
CrowdStrike
クラウドストライク
Falcon Prevent
- CrowdStrikeが提供するNGAV機能では、マルウェアやランサムウェアといった悪性実行ファイルのブロック/隔離のみならず、豊富な検知ロジックによる振る舞いベースでの防御機能が提供されます。
- 本機能をご利用いただくことで、既知/未知およびマルウェアの有無によらず悪性な攻撃からエンドポイントを保護します。
- 豊富な検知ロジックを有しているため、本機能をご利用いただくのみで、端末上にて多層的な防御を行うことが可能であり、最新の攻撃に対して素早い検知・ブロックを行うことができます。
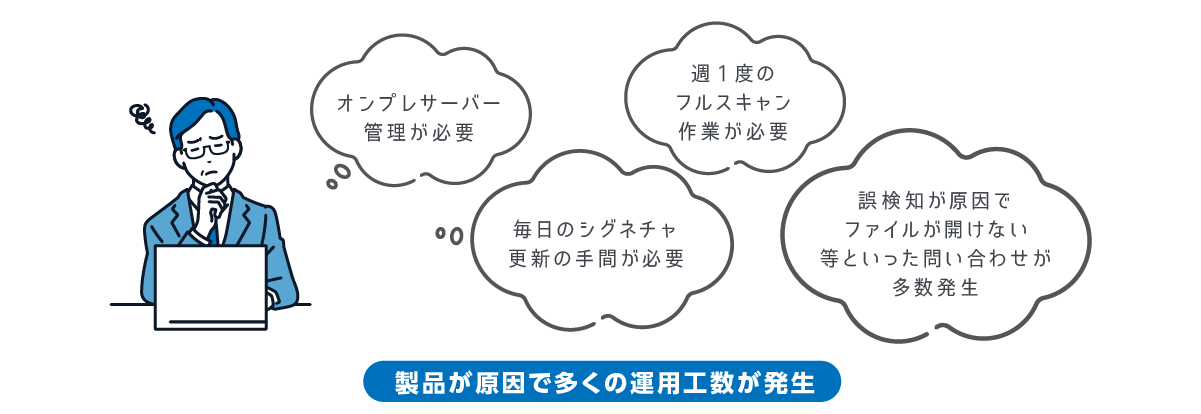
従来型アンチウイルス製品の課題
課題① 防げない攻撃の増加
従来型のアンチウイルス製品では、ウイルスパターン(シグネチャ)に一致した既知のマルウェアしか検知できず、未知のマルウェアからエンドポイントを保護することができません。
また、実行ファイルを使用しないファイルレス攻撃(OSの正規コマンドを使用した攻撃)が年々増加しています。
こういったファイルレス攻撃に関しても、従来型のアンチウイルス製品では対応できない状況です。

未知のマルウェアやファイルレス攻撃への対策が必要!
課題② ユーザーへの負荷

膨大なパターンファイル(シグネチャ)の更新、定期スキャンによるPCの負荷で業務に支障が出る
定期的なアンチウイルスソフトのアップデートによるPC負荷で業務影響が発生
アップデート後の再起動が必要になる

