
Introduction ~XDR Anything Consultation No.1~
One day, Yamada, a security expert and evangelist working at Macnica, was consulted by Yoshikawa, who works on a security product sales team. The content of the consultation was, "I want to know what XDR is from the very beginning." Yamada answers Yoshikawa's question.
Character

| name | Kohei Yamada |
| age | 30's |
| sex | Male |
| Occupation | pre-sales engineer |
| Belonging department | Suspect |
| Outline | Active as a pre-sales engineer for security products. He also plays an evangelist role to raise awareness of the necessity of XDR inside and outside the company. |

| name | Rina Yoshikawa |
| age | 20's |
| sex | Woman |
| Occupation | sales |
| Belonging department | field sales |
| Outline | A new mid-career recruit assigned to Macnica 's security products sales team. In my previous job, I worked in IT product marketing and field sales for five years. However, I have no experience in sales of security products. |
What is "XDR"?

Mr. Yamada, thank you for taking the time.
No, no problem at all. You want to know about "XDR", right?


yes. As a matter of fact, I was put in charge of sales of XDR products, and I thought that there should be no mistakes in the information I conveyed to customers.
I see. Then you've already checked that XDR is an abbreviation for "eXtended Detection and Response".


yes. However, the more I researched about XDR, the more confused I became...
Maybe. After all, providers have different definitions of XDR. It's easy to get confused.


That's right. I couldn't decide which was the correct definition, so I started by asking Mr. Yamada, "What is XDR?"
I got it. Let me explain. First, what exactly is XDR? The correct definition can be summarized as "By collecting information from various sensors (data sources) and analyzing it cross-sectionally, we will improve the visibility and detection power of 'what is happening now' in the internal network. and protect the organization and company by improving the ability to deal with and respond to incidents.” did you make a note of it?


yes. I'm good at work. I take notes on people's stories.
By the way, what exactly do you mean by "diverse data sources"?
By the way, what exactly do you mean by "diverse data sources"?
At the moment (as of February 2023), EDR sensors (or data sources) include security solutions such as "EDR", "NDR", "MDR", "SIEM", "SASE", and "IDaaS". . In the future, IoT devices will also be included as data sources. If you conceptually show the concept of XDR, it will look like this.

Figure 1: Conceptual diagram of XDR
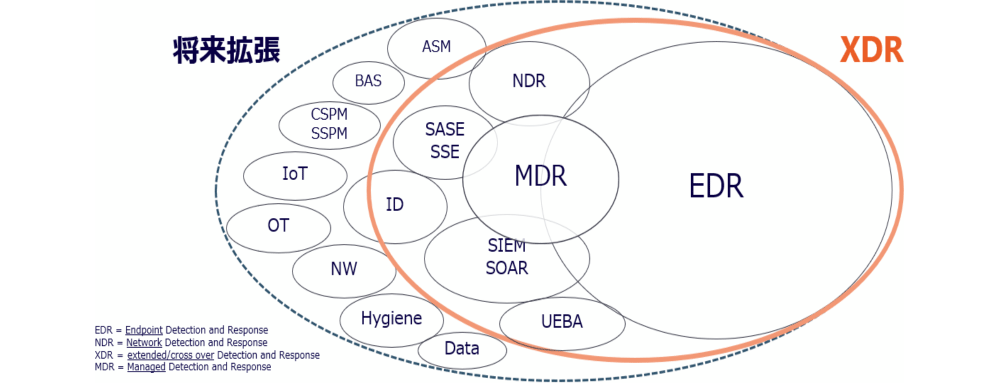
| EDR | Abbreviation for Endpoint Detection & Response. A solution that executes "detection," "investigation," "containment," and "recovery" of threats at endpoints such as servers and clients. |
| NDRMore | Abbreviation for Network Detection & Response. A solution that executes “detection,” “investigation,” “containment,” and “recovery” of threats in networks |
| MDR | Abbreviation for Managed Detection and Response. A service that provides EDR and NDR functions and operation services |
| SIEMs | Abbreviation for Security Information and Event Management. A large amount of logs are collected from various devices that make up the system, correlated analysis is performed, and abnormalities are examined. A solution that alerts |
| SOAR | Abbreviation for Security Orchestration, Automation and Response. A solution that efficiently monitors and responds to security incidents with technology that is complementary to SIEM |
| SASE | Abbreviation for Secure Access Service Edge. A cloud service that integrates network and security solutions into one. SSE (Security Service Edge) is a subset of SASE. |
| UEBA | Abbreviation for User and Entity Behavior Analytics. A solution for detecting anomalies by analyzing end-user behavior of systems |
| IDaaS | Abbreviation for ID as a Service. Refers to a cloud-type ID management service |

I see. XDR is based on existing security solutions.
I agree. In other words, it can be said that EDR is a mechanism for expanding the inspection targets of security solutions such as EDR and SIEM.


The explanation is easier to understand. Anyway, is XDR not a completely new security technology solution?
that's right. XDR is a solution that uses proven and mature threat detection technology, and is a mechanism for enhancing threat detection and visualization capabilities while using existing technology. In that sense, it is by no means a new security technology with unknown capabilities. That is why XDR products can be said to be highly reliable and effective.

