In recent years, cyber threats such as targeted attacks have become more sophisticated, increasing the burden on security operations.
The shortage of security engineers and IT personnel and the lack of skills have become serious, both physically and mentally.
The current situation is approaching the limit.
As a solution to this problem, we will improve operations by utilizing threat intelligence and
Automation of operation by
SOAR is attracting attention.
 of
of teeth,
teeth,
Trellix (formerly FireEye) Proprietary Threat Intelligence,
cloud service monitoring,
automation technology to comprehensively solve multiple issues faced by security operators with a single solution.
Free to join! Individual consultation
Individual consultationSecurity operation automation
(Next-generation SIEM/SOAR)
- I've heard about "next-generation SIEM/SOAR" several times,
I do not have a concrete image of how to use it in my company - I want to hear a detailed explanation in a discussion format while asking questions
- I would like to see a live demo
- I want to simulate how it works in my environment
- I want to know the fee structure
Our sales and SE will answer your concerns and questions that are not posted on the web, such as
I will answer frankly! Please take advantage of this opportunity.
ONLINE schedule:
According to your company's request (15 minutes to 1 hour)
white paper
Security operations that should be promoted in the future based on the “four keywords”
Transforming security operations
-
Shortage of security personnel
Operational automation
Automate initial investigations and simple daily tasks, and invest in tasks that should be performed by humans
-
Uncertainty about dealing with increasingly sophisticated attacks
Harnessing Threat Intelligence
Leverage attacker information to implement effective responses to triggered alerts
-
セキュリティ運用に工数がかかる
cross-system
Operation monitoringCreate a system to comprehensively monitor the attack cycle
-
Unable to keep up with diversifying work styles
of the cloud environment
Operation monitoringBuild a monitoring system for IasS and SaaS that could not be monitored until now
"Trellix (former FireEye) Helix" supports countermeasures with three functions
Security operations to be implemented and functions provided by Helix
Cross-system operation monitoring
It constantly monitors the system comprehensively from initial intrusion, lateral expansion, and purpose execution, and finds unauthorized communication and suspicious behavior.
Harnessing Threat Intelligence
Efficient incident response using attacker information associated with alerts
Operation monitoring of cloud environment
Constantly monitors IasS and SaaS to detect unauthorized logins and usage
Operational automation
Triggered by an alert, it quickly implements an initial investigation and response in accordance with pre-determined rules.
 システムの横断的な運用監視
システムの横断的な運用監視
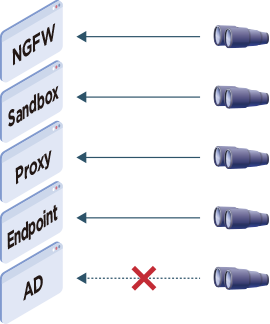
- Monitor each product individually
- When an incident occurs, we investigate each product individually, and it takes time to find correlations
- You have unmonitored systems
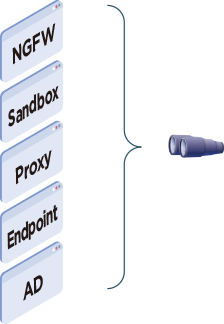
- cross-monitoring of the entire system
- A single system can be used to investigate the context of an alert when an incident occurs.
- Include critical systems that were previously unmonitored
 脅威インテリジェンスの活用
脅威インテリジェンスの活用
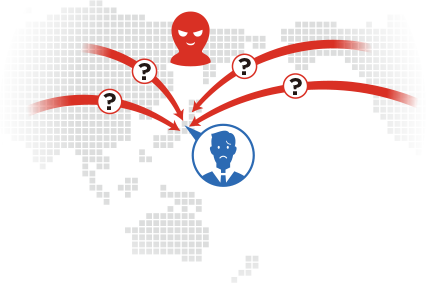
- I don't know what the detected alert means
- Not sure how to respond to alerts
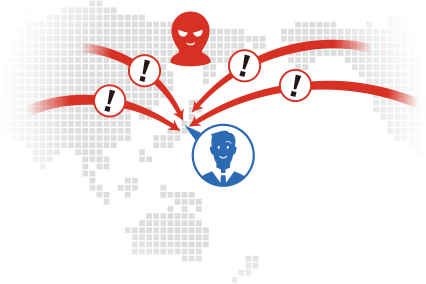
- Know the attacker information associated with the alert
- Discover threats that slip through other products
- Can determine next actions for triggered alerts
Threat Intelligence- Threat Intelligence from Trellix (formerly FireEye) -
| attacker intelligence |
machine intelligence |
victim intelligence |
|
|---|---|---|---|
| phase | before attack | under attack | After attack |
| Collected information |
|
|
|
| Achievement |
|
|
|
| Usage | Preparing for future threats | Detect and prevent threats | Take action against threats optimization |
 クラウド環境の運用監視
クラウド環境の運用監視
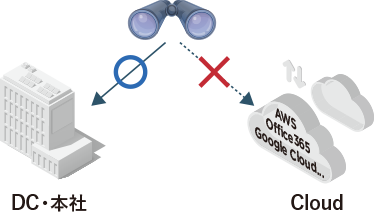
- I don't know the location of my login terminal
- It is difficult to manage login errors, etc.
