
Mpression Cyber Security Service™
Mpression Cyber Security Service™


Trends in recent cybersecurity threats
Major incident factors in recent years
According to the recently published multiple period investigation reports, the top incident cause is “caused by externally disclosed assets”.
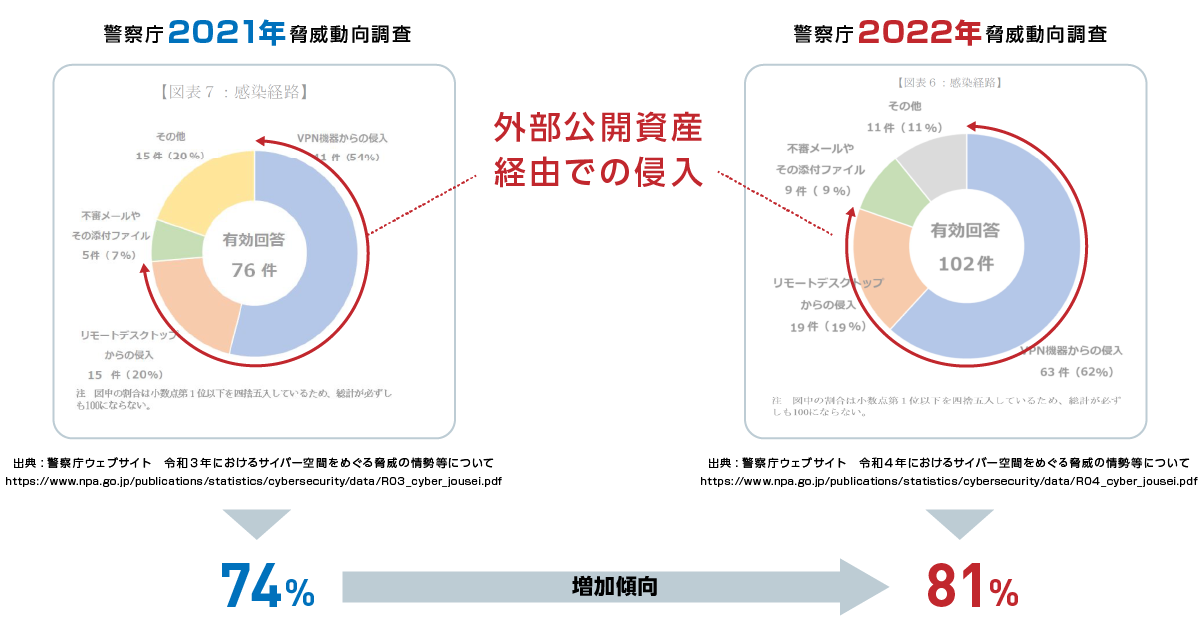
Why are there so many security incidents now?
Attack techniques have changed in recent years and are extremely effective at exploiting weaknesses in enterprise security.

