
Splunk
スプランク
auカブコム証券のゼロトラストへの取り組みとSplunk活用【Splunk Circle 2021 秋】
コロナ禍への対応でリモートワークが急激に普及したことから、従来の企業ネットワークを中心とした多層防御では脅威を防ぐことが難しくなりました。そこで注目を集めているのが、すべての通信を“信頼しない”ことを前提に、情報資産へアクセスするすべてのトラフィックの安全性を検証する「ゼロトラスト」の考え方によるセキュリティ対策です。auカブコム証券は、Splunkを軸にセキュリティ対策を推進し、ゼロトラストを実現しています。ここでは、auカブコム証券 システム統括役員補佐 石川陽一氏による「Macnica Splunk Circle 2021 秋」の基調講演の模様を紹介します。
auカブコム証券の従来の取り組み
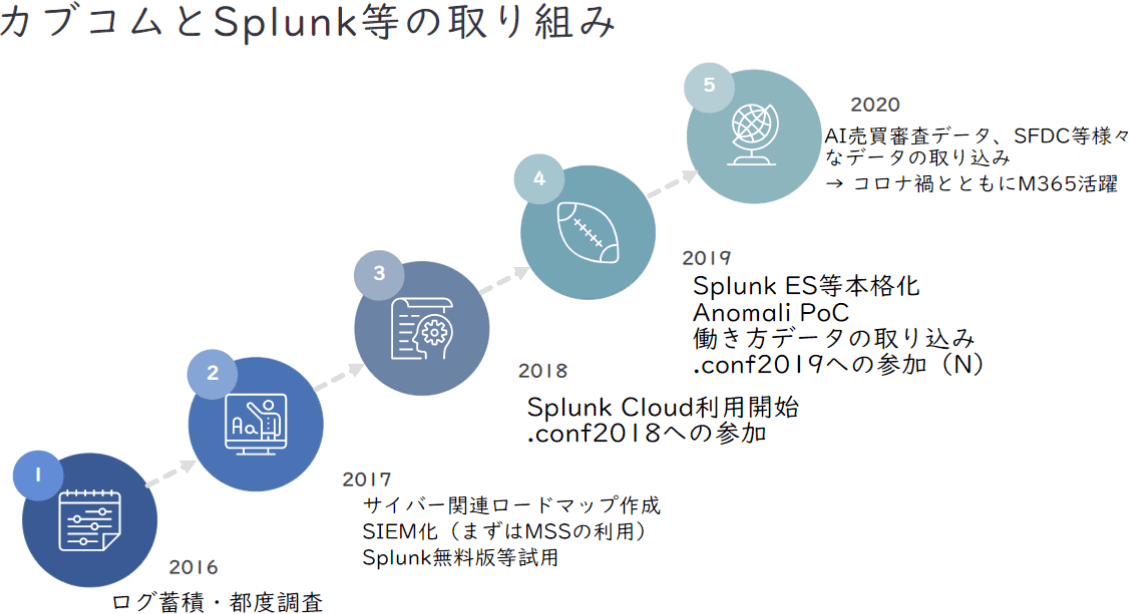
auカブコム証券では、2018年から「Splunk Cloud」の利用を開始し、2019年には「Splunk ES」を導入しています。それ以前はSIEM(セキュリティ情報およびイベント管理)のマネージドサービスを利用しており、当時からSplunkの無料版を試用していました。その後、Splunkの主催イベント「.conf 2018」に参加し、様々な活用事例から導入の効果を確認し、Splunk製品の本格活用に至りました。
また、働き方改革の観点から2018年にテレワーク制度を正式試行。セキュリティ対策としては、支給したiPhoneをMDM(モバイルデバイス管理)で管理し、Microsoft Intuneでアプリ間でのコピーを禁止しています。ただ、同じアプリ内、例えばOutlookの中でもコピーができないという不便さもあったといいます。2019年にはMicrosoft 365とTeamsの利用を開始して、BCPの訓練としてTeamsを活用していました。
Microsoft 365についてはライセンスの種類によって制約が異なりますが、その内容が把握できていなかったため、SIerなどに相談。セキュリティ面の優位性や多様性からE5を選択しました。なお、E5には「Office 365 E5」「Microsoft Enterprise Mobility + Security E5」「Windows 10 Ent. E5」があります。
そして2020年、急なコロナ禍への対応によって状況が大きく変わりました。「急激なテレワーク移行によってVPNの帯域が厳しくなりました。例えばデバイスにEDRが入っているので、Microsoft 365がローカルブレイクアウトでアクセスするなど、アプリケーションごとの経路の調整などに追われました」(石川氏)。
ゼロトラストの「3つのポイント」
auカブコム証券では、テレワーク対応と並行してゼロトラストの推進もコロナ禍で進めました。時間が限られているため、「やりたいこと」「大事なこと」を明確にし、実践していきました。その結果、「ID周りをより良くする」「EDRは高い優先度で進める」「情報の理解・共有等も大事にする」という3点に注力することになりました。
