product
- Web application vulnerability diagnosis
- Integrated SOC service
- security advisory
- security assessment
- Website security monitoring service
- CrowdStrike Monitoring Operation Support Service
- Active Directory Diagnostic/Monitoring Service
- CSIRT enhancement exercise
- Suspicious email training service
- platform diagnostics
- CSIRT construction support
service

Macnica
Macnica
The increasing number of cyber security crimes has become one of the management issues, and from the perspective of security governance and requests from stakeholders, the CSIRT/SOC system has been established to ensure smooth security operations during normal times and emergencies, mainly for listed companies. is becoming commonplace.
CSIRT and SOC are complementary. SOC is usually outsourced to security specialist analysts who have special knowledge to collect, understand, analyze, and deal with incident information that occurs in cyberspace. On the other hand, CSIRTs need to understand their own organization and environment, create an environment in which incidents are unlikely to occur during normal times, and carry out activities to minimize risks during emergencies (incidents).
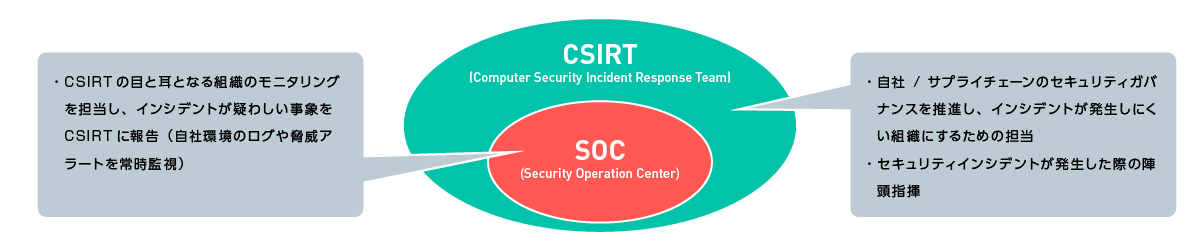