What is ASM (Attack Surface Management)?
What is ASM (Attack Surface Management)?
Attack Surface Management (ASM) is an initiative to identify and manage assets (Attack Surface) that can be used as attacks by cyber security threats.
Since the first step of ASM starts with an accurate grasp of assets, it is necessary to comprehensively grasp the company's assets.
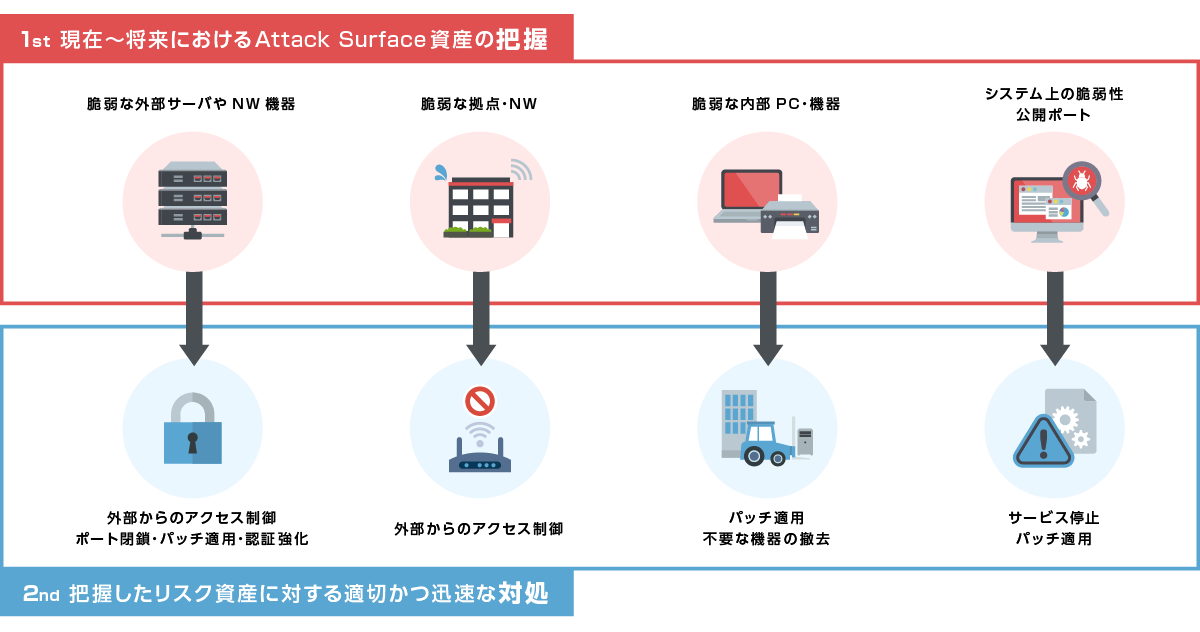
Key points that customers should do with ASM
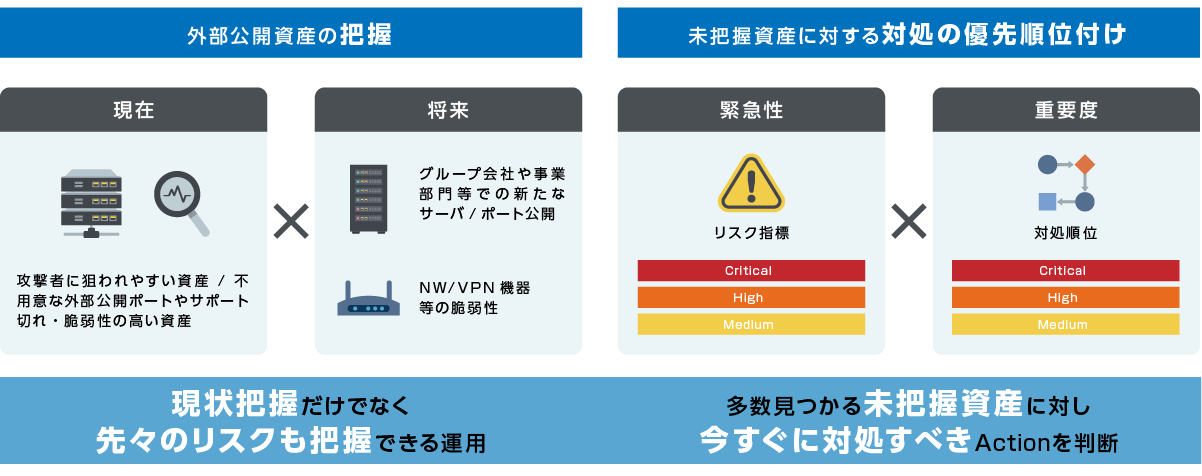
The important points when implementing ASM are not only the current situation, but also the comprehensive "understanding" of assets that can respond to changes in the future, and the "priority" of countermeasures that take into account the urgency and importance of the identified asset risks. ranking”.
