製品・サービス
製品
- ラインアップ
- ネットワークセキュリティ:Trellix(旧FireEye)Network Security
- ネットワークセキュリティ:Trellix(旧McAfee)Advanced Threat Defense
- ネットワークセキュリティ:Trellix(旧McAfee)Network Security Platform
- エンドポイント:Trellix(旧FireEye)HX
- エンドポイント:Trellix(旧McAfee)Mvision
- データ保護:Trellix Data Security
- Emailセキュリティ:Trellix(旧FireEye)Server Edition
- Emailセキュリティ:Trellix Cloud Edition
- セキュリティ運用:Trellix(旧FireEye)Helix
- セキュリティ運用:Trellix(旧McAfee)SIEM(Security Information and Event Management)
- クラウドガバナンス強化:Trellix(旧FireEye)Cloudvisory
- ファイルセキュリティ:Trellix(旧FireEye)Malware File Storage Scanning
- 統合管理ソリューション:Trellix(旧FireEye)Central Management
- NDRソリューション:Network Investigator(NI) / Packet Capture(PX)
- クラウド上のファイル脅威対策:Trellix IVX Cloud
仕様・技術情報
仕様・技術情報
- Trellix(旧FireEye)技術情報
- Trellix(旧FireEye)仕様
- ネットワークセキュリティ:Trellix(旧FireEye)Network Security 技術情報
- ネットワークセキュリティ:Trellix(旧McAfee)Network Security Platform 技術情報
- ネットワークセキュリティ:Trellix(旧McAfee)Network Security Platform 仕様
