Specifications/Technical Information

Thales
Thales
Data Discovery and Classification / Data Discovery and Classification + Cipher Trust Manager / Key Management
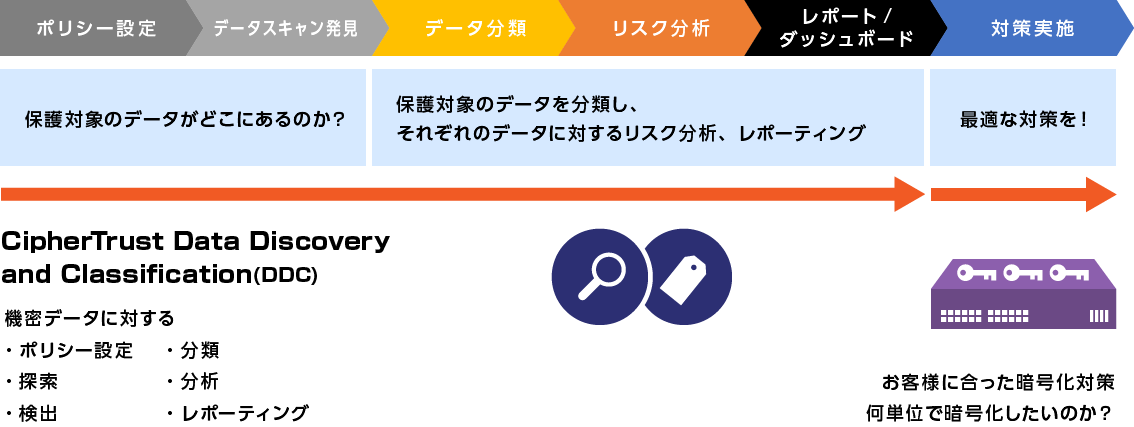
Thales and Macnica propose steps towards data protection
In terms of data protection, where is the confidential data, the data that must be protected? We need to start by clarifying the whereabouts of
After that, the correct procedure is to classify each data, conduct a risk analysis for each data, and take appropriate protection measures.
Data Discovery and Classification
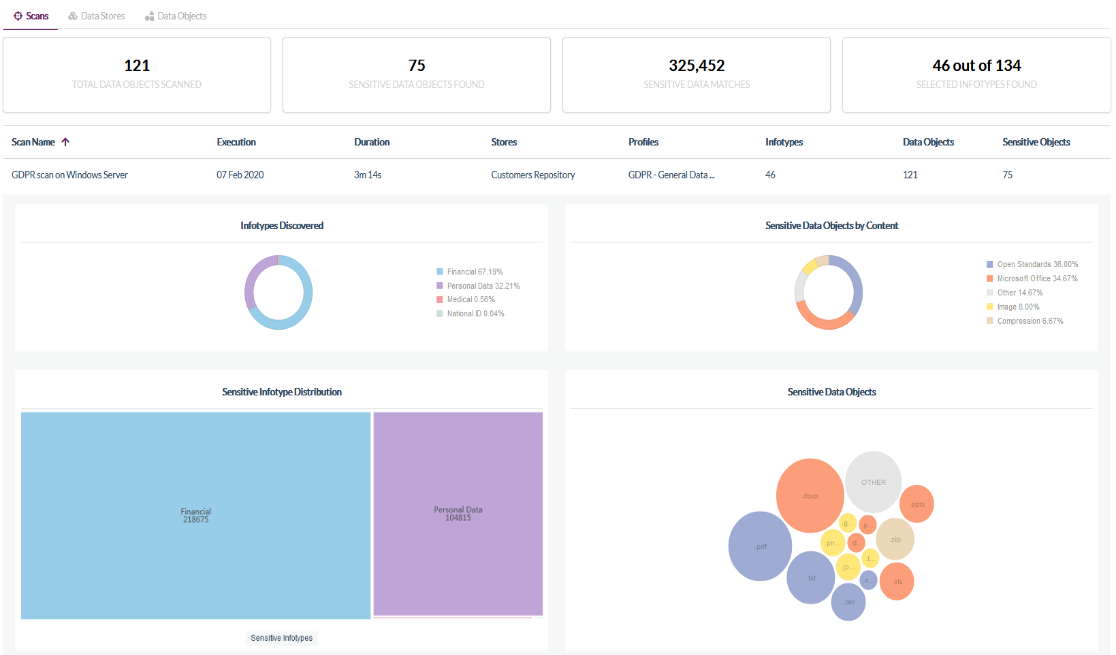
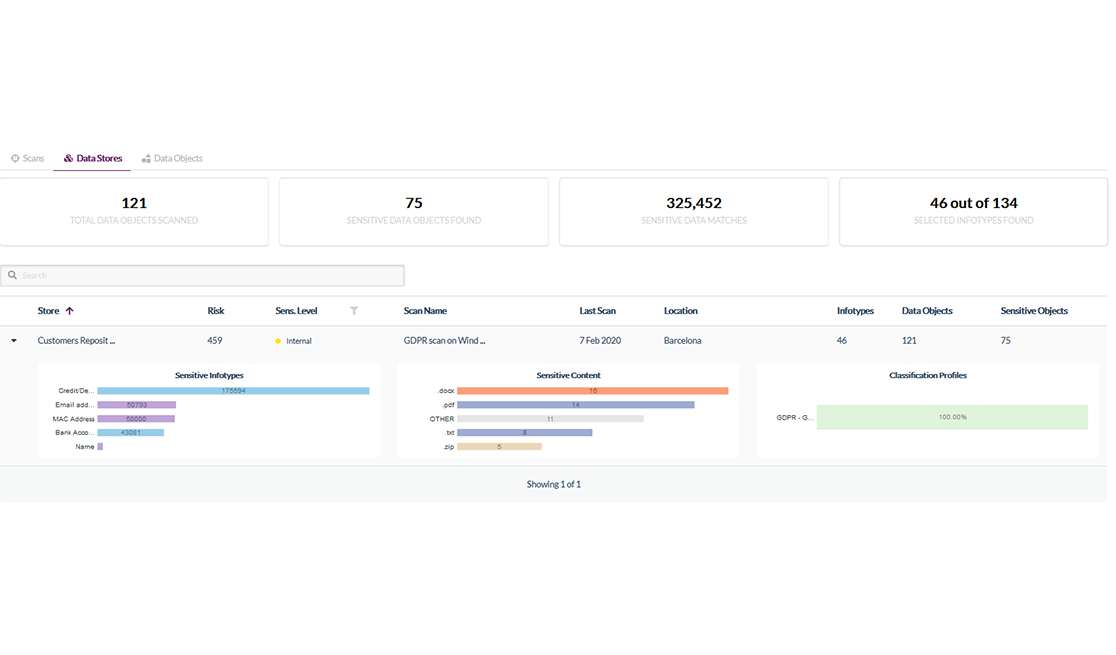
By using Thales' Data Discovery and Classification (DDC), it is possible to search for data to be protected (so-called confidential data), analyze risks, and visualize it as a dashboard all at once in the customer's environment. I have no idea where the data is. This is a recommended product for customers.