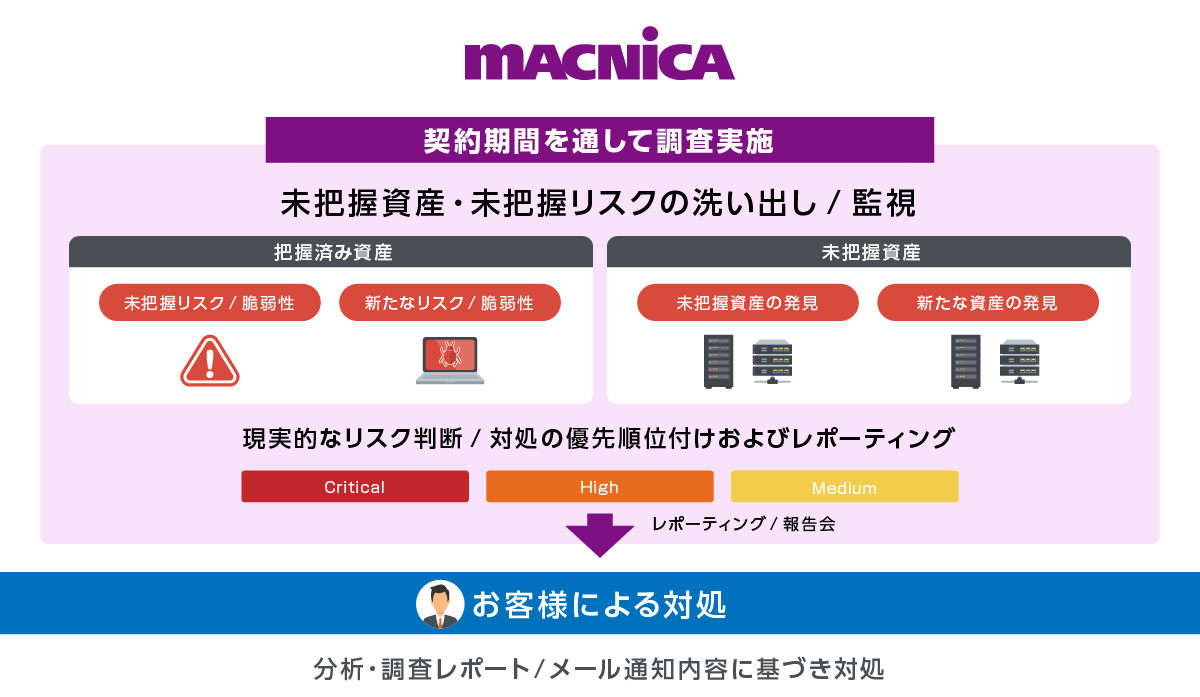
Macnica 's Attack Surface Management service
Overall service image
Macnica 's Attack Surface Management service is a completely unique service provided by Macnica that focuses on understanding the most important points and prioritizing countermeasures. Our Security Research Center uses its unique knowledge to conduct accurate and comprehensive investigations with the "human hands and eyes."
Macnica 's proud group of security experts - Security Research Center -
Analysts from the Security Research Center, who are familiar with trends and methods of domestic and international cyberattacks, discover assets and determine threats from the perspective of attackers.

