
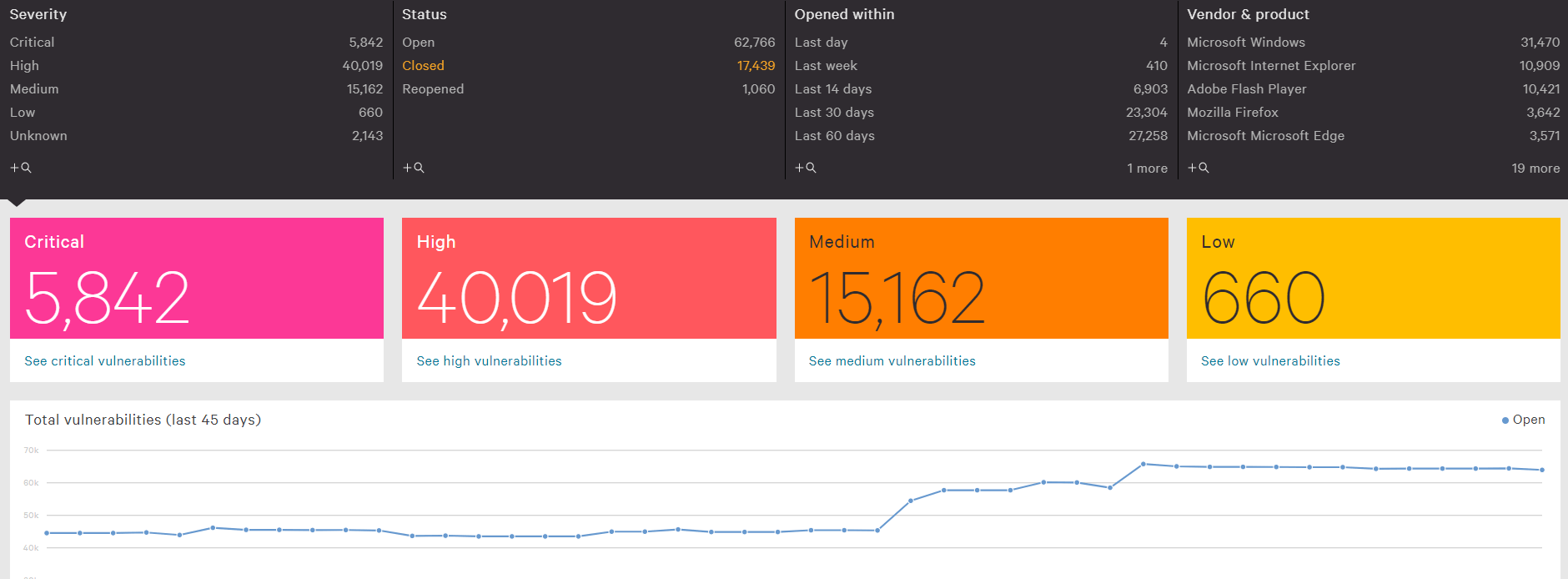
CrowdStrike
クラウドストライク
CrowdStrikeが提供する各ソリューション
担当者を悩ませる企業にIT環境を取り巻く諸課題
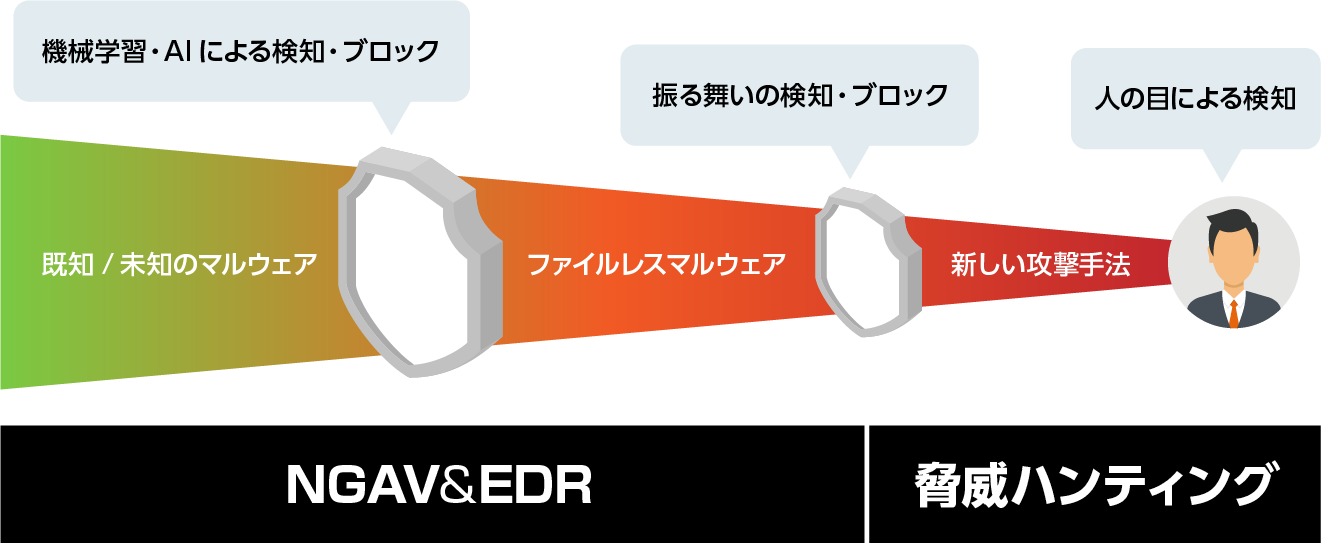
CrowdStrikeFalconは機械学習・AI・振る舞い・人の目で検知を行うため、既知/未知のマルウェアだけでなく従来型アンチウイルス製品などで検知することが難しいファイルレスマルウェアなどの高度な攻撃まで検出可能。
CrowdStrike FalconのOverWatchは24時間365日専門家がお客様の環境を監視し、機械で見つけられない高度な脅威の検知だけでなく、影響範囲の調査や対処方法のアドバイスを実施。時間を問わない監視体制のため、業務時間外に着弾した脅威も検出可能。