課題③ 運用者の負荷
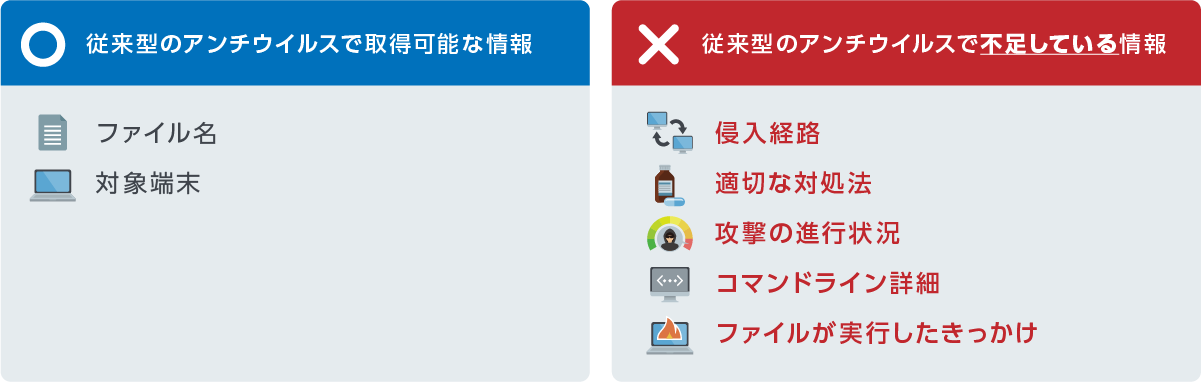

対処・再発防止に必要な情報が足りていない!
Falcon Prevent でこれらの課題を解決します!
課題①
防げない攻撃の増加
防げない攻撃の増加

機械学習/AI/振る舞い検知により未知のマルウェアやファイルレス攻撃が検知可能に
課題②
ユーザーへの負荷
ユーザーへの負荷

リアルタイムログ転送でも転送量が1日あたり5MB/台 程度と軽量なエージェントでPC環境が快適に
課題③
運用者への負荷
運用者への負荷

オンプレミスサーバ不要、パターンファイル更新不要で作業工数の軽減、侵入経路/攻撃の進行状況/コマンドライン詳細/ファイル実行したきっかけなど情報取得している為インシデント後調査が容易
Falcon Prevent の特徴
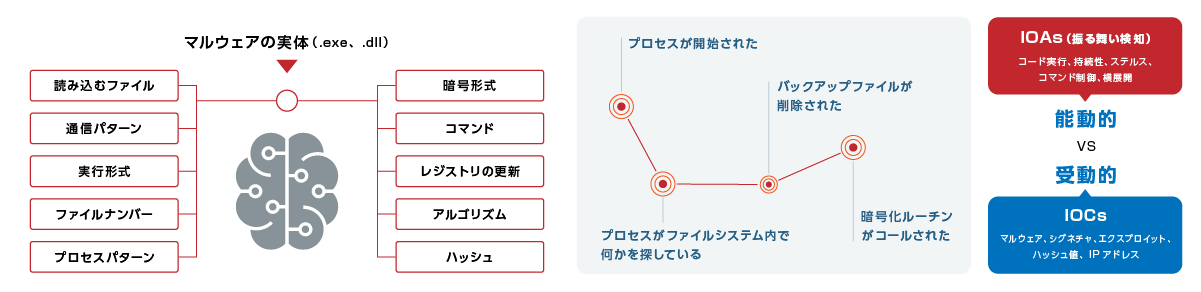
機械学習とIOA(振る舞い)検知とブロック
Preventは機械学習とIOA(つまりは振る舞い検知)による2つのアプローチで検知・ブロックするため、マルウェア、ファイルレスのどちらもブロックすることが出来ます。
また、オフライン環境でもブロックは可能なため、一時的にインターネット接続できないような状況でも動作します。
機械学習でブロックされたファイルは安全な形式で隔離されます。万が一、悪意のないファイルが検出された場合は、管理コンソールからリリースやホワイトリスト化を行うことができます。
隔離されたファイルの保存期間は30日間となり、それ以降は自動で削除されます。
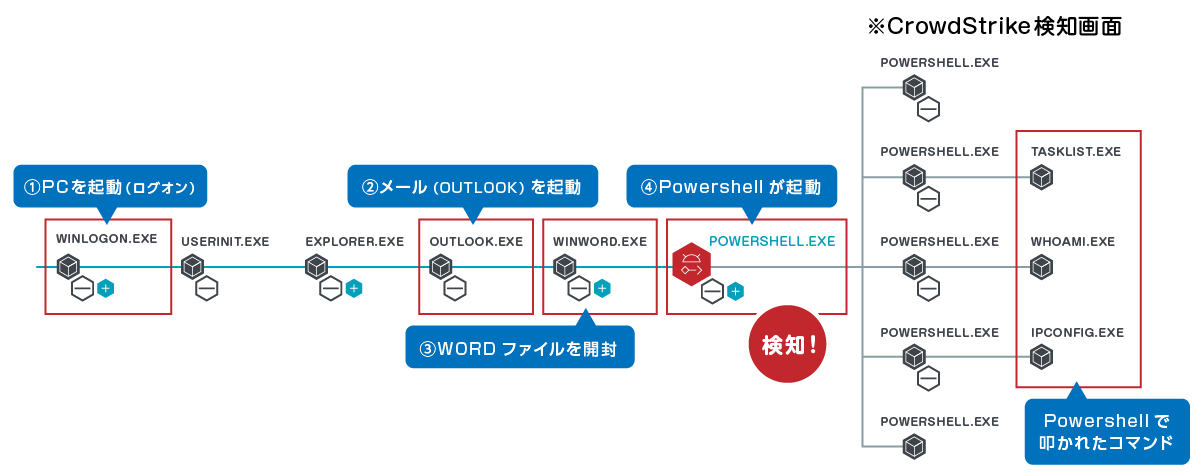
プロセスツリー表示により、直感的に何が発生したか把握可能
セキュリティ運用の自動化(SOAR機能)
