product
- Line up
- Network Security: Trellix (formerly FireEye) Network Security
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense
- Network Security: Trellix (formerly McAfee) Network Security Platform
- Endpoint: Trellix (formerly FireEye) HX
- Endpoint: Trellix (formerly McAfee) Mvision
- Data Protection: Trellix Data Security
- Email Security: Trellix (formerly FireEye) Server Edition
- Email Security: Trellix Cloud Edition
- Security Operations: Trellix (formerly FireEye) Helix
- Security Operations: Trellix (formerly McAfee) SIEM (Security Information and Event Management)
- Enhanced cloud governance: Trellix (formerly FireEye) Cloudvisory
- File Security: Trellix (formerly FireEye) Malware File Storage Scanning
- Integrated Management Solution: Trellix (formerly FireEye) Central Management
- NDR Solution: Network Investigator (NI) / Packet Capture (PX)
- Cloud-based File Threat Protection: Trellix IVX Cloud
Specifications/Technical Information
- Trellix (formerly FireEye) Technical Information
- Trellix (formerly FireEye) Specifications
- Network Security: Trellix (formerly FireEye) Network Security Technical Information
- Network Security: Trellix (formerly McAfee) Network Security Platform Technical Information
- Network Security: Trellix (formerly McAfee) Network Security Platform Specifications
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense Technical Information
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense Specification
- Email Security: Trellix (formerly FireEye) Server Edition EX Series Technical Information
- Email Security: Trellix (formerly FireEye) Server Edition EX Series Specifications
- Integrated Management Solution: Trellix (formerly FireEye) Central Management (CM) Series Specifications
- Security Operations: Trellix (formerly McAfee) SIEM (Security Information and Event Management) Technical Information

Trellix
Trellix
