
CrowdStrike
クラウドストライク
IDプロテクション(ITD/ITP)
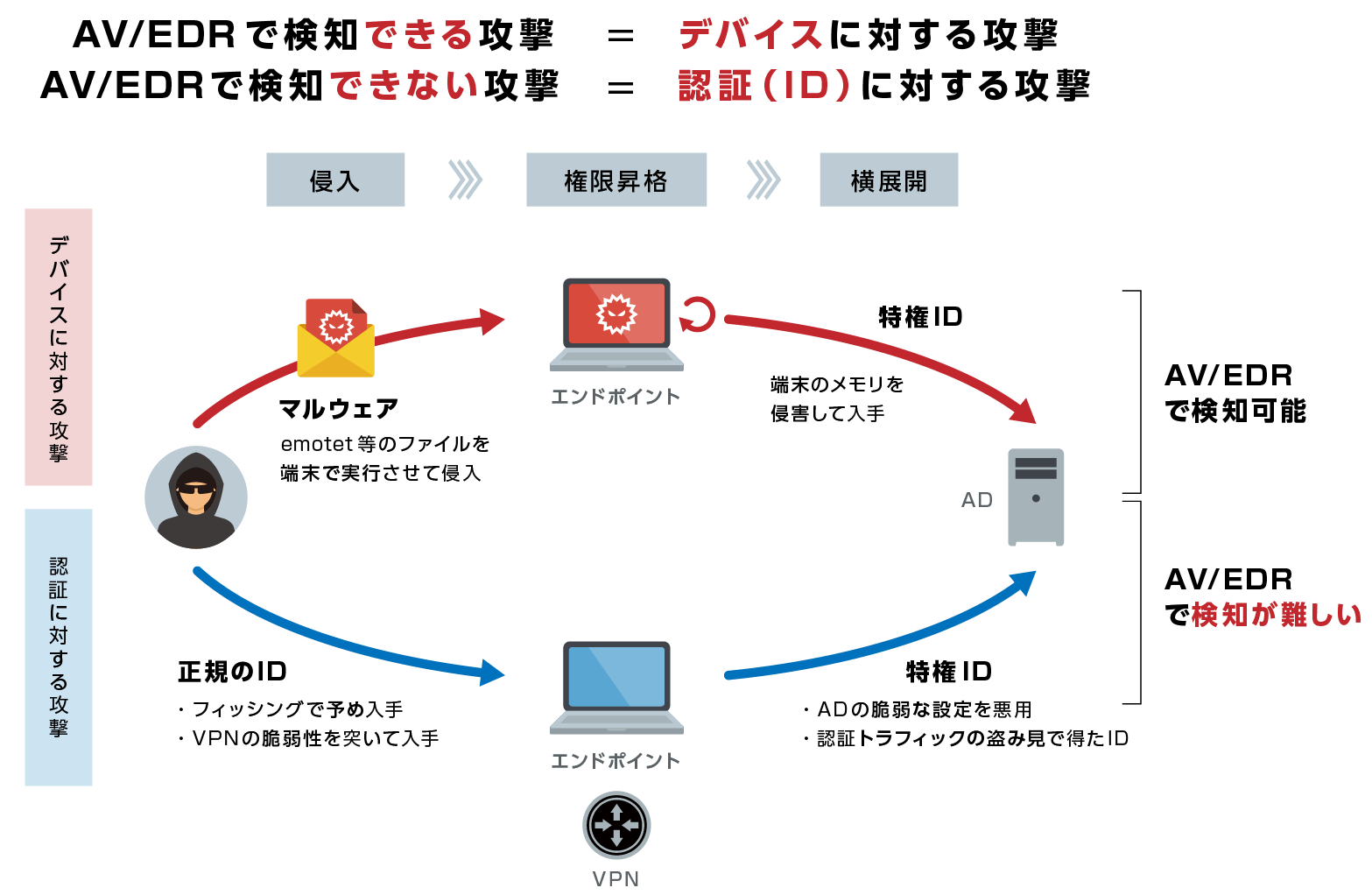
Falcon Identity Threat Protection/Detectionは従来のAV/EDRでは検知/ブロックが困難である認証(ID)に対する攻撃に対して検知/ブロックが可能なソリューションです。
導入環境上における認証トラフィックを学習することで、正規クレデンシャルを元にした認証動作に対しても当該認証行為の異常性を評価(例:認証元が国外等いつもとは違う送信元である場合/本来ADへ認証試行が走るはずのない送信元IPからのアクセスが発生する場合)し、アラートを上げるという考え方でございます。
大きく「アセスメント」、「インシデント検知」、「条件付きアクセス」の三つの機能を有します。
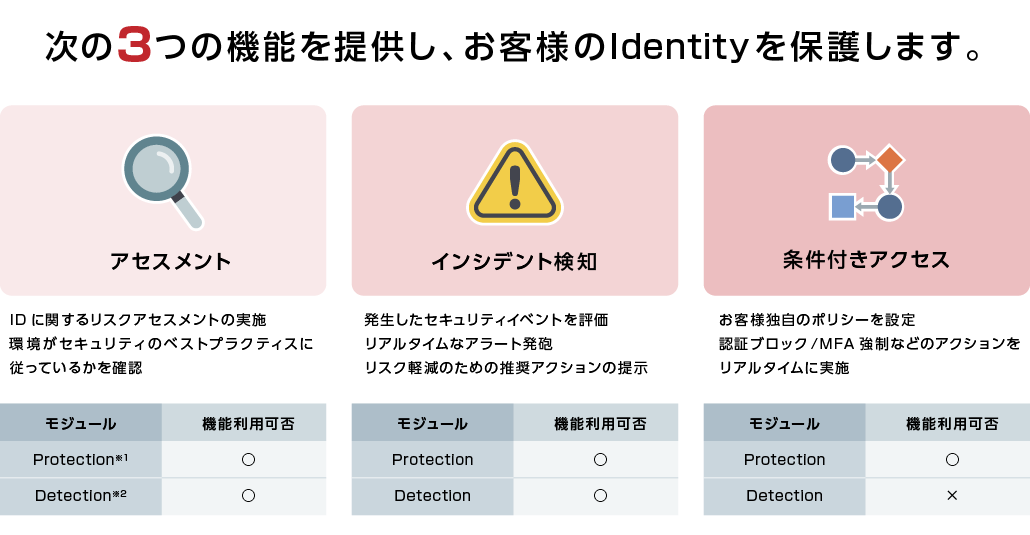
※1 Falcon Identity Threat Protection機能を指します。
※2 Falcon Identity Threat Detection機能を指します。
従来と昨今の組織侵入型のサイバー攻撃の特徴として、それぞれ下記に整理をします。
- 【従来】
端末上でのマルウェア実行やクレデンシャルダンプにより認証情報を抜き取り横展開が進むが、デバイス上で攻撃が実施されるため、AV/EDRで検知/防御が可能。 - 【昨今】