manager of centre
Kenzo Masamoto

Assistant Director
Yutaka Sejiyama

Chief
Ryo Shota

Chief
Hajime Yanagishita

chief
Hiroshi Takeuchi

chief
Takeshi Teshigahara

chief
Goya Yamazaki
- international conference
- Black Hat USA Arsenal 2013 - 2016
- Black Hat Asia Arsenal 2017
- DEF CON 25 Demo Labs
- HITCON Pacific 2018
- FIRST Annual Conference 28
- Domestic conference
- Japan Security Analyst Conference 2018
- Internet Week 2015
- Shirahama Symposium 18th
- Information Security Expo Specialized Seminar
- Supervised translation of books
- Incident Response 3rd Edition
- Other social activities
- SECCON executive committee
- Security Camp National Convention Instructor
- Government Security Advisor
- Japan Business Federation 21st Century Policy Research Institute Research Committee
- threat research
Service features and research methods
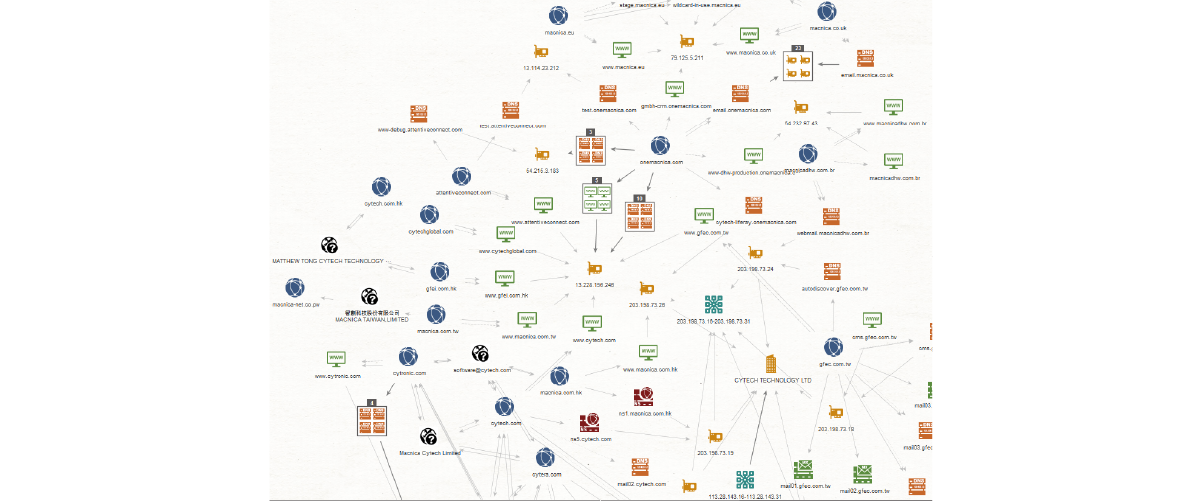
The Security Research Center uses its own knowledge to conduct accurate and comprehensive investigations with "human hands and eyes".
Using the customer's head office domain and group company domain posted on the website as the initial value, we check Whois information, MX records, NS records, etc., and trace related domains and IP address connections from there to identify customer-related assets. Wash out. It is also possible to identify assets, including domains, stray servers, and overseas bases that the customer is not aware of.
Survey image
Output Samples -Now/What/Priority Should Be Implemented-
We provide a report that shows discovered unidentified assets, risk indicators, and response priorities that can be understood at a glance and can be used immediately. Since it is also written in English, it is possible to smoothly provide explanations to overseas bases.

