Specifications/Technical Information

Thales
Thales
Environmental Changes Surrounding the Manufacturing Industry: Digital Integration Accompanying Smart Factories
In recent years, I think that the number of customers in the manufacturing industry who are considering smart factories is increasing.
By visualizing the data collected from manufacturing sites and production equipment, we can accelerate the improvement cycle of manufacturing sites and improve manufacturing sites for the future prosperity of our customers' businesses and the development of society. is important to
As smart factories are promoted, it is expected that data will be utilized beyond the manufacturing site, such as analyzing customer data and using it for product design. Also, with the use of IoT devices, the amount of data collected will increase. By utilizing such diverse data, the manufacturing industry will be digitally integrated in order to expand the business of our customers.
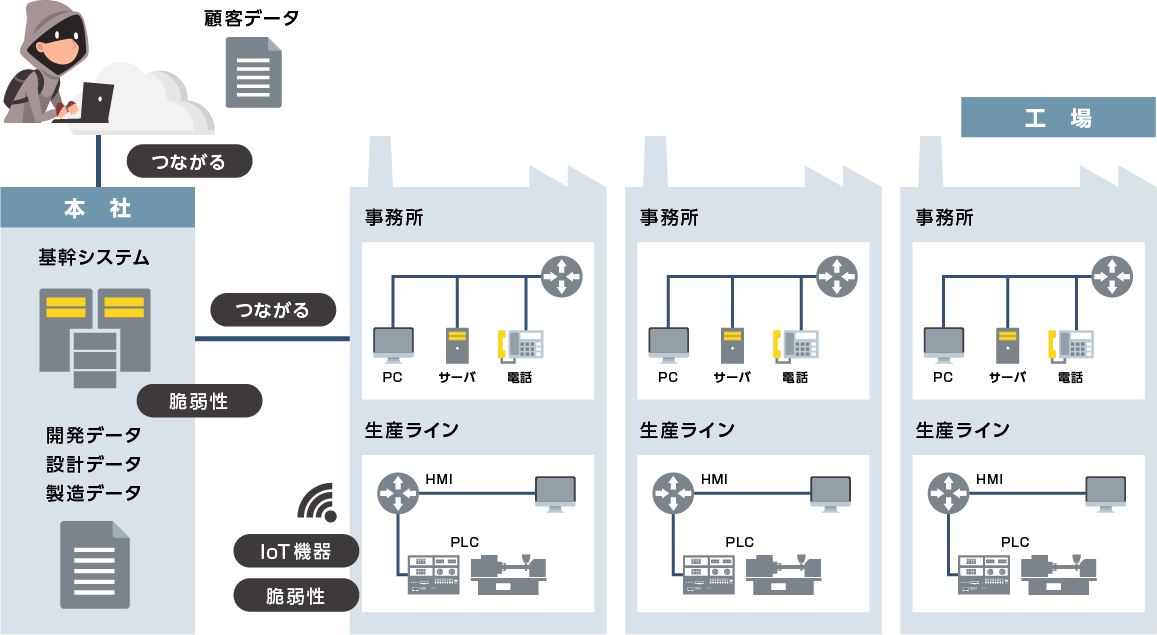
However, as the number of places connected to the network increases, security threats such as a rapid increase in the intrusion routes of external attacks and system vulnerabilities occur at the same time.
A future where manufacturing is digitally integrated? Rapid increase of intrusion routes x weaknesses (vulnerabilities)
Sensitive data security measures
Customers in the manufacturing industry need to protect a wide range of confidential data, including product design data, data collected from IoT devices, and data from business partners. In the unlikely event that confidential data is leaked, there is a possibility that the trust as a company will be lost, and that huge costs will be incurred due to compensation for damages and legal sanctions.
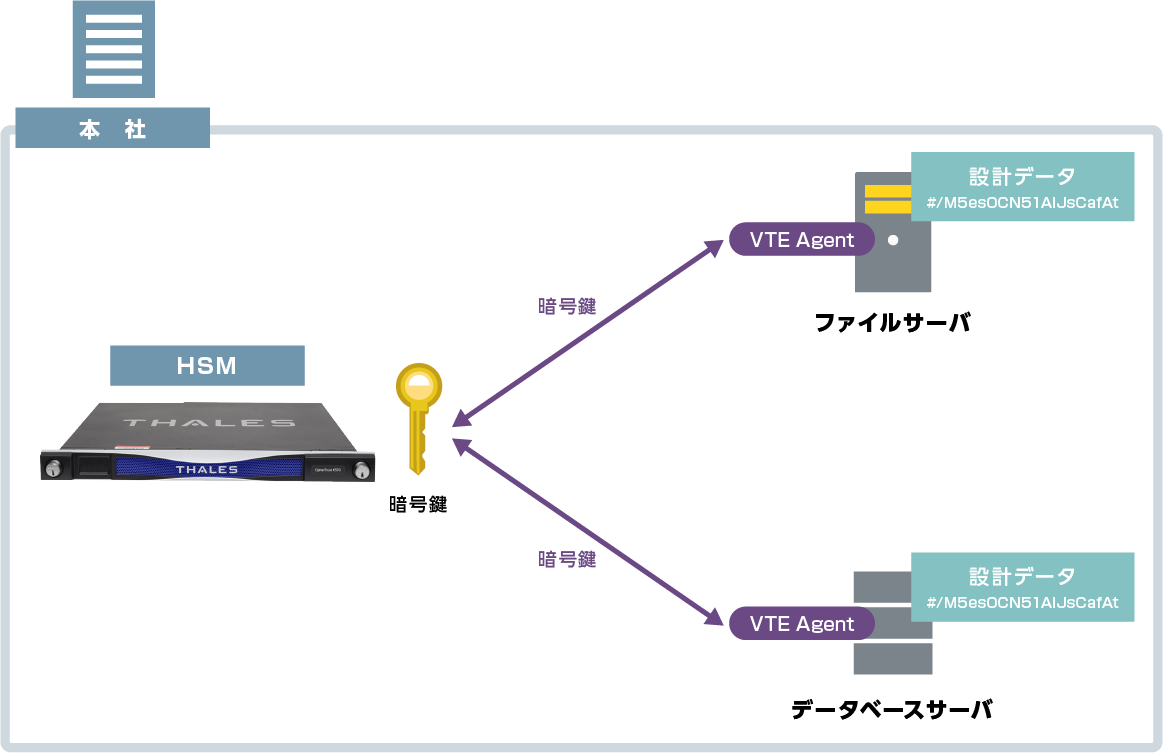
Here, we introduce an encryption + key management solution using design data as an example.
