product
- What you can do with CrowdStrike
- CrowdStrike Modules Falcon
- Falcon Prevent(NGAV)
- Falcon Insight(EDR)
- Falcon OverWatch (Threat Hunting)
- Falcon Discover (IT Asset Management)
- Falcon Spotlight (vulnerability management)
- Falcon Adversary Intelligence
- Falcon Identity Threat Protection/Detection
- Falcon Cloud Security(CNAPP)
- Falcon Surface(EASM)
- Falcon Shield(SSPM)
- Falcon Next-Gen SIEM
service
Application for evaluation machine
- FAQ

CrowdStrike
CrowdStrike
Key features that represent CrowdStrike
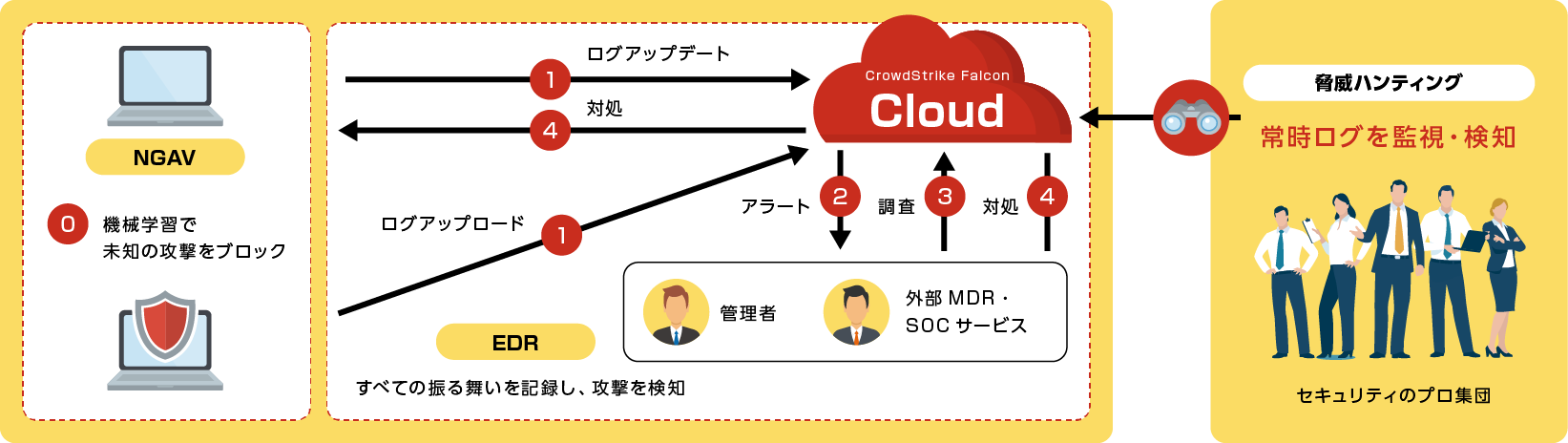
【NGAV】Falcon Prevent / Falcon USB Device Control / Falcon Firewall Management
By combining machine learning, AI, behavior detection, etc., it detects and blocks unknown attacks that cannot be detected by conventional antivirus.
- Block fileless attacks
- Detect and block even offline
- Easy process tree
[Point] Thorough cause investigation is possible with detailed logs
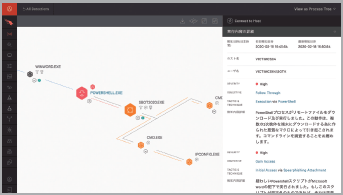
CrowdStrike Falcon provides a screen that allows you to check the operation and behavior in a flow based on detailed logs. You can quickly find out when, where, and what happened without having to worry about "running out of logs and not knowing the cause".
【EDR】Falcon Insight
Detect attacks that slip through NGAV by monitoring actual behavior based on logs. All logs are uploaded to the cloud, so even if the logs in the device are deleted by an attacker, they can be investigated.
- Real-time raw log visualization
- Integrity that attackers cannot delete logs
- It is also possible to isolate terminals remotely
[Threat Hunting] Falcon Overwatch
- Detecting everything... Too many alerts increase the operational burden
- If you give up on detection, the risk of not noticing the intrusion of threats increases.
Pinpoint detection of attacks and threats through human monitoring
- File-based detection
- Behavior-based detection
- Threat hunting detects attacks that slip through NGAV/EDR
Windows standard commands used in daily work are also checked by human eyes.
[MDR Service] Falcon Complete
The MDR service “Falcon Complete” provided by CwordStrike is a 24/365 MDR service. The Falcon Complete team carries out the entire management, prevention, monitoring and response process for you.