The following elements are necessary for the CSIRT to conduct its activities smoothly.
- Develop a functional system that matches your company's security sufficiency level and organizational structure
- Preparation of procedure manuals and flows for emergencies (when an incident occurs)
- A tabletop exercise to check if the CSIRT works as designed
- System for consulting with security experts on issues in CSIRT operations during normal times and countermeasures against changes in security risks
- Consider and implement measures to be implemented on a regular basis to improve employee literacy
It can be said that by regularly turning these, you can protect your company from cyber attacks and have a security operation system that can respond quickly in the event of an emergency.
Macnica provides services from the construction of your CSIRT to its smooth operation.
1. Develop a functional system that matches your company's security sufficiency level and organizational structure
CSIRT and group security management system design support
In order to respond quickly when an incident occurs, we will clarify the roles and departments necessary for incident response and provide support to strengthen CSIRT activities.
| item | content |
| Purpose | In order to respond quickly when an incident occurs, we will clarify the roles and departments necessary for incident response and provide support to strengthen CSIRT activities. By clarifying the security management system of the entire group, it will lead to prompt cooperation in the event of an incident and strengthening of daily security operations. |
| Implementation content |
*Internal approval will be implemented by the customer according to the customer's internal rules. |
| Coverage | Group security management system |
| Artifact | CSIRT and group security management system chart |
Image of deliverables for CSIRT and group security management system design support
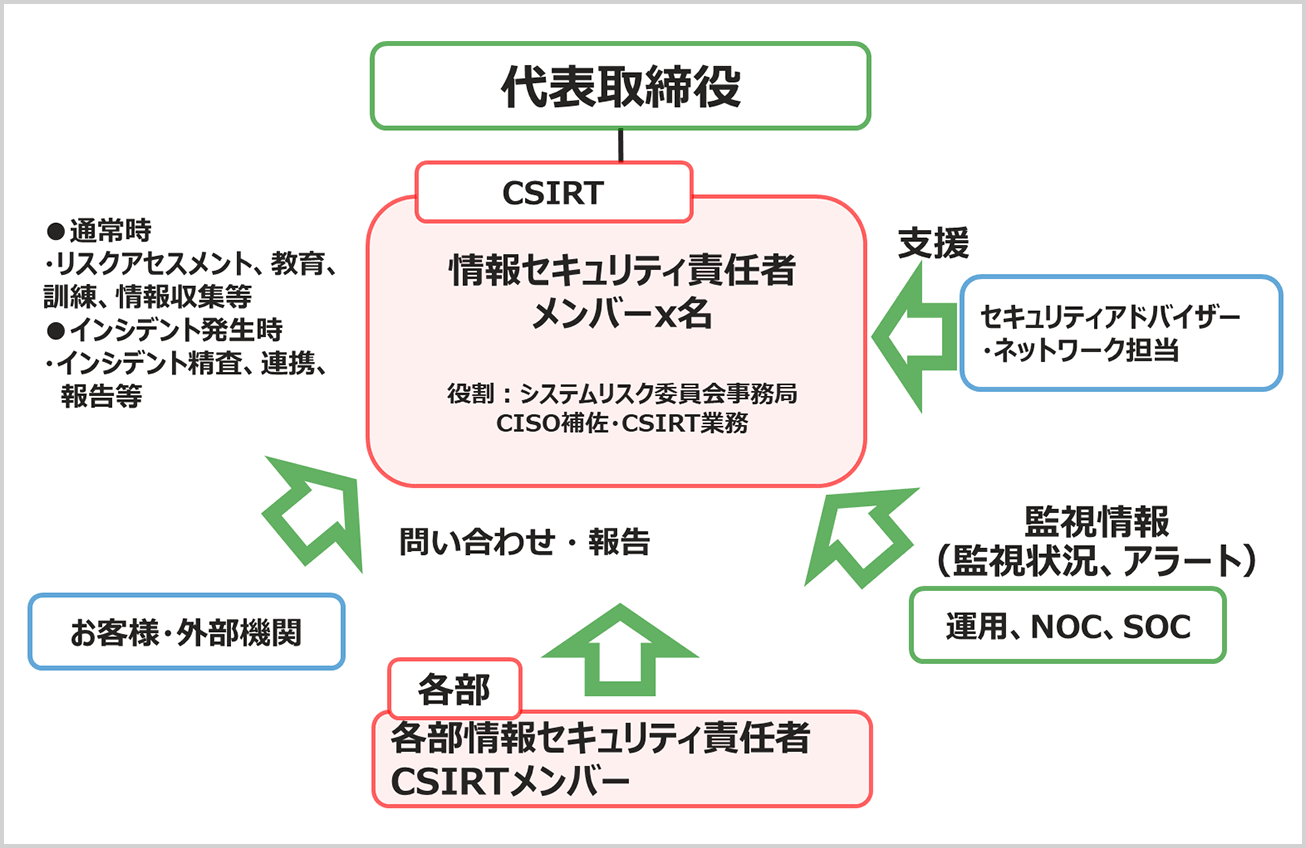

CSIRT sample
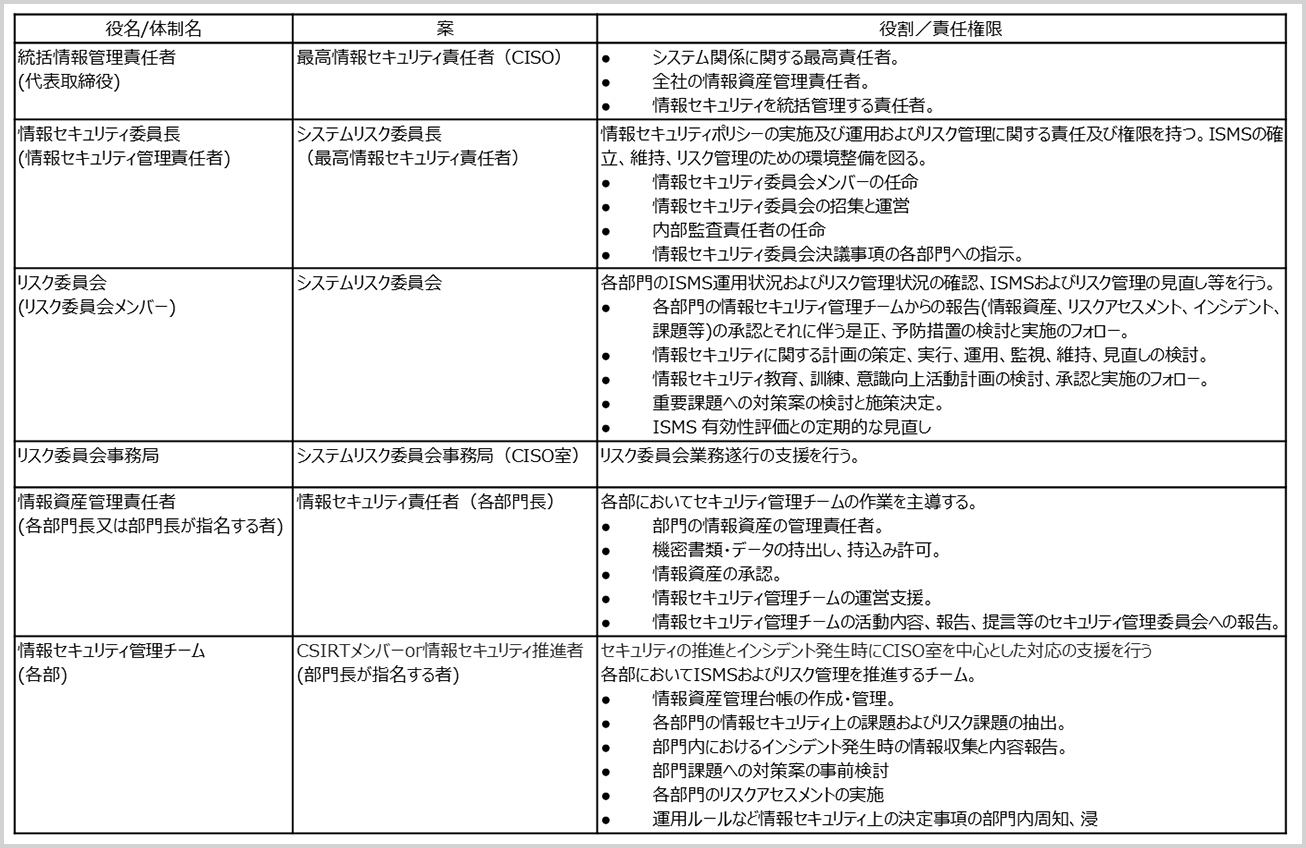

role sample
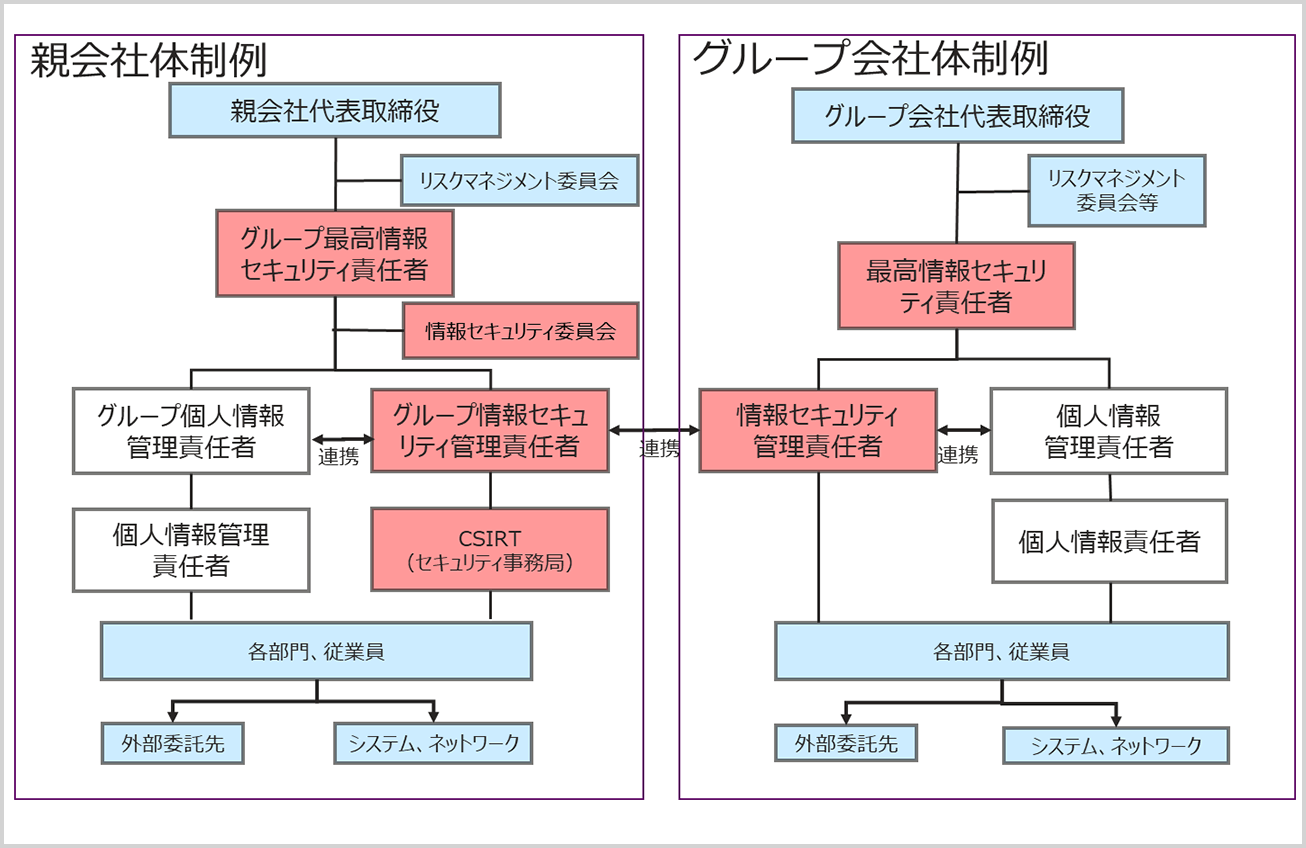

Group security management system sample
2. Preparation of procedure manuals and flows for emergencies (when an incident occurs)
Incident response procedure manual and incident response flow creation support
| item | content |
