Mpression Cyber Security Service™
Mpression Cyber Security Service™
Threat Hunting & Incident Response Service
Mpression Cyber Security Service™
A cloud-based security service in which analysts investigate and support total detection, investigation, response, and prevention.
Over the past few years, we've observed sophisticated attacks slipping past our sensors. These threats are difficult to detect, and even if you can spot them, you need analysis that requires expertise to deal with them appropriately and take countermeasures against similar threats.
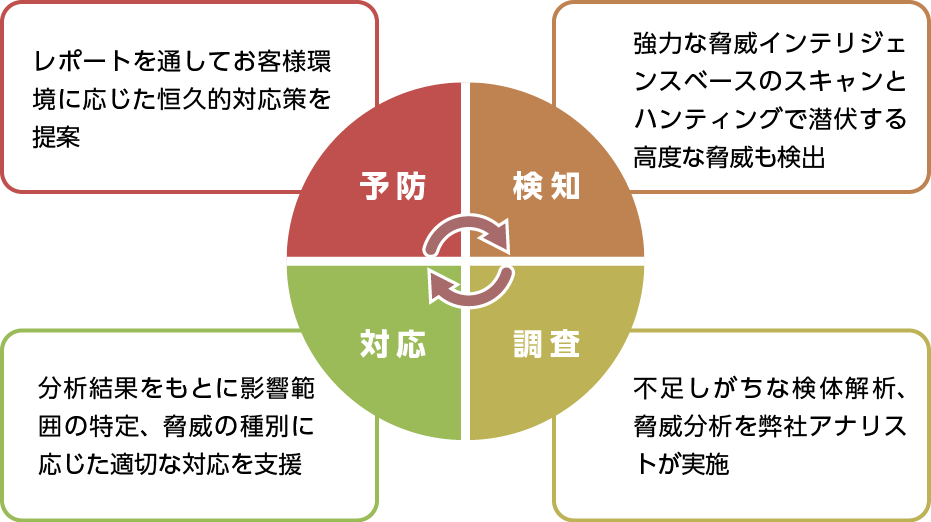
This service provides a total of endpoint investigation tools, monitoring services during normal times, investigation services when incidents occur, and reports on investigation results and countermeasures. It improves the ability to detect advanced attacks during the detection phase, and helps ensure proper and rapid implementation during the investigation, analysis, and response phases.
Service overview
INCLUDED IN THE SERVICE PROVISION
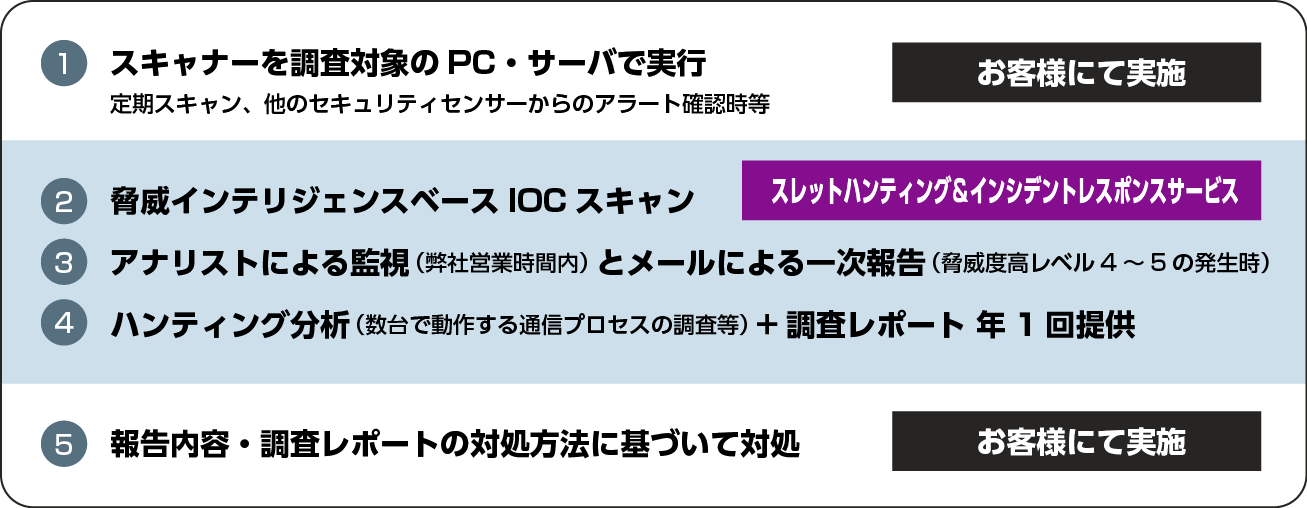
- Provision of tools for PC/server investigation (EXE file/Linux shell script)
- Accessing the cloud management console
- Monitoring by analysts (during our business hours) and primary reporting by email (when threat level 4-5 occurs)
- Hunting analysis (survey of communication processes that operate on several machines, etc.) + survey report provided once a year
* The number of times provided can be adjusted individually for an additional fee.
*The investigation report includes samples and memory collected by the investigation tool, infection timeline, analysis of lateral infection, and mid- to long-term countermeasures according to the threat level.
*The provision of survey tools only, detailed analysis of samples, the number of survey reports provided, etc. are negotiable.
Image of operation when using this service
Division of roles for investigation during normal times and incidents
Features of this service
- 強力な脅威インテリジェンスとアナリストによる徹底的な調査のハイブリットで圧倒的な検出力を実現
- Utilize the threat intelligence and investigation tools of TeamT5 which boasts overwhelming incident response of targeted attacks in Asia
*What is TeamT5 - Macnica analysts, who have investigated targeted attacks and supported numerous companies for many years, have added domestic detection rules to discover and analyze threats that have slipped through security equipment.