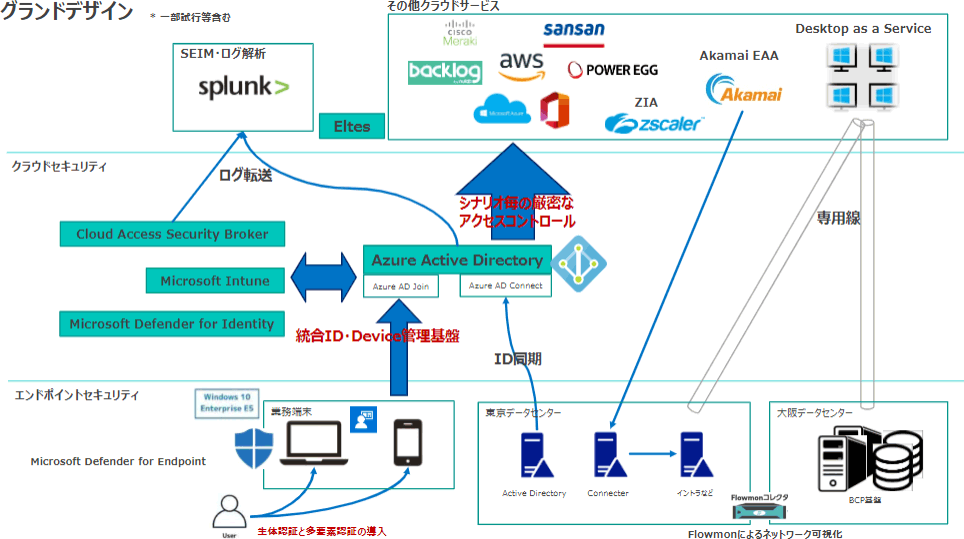
ID周りでは、ゼロトラストの取り組みを機にパスワードレスを目指すことに。多要素認証には「OneLogin」を使っていましたが、これをAzure ADベースに変えていき、Authenticatorを活用し始めています。二要素認証にiPhoneを使うことで、デバイスとIDを同時に確認できる環境を構築。ポータル画面を用意し、一度のログインで様々なアプリケーションをワンクリックで利用できるようにすることで、利便性を高めました。
一方EDRについては、設定の手順を踏んでいけば、リファレンスモニターとしてMicrosoft Security Centerでログを吸い上げ、脅威を検知すると止めることができたり、リスク評価を行ってアウトプットしたり、Azure Sentinelとの連携が可能になったりすることもわかりました。Azure Sentinelがなくても、Microsoft 365のE5ライセンスであれば、セキュリティアラートのキャッチアップや、エンドポイントのログの可視化などが可能になるのです。
また、Azure Secure Scoreという機能を使えば、自社のセキュリティ状況を数値化したスコアとして確認でき、どの部分がスコアを下げているのか、類似の組織がどのくらいの割合で存在するのかを確認することができます。同様にコンプライアンススコアも確認できます。
石川氏は「9つのAzure AD関連の観点を踏まえたゼロトラストの取り組み」を示しました。これは、マイクロソフトの「Azure ADウェビナー」の内容を元に要素を8つ抜き出し、コンプライアンスを加えたものです。ゼロトラストの取り組みを要素ごとにビフォー、アフターで記載しています。要素と内容は次の通りです。
- テナント構成
AD(組織内、パスワード/指紋認証)から、AD同期したAzure AD(組織内外、貸与iPhoneと二要素、リスクベース認証、パスワードレス、顔認証/Windows Hello)へ - デバイス管理
デスクトップPC+リモート用ノートの2台、端末証明書、シンクライアント的利用、マスター複製)から、MDM/Intune、Azure AD Join、Windows Enterprise E5、デバイス保護/WD Device Guard、暗号化/BitLocker、リモートワイプで、ノート一本化へ - アクセスコントロール
VPN接続、Akamai EAAから、条件付きアクセスへ(ユーザー、場所、デバイス、アプリ、リアルタイムリスクチェック) - アプリケーション管理
RDP、OneLogin(SSO、AD連携)から、エンタープライズアプリケーション(SSO)、Apps on Azure ADへ - 外部ユーザー協業
