Specifications/Technical Information

Thales
Thales
Is data safe with encryption?
Encryption technology in security is widely used as an effective means, and the number of companies that have introduced encryption measures is increasing.
However, it is easy to overlook the management of “encryption keys” that are required for encryption.
If the encryption key is stolen, there is a risk of misuse of encrypted important data. It has a very large impact on companies and organizations, such as leakage of confidential corporate information and damage caused by credit card counterfeiting. Therefore, not only encryption, but also safe management of encryption keys is an important point in data protection.
What are the countermeasures?
In order to protect the data safely, by encrypting the data and applying strong access restrictions (segregation of duties)to the encryption key used at that time, create a mechanism that only specific administrators can access the encryption key. is effective.By separating the encrypted data and the encryption key using ahardware security module (HSM) and protecting the encryption key with robust hardware, it is possible to prevent the encryption key from being leaked to the outside.
What is HSM? - crypto key vault
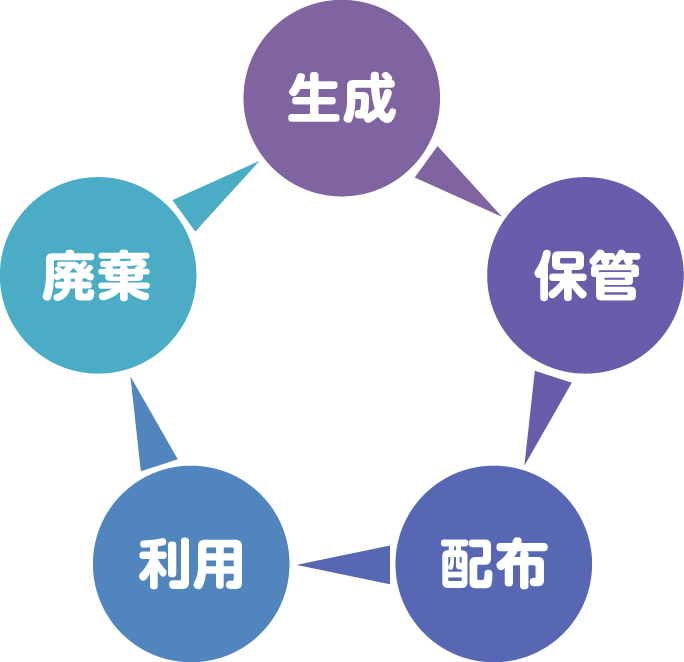
Hardware Security Module (Hardware S ecurity Abbreviation for Module. The key lifecycle (generation/storage/distribution/use/disposal) can be managed and all cryptographic processing can be performed within a secure HSM that is tamper-resistant*1. We have also obtained various certifications (FIPS140-2 Level 2/3, Common Criteria). Macnica handles products from Gemalto (formerly SafeNet) and Thales, two of the top HSM companies in Japan and overseas, and has a proven track record in government, finance, enterprise, and payment networks.
*1 Tamper resistance: (1) physical or (2) logical difficulty in reading internal information. In HSM, data is safely protected by a mechanism that erases data when the housing is opened and a division of duties function.
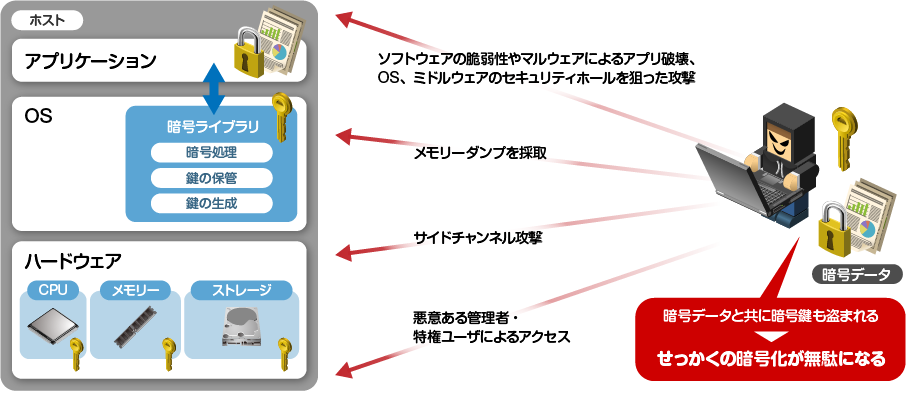
normal encryption
Normally, the encryption key is developed in the memory of the host server, encryption/decryption processing is performed, and the encryption key is stored together with the encrypted data in the host server. Then, if you are attacked by an unauthorized accessor, the encrypted data and the encryption key will be stolen together and easily decrypted, and the encryption will be wasted.
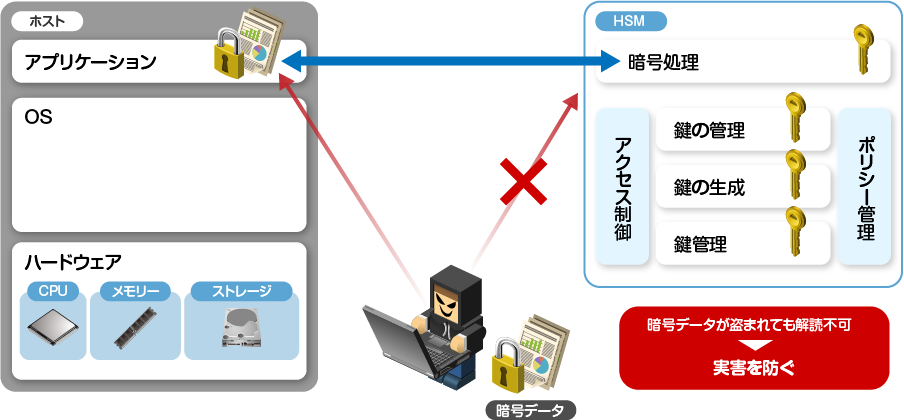
HSM encryption & key management
In order to prevent decryption of encrypted data by unauthorized access, it is effective to separate encrypted data and encryption keys and perform key management with HSM. Keys are stored inside the hardware and strict access control is performed. Since the HSM does not have a mechanism to release the key outside the HSM * 2, the encryption key cannot be stolen.
*2 In the case of Thales products, the master key is not exposed outside the HSM.
Inquiry/Document request
In charge of Macnica Thales Co., Ltd.
- TEL:045-476-2010
- E-mail:thales-sales@macnica.co.jp
Weekdays: 9:00-17:00