User company interviews
Arconics Co., Ltd.
SEGA SAMMY HOLDINGS CO., LTD.
reference
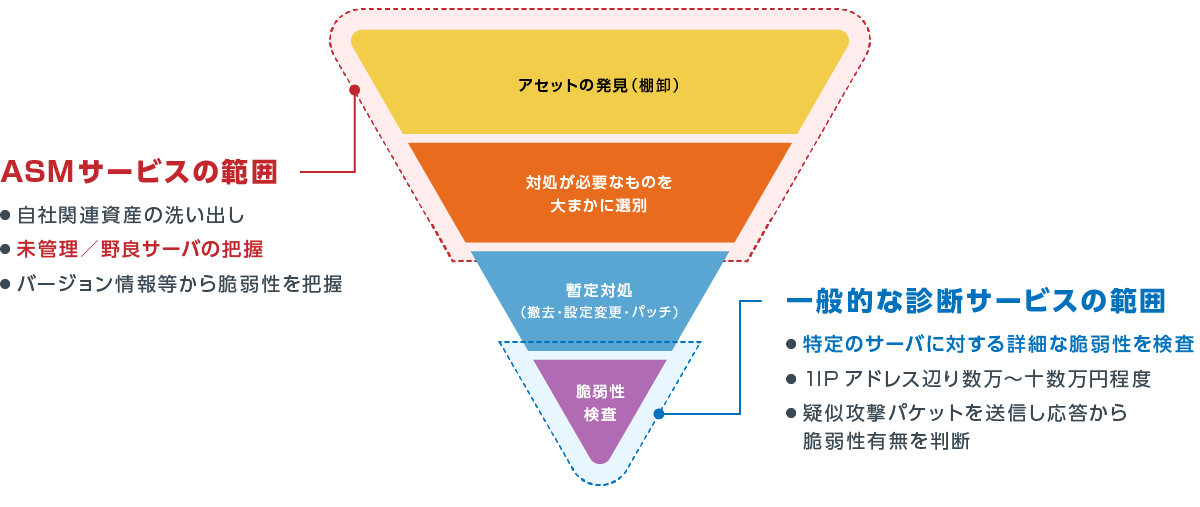
Difference from vulnerability diagnosis
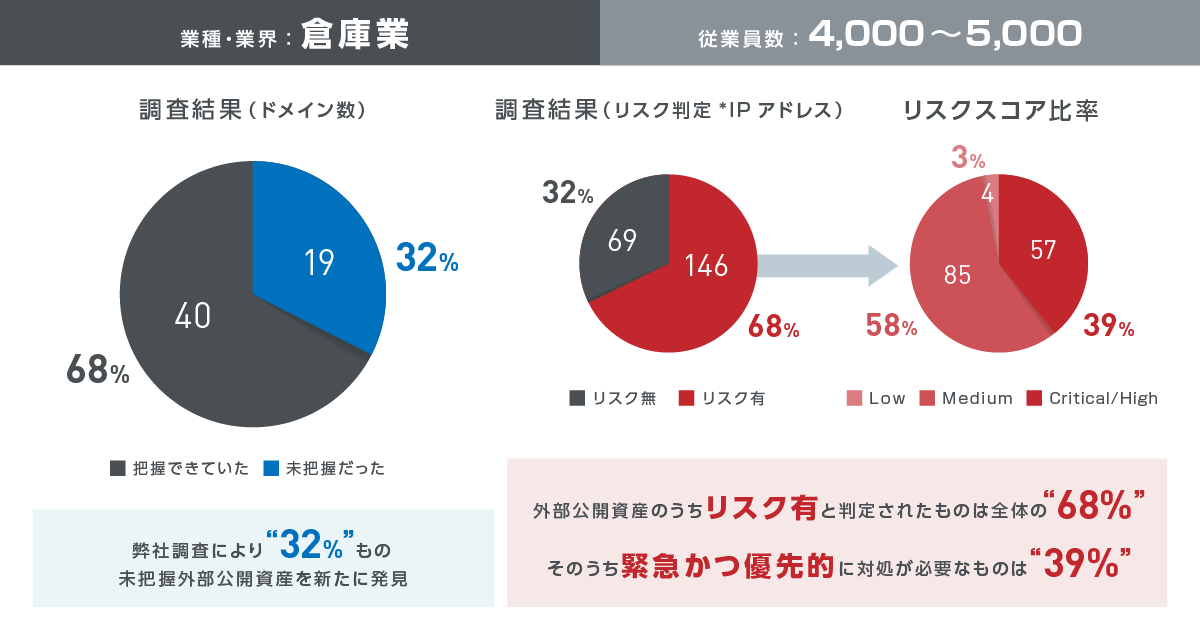
Customer survey case of introducing our service①
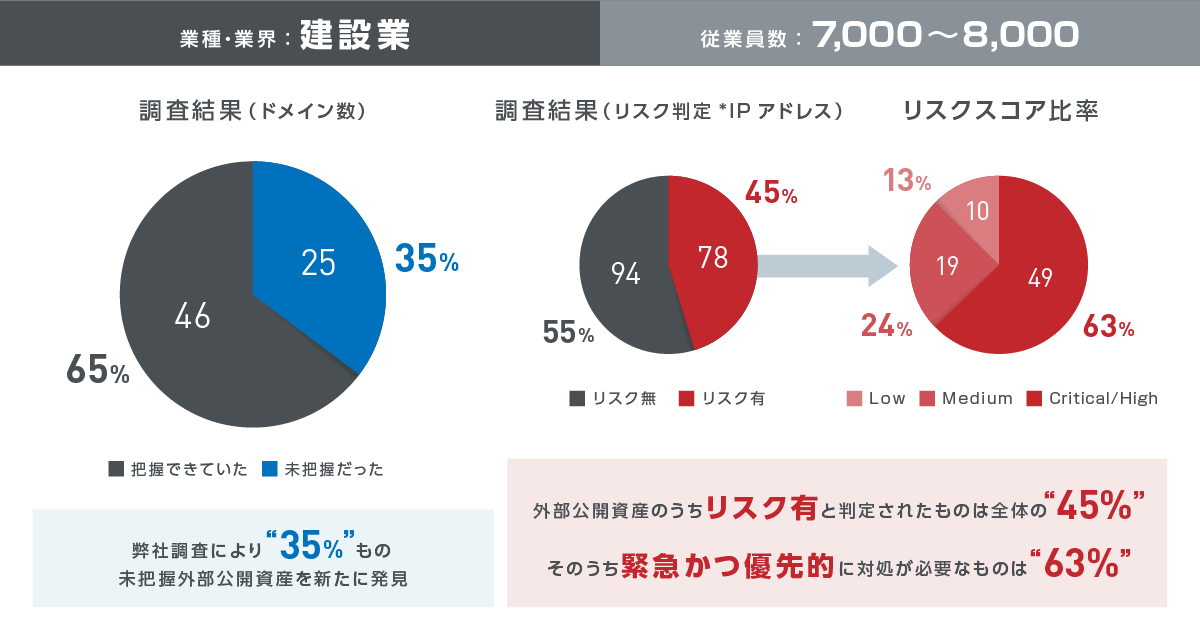
Customer survey case of introducing our service②
Inquiry/Document request
In charge of Macnica Security Service Co., Ltd.
- TEL:045-476-2010
- E-mail:sec-service@macnica.co.jp
Mon-Fri 8:45-17:30