- ネットワークセキュリティ:Trellix(旧McAfee)Advanced Threat Defense技術情報
- ネットワークセキュリティ:Trellix(旧McAfee)Advanced Threat Defense仕様
- Emailセキュリティ:Trellix(旧FireEye)Server Edition EXシリーズ 技術情報
- Emailセキュリティ:Trellix(旧FireEye)Server Edition EXシリーズ 仕様
- 統合管理ソリューション:Trellix(旧FireEye)Central Management(CM)シリーズ 仕様
- セキュリティ運用:Trellix(旧McAfee)SIEM(Security Information and Event Management)技術情報
ソリューション
ソリューション

Trellix
トレリックス
エンドポイントでのインシデント検知・解析・解決 「Trellix(旧FireEye)HX」

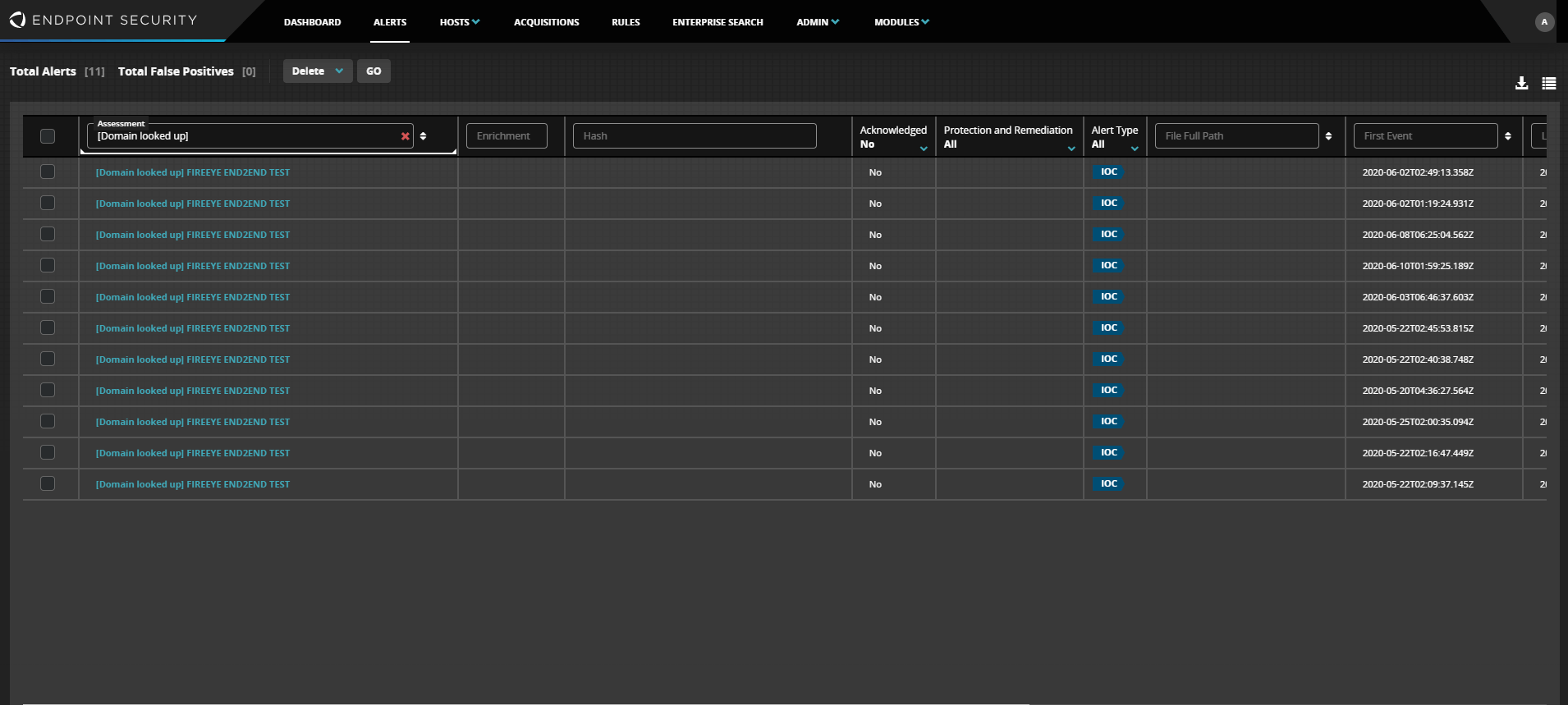