Security Operation (4) - 3 Steps for Introducing SOAR to Realize "Automation of Security Operations"

SOAR introduction flow and points you should know
In the previous article, we explained that SOAR has the following four advantages.
- Reduction of operational load
- Speed up incident response
- Optimized use of human resources
- Addressing skill shortages
*For details, please refer to the article below.
Security Operation ③ - What is SOAR (Security Orchestration and Automated Response)?
However, if SOAR is not introduced in a way that is suitable for the company's security operations, the expected effects cannot be obtained. When introducing SOAR, technical tuning based on knowledge is essential in order to match it with your company's security operations. This article introduces the flow and key points.
In general, SOAR adoption drives three phases:
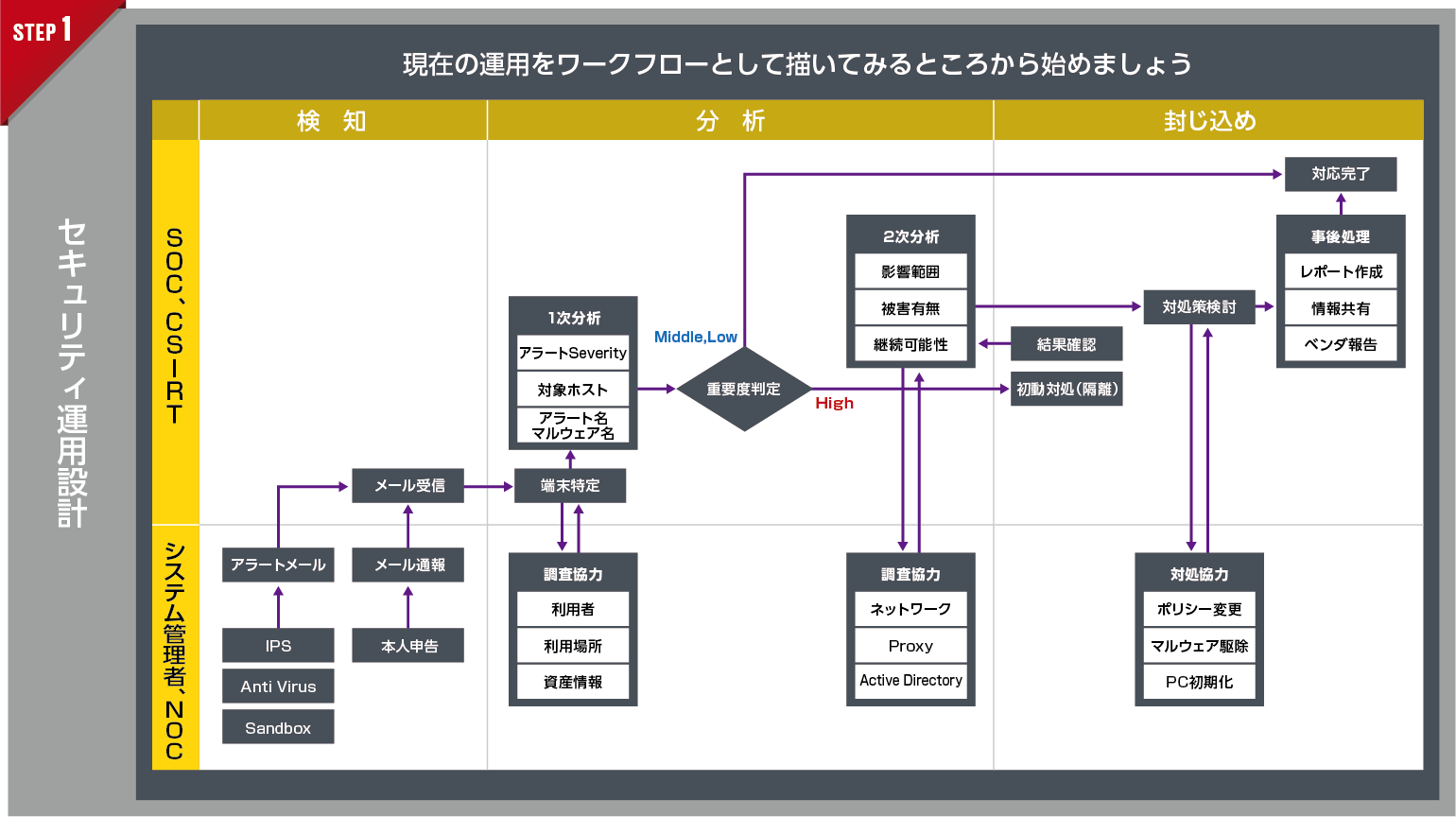
① Security operation design
"Defining security operations" is a prerequisite for introducing SOAR. On the other hand, it is also true that there are many companies that do not have an operational design in the first place, or that have an operational design for using specific products. For companies that have not had a clear operational design until now, let's start by drawing the current operation as a flow.
POINT
- In particular, by focusing on tasks that take a long time, tasks that place a heavy burden on operators, simple tasks that are easy to automate, and tasks that cannot be done now, subsequent automation will be smoother.
- The end user who is in charge of operation is responsible for the operation design, and the vendor who knows the operation supports it.
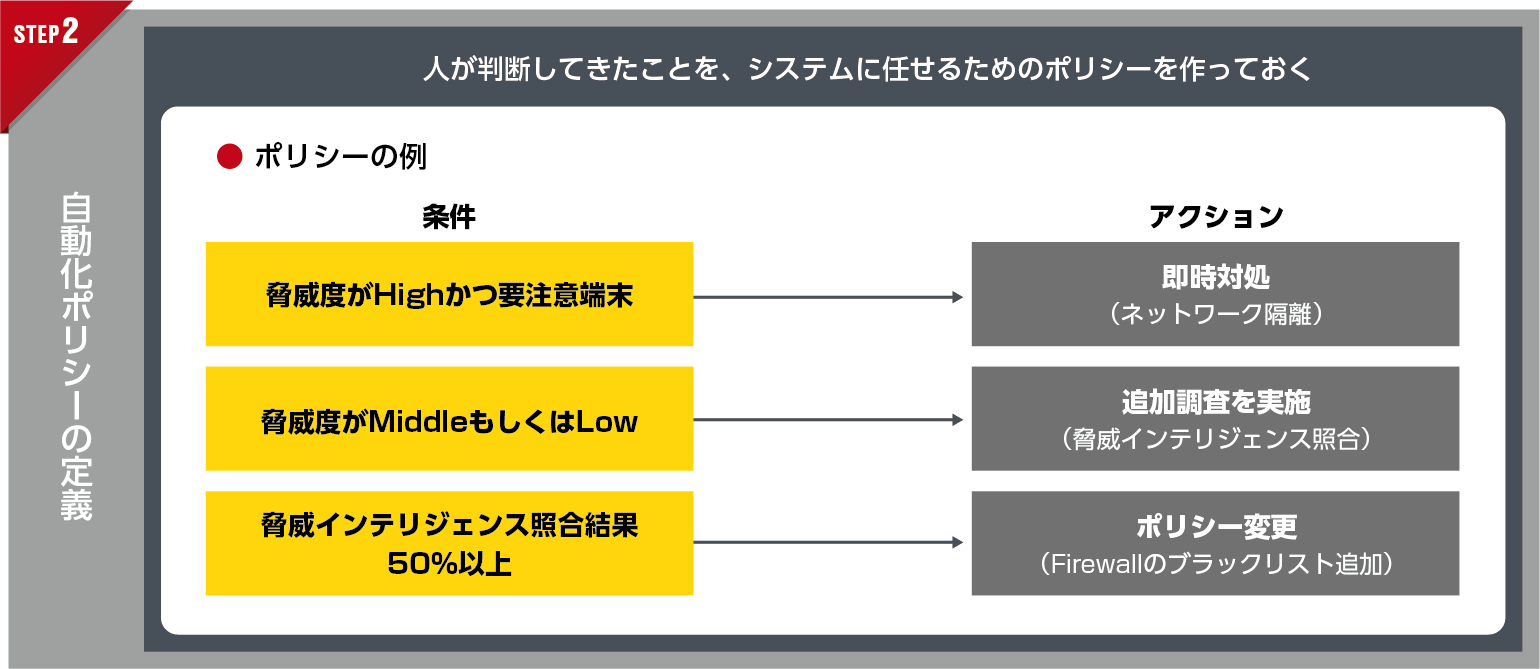
② Definition of automation policy
In order to let the system handle the judgments that have been made by humans up until now, we assume various operational scenarios and define an automation policy that says, "When this condition occurs, this action should be taken."
