Products/Services
product
- Why choose Splunk
- Installation record
- price
- Splunk Enterprise Security
- Splunk Phantom (SOAR)
- Splunk ITSI (Next Generation IT Operations)
- Splunk Observability Cloud
- Splunk UBA
- Macnica CSIRT App Basic
- App for Splunk for Financial Institutions
- Splunk Analytics for Hadoop
- About Apps
- Splunk Edge Hub
- What is Splunk
service
- Dashboard/SPL Creation Pack [Implementation/Building Support]
- Version upgrade service [implementation and construction support]
- Smart Security Monitoring App [Original App/Service]
- Splunk × LANSCOPE Original App [Original App/Service]
- Security Monitoring App for Box [Original App/Service]
- Cloud Security Monitoring App [Original App/Service]
- List of services
Specifications/Technical Information
Specifications/Technical Information
Evaluation machine application/FAQ
Application for evaluation machine
- FAQ

Splunk
Splunk

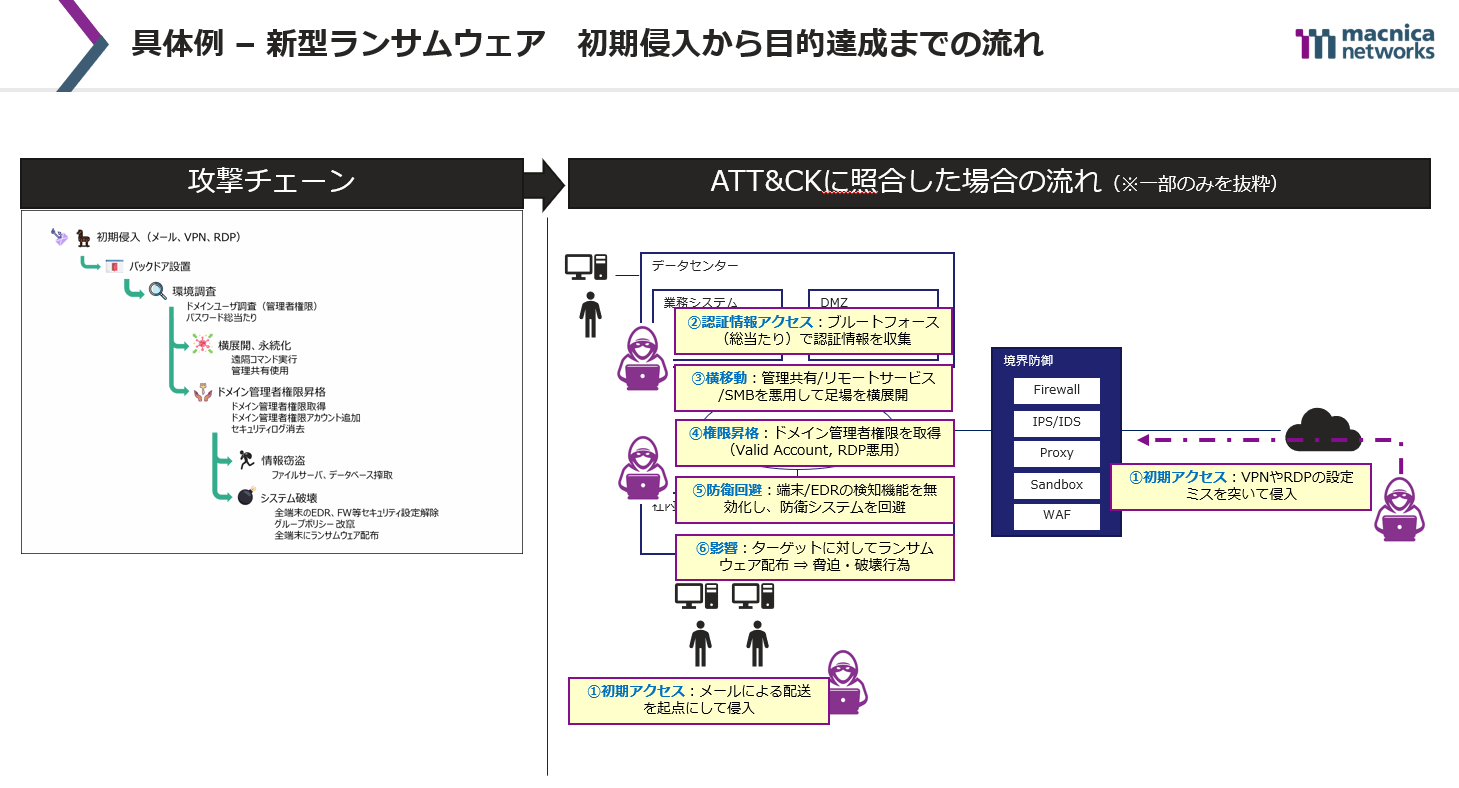
