product
- Line up
- Network Security: Trellix (formerly FireEye) Network Security
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense
- Network Security: Trellix (formerly McAfee) Network Security Platform
- Endpoint: Trellix (formerly FireEye) HX
- Endpoint: Trellix (formerly McAfee) Mvision
- Data Protection: Trellix Data Security
- Email Security: Trellix (formerly FireEye) Server Edition
- Email Security: Trellix Cloud Edition
- Security Operations: Trellix (formerly FireEye) Helix
- Security Operations: Trellix (formerly McAfee) SIEM (Security Information and Event Management)
- Enhanced cloud governance: Trellix (formerly FireEye) Cloudvisory
- File Security: Trellix (formerly FireEye) Malware File Storage Scanning
- Integrated Management Solution: Trellix (formerly FireEye) Central Management
- NDR Solution: Network Investigator (NI) / Packet Capture (PX)
- Cloud-based File Threat Protection: Trellix IVX Cloud
Specifications/Technical Information
- Trellix (formerly FireEye) Technical Information
- Trellix (formerly FireEye) Specifications
- Network Security: Trellix (formerly FireEye) Network Security Technical Information
- Network Security: Trellix (formerly McAfee) Network Security Platform Technical Information
- Network Security: Trellix (formerly McAfee) Network Security Platform Specifications
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense Technical Information
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense Specification
- Email Security: Trellix (formerly FireEye) Server Edition EX Series Technical Information
- Email Security: Trellix (formerly FireEye) Server Edition EX Series Specifications
- Integrated Management Solution: Trellix (formerly FireEye) Central Management (CM) Series Specifications
- Security Operations: Trellix (formerly McAfee) SIEM (Security Information and Event Management) Technical Information

Trellix
Trellix
Network Security: Trellix (formerly FireEye) Network Security Technical Information
We will explain in detail how the NX series detects targeted attacks.
Virtual execution engine MVX
MVX is a patented technology from Trellix (formerly FireEye), a virtual execution engine that can detect advanced malware in real time. While capturing monitored communication packets, it is possible to dynamically analyze suspicious (suspicious) web contents and email attachments that trigger zero-day and targeted attacks using multiple virtual machines/network environments. is.
See product information for an overview
Monitor HTTP communication from mirrored packets using switch span ports. At this point, all suspicious communications that could serve as "attack triggers," such as Java Script that obfuscates web content and downloads of executable files, were detected, including those in the gray zone that would be difficult to determine using signature-based technology alone. increase.
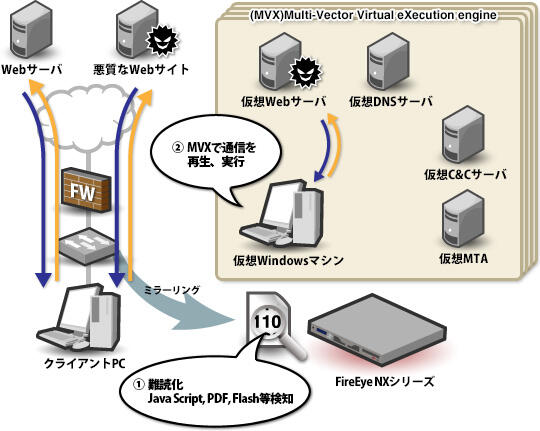
The detected communication is executed in the MVX virtual environment based on the packet capture actually performed between the client PC and the web server on the Internet. (Fig. 3) In addition to the Windows OS, browsers such as IE and FireFox, plug-ins such as Java and Adobe, and Office software such as Word and Excel are installed on the virtual Windows machine in the virtual environment. Attacks with sexuality can be reproduced.
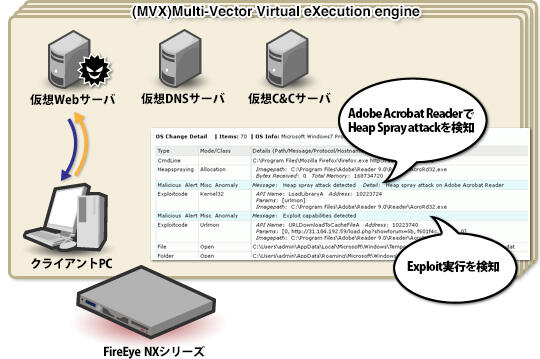
As a result of reproducing communication within the MVX virtual environment, all changes that occur within the virtual machine (file open/close, creation/change/delete, registry changes, malware infection history such as called APIs and addresses) are It is recorded and it becomes possible to identify malware from its behavior. This information can be viewed from the management GUI, and you can even see why Trellix (formerly FireEye) has determined it to be malware.
In addition, MVX is not a Box where only a virtual machine operates alone, and communication behavior with external servers including C&C servers performed by malware can be executed only in a closed network environment within the virtual environment. (Fig. 4) As a result, callback information such as which site (URL information) the malware accesses and what information it sends when accessing (headers and parameters of User Agent, etc.) can be sent on the actual network. It can be collected regardless of whether or not it occurs in In addition to HTTP, it also supports protocols such as SSL, FTP, and IRC.
