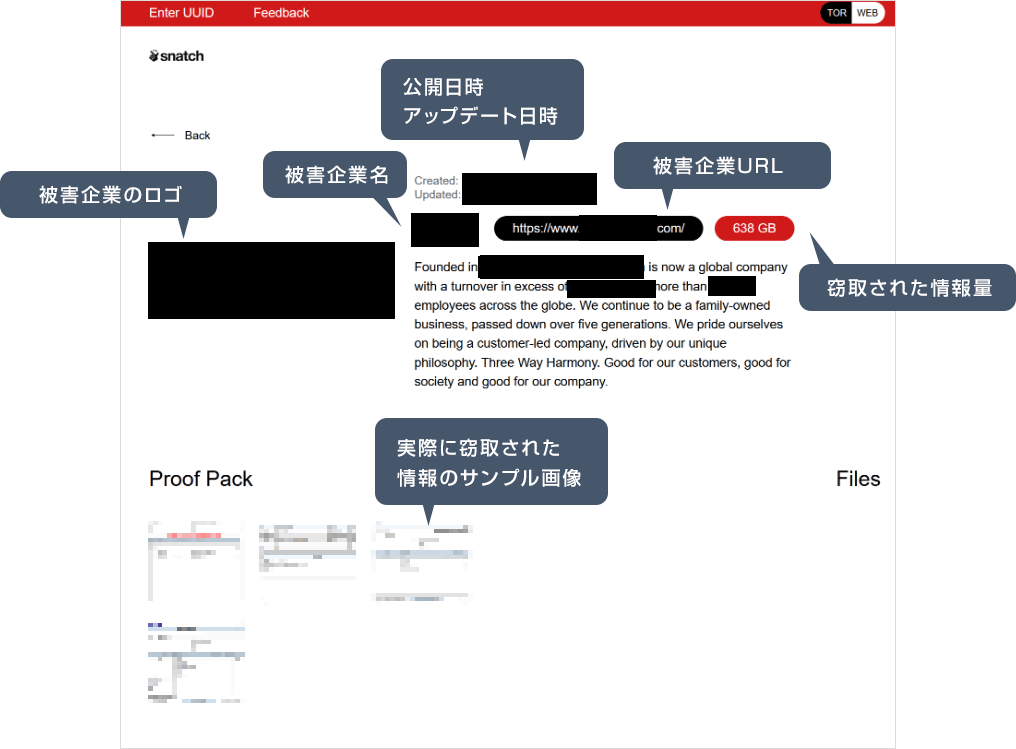
Ransomware infection
Correspondence is
really perfect! ?
What is the actual situation of new ransomware and how to deal with it
What is new ransomware?
The new type of ransomware, also known as exposure ransomware or double-intimidation ransomware, is an extremely heinous type of ransomware that steals personal information and important company information, threatens disclosure, and demands a large ransom from the victim company several times. cyber attack.
- subject
- Mainly client PCs, various servers
- phenomenon
- Client PC, server encryption and self-diffusion
- Purpose
- Ransom demanded for decryption
Ransom demand for business recovery
- requested amount
- tens of thousands of yen
- subject
- File server, client PC, control system
- phenomenon
- After hijacking Active Directory and taking control of the corporate network, encryption and information theft of file servers and client PCs
- Purpose
- ransom demand for decryption, Ransom demands to stop disclosure of stolen information
In some cases, the stolen information is sold to other companies.
- requested amount
- Tens of millions of yen
The damage caused by the new ransomware, which seemed to subside at the beginning of 2021, has increased sharply since the spring of 2021. Including those that have not been reported in the media or published on the attacker's site, it is believed that there are a considerable number of companies that have suffered damage. Another recent feature is the conspicuous attacks that exploit vulnerabilities in the overseas bases of Japanese companies.