Now that we have identified the location and risks of data using DDC, we will move on to specific data protection measures.
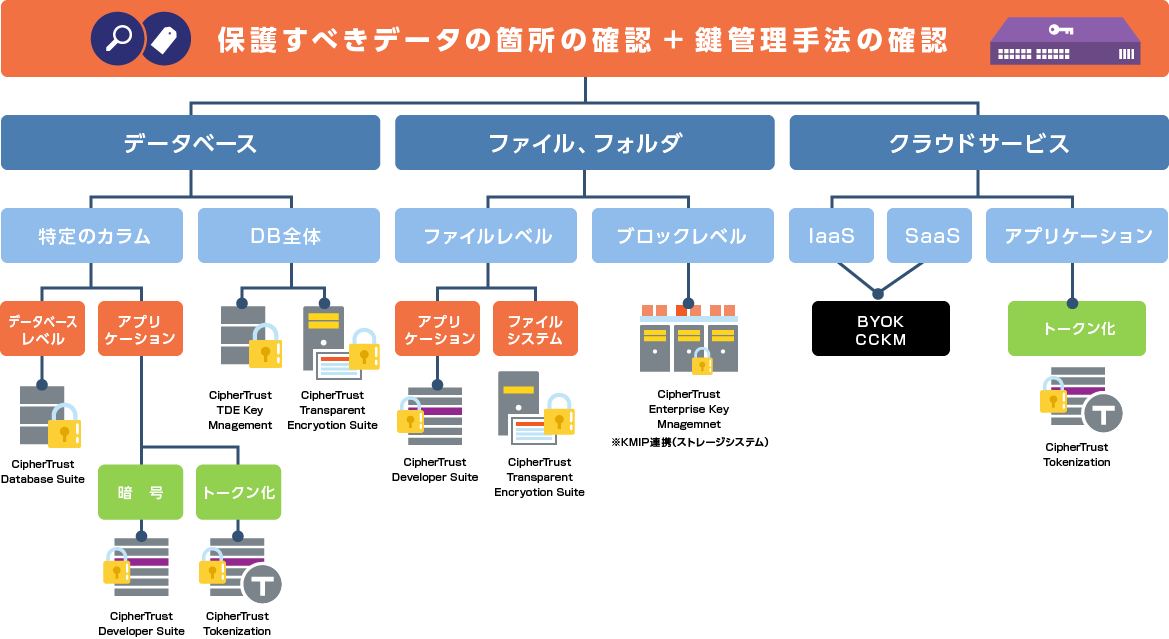
Cipher Trust Manager/Key Management
Once you have clarified the data you want to protect, the next step is to think about how many units you want to encrypt. By using Thales Cipher Trust Manger, it is possible to protect data from different risks at different layers. In addition to data protection, we use HSMs that have acquired FIPS140-2 certification from NIST for "encryption key management", which is important for encryption.
Inquiry/Document request
In charge of Macnica Thales Co., Ltd.
- TEL:045-476-2010
- E-mail:thales-sales@macnica.co.jp
Weekdays: 9:00-17:00