- You can consult with our analysts about sample analysis and containment of actual incidents, which your company tends to lack, so you can respond quickly and appropriately.
- Analysts who have provided information on malware functions, degree of danger, and related attack groups at overwhelming speed through the quick triage service to support response
- Accurately analyze the situation and take appropriate measures such as the timing of extermination, the scope of investigation, and necessary system setting changes to prevent the same threat from being exposed again.
- Comprehensive support for the defense life cycle without in-house equipment
- Provides survey tools, cloud management console
- Supports all phases of the defense lifecycle (detection, investigation, response, prevention)
Leverage the unique intelligence of TEAM T5 and Macnica

A security vendor that provides analysis and solutions for cyber threats headquartered in Taiwan. We have expanded our business not only in Taiwan, but also in the United States, Japan, and South Korea. He started his business with cyber threat research and has been providing cyber threat intelligence for over 5 years. Compared to other threat intelligence vendors, it has particularly strong intelligence against attacker groups operating in Asia. Utilizing cyber espionage's knowledge of attackers and advanced intelligence, we are developing methods to deal with targeted attacks.
Macnica Threat Intelligence
Macnica ’s threat intelligence efforts
For many years, we have supported Japanese companies as an agent for overseas security vendors. Through the provision and support of security solutions, we have received numerous consultations on specimens and incidents from customers. While investigating these specimens, we observed specimens used only in Japan that landed in Japanese organizations. Under these circumstances, we feel the need not only to provide support through support, but also to disseminate threat information and provide IOCs, and provide our own threat intelligence.
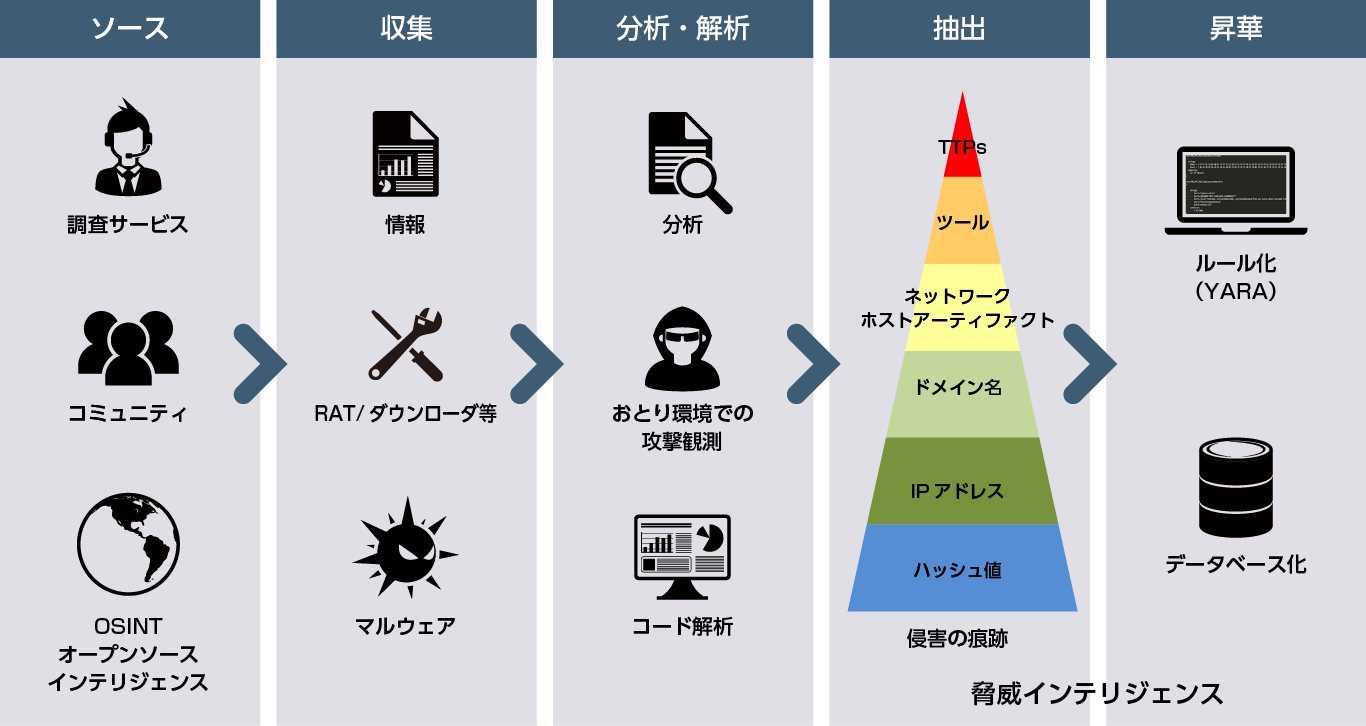
Generating IOCs with Threat Intelligence
Analyze samples used in attacks and generate IOCs by focusing on memory code and behavior (files, registries, communication destinations) that are difficult for attackers to change. It is possible to conduct investigations to detect relevant targeted attacks and identify the extent of their impact.
In addition to this service, our company offers a wide range of services from assessment/consulting of the customer's security system to comprehensive monitoring of various devices including EDR, servers, and NW equipment, to response support in the event of a serious incident. We can help you. Please refer to each service page for details.
Inquiry/Document request
In charge of Macnica Security Service Co., Ltd.
- TEL:045-476-2010
- E-mail:sec-service@macnica.co.jp
Mon-Fri 8:45-17:30