GUIから簡単にワークフローが作成でき、運用の自動化を図ることが可能です。
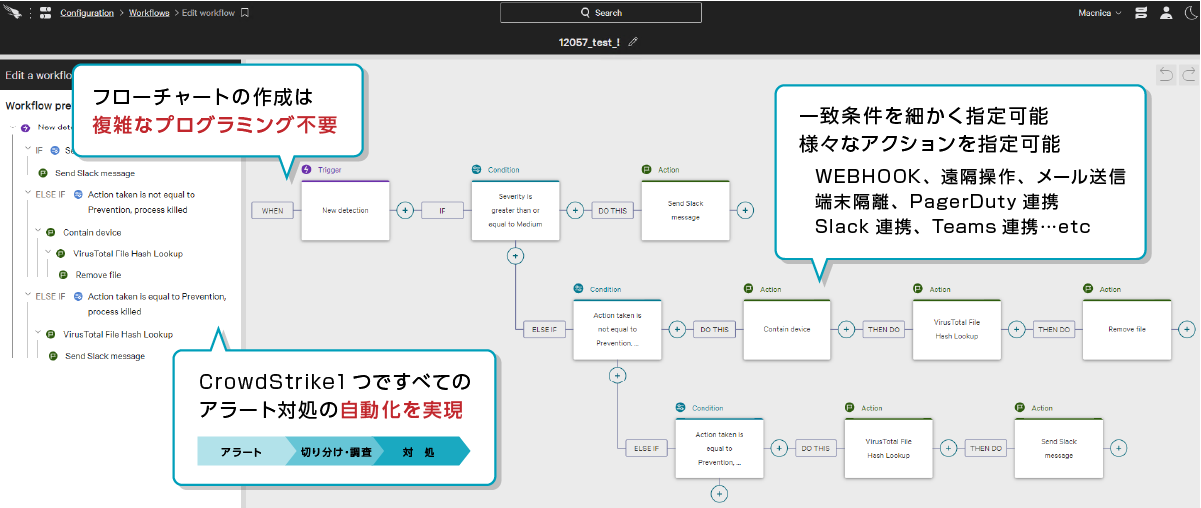
例えば以下のようなことが可能です
- 平日日中帯に重大度「クリティカル」または「高」の検知が発生した場合、決められた宛先にメールで通知
- 平日夜間帯または土日に重大度「クリティカル」の検知が発生した場合、対象端末を隔離しTeamsのチャネルに通知
統合されたプラットフォーム
- シングルコンソール
一つの管理画面で全ての機能を管理いただくことが可能です - シングルエージェント
新たなモジュールを追加購入いただいた場合でも、追加のインストールは不要です - Windows / Linux / macOSに対応
※対応バージョンはお問い合わせください
Falcon Device Control
- USB Device Control(デバイス制御)モジュール
- 本機能を利用することで、Falconをインストールしている端末に対して、USB利用状況の可視化や制御が可能となります。
・USBデバイス利用状況の可視化
・USBデバイスの利用制御 - ライセンス追加購入により、新たなセンサーのインストール不要でUSB利用に対してガバナンスが効いていない拠点への制御を行う事が可能です。
- 本機能を利用することで、Falconをインストールしている端末に対して、USB利用状況の可視化や制御が可能となります。

以下のような運用課題を解決します。

運用課題①
- そもそもUSB利用におけるガバナンスを現状取っていない為、どの程度利用されているかが分からない。
- 利用を会社指定USBのみとしているが、システム的な制御は出来ていない。その為、本当に会社指定USB以外のUSBが使われていないか可視化できていない。