メール等で限定的であったのを、Azure AD B2B、外部も二要素化、Teamsゲストユーザー運用の確立へ - セキュリティ強化
ファイルサーバー部暗号化、USB禁止、SSI社内端末管理、個別端末対策の組み合わせ、Web分離環境、MD for Office 365から、MD for Endpoint(EDR)、端末がSecurity Center連携、Endpoint DLP、セキュリティベースライン、Secure Score、Security Posture、ハイジーン、脅威インテリジェンスへ - ガバナンス
権限ワークフロー、アカウント棚卸し/アカンサスから、権限の付与・はく奪の効率化・自動化、情報保護/ラベル Information Protection&Governanceへ - コンプライアンス
内部脅威検知/エルテスIRI等から、Communication Compliance、Insider Risk Management、CASB/MCAS、DLP、自動暗号化/検出、Zscaler等へ - 監査
ログ定期分析、SIEM(Splunk ES)等から、SIEM(既存+Azure Sentinel試行)、原則ゼロトラストベースへ

ゼロトラストの進め方のポイント
ゼロトラストの実現には見える化が欠かせません。見える化について石川氏は「Power BI」を評価しています。「ログを取得するには、やはりSplunkやAzure SentinelといったSIEM製品がいいのですが、Microsoft 365でもAPIやコネクタでかなりのデータを集めることができ、集めたデータをPower BIにエクスポートすることができます」(石川氏)。
具体的には、「Power BIエクスポート」で出力できるため、集めたデータをPower BIで見える化できます。これはSplunkでも同様で、ログデータをPower BIにエクスポートすることで可視化が実現できるのです。
最後に石川氏は、「ゼロトラスト等に関する進め方のポイント」を示しました。
- やりたいことありきで考える
- 脱サイロ化:担当範囲を少し広げて柔軟に対応する
- 3つのポイント(ID、EDR、共有)を念頭に置く
- 社内外の関係者とコミュニケーションを取る
- 勉強会(社外、社内)、動画、外部資料、SNSを実施する
- セキュリティ&データはSplunk、Microsoft 365系、Power BIを柱にする
「ゼロトラストというと情報がたくさんあって頭が痛くなりますが、ひとつひとつ進めていくことが重要です。また、一人だけで頑張らずに社内外のコミュニケーションを積極的に行って、悩みや解決法を共有していくといいと思います」と石川氏はゼロトラスト推進のポイントを語り講演を締めくくりました。
お問い合わせ・資料請求
株式会社マクニカ Splunk 担当
- TEL:045-476-2010
- E-mail:splunk-sales@macnica.co.jp
平日 9:00~17:00