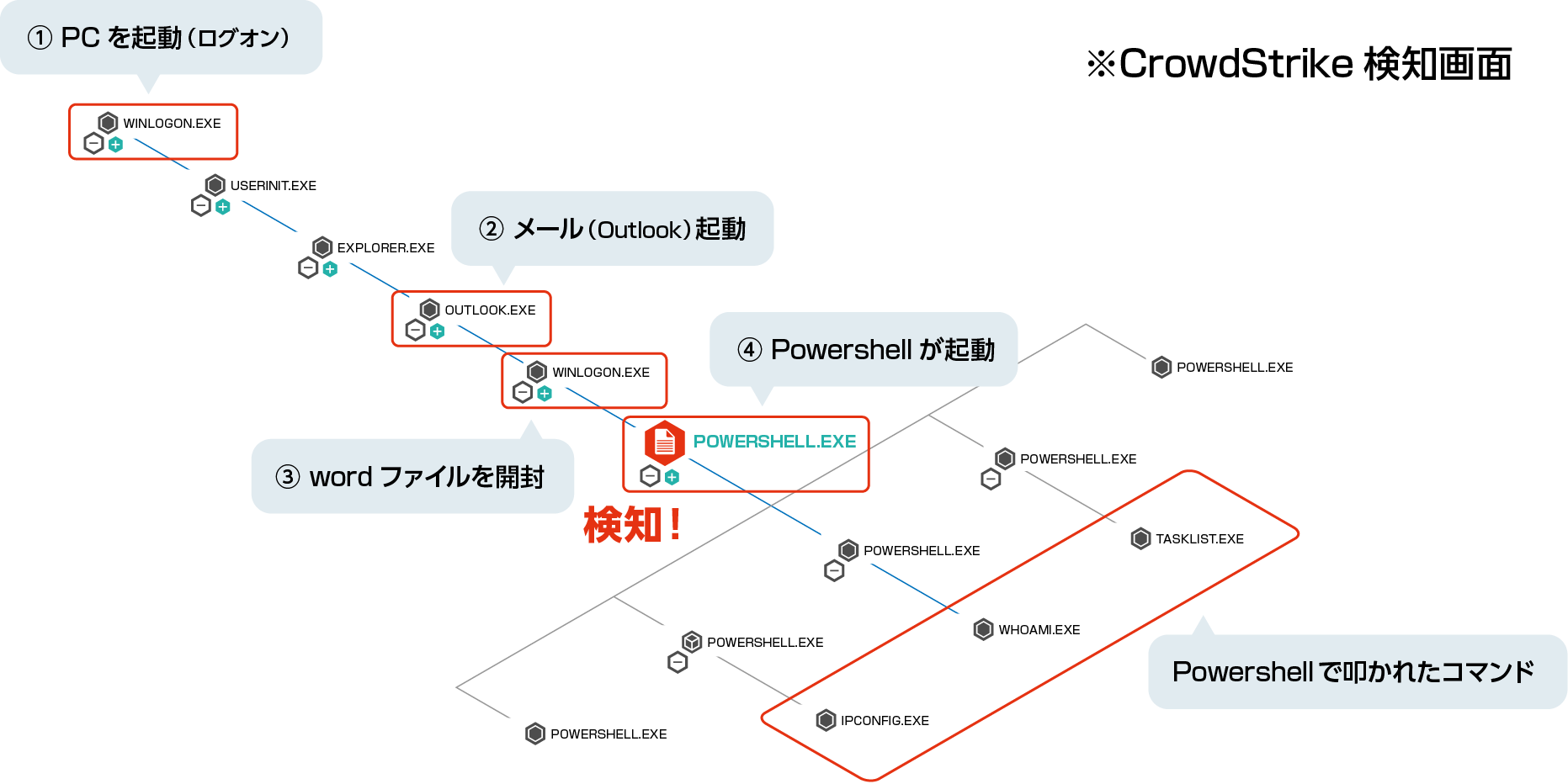
CrowdStrike Falconはリアルタイムにログをクラウド上に記録するため、攻撃者が端末から痕跡を削除した場合でも侵入経路などのインシデントの詳細を調査することが可能。プロセスアクティビティ―を時系列に沿って視覚的に表示するため、インシデント状況も容易に把握。
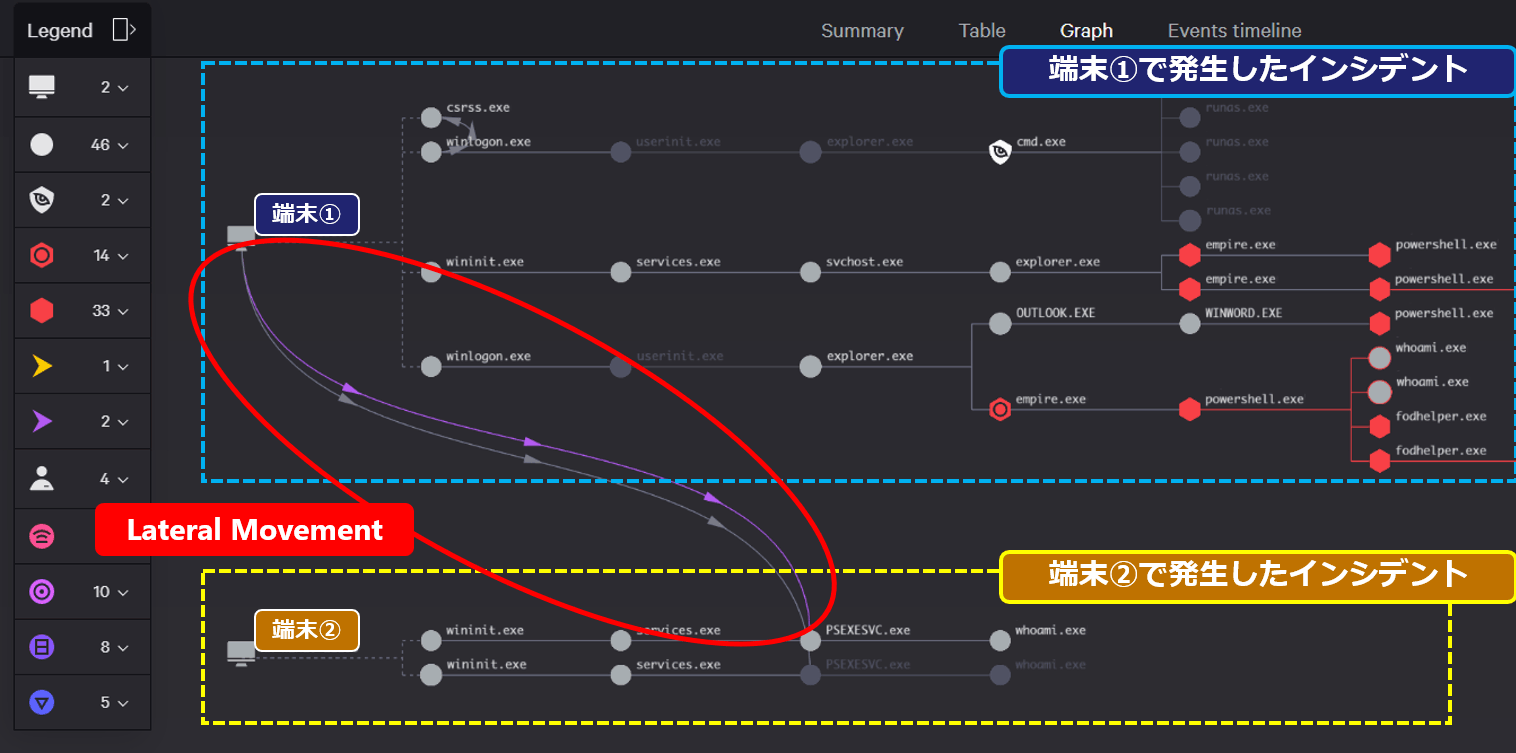
CrowdStrike Falconではアラート単位での調査のみならず、アラートを集約しインシデント単位での調査も可能なため、アラートは10倍以上削減されて表示可能となり、運用負荷も軽減。 さらには、端末から端末への横展開状況も把握可能。