Endpointは、エンドポイントで発生したインシデントを検知・解析・解決するエンドポイントセキュリティ製品です。Network Security/Server Emailの検知情報や、Mandiant(マンディアント)のインテリジェンス情報を元に、感染端末を特定し、隔離することが可能です。同時に他のエンドポイントの感染状況の確認も可能です。
感染端末、影響範囲の特定
- Network Security/Server Emailの検知情報を元に、感染端末を特定。同時に同じ脅威を持つ端末も特定
- Mandiantのインテリジェンス情報を使った潜在的な感染端末の検出
- 3rdパーティ、独自IOC情報を使った潜在的な感染端末の検出
感染状況の確認、調査、隔離
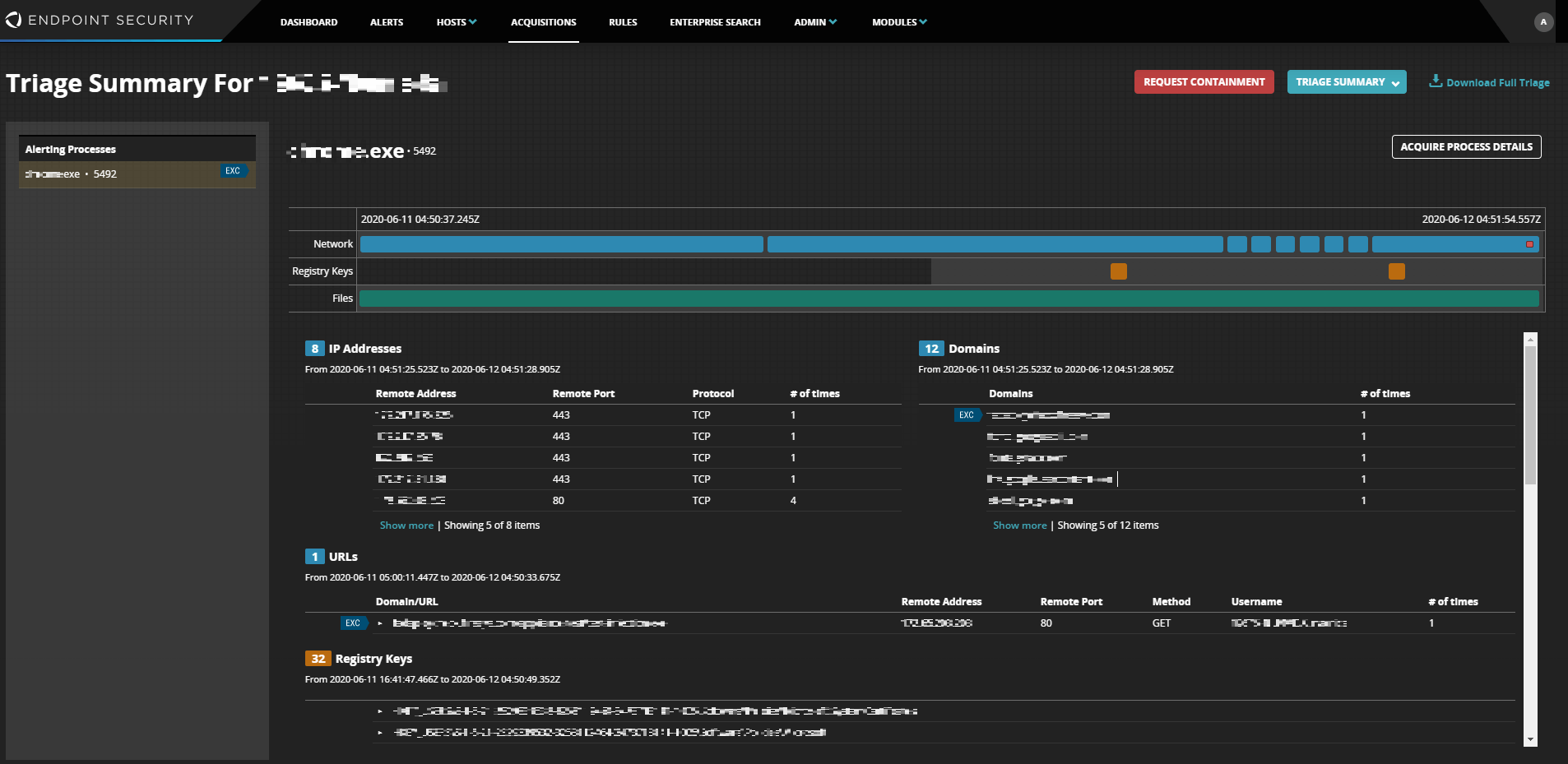
- 実端末にマルウェアが送り込まれたのか、感染したのか脅威進度をステータス表示
- 端末エージェント側でプロセス起動、通信履歴、ファイルの作成、変更、削除などのアクティビティ履歴を自動的に収集。イベント発生時刻に遡って調査可能
