product
- Line up
- Network Security: Trellix (formerly FireEye) Network Security
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense
- Network Security: Trellix (formerly McAfee) Network Security Platform
- Endpoint: Trellix (formerly FireEye) HX
- Endpoint: Trellix (formerly McAfee) Mvision
- Data Protection: Trellix Data Security
- Email Security: Trellix (formerly FireEye) Server Edition
- Email Security: Trellix Cloud Edition
- Security Operations: Trellix (formerly FireEye) Helix
- Security Operations: Trellix (formerly McAfee) SIEM (Security Information and Event Management)
- Enhanced cloud governance: Trellix (formerly FireEye) Cloudvisory
- File Security: Trellix (formerly FireEye) Malware File Storage Scanning
- Integrated Management Solution: Trellix (formerly FireEye) Central Management
- NDR Solution: Network Investigator (NI) / Packet Capture (PX)
- Cloud-based File Threat Protection: Trellix IVX Cloud
Specifications/Technical Information
- Trellix (formerly FireEye) Technical Information
- Trellix (formerly FireEye) Specifications
- Network Security: Trellix (formerly FireEye) Network Security Technical Information
- Network Security: Trellix (formerly McAfee) Network Security Platform Technical Information
- Network Security: Trellix (formerly McAfee) Network Security Platform Specifications
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense Technical Information
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense Specification
- Email Security: Trellix (formerly FireEye) Server Edition EX Series Technical Information
- Email Security: Trellix (formerly FireEye) Server Edition EX Series Specifications
- Integrated Management Solution: Trellix (formerly FireEye) Central Management (CM) Series Specifications
- Security Operations: Trellix (formerly McAfee) SIEM (Security Information and Event Management) Technical Information

Trellix
Trellix
Security Operation ①-Before introducing SIEM or SOAR! Visualization of the current state using frameworks

general remarks
Recently, I often hear from security personnel that "operations have become difficult." In terms of physical strength, such as "the amount of work is large in the first place", "a lot of work is done on holidays and at night", "the load is concentrated due to a shortage of manpower", "the responsibility is heavy", and "you don't know when you will be called, so you can't get rid of the tension." "It's taken for granted that nothing happens, and it's hard work, but it's not appreciated."