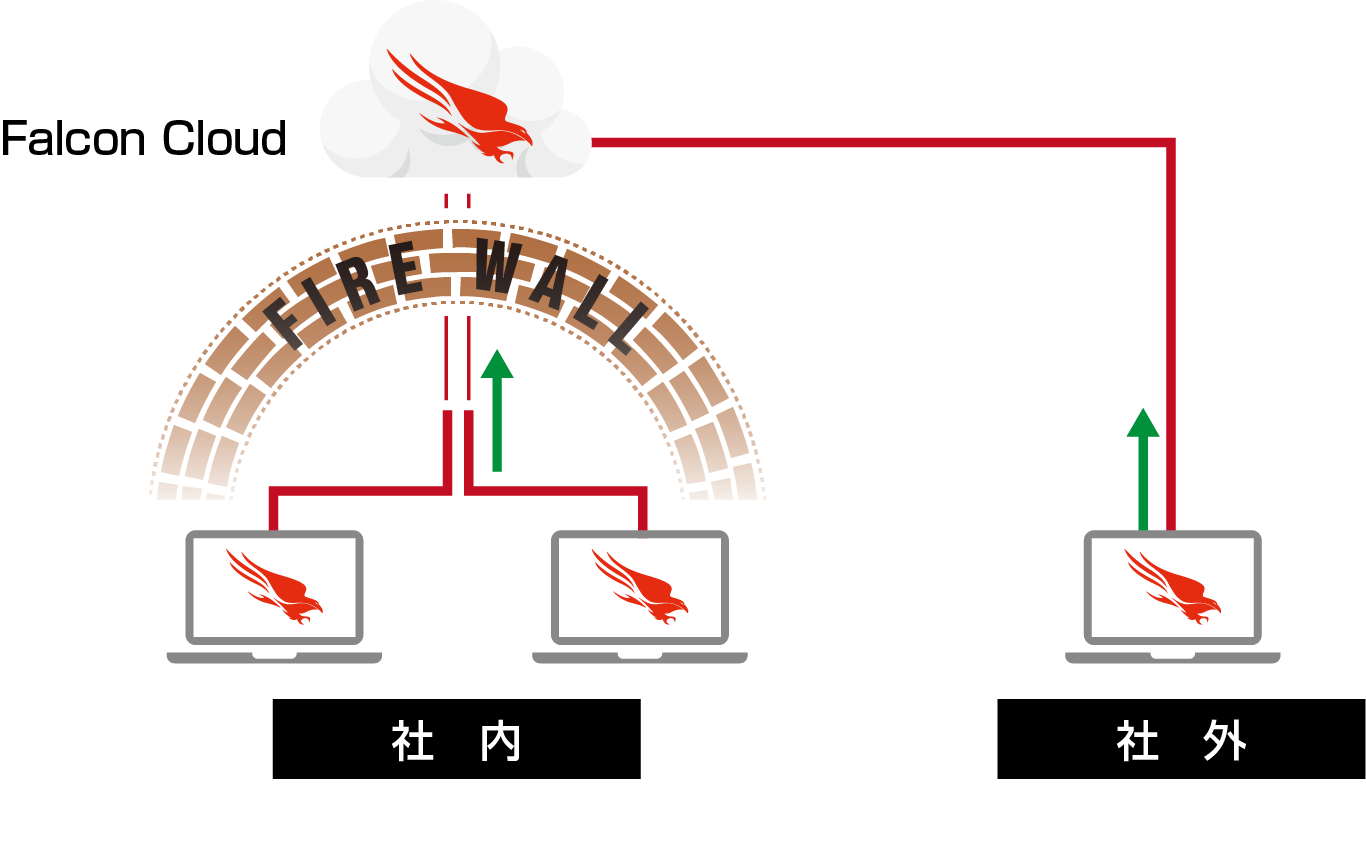
CrowdStrike FalconはSaaS型のアプローチを取っている為、端末のロケーションに依存せず、ネットワークにさえ繋がっていればリアルタイムにログをクラウド上に記録。リアルタイムに検知・ブロックも実施するため、社外の端末においても脅威の確実な防御が可能。
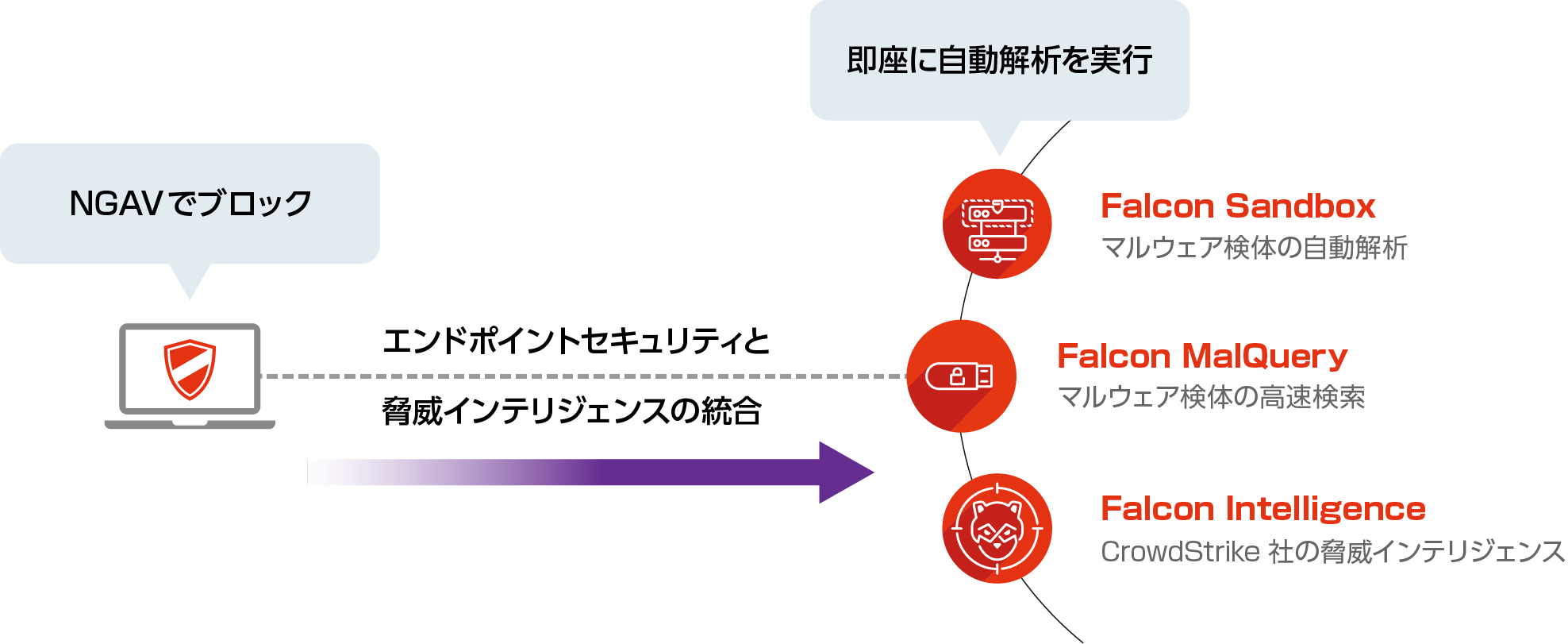
Falcon Preventで検知した攻撃を確実にブロック(ファイル隔離・プロセスの停止等)し、Falcon Adversary Intelligenceに自動連携することで即時の攻撃に利用されたファイルの挙動解析、攻撃者の特定、関連性のあるマルウェアの有無の確認を実行するため、対処の時間の大幅削減を実現。