New ransomware modus operandi and damage
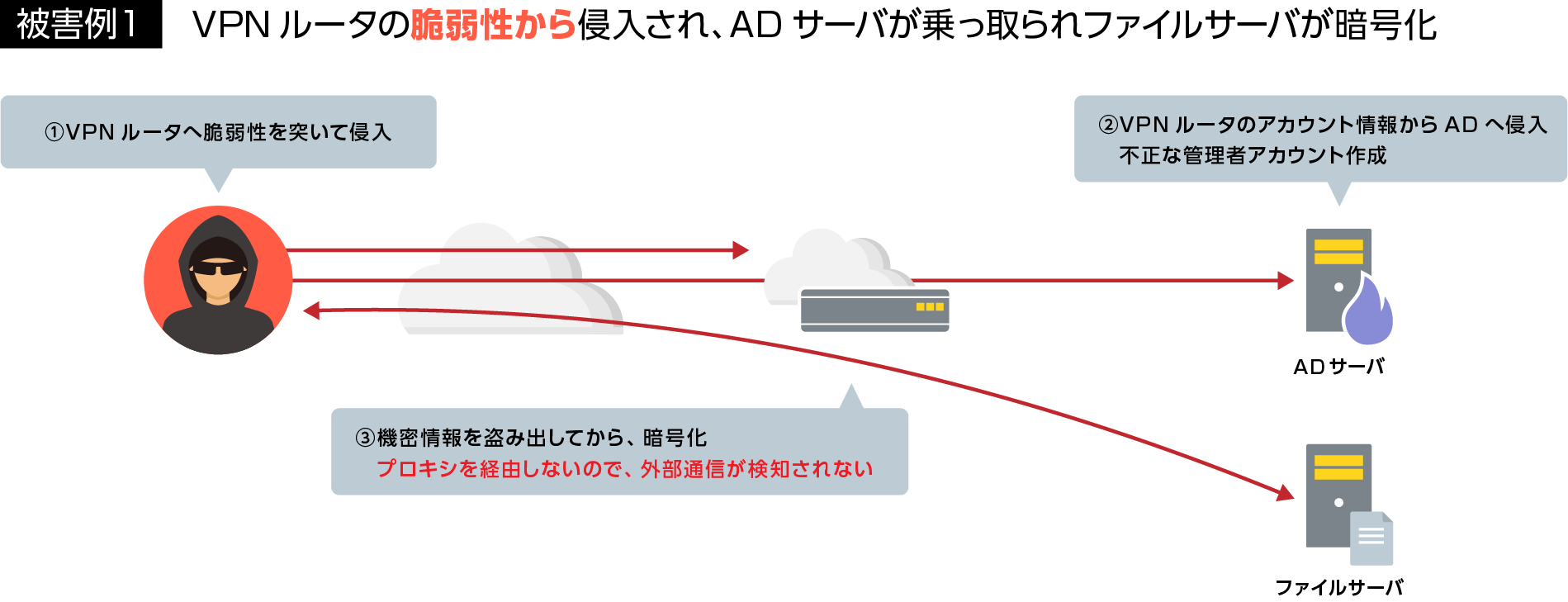
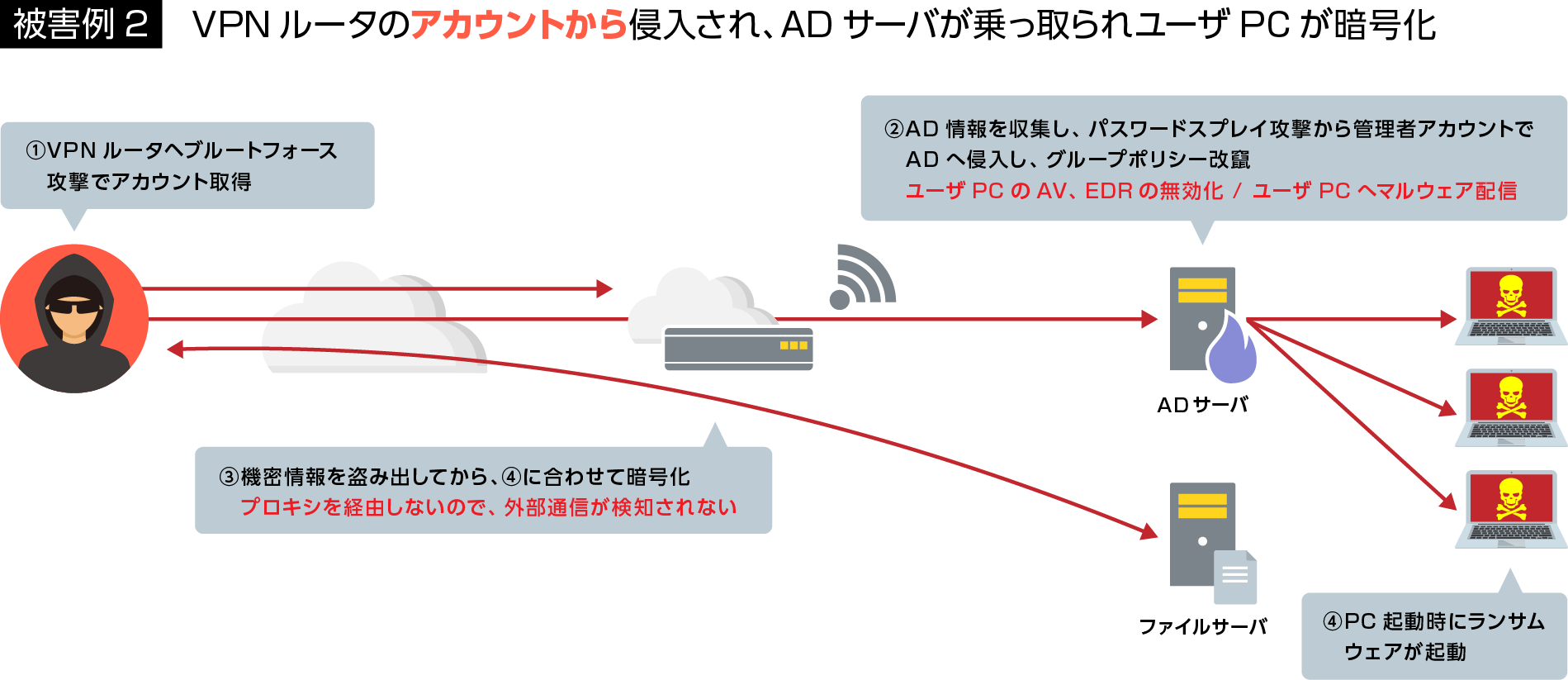
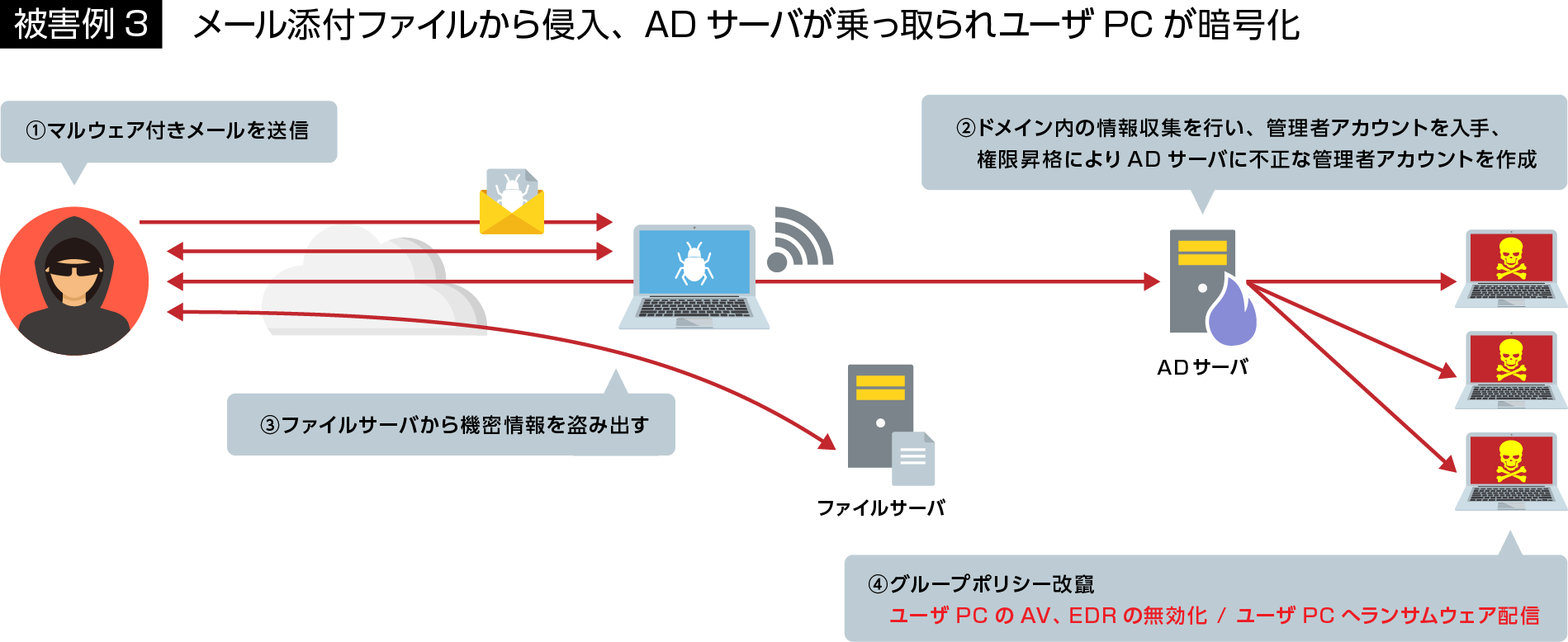