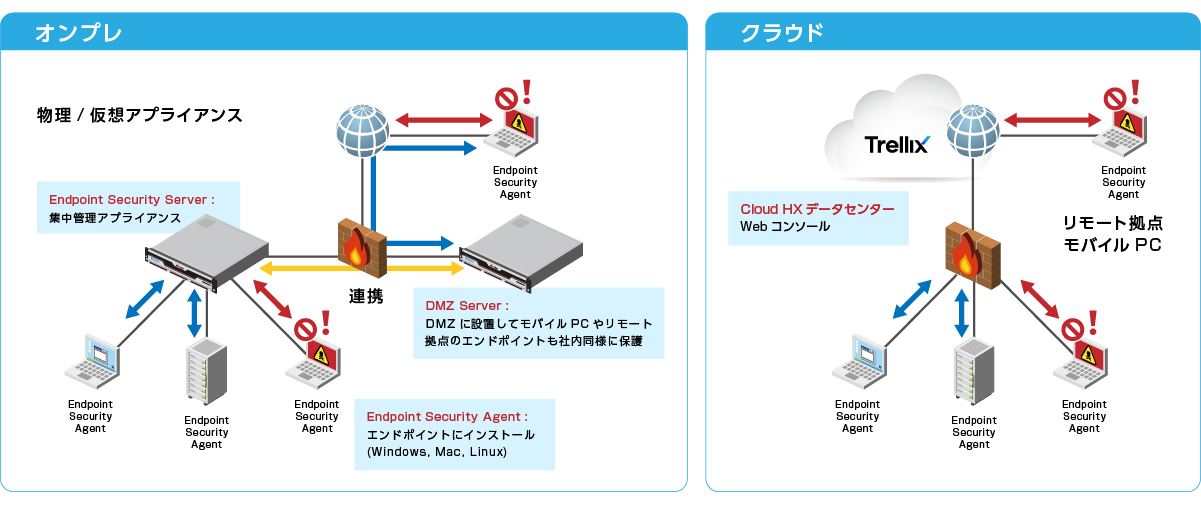
どこにいても検知、調査、隔離が可能
オンプレ、クラウド2つのご利用形態を提供。どちらにおいても、社内だけでなく、外出先、リモートワーク端末についても検知・調査・隔離が可能
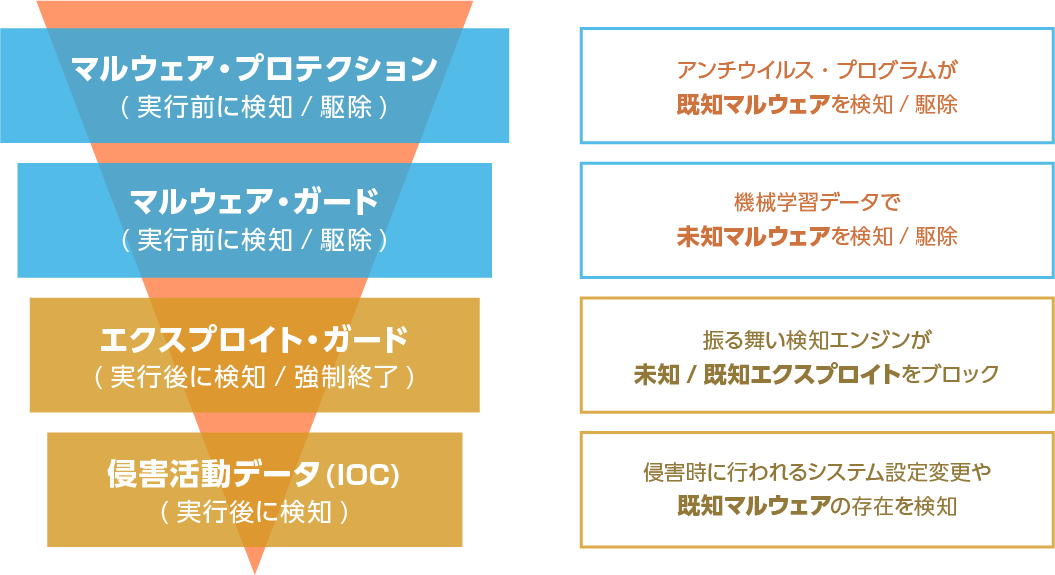
未知のマルウェア、エクスプロイトの検知/ブロック
マルウェア・プロテクション、マルウェア・ガード、エクスプロイト・ガード、IOCという4つの異なるエンジンがエンドポイントを多重防御します。
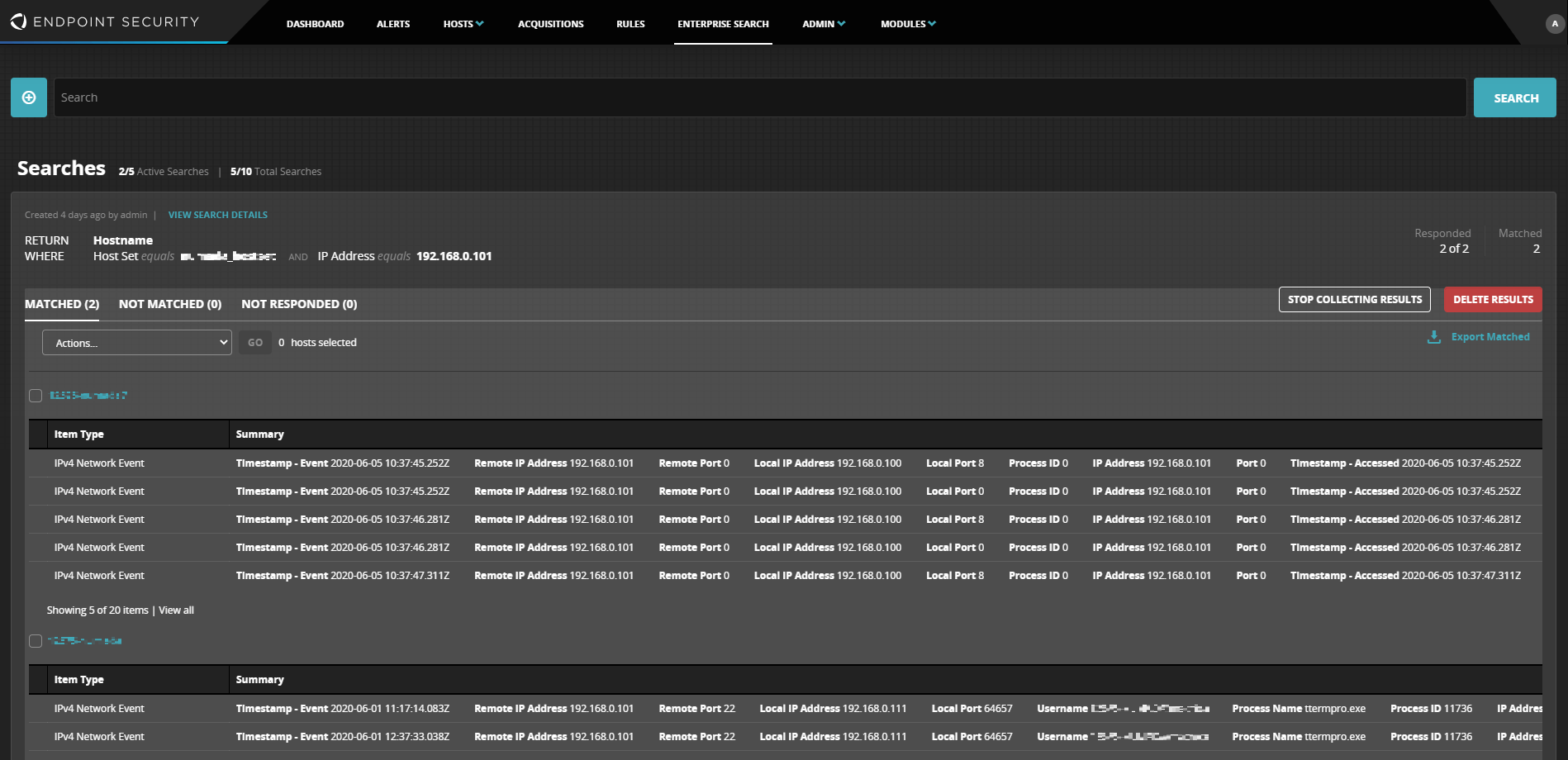
管理者端末の稼働状況や被害拡散状況を検索
- 外部より入手したマルウェアファイル名、ハッシュ値のプロセス稼働の有無を調査
- マルウェアや攻撃者の悪意ある行為をプロアクティブに検索
- 全ての端末を対象とした被害の拡散状況の分析と追跡
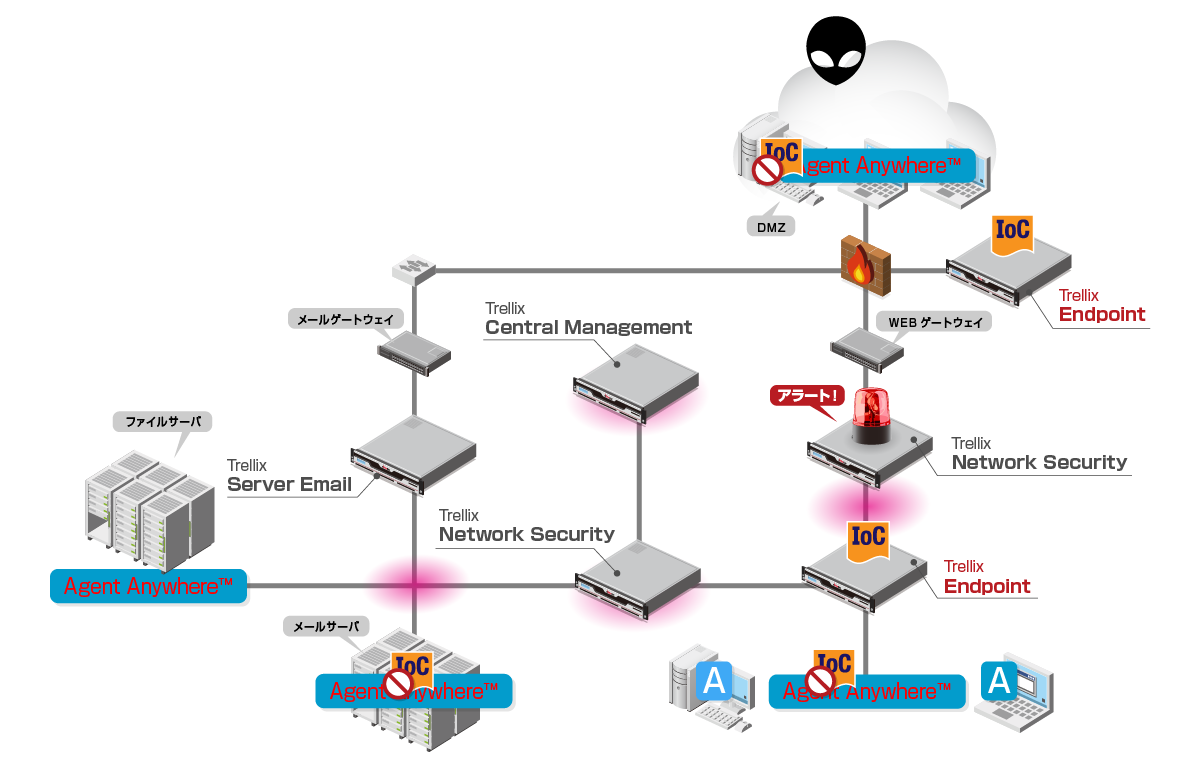
動作イメージ
- エージェントは常時端末上での動作・変更履歴を記録
- 各機器(Network Security/Server Email)からのアラートをEndpointに送信
- Endpointで各機器からのアラートを受信
- EndpointでIndicators(IOC)を自動生成
- IOCを全端末へ配信し、痕跡の有無を端末側(エージェント)で調査
- 感染端末を特定し、さらに調査をすすめる調査ファイル(Triage Package)を生成・取得
- Endpointから感染端末をネットワーク的な隔離を実行
IOCの種類

IOC (Indicator of Compromise)とは
- Mandiant社が提唱した、マルウェアなどに感染した端末上に、その存在や脅威の存在を示す痕跡を捜索・検知するための「定義」「規格」
- IOCを生成出来る情報
- ファイル名/フォルダパス
- ファイル/フォルダパス
- ファイルMD5ハッシュ
- 起動プロセス
- レジストリ
- DNS
- 外部通信ポート など