product
- Web application vulnerability diagnosis
- Integrated SOC service
- security advisory
- security assessment
- Website security monitoring service
- CrowdStrike Monitoring Operation Support Service
- Active Directory Diagnostic/Monitoring Service
- CSIRT enhancement exercise
- Suspicious email training service
- platform diagnostics
- CSIRT construction support
service

Macnica
Macnica
Common challenges in security monitoring
Each security product is monitored by a separate operator, and it takes time to respond to incidents.
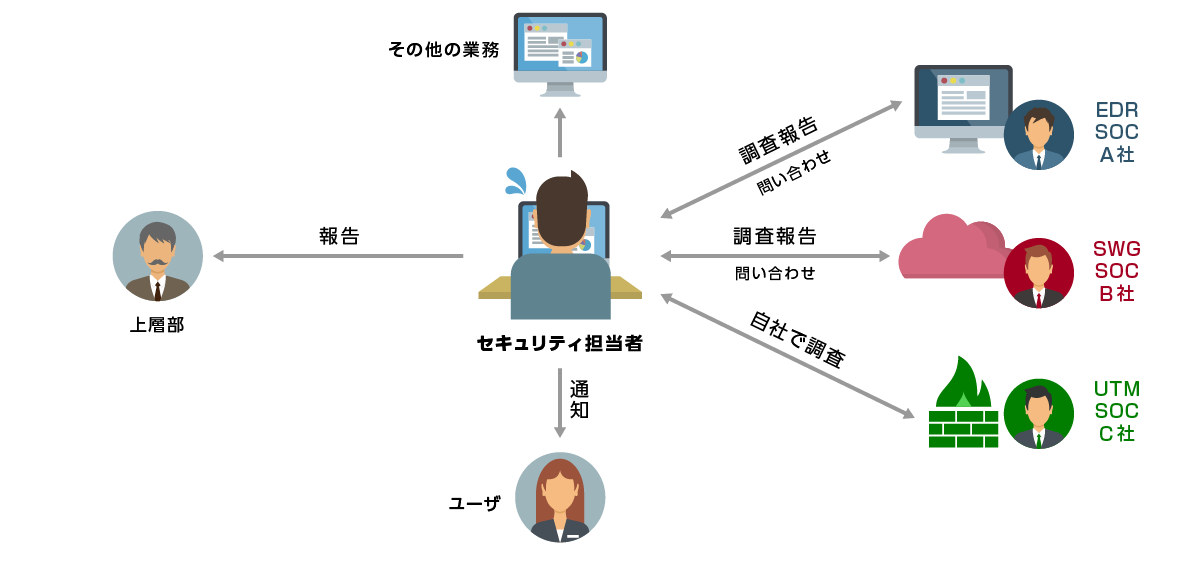
Insufficient resources and knowledge for alert monitoring and log analysis of security devices
- Security products start operation after introduction
- Every time an alert is raised, it is necessary to investigate, make a decision, make an initial response, and take action.