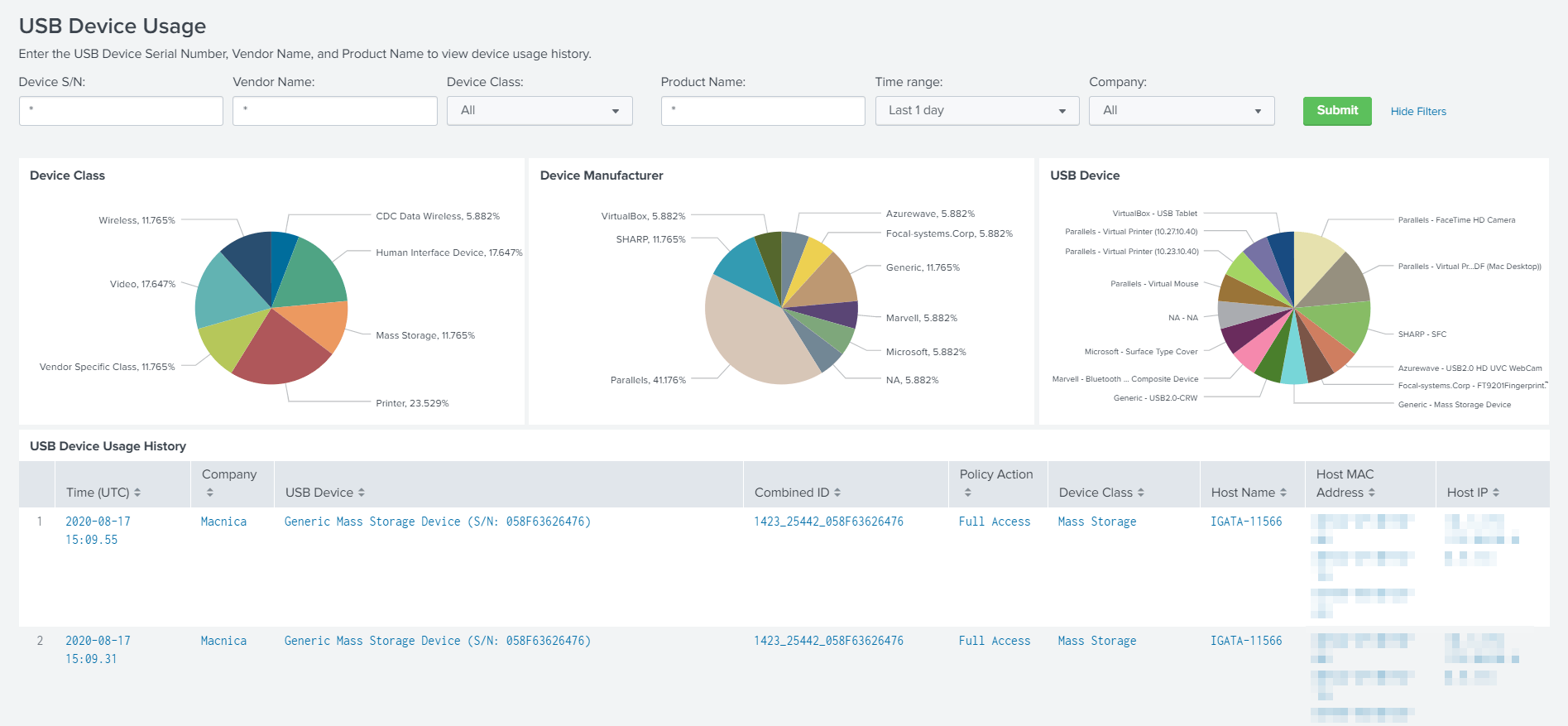
Falcon USB Device Controlでは利用されているデバイスクラス(種別)や、メーカ、デバイスの傾向を可視化可能。また、ポリシー指定により、USBデバイス制御が可能(グループ毎に分ける事も可能)であり、ポリシによってブロックされた場合も、どのUSBデバイスが、いつ、どの端末によって利用が施行されたか確認可能。
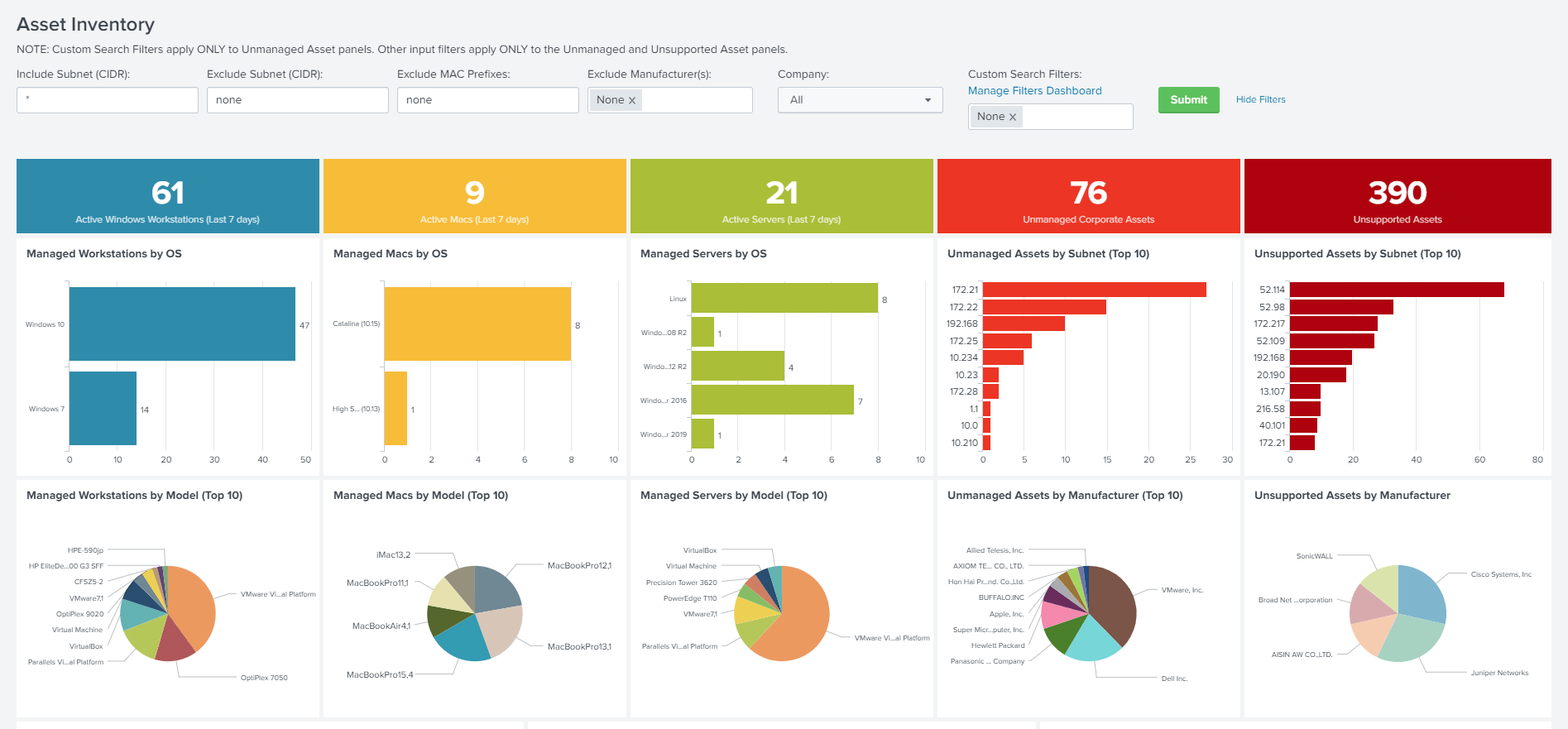
Falcon Discoverのアセット管理の機能では、Falconがインストールされている端末/サーバがどのようなアセットで利用されているかを可