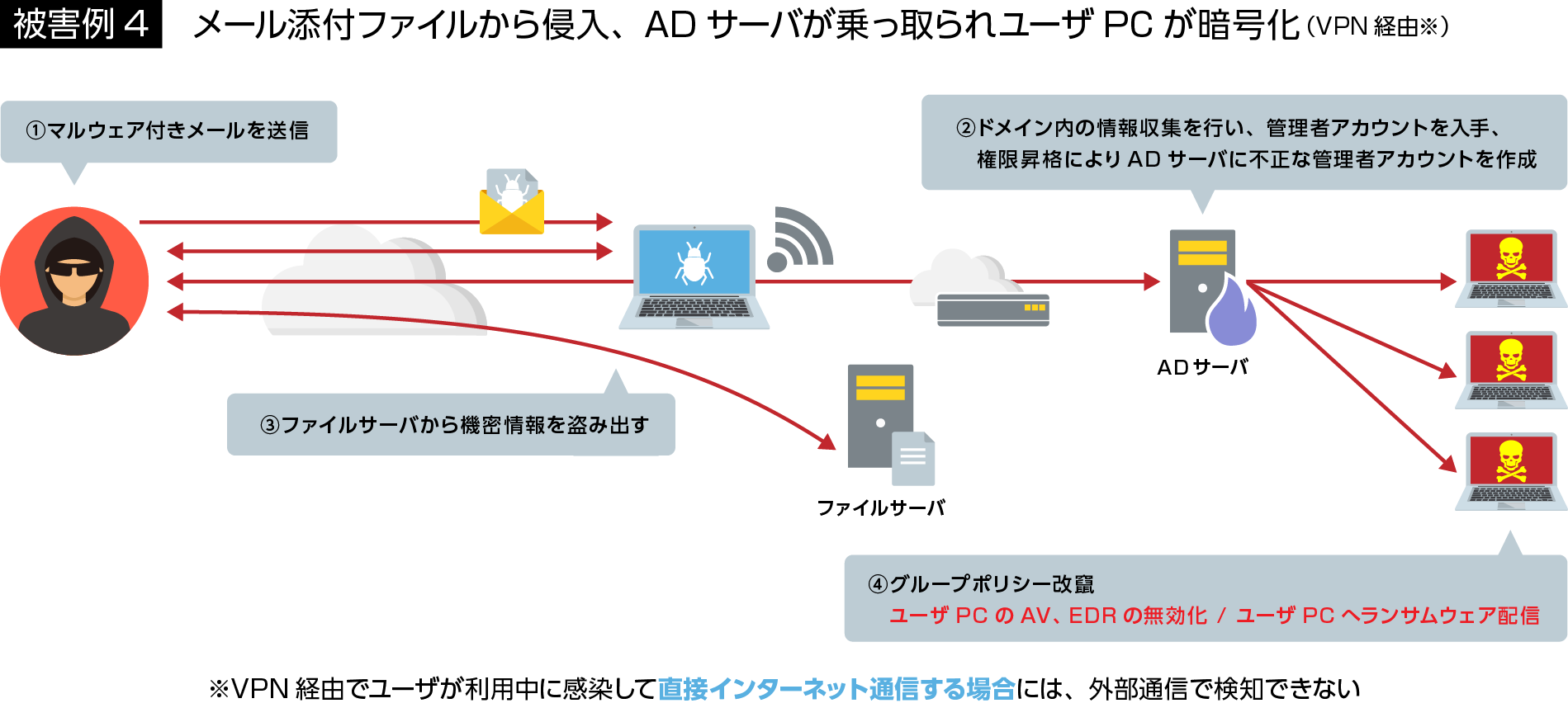
There are two main methods of new ransomware: intrusion via VPN vulnerabilities and intrusion due to the client PC opening suspicious e-mail attachments. After that, 1) the AD is hijacked, 2) important information is stolen, 3) the PC or file server is encrypted, and 4) the information is threatened to be disclosed.