| Purpose | In operating the CSIRT, the procedures for responding to incidents are summarized in a procedure manual, and support is provided so that the CSIRT can operate smoothly in the event of an emergency.In addition, by creating an incident response flow, the flow of incident response can be visualized. It will also lead to an improvement in the level of CSIRTs that will start operation. |
| Implementation content |
*Internal approval will be implemented by the customer according to the customer's internal rules. |
| Coverage | Incident response procedures and incident response flow |
| Artifact | Incident response procedures and incident response flow |
Deliverable image of incident response procedure creation support

Incident Response / Sample Operating Procedures for CSIRT during Normal Times
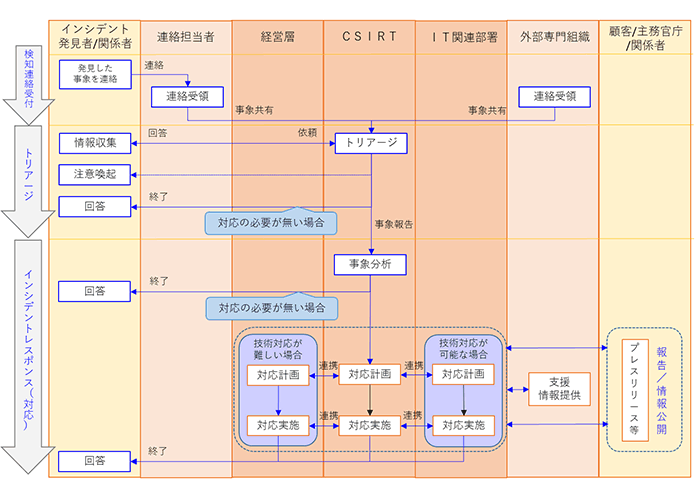
Incident response flow sample
3. A tabletop exercise to check if the CSIRT works as designed
4. System for consulting with security experts on issues in CSIRT operations during normal times and countermeasures against changes in security risks
5. Consider and implement measures to be implemented on a regular basis to improve employee literacy
Inquiry/Document request
In charge of Macnica Security Service Co., Ltd.
- TEL:045-476-2010
- E-mail:sec-service@macnica.co.jp
Mon-Fri 8:45-17:30