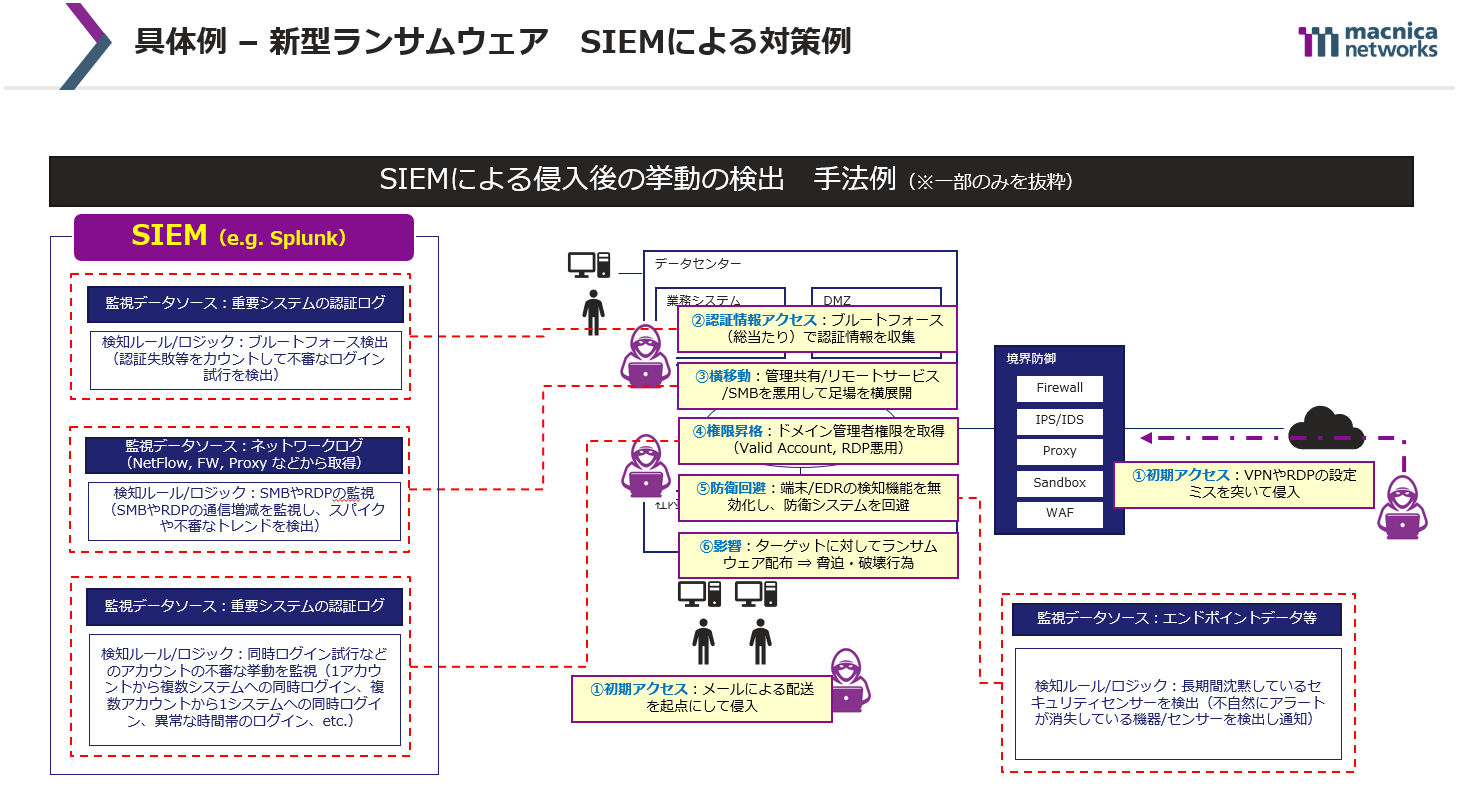
In this video, we focus on three trends: (1) the sophistication and diversification of attackers' methods, (2) new security risks associated with remote work becoming the norm, and (3) new security risks associated with the use of SaaS and IaaS. We will explain each design element with examples of actual incidents and specific examples of detection rule design for the "ideal form of SIEM" to deal with these.
POINT
- Flow of new ransomware attacks and examples of countermeasures using SIEM
- Remote work security risks and examples of SIEM countermeasures
- Cloud security risks (IaaS, SaaS) and examples of countermeasures using SIEM
Example of content
Contact information
Macnica
In charge of Splunk
- TEL:045-476-2010
- E-mail:splunk-sales@macnica.co.jp
045-476-2010
Weekdays: 9:00-17:00
Weekdays: 9:00-17:00
Inquiry/Document request
In charge of Macnica Splunk Co., Ltd.
- TEL:045-476-2010
- E-mail:splunk-sales@macnica.co.jp
Weekdays: 9:00-17:00