In this paper, we will organize the issues of security operation and guide you on how to organize and improve security operation using the security measures framework.
Finally, we have also included a video summarizing examples of how security operations were organized and improved through the use of frameworks, so be sure to check it out.
Specifics
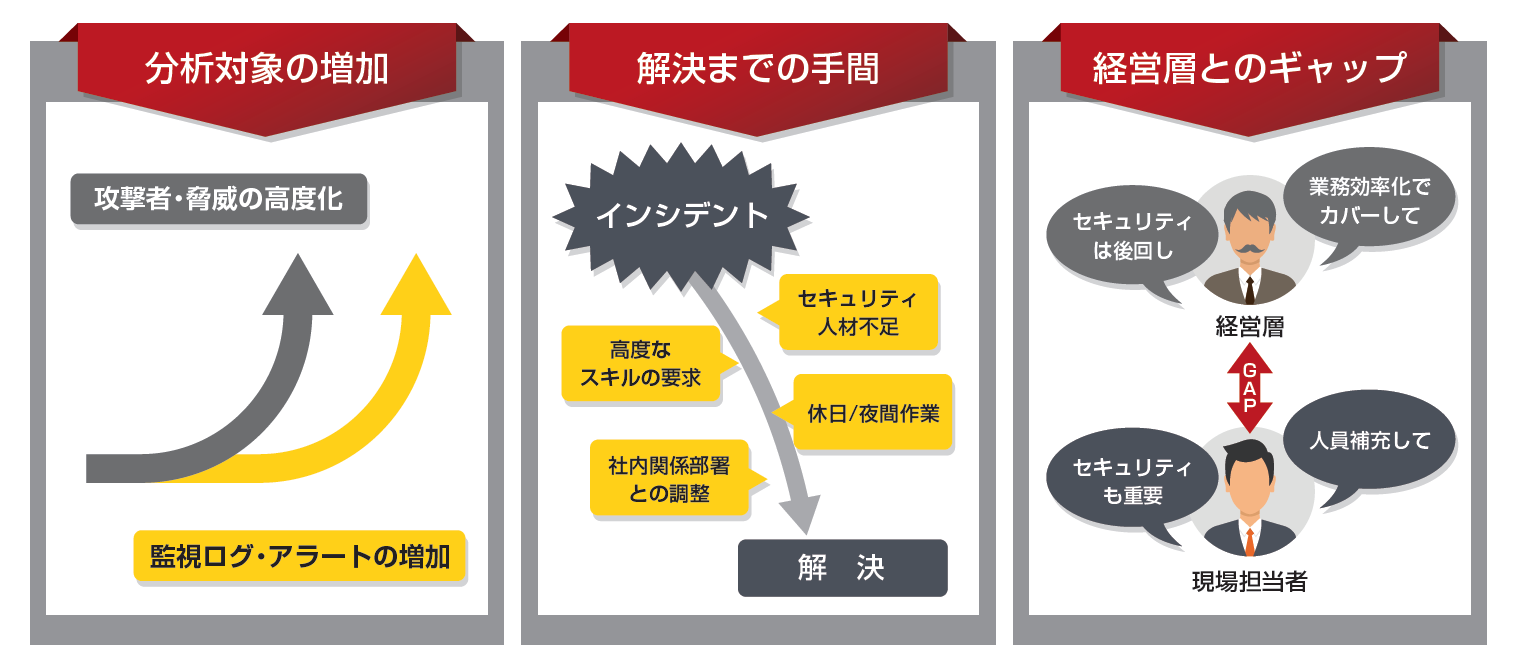
Security operation challenges
What kind of specific burdens do you have in the field of security operations? What I hear from the person in charge at the site is the following severe situation.
- Increased analysis target
Cyberattacks are becoming more sophisticated every day, and security threats are becoming more sophisticated. Along with this, the volume of logs and alerts to be monitored has also increased dramatically. Recent operational monitoring products have begun to proactively issue alerts even for gray threats that cannot be determined as incidents. A large number of alerts are generated, and the person in charge must decide one by one whether it actually leads to an incident. Although it is unavoidable to ensure security, it is one of the reasons for the increase in the amount of work. - time to resolve
In order to prepare for various threats, the types and number of security products introduced in enterprises are increasing. There are a wide variety of management and operation methods, and procedures are becoming more complex, requiring security personnel to have advanced skills. Skills become obsolete quickly, and new knowledge must be acquired one after another. Work is concentrated on limited security personnel, and companies are constantly suffering from a shortage of personnel. Working on holidays and at night, and coordinating with the department in charge are also burdensome for the person in charge.
Comprehensive understanding of security operations using the security framework
In order to solve the operational issues mentioned earlier, it is necessary to first visualize the current security operation status. There are many frameworks in the world, but this article is based on the Cybersecurity Framework (hereinafter referred to as CSF) advocated by NIST (National Institute of Standards and Technology), which is good at overlooking the situation in terms of operation. describes the visualization method for security operations.