正規クレデンシャルベースで横展開が進むが、あくまでも認証動作であるためエンドポイント上での検知が難しく、AV/EDRでの検知/防御が困難。
標的型攻撃等攻撃者による攻撃手法の高度が進んでいる昨今、正規クレデンシャルベースで攻撃が進行する「認証」に対する攻撃についても防御/検知/対応を行うための仕組みが必要です。
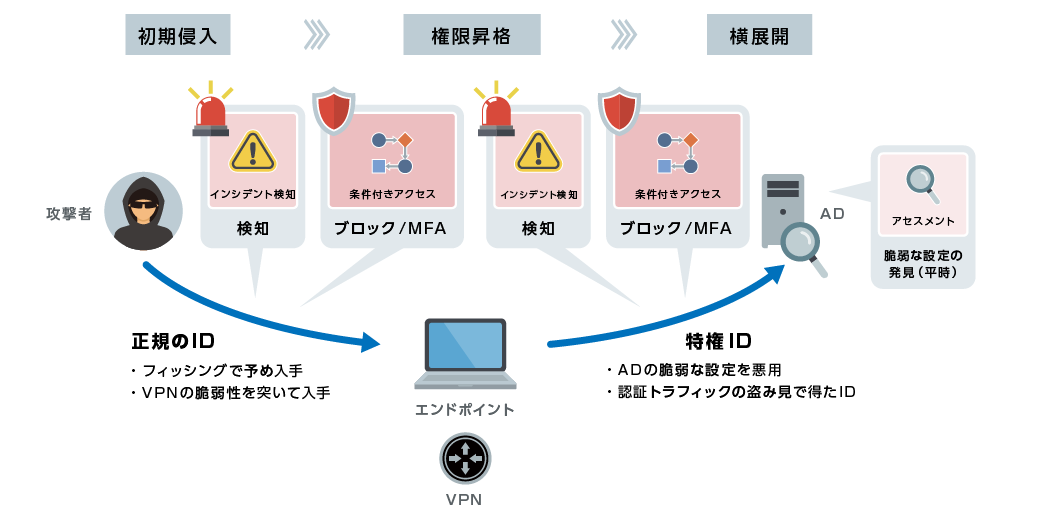
Falcon Identity Threat Protection/Detectionを導入することで、「認証」に対する攻撃についても防御/検知/対応を行うことが可能です。
初期侵入から横展開までの各段階ごとに正規クレデンシャルベースの攻撃であっても適切な検知/ブロックが可能です。
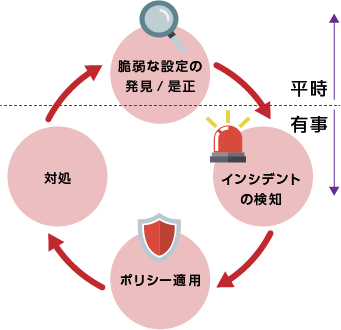
また平時における未然防止の観点においてもADサーバーの脆弱な設定等お客様のセキュリティ環境がベストプラクティスに従っているかをアセスメントし、脆弱なリスク箇所について可視化する「アセスメント」機能を活用することで未然防止のための調査が可能となります。
攻撃が発生時のITDRでの対処イメージ
お問い合わせ・資料請求
株式会社マクニカ CrowdStrike 担当
- TEL:045-476-2010
- E-mail:crowdstrike_info@macnica.co.jp
平日 9:00~17:00