視化するだけでなく、Falconがインストールされていない端末の情報も可視化可能なため、非管理端末を見つけることが可能。
Falcon Discoverのアプリーション可視化の機能では、各端末にインストールされているアプリケーションおよびバージョンを可視化するため、アプリケーションの脆弱性が発表された際に、どの端末に脆弱性が存在しているか調査することが可能。またSpotlightでは端末に存在する脆弱性(CVE)や未適用KBを自動的に収集し可視化するため、リアルタイムでの脆弱性可視化が可能。
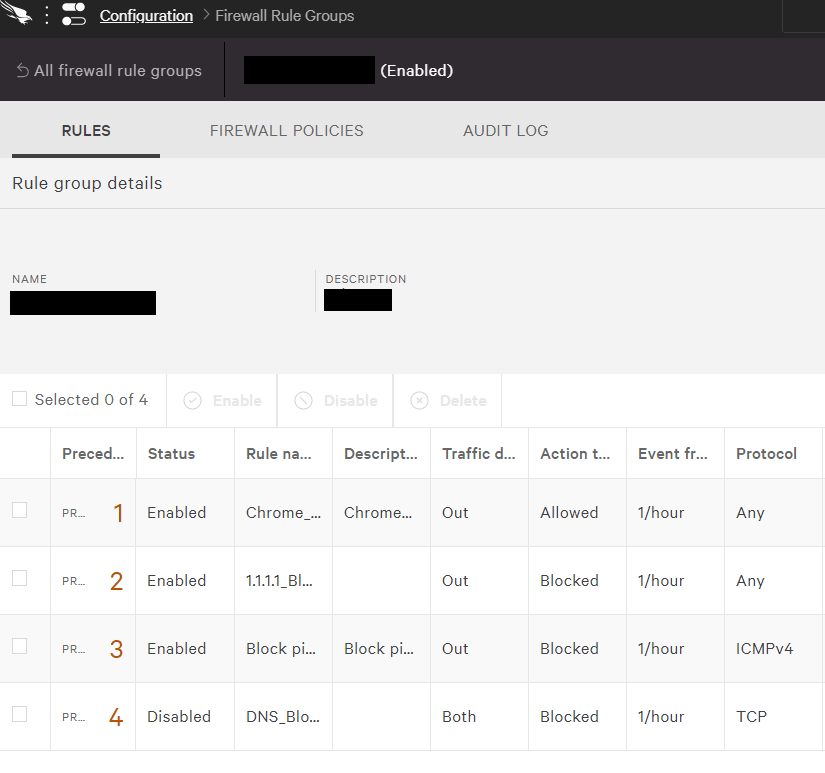
Windows OS標準のFirewallをFalconの管理コンソールより管理することが可能。Falconのエージェントを介してFirewallポリシーを設定することで、環境全体へ迅速なルール適用を実現。