Many operators have restrictions on products that can be monitored
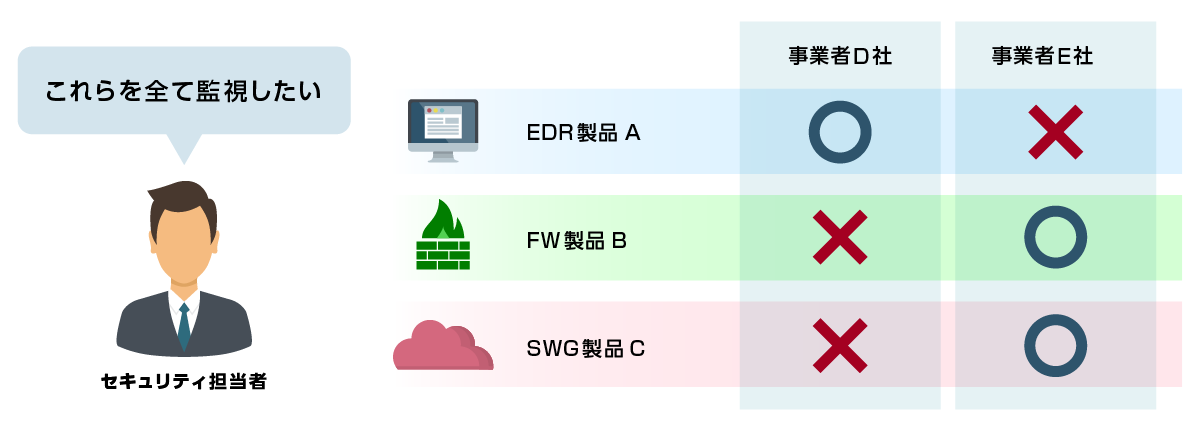
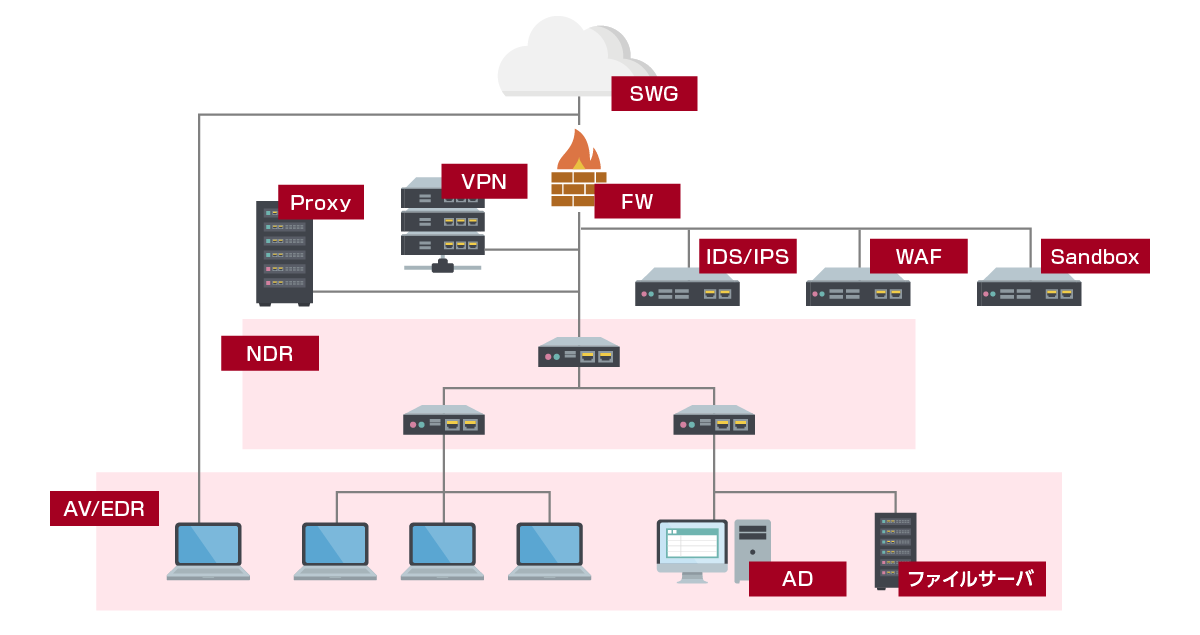
Image of integrated SOC service
Our security experts monitor security device alerts 24 hours a day, 365 days a year and perform correlation analysis of network device logs, and promptly and accurately investigate and report important alerts for our customers. .