VPN vulnerabilities have been mentioned repeatedly, but new vulnerabilities have been found recently, and there are still many assets that have not been addressed in the first place.
On the other hand, regarding the method of using email, EUROPOL (European Criminal Police Organization) succeeded in taking down Emotet in January 2021, and although Emotet suspended its activities for a while, it resumed its activities in November 2021. It has been reported that
What to do when you are hit by ransomware
In the event of an attack, it is necessary not only to restore business, but also to investigate and take appropriate measures to prevent future attacks.
What to investigate
- ransomware identification
Check ransomware and encrypted file extensions: By identifying ransomware, it is possible to determine whether it is a new type of ransomware, and from the attack method used, information can be obtained to narrow down the investigation target and respond quickly. there is. - attacker's entry path
Logs other than security products such as AD server event logs, VPN logs, and proxy logs are also investigated to identify intrusion routes. As a result, it is possible to confirm the extent of damage leading to ransomware execution and the details of the damage, and to strengthen the security of the intrusion points to prevent recurrence.
ransom payment
Attackers demand a ransom to stop the decryption key and information disclosure. In the rush to restore business, it is tempting to think of responding to the attacker's demands, but the following risks must be considered.
- Data may not be recoverable
Paying the ransom does not guarantee that the attacker will provide the decryption key. *1 There have also been reports of cases where decryption keys were provided, but the recovery speed was too slow to be of any use. - reputation risk
If information that a ransom has been paid is released to the market, it will be seen as funding a criminal organization, resulting in a loss of reputation for the company. - invite more attacks
As the company paying the ransom, the victim company is more likely to be attacked repeatedly.
*1: According to the Sophos report "The State of Ransomware 2021", in January to February 2021, the surveyed companies paid a ransom to restore all encrypted data, and the percentage of recovered data was 8%. stay in. Twenty-nine percent of companies recovered less than 50% of their data.
business recovery
- When damaged by ransomware, in many cases it is necessary to cut off internet communication to stop external communication and restore data to restore encrypted servers and PCs. However, in recent years, there have been cases of stealing only information without encryption and threatening a ransom. In either case, business must be resumed after a thorough investigation and provisional measures to prevent recurrence. If you make a mistake in responding to it, you may become a target again and again.
In the event of a ransomware attack, it is necessary to have specialized knowledge and experience, and at the same time to proceed with many tasks in parallel. On the other hand, it is also necessary to set checkpoints to determine when business can be restored, and to make detailed external reports (including progress reports).
Therefore, it is also effective to receive the support of security experts who have experience and expertise in dealing with incidents in conducting these prompt investigations and responses.
弊社は事案対応は元より、企業の状態を調査し、そもそもランサムウェアの被害に合わないように企業が取るべき対応・対策の支援も行わせていただきます。
Service introduction
| Service name | support |
| security advisory | We will interview and advise on the sufficiency and planning of your security measures. In addition, we will hold regular meetings to review vulnerability information and recent security topics that require attention. We will create a customer chart, and in the unlikely event that an incident occurs, we will respond with priority. |
| Active Directory Diagnostic/Monitoring Service | We will check and report whether the required patches have been applied to Active Directory and whether the settings are set so that logs sufficient for investigation can be obtained in the event of an emergency. In addition to detecting unauthorized logons and failed logon attempts, it also detects suspicious Powershell and task registrations and allows customers to escalate or stop the suspicious behavior. |
| Mpression Cyber Security Service™ Attack Surface Management Service | We provide advice on discovering externally published assets (servers, VPN devices, etc.) including stray servers and dealing with and correcting high-risk assets. |