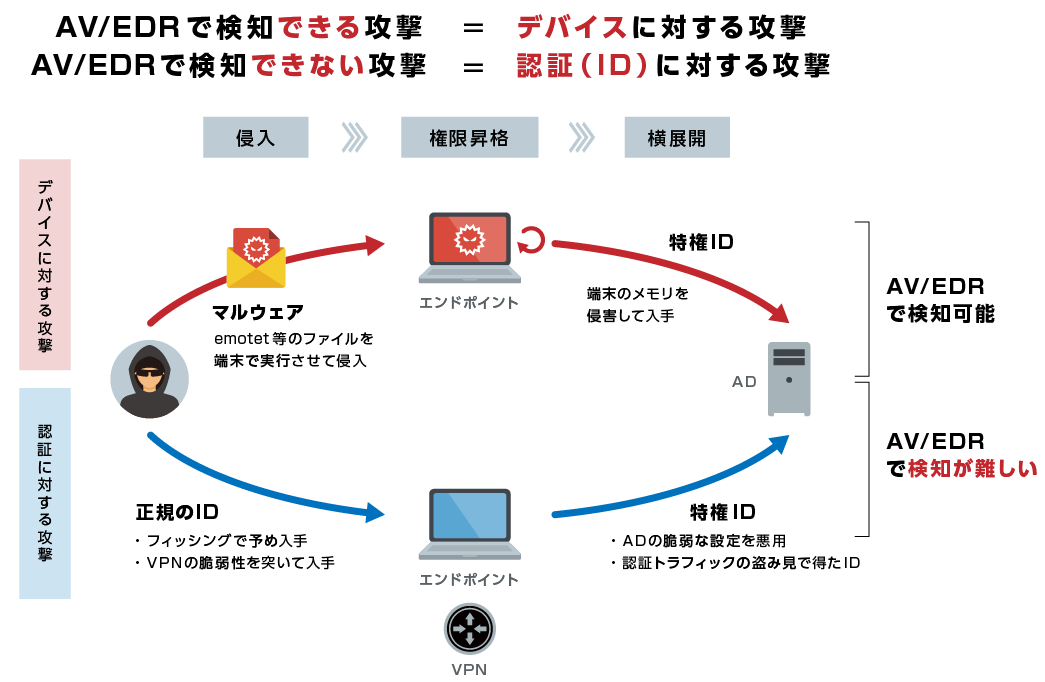
Falcon Identity Threat Protection/Detectionは導入環境上における認証トラフィックを学習することで、従来のAV/EDRでは検知/ブロックが困難である認証(ID)に対する攻撃に対して検知/ブロックが可能。
Falcon Cloud Securityではクラウドサービスの設定ミスの可視化やクラウドワークロードとコンテナ、Kubernetesアプリケーションの保護を実現します。
1つのモジュールで以下3つの機能を提供します。
クラウドサービスの設定ミス(IOM)や疑わしい動作/攻撃(IOA)の特定、
