product
- Line up
- Network Security: Trellix (formerly FireEye) Network Security
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense
- Network Security: Trellix (formerly McAfee) Network Security Platform
- Endpoint: Trellix (formerly FireEye) HX
- Endpoint: Trellix (formerly McAfee) Mvision
- Data Protection: Trellix Data Security
- Email Security: Trellix (formerly FireEye) Server Edition
- Email Security: Trellix Cloud Edition
- Security Operations: Trellix (formerly FireEye) Helix
- Security Operations: Trellix (formerly McAfee) SIEM (Security Information and Event Management)
- Enhanced cloud governance: Trellix (formerly FireEye) Cloudvisory
- File Security: Trellix (formerly FireEye) Malware File Storage Scanning
- Integrated Management Solution: Trellix (formerly FireEye) Central Management
- NDR Solution: Network Investigator (NI) / Packet Capture (PX)
- Cloud-based File Threat Protection: Trellix IVX Cloud
Specifications/Technical Information
- Trellix (formerly FireEye) Technical Information
- Trellix (formerly FireEye) Specifications
- Network Security: Trellix (formerly FireEye) Network Security Technical Information
- Network Security: Trellix (formerly McAfee) Network Security Platform Technical Information
- Network Security: Trellix (formerly McAfee) Network Security Platform Specifications
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense Technical Information
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense Specification
- Email Security: Trellix (formerly FireEye) Server Edition EX Series Technical Information
- Email Security: Trellix (formerly FireEye) Server Edition EX Series Specifications
- Integrated Management Solution: Trellix (formerly FireEye) Central Management (CM) Series Specifications
- Security Operations: Trellix (formerly McAfee) SIEM (Security Information and Event Management) Technical Information

Trellix
Trellix
Oita University

National University Introduces Next-Generation Box to Counter Targeted Attacks Detects Box Evasion Malware with High Accuracy and Supports Advanced Cyberattacks on Educational Institutions Expected to Expand
Click here for PDF download (581KB/2P)
Points
- Many backdoor communications were discovered by evaluation using a verification machine, and its effectiveness was demonstrated.
- Implemented within budget by reviewing entire network and applying academic package
- The false detection rate and gray judgment are low, and it is easy to separate after detection, so it is possible to operate with a small number of people.
- A comprehensive attack detection system that also supports Mac OS

Oita University
Academic Information Center Deputy Director
(Information Technology Center)
Professor Doctor of Engineering
Kazuyuki Yoshida Mr