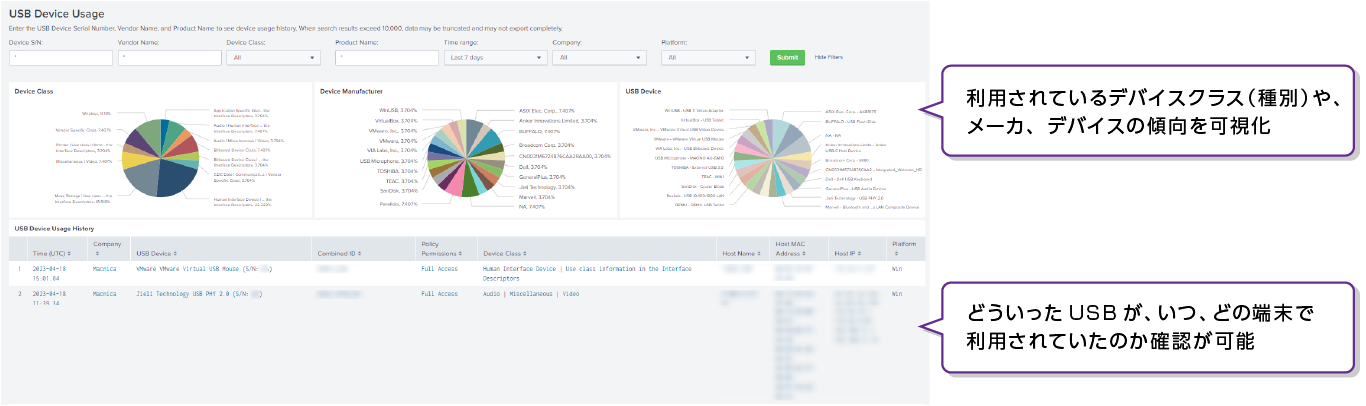
- 利用されているデバイスクラス(種別)や、メーカ、デバイスの傾向を可視化
- 対象のデバイスクラスは、大容量記憶装置をはじめ多くのクラスに対応可能
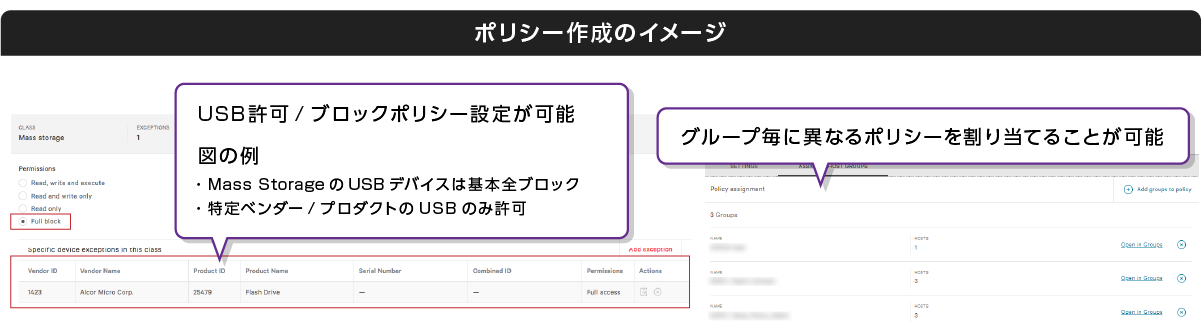
- ポリシー指定により、USBデバイス制御が可能(グループ毎に分ける事も可能)
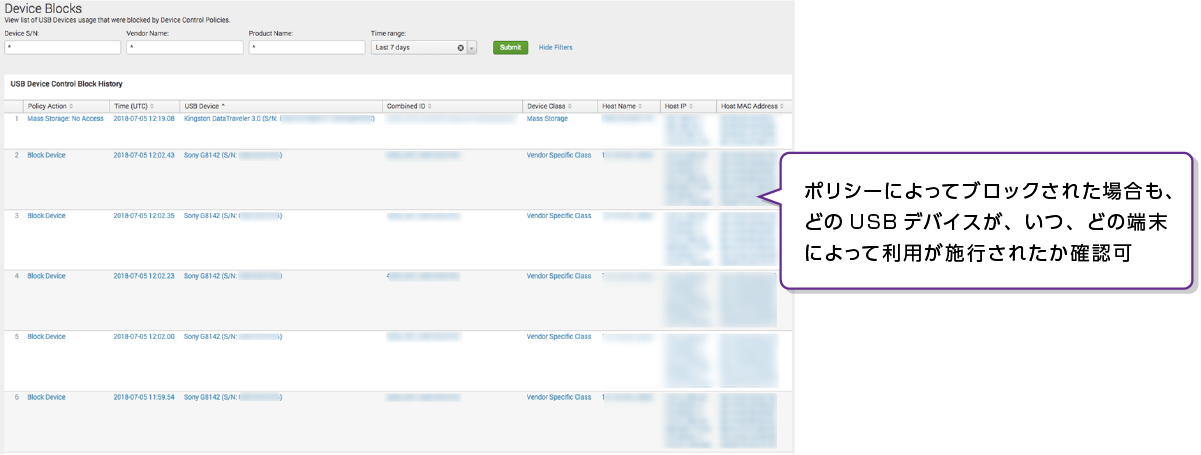
- ポリシーによってブロックされた場合も、どのUSBデバイスが、いつ、どの端末によって利用が施行されたか確認可能
- ブロック対象のUSBが差し込まれた際にポップアップメッセージも表示可能
Falconがインストールされている端末上で利用されているUSB利用状況を可視化
ポリシーを指定することでUSBデバイス制御が可能
(グループ毎に分ける事も可能)
ブロック対象のUSBが差し込まれた際にポップアップメッセージの表示も可能
ポリシーによってブロックされた、USBデバイスや端末の可視化
Falcon Firewall Management
管理コンソール上にて定義・更新頂くファイアウォールポリシーを任意のグループごとに一括適応していただけるほか、ポリシーが適応されたアクティビティをご確認頂くことにより、ポリシー最適化のための検討を頂くことが可能です。

