the SDP controller via Splunk and build a mechanism to revoke the token on the client side. (Mr. Yamada).
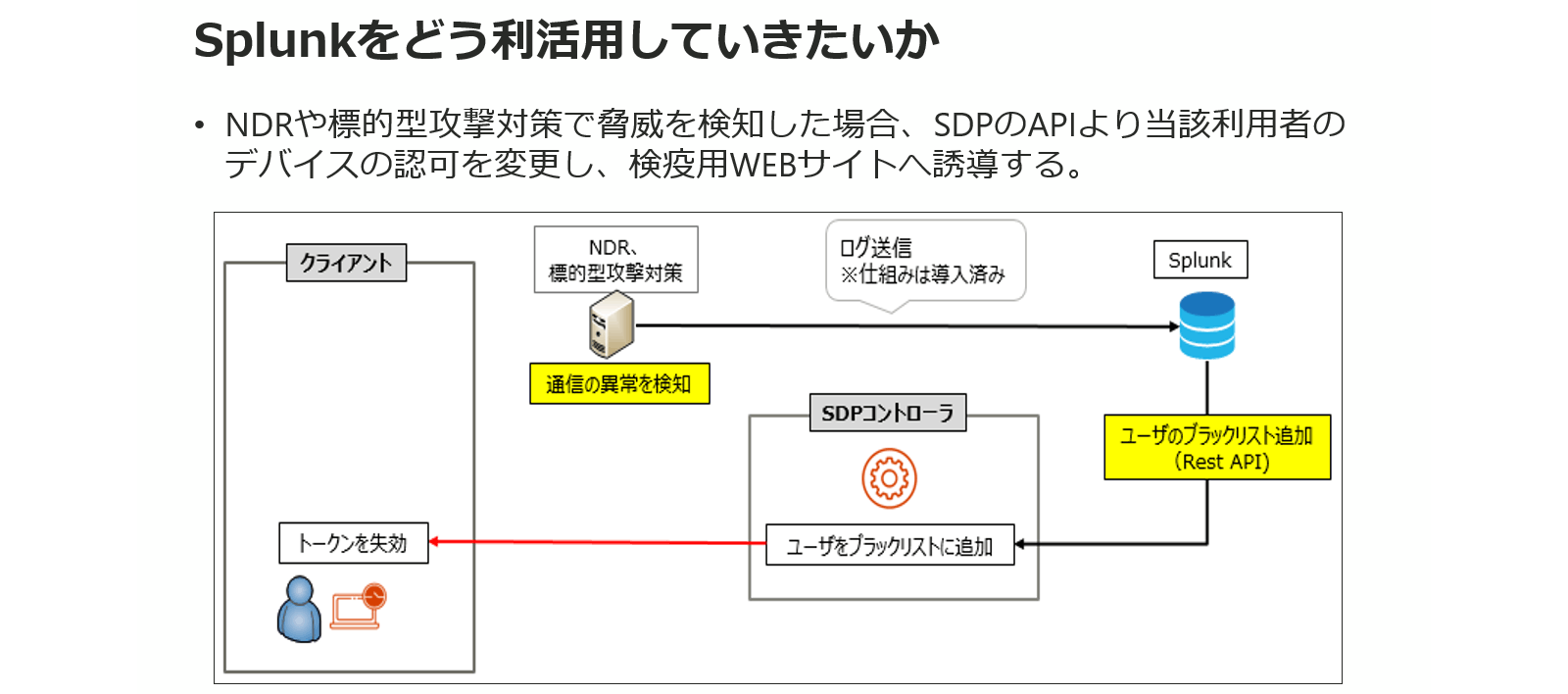
In this way, Taisei Corporation has been promoting zero trust, but it is said that there are many issues.
“We are steadily moving forward with the process of creating operational operations centered on Splunk, but I think the operation after that will be a major issue. So, I plan to create a mechanism for sorting based on the priority of alerts, one by one, and put it into operation.” (Mr. Yamada).
また、大成建設様では内部不正対策にも積極的に取り組んでいます。
“If data is taken out, or if an account is stolen unintentionally, especially if the account is stolen, the data will be accessed in a legitimate way. I'm thinking of adding a score if there is, and raising an alert when it reaches a certain score.
There are cases where the account on the SaaS side is hijacked on the cloud side, but we plan to cover that with operations such as anti-phishing measures. We believe that CASB is also an effective measure for using SaaS with a low level of security." (Mr. Yamada).
Utilization of Splunk at SEGA SAMMY HOLDINGS
SEGA SAMMY HOLDINGS imports logs from CrowdStrike Holdings、Inc. 's EDR product Falcon into Splunk for analysis. Splunk provides an app development tool called Splunkbase, and many vendors publish their apps. By using these, protocol analysis and terminals with high traffic can be easily visualized. Sega Sammy Holdings is using CrowdStrike's dashboard in Splunk.
So, how do you actually operate to link from Splunk to another product? Mr. Sato of Sega Sammy Holdings explains as follows.
"I don't directly hit the API, but the alerts alone don't provide enough information. In many cases, the only information I can get is the host name, user name, and IP address. So, with Splunk, We supplement information such as the terminal and operation, and use it to throw it back to another alert tool.” (Mr. Sato).
With SIEM, it is possible to link with other products using APIs in order to add additional information to alerts, and Macnica also offers a SOAR-based product called Splunk SOAR, allowing us to create a system that can respond to all needs. going.
At SEGA SAMMY HOLDINGS, we are aware of the unavoidable issue of "logs distributed in various places" in future Zero Trust initiatives.
“With SaaS, it takes a lot of time and effort to get the logs you want. For example, even if you set up another indexer in AWS, it is efficient because you can search both on-premises and AWS.
It also helps us analyze user behavior. For example, when dropping large amounts of data from a file server or transferring large amounts of data is a hook. However, since the amount of data handled by the person in charge of development is originally large, it is difficult to judge whether or not it is illegal. In that case, it would be necessary to set conditions such as things that are not usually done, and writing the SPL would be a considerable amount of work, so in such cases, a special tool would be required." (Mr. Sato).
As we consider Zero Trust, the areas that need to be protected will expand. Cloud services are one of them. In that case, sensors will be needed in new areas, creating silos, so it is important to concentrate on something.
For example, there is a way to separate the on-premises Splunk environment and the cloud environment into a single site and create a single-site, multi-indexer cluster, but if the distance increases, network latency issues will arise.
On the other hand, "Splunk 8.2" introduced federated search. This allows you to search Splunk in different environments side by side, and it is designed to meet the above needs.
There are various challenges in aiming for the ideal Splunk utilization for Zero Trust. You will also need to adapt to your environment and policies.
How do we find the optimal solution then? We hope that through sharing information and exchanging opinions in this community, you will be able to find what is best for your company.
Inquiry/Document request
In charge of Macnica Splunk Co., Ltd.
- TEL:045-476-2010
- E-mail:splunk-sales@macnica.co.jp
Weekdays: 9:00-17:00




