product
- Line up
- Network Security: Trellix (formerly FireEye) Network Security
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense
- Network Security: Trellix (formerly McAfee) Network Security Platform
- Endpoint: Trellix (formerly FireEye) HX
- Endpoint: Trellix (formerly McAfee) Mvision
- Data Protection: Trellix Data Security
- Email Security: Trellix (formerly FireEye) Server Edition
- Email Security: Trellix Cloud Edition
- Security Operations: Trellix (formerly FireEye) Helix
- Security Operations: Trellix (formerly McAfee) SIEM (Security Information and Event Management)
- Enhanced cloud governance: Trellix (formerly FireEye) Cloudvisory
- File Security: Trellix (formerly FireEye) Malware File Storage Scanning
- Integrated Management Solution: Trellix (formerly FireEye) Central Management
- NDR Solution: Network Investigator (NI) / Packet Capture (PX)
- Cloud-based File Threat Protection: Trellix IVX Cloud
Specifications/Technical Information
- Trellix (formerly FireEye) Technical Information
- Trellix (formerly FireEye) Specifications
- Network Security: Trellix (formerly FireEye) Network Security Technical Information
- Network Security: Trellix (formerly McAfee) Network Security Platform Technical Information
- Network Security: Trellix (formerly McAfee) Network Security Platform Specifications
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense Technical Information
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense Specification
- Email Security: Trellix (formerly FireEye) Server Edition EX Series Technical Information
- Email Security: Trellix (formerly FireEye) Server Edition EX Series Specifications
- Integrated Management Solution: Trellix (formerly FireEye) Central Management (CM) Series Specifications
- Security Operations: Trellix (formerly McAfee) SIEM (Security Information and Event Management) Technical Information

Trellix
Trellix
Network Investigator (NI) and Packet Capture (PX) are NDR solutions that visualize hidden threats through deep analysis.
What is NDR (Network Detection and Response)?
Solutions for monitoring communications (Network) and detecting and responding to threats.
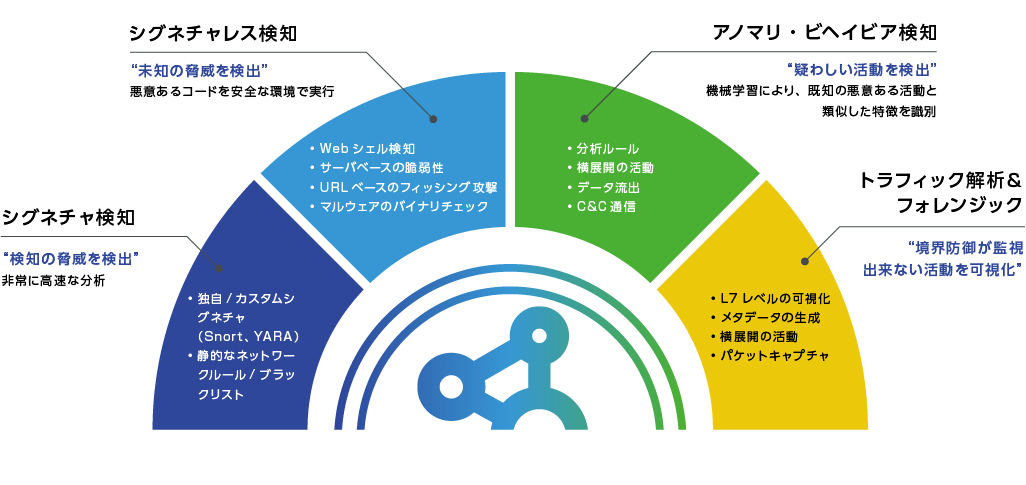
Detection technology required for NDR
What are the benefits of introducing NDR?
Recent attack methods are designed to go unnoticed by using standard commands such as webshells.
It also continues to compromise other hosts as it moves through the network, ensuring the persistence of the attack over time.
As a result, it is difficult to see threats and it is difficult to investigate how many hosts have been compromised.
Compared to EDR (Endpoint Detection and Response), which is good at dealing with infected hosts, NDR is better at detecting and dealing with the horizontal spread/expansion phase to other hosts.
By introducing NDR, it becomes possible to "further visualize threats," "countermeasure internal fraud," and "accelerate investigation and analysis," making invisible threats on the network visible.

What is Trellix's NDR?
Trellix's NDR can be achieved by implementing the following two products.
- Network Investigator (NI): A product that visualizes infringing activities from linked Sensor data.
- Packet Capture (PX): A product that allows you to store and download mirrored packets.