POINT
- You don't have to automate everything from scratch. Start with tasks that are easy to automate, such as simple tasks and simple branching.
- If there is a work that is "somewhat doing" from the experience of the individual operator, we will grasp it and reflect it.
- We will mutually agree in advance that we will coordinate between departments on a case-by-case basis.
- The criteria defined in this phase can be flexibly changed later.
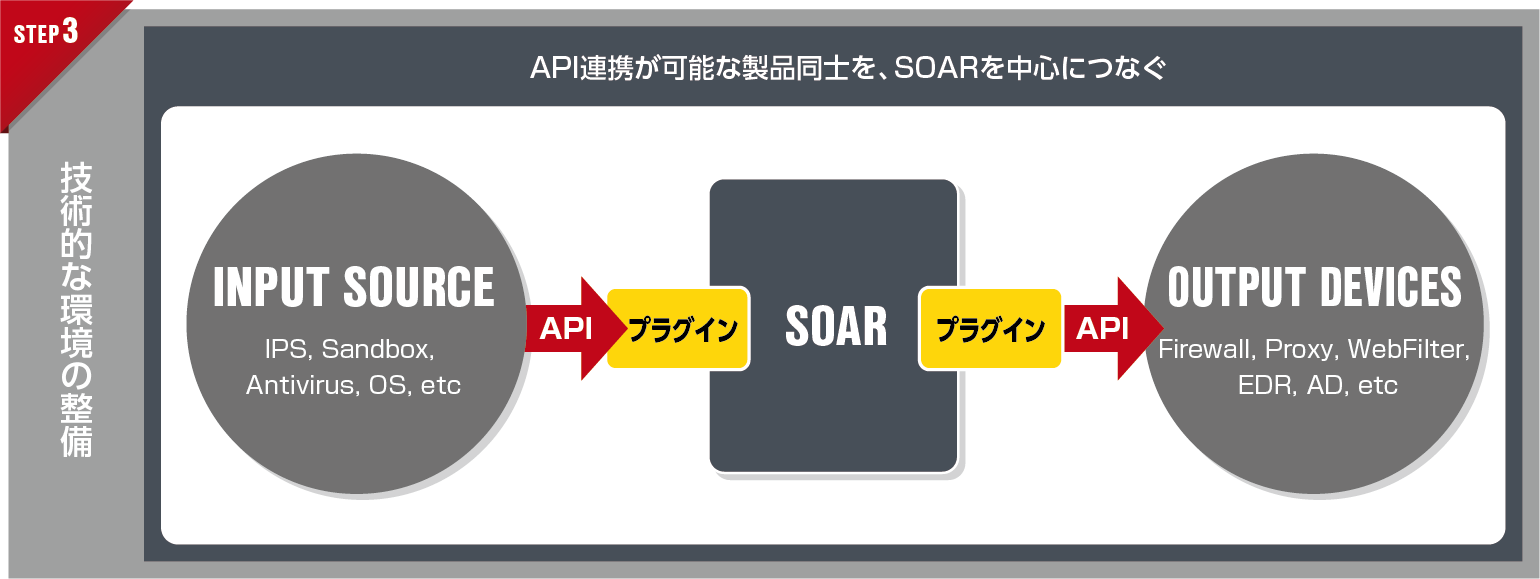
③ Development of technical environment
Decide which security products will work with SOAR and prepare the technical environment. Products that can be linked with APIs are "connected" with SOAR as the core.
POINT
- Currently, there are many products that do not have an API, products that are not officially supported, and products that have an open API but lack documentation. For easy implementation, select a product that provides sample code or an APP that relays API and SOAR.
- Since the API is subject to change, it is necessary to consider in advance how to deal with the version upgrade, such as the method of impact investigation and the scope of maintenance.
- Linking across multiple products makes it difficult to separate the product vendor's scope of responsibility and contact information.
- As mentioned above, there are many technical issues in the implementation phase, so the experience of vendors and distributors, concrete support based on actual results, and knowledge gained in the community are extremely important.
Summary
The burden of security operations is increasing due to multiple factors such as the increasing sophistication of threats, the increasing complexity of security product operations, and the increase in alerts. Companies can obtain various benefits by automating with SOAR, but at the same time they need to consider the best implementation method for their own security operations. The following video explains the SOAR introduction flow in more detail, so please take a look.
In addition, if you are concerned about the increasing burden of security operations, or if you have an awareness of issues in the exhausting operation site, please feel free to contact us.
Inquiry/Document request
In charge of Macnica Trellix Co., Ltd.
- TEL:045-476-2010
Weekdays: 9:00-17:00