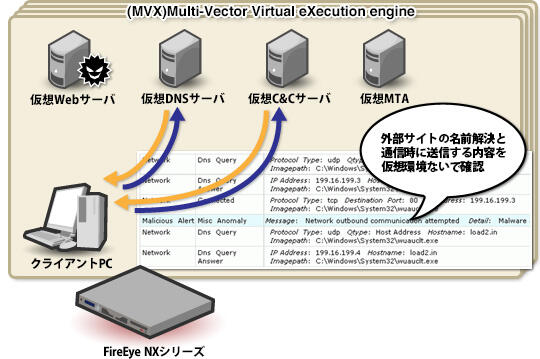
In this way, MVX provides an environment for dynamic malware analysis, and can collect malware identification and callback information independently, signature-less, and in real time.
The NX series can run multiple MVX virtual environments simultaneously, and is devised to increase the overall analysis processing speed by repeating dynamic analysis of suspicious communications and refresh of the virtual environment in parallel processing. increase. The number of virtual environments that perform parallel processing differs depending on the device model. (Same for EX series)
Advanced filters & real-time information sharing (MPC)
Callback Filter is a filter that detects and prevents external communications that malware attempts to provide information to C&C servers and cyberattackers' servers, and automatically investigates external sites based on information collected from malware detected by MVX. Automatically learns unknown attacks as known attacks and automatically generates signatures. (Fig.5)
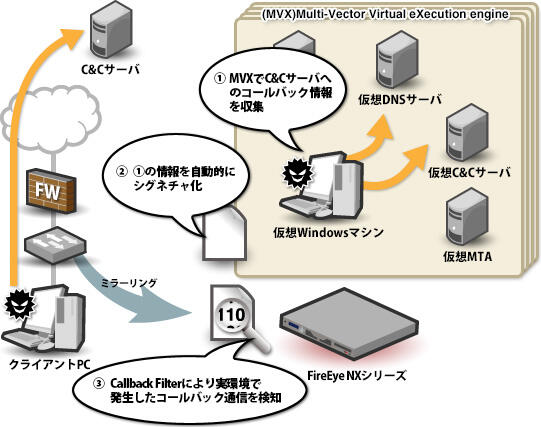
In addition, communication packets detected by Callback Filter are captured and can be checked and downloaded from the management GUI. By looking at the sent content and the response from the server, you can also check whether the communication has been established.
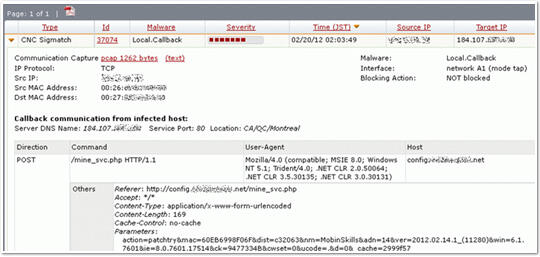
On the other hand, by subscribing to Trellix (formerly FireEye) MPC (Malware Protection Cloud), malware and callbacks provided by Trellix (formerly FireEye), technology partners, and Trellix (formerly FireEye) users operating around the world You will be able to receive information supply.
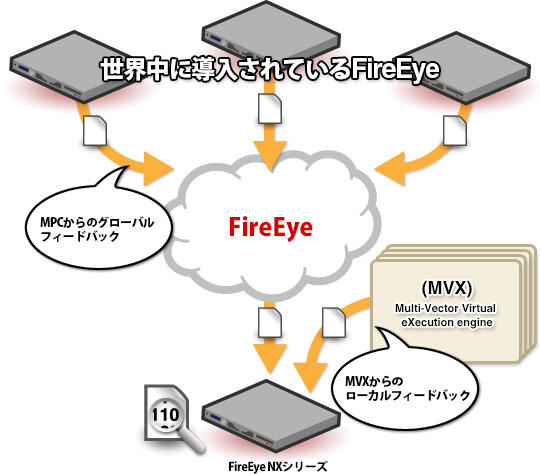
In this way, Trellix (formerly FireEye) MPSs installed around the world act as terminals that collect, analyze, and generate signatures for unknown attacks and malware, while MPCs detect zero-day attacks and targeted attacks using malware. Learn/share as information. The content provided to MPC in global feedback does not include information that identifies the user, such as the user's host name or IP address information.
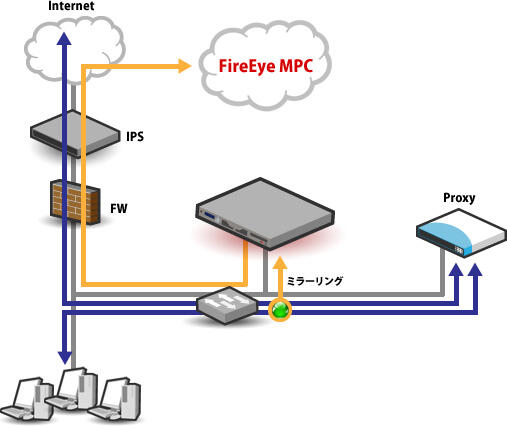
NX series configuration example
Inquiry/Document request
In charge of Macnica Trellix Co., Ltd.
- TEL:045-476-2010
Weekdays: 9:00-17:00

