product
- Why choose Splunk
- Installation record
- price
- Splunk Enterprise Security
- Splunk Phantom (SOAR)
- Splunk ITSI (Next Generation IT Operations)
- Splunk Observability Cloud
- Splunk UBA
- Macnica CSIRT App Basic
- App for Splunk for Financial Institutions
- Splunk Analytics for Hadoop
- About Apps
- Splunk Edge Hub
- What is Splunk
service
- Dashboard/SPL Creation Pack [Implementation/Building Support]
- Version upgrade service [implementation and construction support]
- Smart Security Monitoring App [Original App/Service]
- Splunk × LANSCOPE Original App [Original App/Service]
- Security Monitoring App for Box [Original App/Service]
- Cloud Security Monitoring App [Original App/Service]
- List of services
Specifications/Technical Information
Application for evaluation machine
- FAQ

Splunk
Splunk
Solving Problems with Splunk - Security
Used by 2,500 companies worldwide for security purposes
Incident detection, analysis, and investigation "Splunk" using log infrastructure
Accurately grasping the situation in a short amount of time is the first step in reducing the damage caused by security threats such as cyberattacks.
The clues are the system and network logs. Since it is nearly impossible to manually analyze the enormous amount of logs that span multiple security devices, this log utilization platform has been introduced by 2,500 companies around the world to quickly and easily detect, analyze, and investigate security incidents.・・・
We will introduce security utilization of machine data analysis platform "Splunk".
Are you having trouble with these security issues?
- Investigation of security incidents takes time
- Cannot be analyzed with existing products
- Unable to collate logs across multiple security devices
- Feeling the limits of human-wave tactics for log analysis
- Research and analysis methods are dependent on the individual

It can be solved by introducing Splunk
Splunk enables you to:
- Centralized management of security events
- Cross-analysis of logs from multiple security devices
- Easy access to logs centralized in Splunk with GUI!
- High-speed extraction of only the information you want to see with the standard functions of search, tabulation, and visualization!
Centralized management of security events
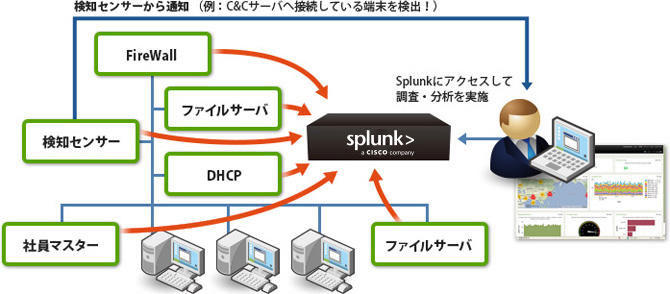
rapid investigation
Incident investigation and management
Analysis scenario
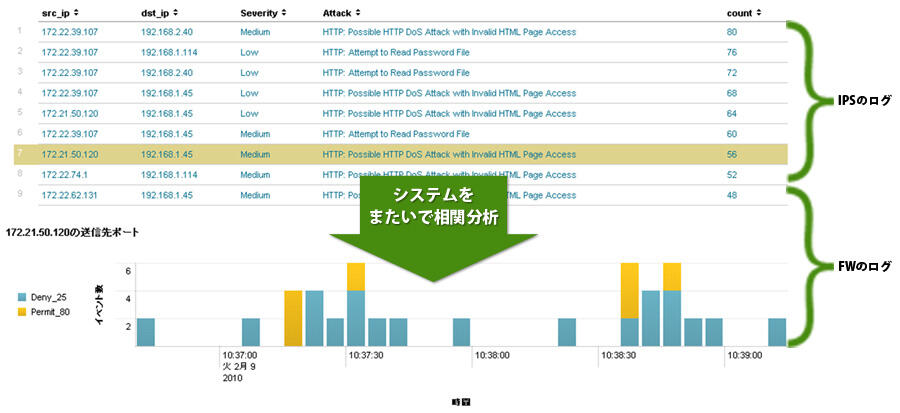
- Aggregates the number of attacks detected by IPS for each source IP address and destination IP address
・Confirm the communication status of Firewall for the specific source IP address "172.21.50.120" in ②. - Communication status of specific source IP address of Firewall Time-series graph
・Display a time-series graph for the source IP address "172.21.50.120" where attacks were detected.
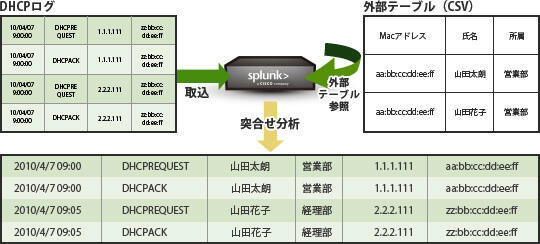
Matching analysis of multiple logs
Example: Analysis of adding employee information to DHCP logs
Even if the information is not recorded in the log, it is possible to add information by referring to the external table and aggregate it.
Dashboard and pinpoint search example
Dashboard for internal controls and PC operation logs
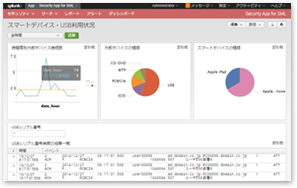
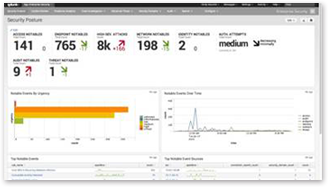
Security health dashboard
Weekdays: 9:00-17:00
Inquiry/Document request
In charge of Macnica Splunk Co., Ltd.
- TEL:045-476-2010
- E-mail:splunk-sales@macnica.co.jp
Weekdays: 9:00-17:00