コンプライアンス準拠状況の確認が可能です。

クラウドサービス上のIDに紐づけられた権限を可視化し、管理します。
過度な権限が付与されたIDを洗い出し、適切な権限運用に役立ちます。
クラウドワークロード、コンテナ、Kubernetes環境の
可視化と脅威からの保護を提供します。
Falcon Surfaceでは外部に公開されている自社のIT資産およびそれらの持つリスク、脆弱性の可視化を実現し、お客様のIT運用、セキュリティ対策をお助けします。

- インターネットに公開された全ての資産を監視
- 環境全体のスコアリングおよび優先的に対策が必要な資産の特定

- 脆弱なサーバやNW機器の脆弱性の特定・可視化
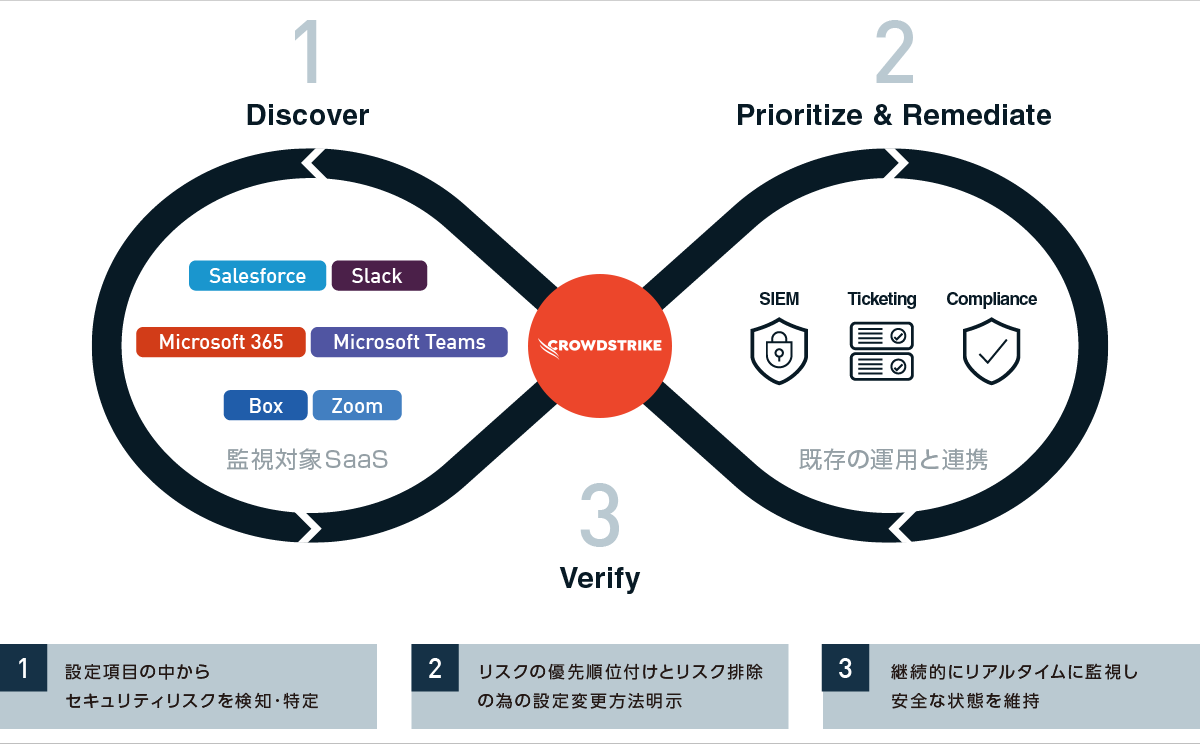
Falcon ShieldはSaaSの設定監査を行うSSPMソリューション(SaaS Security Posture Management)です。SaaSの安全な利活用のために、主にセキュリティ設定や各種コンプライアンスに対する準拠有無に対して、継続的にチェックする機能を提供します。
様々な事業部で使われているSaaSの横断的なリスク管理ができ、SaaSやセキュリティフレームワーク等の最新状態が反映されたベストプラクティスを実現。今のセキュリティ業務の一環として、最小の追加工数でSaaSのガバナンス管理が可能です。
お問い合わせ・資料請求
株式会社マクニカ CrowdStrike 担当
- TEL:045-476-2010
- E-mail:crowdstrike_info@macnica.co.jp
平日 9:00~17:00