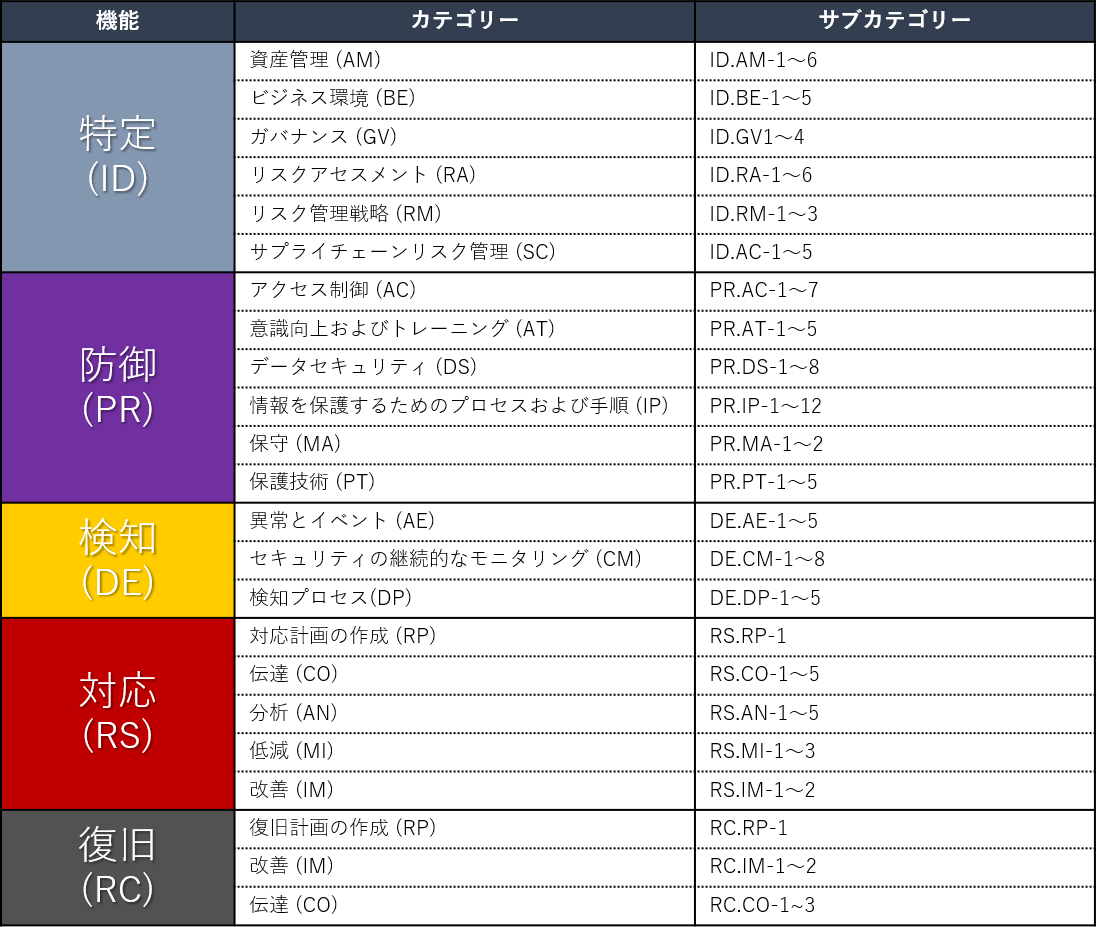
CSF consists of 5 functions.
It is categorized by operation stage: "Identification", "Protection", "Detection", "Response", and "Recovery".
Figure 1: Structure of NIST Cybersecurity Framework (1)
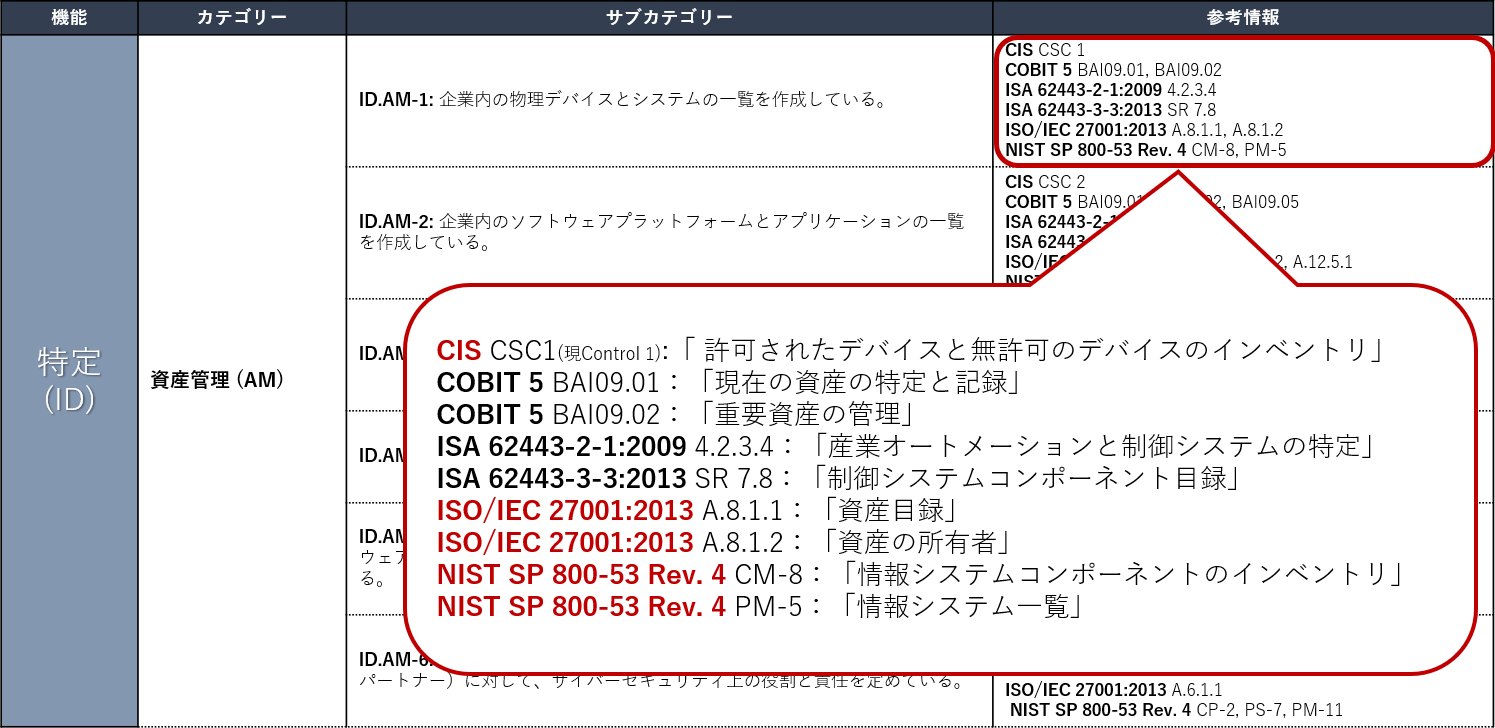
In addition, each category consists of multiple subcategories, and these subcategories have more detailed action items. There are also external materials (below, in the red frame) that can be used as a reference for concrete consideration and implementation.
Figure 2: Structure of NIST Cybersecurity Framework (2)
How to use the NIST Cybersecurity Framework
So how should we use this CSF?
The procedure for using CSF is briefly summarized below.
- Using CSF, consider necessary items, unnecessary items, and new items to be added to your company, and create a base for your own company profile.
- Enter the current level of achievement (Tier) for each subcategory
- For each subcategory, set the achievement level (Tier) that the company should aim for
- Set priorities for response to subcategories where there is a gap between the current situation and the level of achievement to be achieved