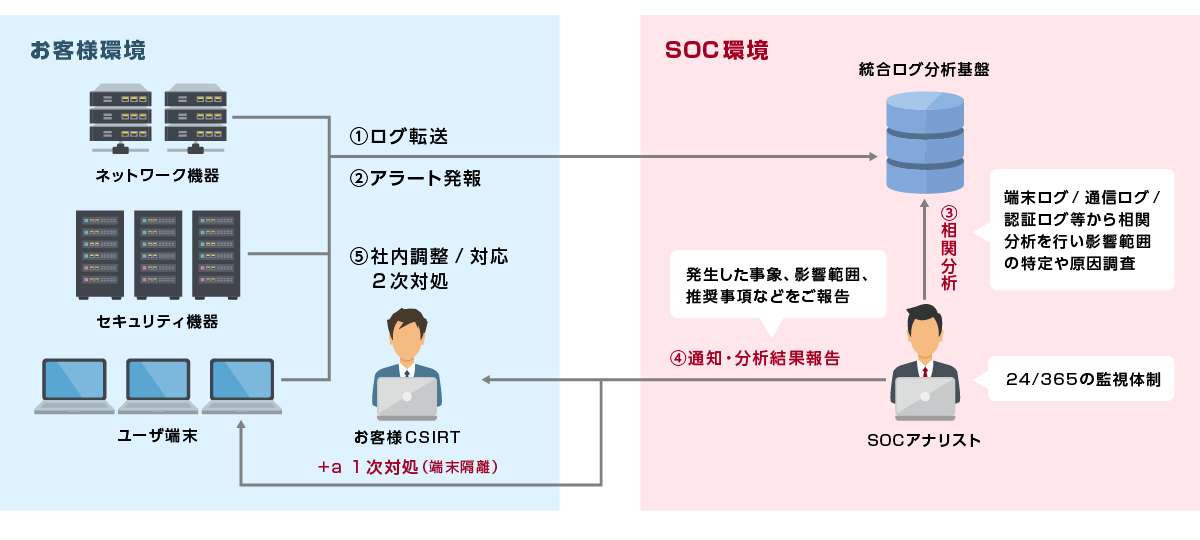
Features of Integrated SOC Service
“Broad” & “Flexible” Surveillance Categories
We provide monitoring for products in various categories:
It is possible to respond flexibly when introducing new equipment or replacing equipment.
Quickly guide “specific” & “easy-to-understand” escalations
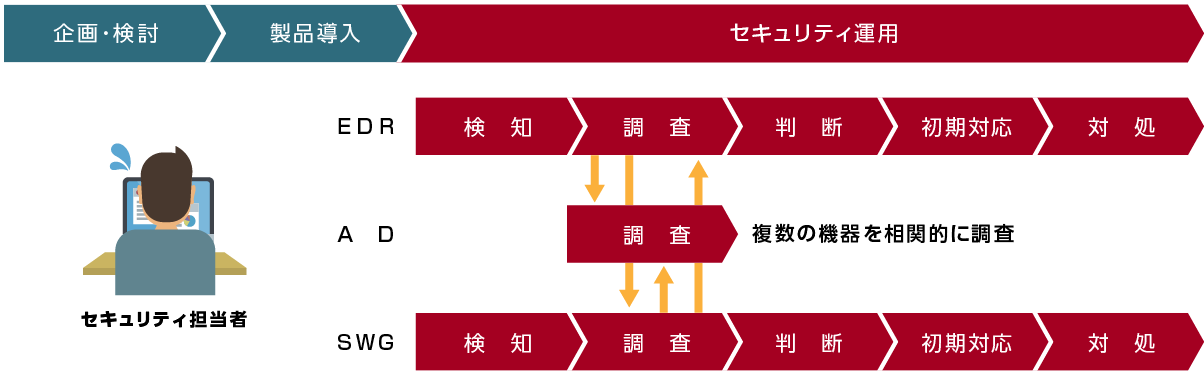
In today's attacks, attackers manually attempt to penetrate deep into networks. Monitoring and investigating these attacks requires the detection capabilities of security equipment as well as in-depth research by security experts.
This service is triggered by alerts raised from security devices such as EDR by our security experts, and after detailed correlation analysis of logs of various security devices and network devices, the alerts to be reported are generated. We will promptly inform you of the event, scope of impact, recommended actions, etc.

*Escalation samples will be provided individually upon request.