Leveraging Sensitive Data Protection Solutions with HSMs
Confidential data in file servers and database servers can be transparently encrypted via a transparent encryption agent, enabling safe data management. The encryption key used for encryption is securely managed in the HSM, so the encryption key cannot be stolen.
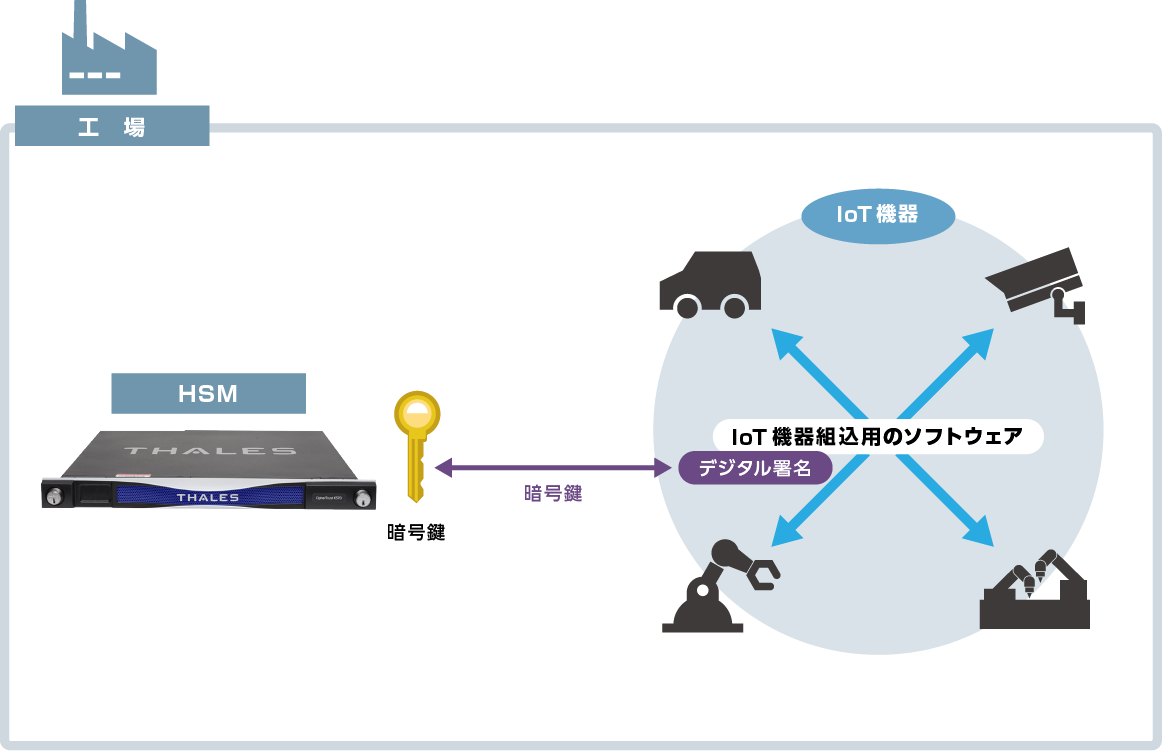
IoT device security measures
In recent years, the use of IoT devices at manufacturing sites and the manufacturing of IoT devices has increased. IoT devices themselves are convenient products, but there are also security concerns such as software tampering and device hijacking by unauthorized accesses due to the leakage of signature keys used for digital signatures of software.
Safe and secure use of IoT devices through signature key management
In order to prevent software tampering and device hijacking, it is effective to strictly manage the signature key with HSM. By managing signature keys with HSM, it is possible to prevent spoofing due to leakage of signature keys and prevent security problems when using IoT devices such as those mentioned above.
Software integration process
Inquiry/Document request
In charge of Macnica Thales Co., Ltd.
- TEL:045-476-2010
- E-mail:thales-sales@macnica.co.jp
Weekdays: 9:00-17:00