- Implement initiatives to achieve the desired level of achievement according to priority
Figure 3: Analysis of the current situation based on the NIST Cybersecurity Framework
Figure 4: Definition of each tier
★ point
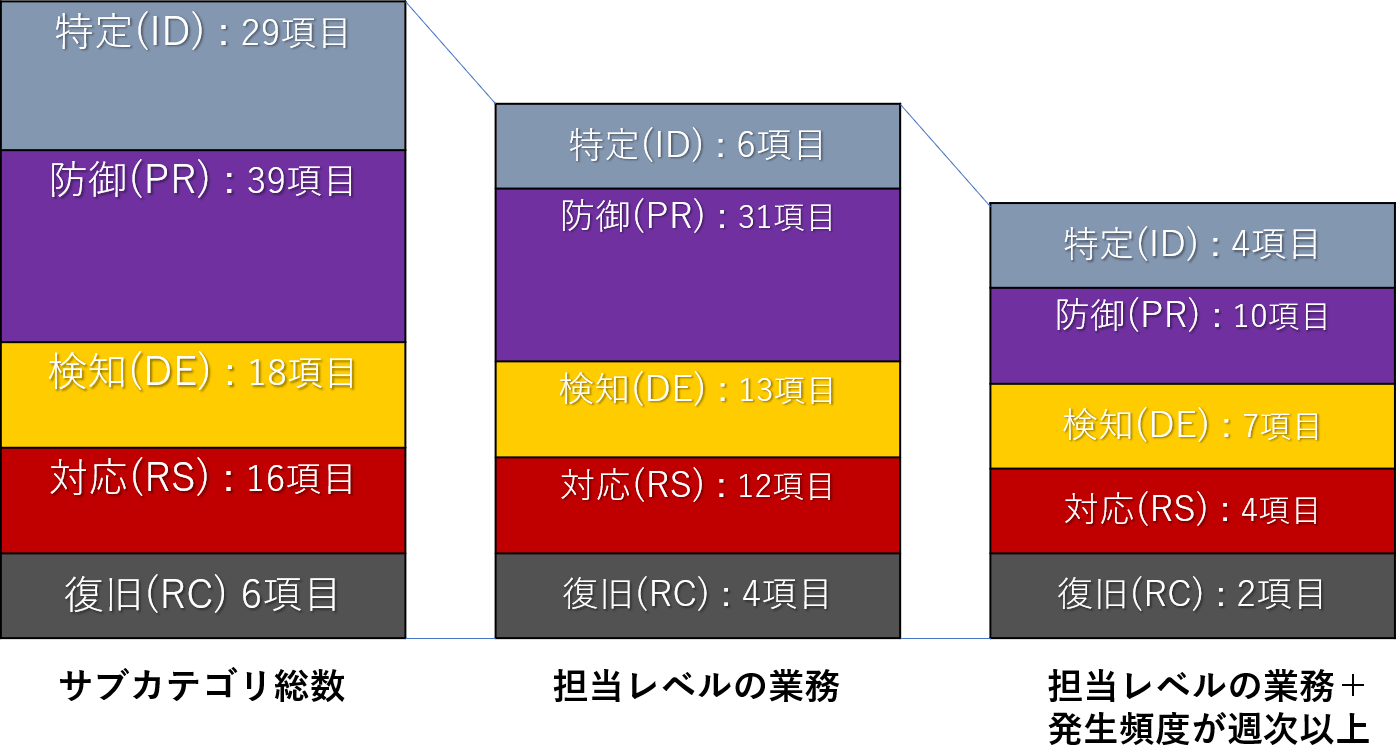
In order to visualize the work of actual operation, it is recommended to break down to the level of responsibility for each category and organize the frequency of occurrence. This is because the CSF is for visualizing and prioritizing the entire organization, so it includes roles at the management and Member of the Board level in addition to the responsible level.
Figure 5: Example of breaking down tasks with a relatively high frequency of occurrence at the responsible level
Measures to be taken after visualization of operation status
After visualizing the security operation status with CSF, it is recommended to classify high-priority operations into operations controlled by the company and operations to introduce/outsource products.
For reference, we recommend that you control the following operations yourself.
- Matters to be determined and executed by management and Member of the Board
- Selection of suppliers and partners
- Approval of improvement process
- Operation and management of systems that remain highly individualized
- Overall handling in incident response (It is good to receive external support)
On the other hand, incident response-related operations included in "detection," "response," and "recovery," tend to be improved through product introduction/outsourcing.
In the video below, we explain the products/service groups linked to each function of CSF, so please take a look.
Conclusion
Even for vague attempts to improve security operations, by analyzing the current situation according to a security framework such as the NIST CSF, we can see the issues that need to be addressed and the appropriate measures for each issue.
In the video below, a person who provides security consulting services to major corporations and also serves as a member of Macnica 's CSIRT uses actual case studies to explain how companies visualize their security operations status and what measures they took to address the issues that came to light.
Before considering security operation products and services, why not take a look at them?
Inquiry/Document request
In charge of Macnica Trellix Co., Ltd.
- TEL:045-476-2010
Weekdays: 9:00-17:00