Seamless support for incident response in the event of an emergency
With the speed of attacks increasing in recent years, it is important to be able to quickly grasp the incident situation and minimize the impact when a highly urgent incident occurs.
We provide comprehensive support from integrated SOC services to incident response support in the event of an emergency.
In addition, by creating a customer chart (configuration diagram, log storage status, contact system, etc.) in advance, in the unlikely event that an incident occurs, we will promptly conduct hearings and propose incident response after understanding the customer environment. .
*Customer chart creation and other incident response support will be charged separately depending on the content of the incident.
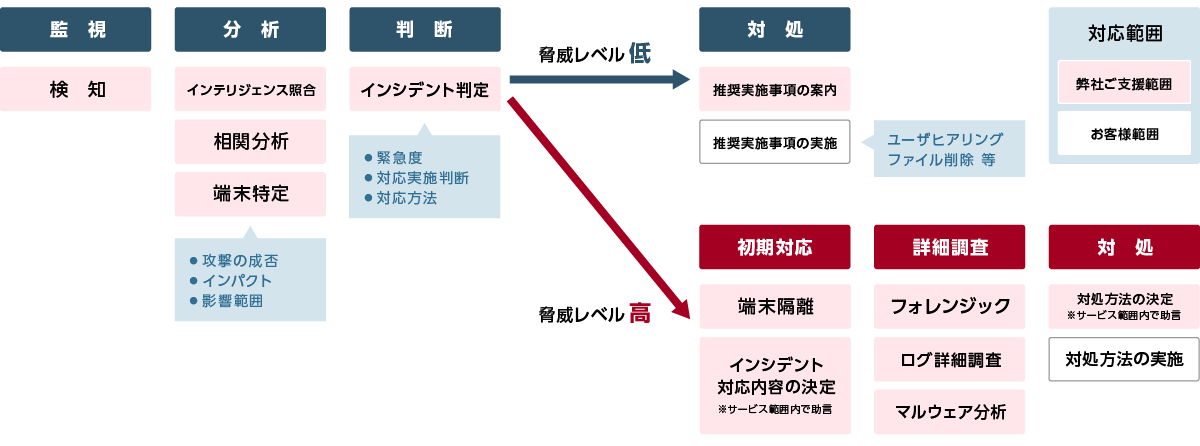
reference
●Incident response support menu
Our company has a wealth of support experience and knowledge for the purpose of investigating when an incident occurs and minimizing the impact.
Our dedicated incident response team is ready to assist you.
| Major item | item | Overview |
| 1. Incident response support preparation | Advance preparation for incident response support | In advance, we will interview you about your company's environment and the log acquisition status of the equipment necessary when an incident occurs, provide advice, and create a communication system and flow. |
| 2. Support in the event of an incident | 2-1. Incident response support | After the initial hearing, we will attend the emergency countermeasures meeting held in the customer's company by e-mail, telephone, etc., and provide advice on containment, eradication, and recovery measures. |
| 2-2. malware analysis | We analyze suspicious emails and samples suspected of being malware, and advise countermeasures. | |
| 2-3. Log analysis | Analyze the presence or absence of suspicious behavior and the possibility of information leakage from the logs of FW, proxy, AD, etc. | |
| 2-4. fast forensics | We analyze whether there is suspicious behavior or whether there is a possibility of information leakage. |
Related Documents
●Introduction example: DMM.com LLC
<Evaluation points>
・Scalability that can handle all kinds of logs such as device version upgrades and new products and services
・Instead of simple alert notifications, there are action instructions and thorough follow-up that should be taken based on analysis results.
https://www.macnica.co.jp/business/security/manufacturers/sandj/case_01.html
●Blog: About how SOC operation should be reconsidered now
https://mnb.macnica.co.jp/2023/07/securityservice/soc.html
For inquiries about this service and consultation on quotations
Feel free to contact us below
Inquiry/Document request
In charge of Macnica Security Service Co., Ltd.
- TEL:045-476-2010
- E-mail:sec-service@macnica.co.jp
Mon-Fri 8:45-17:30
