製品・サービス
製品
- ラインアップ
- ネットワークセキュリティ:Trellix(旧FireEye)Network Security
- ネットワークセキュリティ:Trellix(旧McAfee)Advanced Threat Defense
- ネットワークセキュリティ:Trellix(旧McAfee)Network Security Platform
- エンドポイント:Trellix(旧FireEye)HX
- エンドポイント:Trellix(旧McAfee)Mvision
- データ保護:Trellix Data Security
- Emailセキュリティ:Trellix(旧FireEye)Server Edition
- Emailセキュリティ:Trellix Cloud Edition
- セキュリティ運用:Trellix(旧FireEye)Helix
- セキュリティ運用:Trellix(旧McAfee)SIEM(Security Information and Event Management)
- クラウドガバナンス強化:Trellix(旧FireEye)Cloudvisory
- ファイルセキュリティ:Trellix(旧FireEye)Malware File Storage Scanning
- 統合管理ソリューション:Trellix(旧FireEye)Central Management
- NDRソリューション:Network Investigator(NI) / Packet Capture(PX)
- クラウド上のファイル脅威対策:Trellix IVX Cloud
仕様・技術情報
仕様・技術情報
- Trellix(旧FireEye)技術情報
- Trellix(旧FireEye)仕様
- ネットワークセキュリティ:Trellix(旧FireEye)Network Security 技術情報
- ネットワークセキュリティ:Trellix(旧McAfee)Network Security Platform 技術情報
- ネットワークセキュリティ:Trellix(旧McAfee)Network Security Platform 仕様
- ネットワークセキュリティ:Trellix(旧McAfee)Advanced Threat Defense技術情報
- ネットワークセキュリティ:Trellix(旧McAfee)Advanced Threat Defense仕様
- Emailセキュリティ:Trellix(旧FireEye)Server Edition EXシリーズ 技術情報
- Emailセキュリティ:Trellix(旧FireEye)Server Edition EXシリーズ 仕様
- 統合管理ソリューション:Trellix(旧FireEye)Central Management(CM)シリーズ 仕様
- セキュリティ運用:Trellix(旧McAfee)SIEM(Security Information and Event Management)技術情報
ソリューション
ソリューション

Trellix
トレリックス
クラウド型 高検知力のメールセキュリティ製品「Trellix Email Security Cloud Edition」
Trellix Email Security - Cloud Editionは、標的型メールを受信した時点でアラートをあげ、管理者にいち早く通知します。クラウド内のIVXを使うことにより、シグネチャにはない未知の脅威を発見します。さらに、Network Securityと連携することにより、ユーザが不正なURLへアクセスしてしまう事態に備えます。
メールセキュリティ

Microsoft365導入企業必見!今実施すべきクラウドメールセキュリティとは
ホワイトペーパー①

Trellix(旧FireEye) Email Security で実現するメールセキュリティ対策
ホワイトペーパー②

ビジネスメール詐欺の実態と 対策アプローチ 巨額な被害を生むサイバー犯罪の巧妙な手口
Trellix Email Security - Cloud Editionの機能概要
Trellix製品特徴:IVX 仮想実行解析エンジン
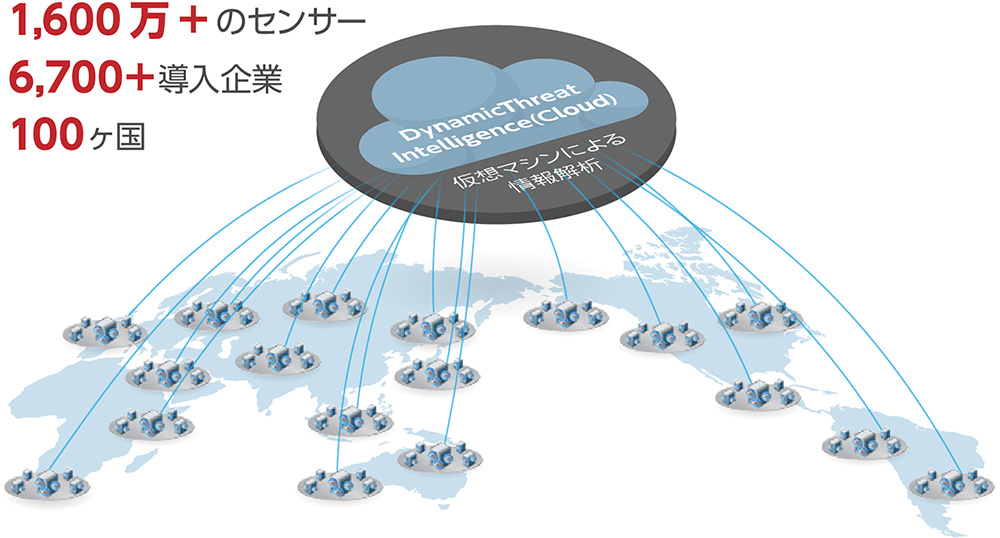
Trellix 製品特徴:Dynamic Threat Intelligence(DTI) クラウド
世界各地で発生している最新の脅威情報を共有し、サービス利用者全体のセキュリティを最新の防御機能で強化します
Trellix Email Security - Cloud Edition IVX 検知機能
メールに添付されたファイルの解析
メール本文中のURLリンク解析
メールヘッダ解析
Trellix Email Security - Cloud Edition 検知機能の強化策
Dynamic URL Analysis
- メール本文中にURLを見つけるとサンドボックス内でアクセスし、ファイルが見つかったらダウンロードして動的解析
Trellix Advanced URL DEfence
- 不審なURLをTrellix社のクラウド(DTI)で分析
マルチステージ攻撃分析
- ファイルそのものがマルウェアの実行ファイルではなく、外部サイトと通信して別のマルウェアを送り込むマルチステージ攻撃分析
フィッシングサイト分析(PhishVision)
- Webサイトのスクリーンショットデータを、『ニューラルネットワーク』と呼ばれる数学モデルの手法で分析
フィッシングサイト分析(Kraken)
- Webサイトのページコンテンツと既知フィッシングサイトを詳細に比較分析
Trellix Email Security - Cloud Edition アンチスパム/アンチウィルス機能
Trellix Email Security - Cloud Edition AV/AS オプションには以下の機能が含まれます。
- Anti Virus
- 3rdパーティ製アンチウィルスエンジンによる添付ファイルのスキャン
- Anti Spam
- RBL (Real-time Block List)
- Directory Harvest Attack
- 送信者認証 SPF/DKIM/DMARC
- カスタムルール(受信者、送信者等の条件によるユーザ作成WL/BL)
導入構成
例1)既に他社Cloud Emailセキュリティ製品の利用中で、機能強化/補完するケース
例2)クラウドメールの標準セキュリティサービスと統合するケース