Oita University
Academic information base
(Information Technology Center)
Associate Professor Doctor of Science
Koichi Yoshizaki Mr
Surge in cyberattacks on educational institutions boosts Box adoption
The Information Technology Center, the Center for Academic Information of Oita University (hereinafter referred to as "Oita University") is Dannoharu campus In close cooperation with the Medical Information Center on the Masuma Campus, it is an organization that promotes the development, enhancement, and sophistication of academic information as the core organization of the university-wide academic information infrastructure at Oita University. It oversees the university's basic information systems (information systems and information networks) as a center for academic information that promotes education and research, and supports the use of students, faculty and staff in various ways.
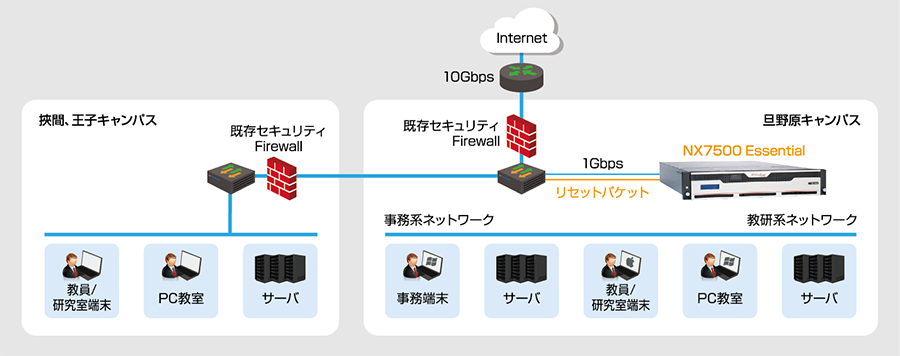
The campus network (on-campus LAN) managed by the Information Technology Center undergoes a large-scale renewal every six years. Among them, the introduction of a state-of-the-art Box was particularly noteworthy this time.
"While the threat of targeted attacks has become a big topic, we have taken measures such as checking attached files and spam countermeasures on the mail server against attacks via email, but when a suspicious program comes in via the web, It was difficult to install a proxy server because the network configuration of the Information Infrastructure Center on the historic Dannohara Campus operates with global addresses distributed throughout the campus.” . Professor Kazuyuki Yoshida, Deputy Director of Oita University's Academic Information Center (Information Technology Center) and Doctor of Engineering, speaks about the situation at that time.
Campus network firewalls include URL filtering functionality that denies access to blacklisted URLs, but detects highly spoofed malicious URLs and web exploits. There was no way to prevent it, and there was a possibility that a virus would invade the terminals on campus, and the only way to prevent it was to check the PC for viruses.
“The main reason why the Information Technology Center considered introducing a Box was the increasing number of unauthorized access to school networks in recent years and the occurrence of information leaks caused by targeted attacks,” says Yoshida. Advanced cyberattacks targeting educational institutions, which are expected to expand in the future, require more advanced security measures. One of the countermeasures was the use of a high-performance Box, which also supported the decision.
Carefully Selecting Multiple Security Vendors Three Reasons for Choosing FireEye
Mr. Yoshida visited the largest ICT exhibition in Japan to be held in Tokyo, and while actively collecting information on various security vendors, he decided on Macnica 's next-generation threat countermeasure solution "FireEye". noticed. He cited the following three advantages of FireEye.
The first is comprehensive detection power. Proprietary virtual execution engine "MVX" (Multi-vector Virtual eXecution engine) multi-analyzes traffic flow instead of file-based analysis, accurately grasps the entire context of cyberattacks, and alerts on false positives. Perform real-time, in-line analysis of suspicious content with minimal effort.
The second is ease of operation. Automatic blocking of unauthorized external communication can greatly reduce the operational load. The third is the introduction results. The overwhelming track record of introduction in the Box market both globally and in Japan has become a great source of peace of mind.
FireEye is also the world's first security vendor to support Apple's Mac OS, identifying advanced persistent attacks (APTs), zero-day attacks, and targeted attacks against Apple's platforms in the same way it does with Microsoft Windows. , also highly evaluated the provision of a function that can block outbound communication of malware. "Although there are many Windows users in the university, the proportion of Mac users is relatively high, especially in the medical department, and Mac OS support was already a necessary requirement." (Mr. Yoshida)
In June 2016, we borrowed a FireEye verification machine from Macnica, placed it within the campus network, and conducted an evaluation using port mirrors for about three weeks. As a result, many attacks that bypassed existing security measures were detected on campus, and backdoor communications were discovered 27 times, proving the effectiveness of FireEye.
Dr. Koichi Yoshizaki, Associate Professor of Information Technology Center, Oita University, who was involved in the verification, said, "FireEye's user interface is so easy that you can operate it intuitively, and you don't even need to refer to the manual. I was able to check the location of the alert and understand what the alert was about.
After the completion of the verification, through the debriefing session in July, it was decided to formulate the requirement specifications for introducing FireEye and add them to the bidding requirements for the network renewal project.
Academic package is applied to achieve introduction within a tight budget
The biggest problem with the introduction of the product was the budget. Initially, the cost of introducing the sand Box was underestimated, so it was difficult to see if it could be left in the required specifications. In addition to reviewing the budget of the entire network to create a certain amount of budget, the FireEye plans to start offering academic packages that are significantly cheaper than the standard license for public and private educational institutions (universities, graduate schools, high schools, and elementary and junior high schools) from November 2016. Since it was applied ahead of schedule, the introduction within the budget was realized.
On the other hand, Mr. Yoshizaki, who regularly exchanges information with administrators of other universities, said that although many universities feel the need for a Box as an effective countermeasure against APT, they cannot raise the budget. It is said that there are many cases where introduction is abandoned. “We should discuss the use of Box more positively as a measure that is directly linked to the risk management of the entire university. If it is difficult to obtain a budget on our own, we will procure the entire network equipment as our university tried this time. I think there is a way to make it possible to introduce it, such as trying it.”
MVX engine detects Box evading malware with high accuracy
The introduction model is "FireEye NX7500 Essential". The new campus network including it started full operation on March 1, 2017. FireEye's coverage is extensive, covering approximately 5,700 students and 1,900 faculty and staff across all campuses. Specifically, when FireEye detects an attack, an alert email is sent to all members of the Information Technology Center. It is a flow of notifying by e-mail and blocking access. Then, the suspected URL is notified to the whole university to prevent the damage from spreading. It is now possible to quickly detect and block callback communications with C&C servers. “Recently, some types of malware have emerged that are sensitive to the Box virtual environment, and there seems to be a problem that malware cannot be detected in general virtual environments because it hides itself. However, FireEye is equipped with MVX, which can detect even malware programmed to evade the Box with high accuracy, so it can detect sophisticated cyberattacks and allow users to use the network with peace of mind. We can,” Yoshida said.
Furthermore, Mr. Yoshizaki added, "In order to securely manage a network in an open environment such as a university, it is necessary not to spend much time on operations. There is little noise, and it clearly marks black and white, so it doesn't take much time to separate after detection.I was attracted to the fact that it is easy to operate even with a small number of managers.
The introduction of FireEye at Oita University should serve as a model for many educational institutions working to strengthen their information security systems in the future.
User Profile
| Oita University | |
|---|---|
| location |
〒870-1192 700 Tannohara, Oita City |
| Introduction time | February 2017 |
| URLs | http://www.oita-u.ac.jp/ |
| Established in October 2003 through the merger of the former Oita University and Oita Medical University. Located in the center of Oita Prefecture, it is the only national university in the prefecture with 5 faculties and 5 graduate schools, a school attached to the Faculty of Education, and a hospital attached to the Faculty of Medicine. Contribute to regional revitalization by functioning as a base of knowledge and advancing regional medical care and welfare. In 2016, the Faculty of Welfare and Health Sciences was established for the first time in 44 years, taking a historic step toward reforming the education and research organization based on the needs of the times and society. | |
*Information at the time of interview.
Inquiry/Document request
In charge of Macnica Trellix Co., Ltd.
- TEL:045-476-2010
Weekdays: 9:00-17:00