Click here for product details
Diverse lineup of functions
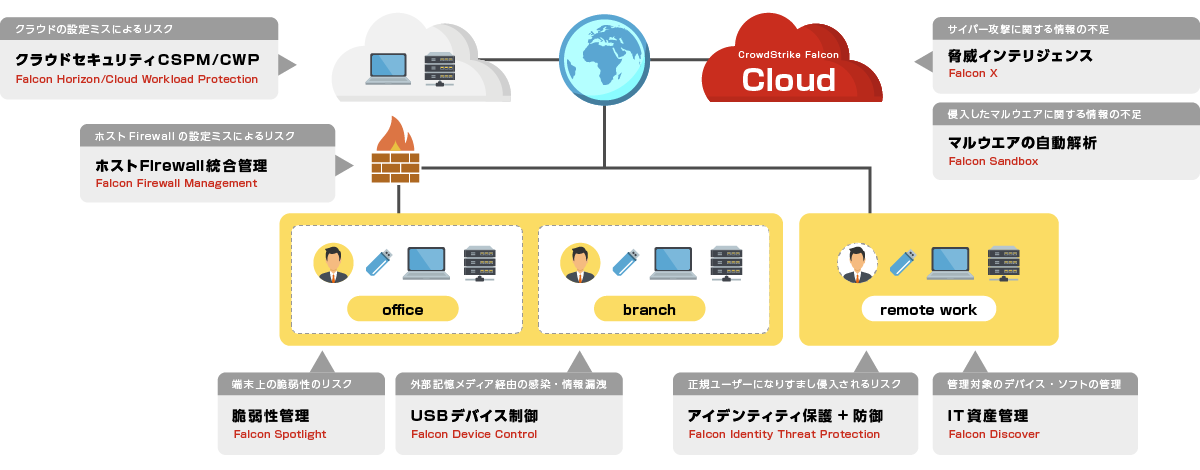
[Cloud Security (CNAPP)] Falcon Horizon/Cloud Workload Protection
Horizon assesses cloud service configurations and activities to identify potential misconfigurations (IOMs) and suspicious behavior/attack patterns (IOAs). Cloud Workload Protection provides visibility into data related to instances/virtual machines (VMs) and containers in multi-cloud and hybrid environments.
[Host Firewall Integrated Management] Falcon Firewall Management
Manage Windows Firewall functionality on Falcon. Visualize and control communications that match pre-created rules. Firewall policies can be set/applied for each host group.
[Threat Intelligence] Falcon Adversary Intelligence
Ability to profile cyber attackers, provide information and reports on attack operations, and query the IOC's database. By deploying it in-house, you can enhance security.
[Automatic Malware Analysis] Falcon Sandbox
Analyze the malware found in the company in the Box and acquire IOC information such as URL and Hash value. Regardless of malignancy judgment, a report of the analyzed sample is generated after analysis, and can be viewed and obtained.
Falcon Sandbox
[Vulnerability Management] Falcon Spotlight
Collects and visualizes vulnerabilities in OS and third-party applications. By utilizing logs from the Falcon agent, visualization is possible in real time. By quickly detecting vulnerabilities and applying patches, attacks that exploit vulnerabilities can be prevented.
[USB device control] Falcon Device Control
Visualize and control USB device usage status for terminals with Falcon agent installed. Get real-time logs of who, when, and what device was used. Policies such as usage prohibition can also be set collectively.
【SSPM】Faicon Shield
It enables cross-sectional risk management of SaaS used by various business divisions, and realizes best practices that reflect the latest state of SaaS, security frameworks, etc. As part of your current security operations, you can manage SaaS governance with minimal additional effort.
Click here for product details
[ID Protection (ITD/ITP)] Falcon Identity Threat Protection/Detection
Conduct a risk assessment regarding IDs and check the internal environment. Get real-time alerts when identity-based incidents occur. By setting your own policy, you can perform actions such as authentication block and MFA symbiosis in real time.
[IT Asset Management] Falcon Discover
Visualize the status of internal IT assets from the three perspectives of applications, terminals, and accounts. Gain real-time visibility into unmanaged devices and application usage, versions, and endpoint environments.
External institution evaluation
System requirements, OS
It supports Windows, macOS, Linux (including Amazon Linux), iOS, and Android operating systems.
Please contact us for details on supported versions for each OS.
Inquiry/Document request
In charge of Macnica CrowdStrike Co., Ltd.
- TEL:045-476-2010
- E-mail:crowdstrike_info@macnica.co.jp
Weekdays: 9:00-17:00
![Security Professional Group [Threat Hunting] Falcon Overwatch](/business/security/manufacturers/crowdstrike/image/crowdstlike_pro_falcon_dr03.png)