*Both NI and PX are compatible with on-premises/cloud (ex. Azure)
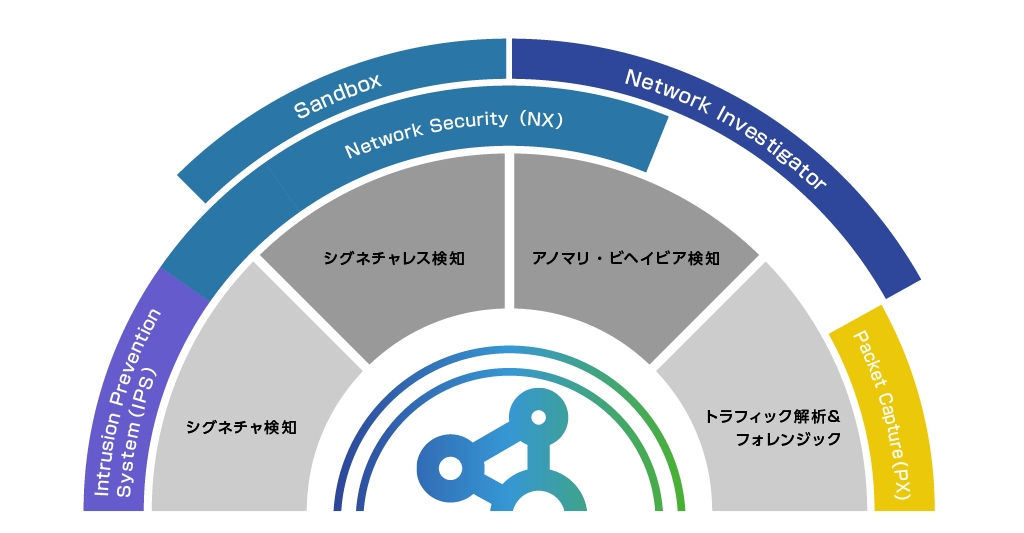
What are the features of NI/PX?
NI
- Application-level fast search
Recognizes diverse protocols for application-level search and analysis - Rebuild content
Rebuild suspicious emails, web communications, and files with one click (*PX required)
PX
- fast capture
Store traffic as an audit trail for a long period of time - fast search
Search packet data over a long period of time and trace back to before the incident occurred - Session analysis
Identify sessions associated with suspicious communications and quickly obtain critical information such as how many hosts are also compromised
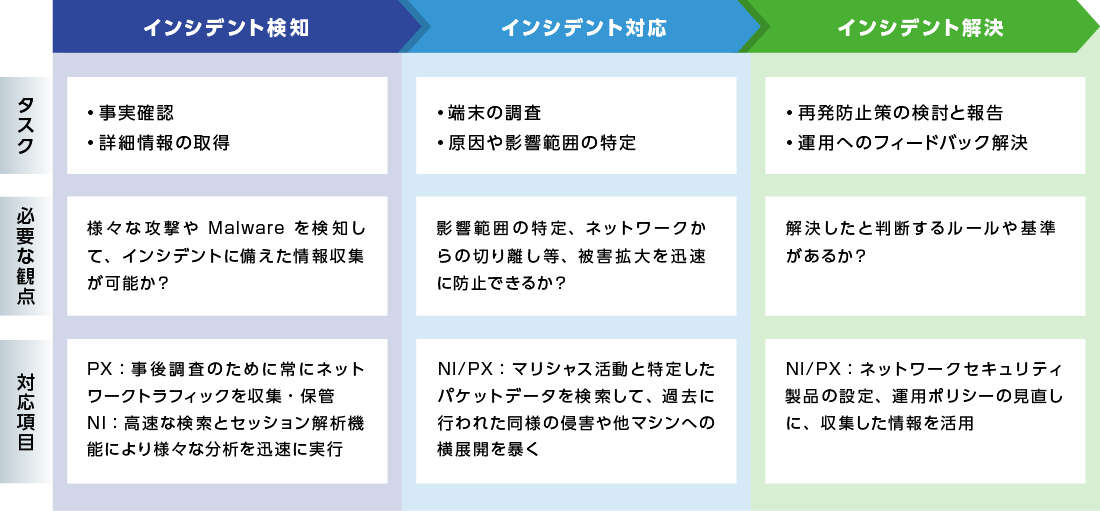
What can NI/PX do when an incident occurs?
Inquiry/Document request
In charge of Macnica Trellix Co., Ltd.
- TEL:045-476-2010
Weekdays: 9:00-17:00