- I don't know what activity on the cloud is suspicious
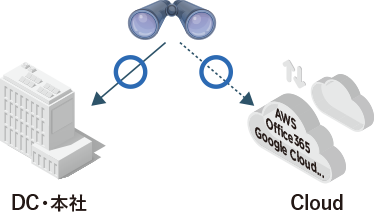
- Regular monitoring by importing cloud logs and creating a dashboard of login status
- Detect cloud-specific threats with built-in and custom rules
 運用の自動化
運用の自動化
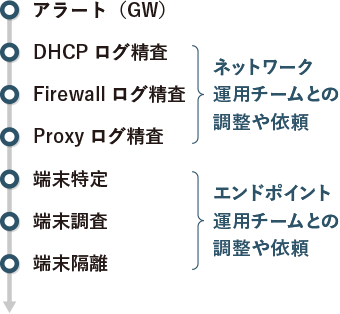
- The investigation process is multi-step and time-consuming
- Coordination destinations are diverse and time consuming

- Leave the initial response/survey to the machine
- Reduce incident response time
- Promote other work in the reduced time
Automation- Playbook (automation workflow) -
① Trellix (former FireEye) NX alert capture
Action according to alert priority
- ・High: Emergency response
- ・~Middle:exit
-
②Case creation
ASSIGN USER
147N16H -
③ Case name and priority
settingUPDATE CASE 3 ATTRIBUTES
17QQNAN -
④ Trellix (former FireEye) Extract HX name and AgentID
CUSTOM SCR… AGENT ID
1CGOQ6I
EXTRACTION -
⑤ Trellix (formerly FireEye) HX terminal isolation
CONTAIN HOST
01VSVRK
-
⑥ From alert
Fraudulent URL extractionCUSTOM SCR… URL EXTRACTION
0IOSRAZ -
⑦ Proxy SG Black
list registrationBLOCK DESTINATION
1O1XPUG
⑧ Close the case
UPDATE CASE STATUS
0EW2KO0Free to join! Individual consultation
Individual consultationSecurity operation automation
(Next-generation SIEM/SOAR)
- I've heard about "next-generation SIEM/SOAR" several times,
I do not have a concrete image of how to use it in my company - I want to hear a detailed explanation in a discussion format while asking questions
- I would like to see a live demo
- I want to simulate how it works in my environment
- I want to know the fee structure
Our sales and SE will answer your concerns and questions that are not posted on the web, such as
I will answer frankly! Please take advantage of this opportunity.
ONLINE schedule:
According to your company's request (15 minutes to 1 hour)
white paper
Overall picture of “Helix” operation
-
Collecting a wide variety of logs
- Trellix (formerly FireEye) Network Security (Box)
- Trellix (formerly FireEye) Endpoint (EDR)
- 3rd party
- Cloud
-

Cross-system monitoring
- Constant monitoring of entrances and exits, internal systems, and rule detection
-
Address threats in all attack phases
Cloud environment monitoring
- Constant monitoring and rule detection of IaaS and SaaS in a few steps
-
Easily protect your cloud environment
threat intelligence
- Correlate threat intelligence to alerts
-
Get hints for future security enhancementsClear next action
-
Operational automation
-
Device isolation
terminal -
Blacklist registration
Firewall Proxy -
Notify operator
operator
-