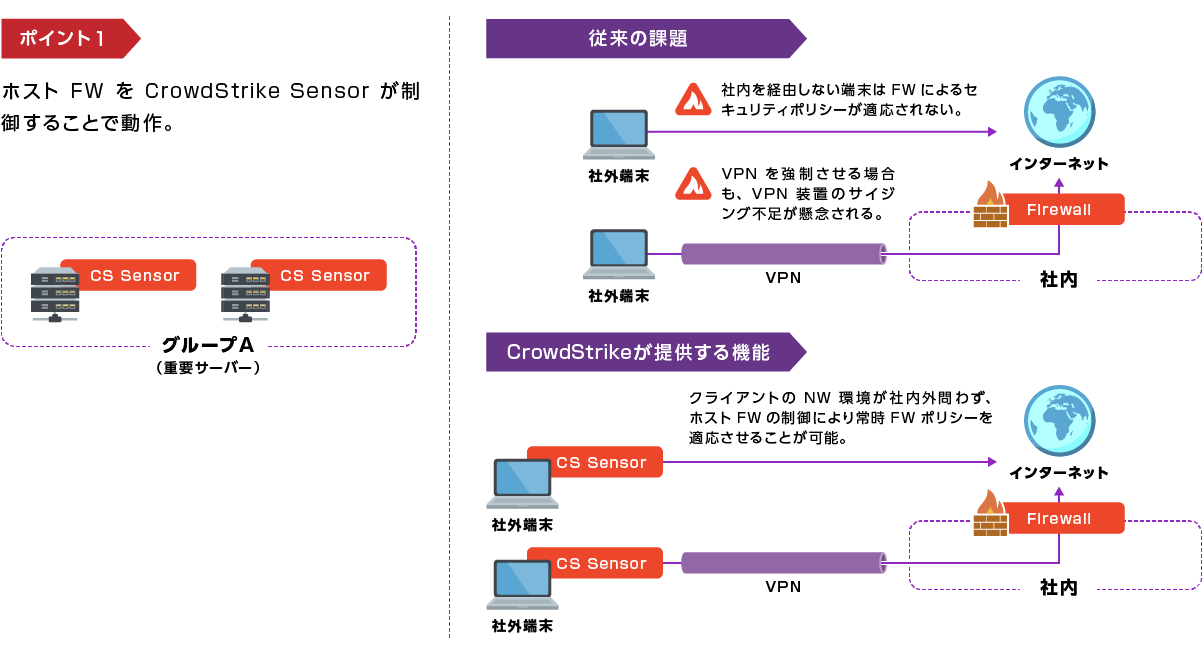
ポイント1:ホストFWをCrowdStrike Sensorが制御することで動作
ポイント2:ポリシー作成/適応/更新作業の高い運用利便性

ポイント3:FWポリシーに関連するアクティビティの確認

お問い合わせ・資料請求
株式会社マクニカ CrowdStrike 担当
- TEL:045-476-2010
- E-mail:crowdstrike_info@macnica.co.jp
平日 9:00~17:00