What can "XDR" improve and what can it do?

I would also like to know specifically what can be done with XDR and what can be improved.
In a nutshell, the effect of introducing XDR is that you can solve all the problems related to the introduction and utilization of security solutions such as EDR, NDR, and SIEM at once. In other words, companies that are serious about protecting their systems from the threat of cyberattacks by implementing EDR, NDR, SIEM, etc., are bound to face major challenges. It can be said that XDR is the solution that solves this problem.


What exactly is the problem that XDR solves? In the first place, I think cyber security will be strengthened by the introduction of EDR, NDR, and SIEM.
Certainly, by introducing security solutions such as EDR, NDR, and SIEM, you can greatly improve your ability to detect potential threats within your company and identify the extent and cause of their impact. However, their introduction entails the risk of causing a kind of "dilemma" that leads to "missing threats".


Are you in a dilemma? What kind of vicious circle is that?
This dilemma is illustrated in this figure (Fig. 2).

Figure 2: Dilemma in introducing and utilizing security solutions
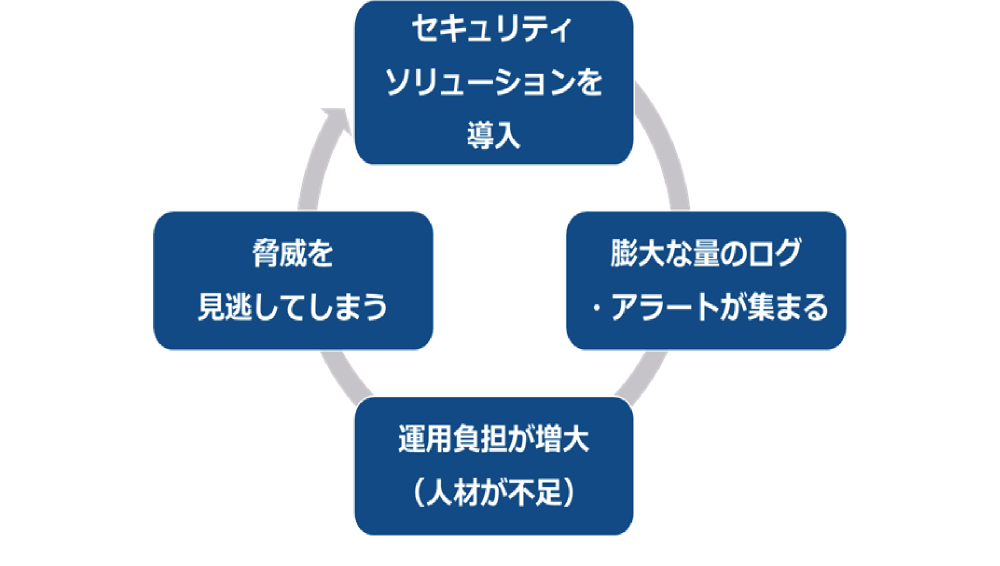

Indeed, with the introduction of EDR, NDR, SIEM, etc., the number of logs collected and alerts issued increased steadily, increasing the operational burden on security personnel. As a result, the risk of missing threats increases.
I agree. And the alerts issued by EDR, NDR, and SIEM solutions are likely to contain false alarms. Therefore, in order to accurately grasp the occurrence of incidents through these solutions, it is necessary to accurately and promptly identify whether the issued alert is due to over-detection or correct detection while looking at a large amount of logs. have to judge.


Hmm, that sounds tough.
It's pretty tough. Moreover, to do so requires considerable knowledge and technical skills related to cyberattacks and security.


Oh, I've heard from customers that they don't have enough security personnel with such advanced skills.
Yes, the absolute number of security personnel is inadequate across the industry. Therefore, the more the internal network is monitored, the more the burden will be concentrated on a handful of personnel, and the greater the risk of detection failure.


By introducing XDR, you can cut off such a dilemma or vicious circle.
that's right. First, XDR's solution will allow logs from disparate data sources to be consolidated, correlated and managed on a single platform. As a result, it is possible to visualize "what is currently happening in the internal network" on the dashboard in real time, improve the efficiency of log searches when incidents occur, and automatically analyze huge logs using AI (artificial intelligence).・Abnormal judgment can be realized.


As a result, will it be possible to reduce the operational burden and man-hours you mentioned earlier?
It can be said that it can be reduced. In fact, by using XDR solutions, it is possible to cross-analyze logs collected from multiple data sources and standardize, streamline, and automate the process of incident detection/discovery and handling/response. As a result, it is possible to reduce both the man-hours required for operation and the skills required for operation while avoiding omissions in detection.


Will it also solve the problem of over-detection?
Yes, we can solve it. By implementing an XDR solution, we can efficiently process logs and alerts to continuously improve the accuracy of threat detection and discovery. More specifically, XDR's solution optimizes the volume of logs collected from multiple sources while suppressing false positives, discovering new threats, prioritizing threats after they are discovered, and managing incidents. Follow-up surveys can be automated and streamlined. This will improve the accuracy of threat detection.


I see, I understand the effect of introducing the XDR solution. By the way, is it easy to build an XDR mechanism in the first place?
Good question. In fact, it is not easy to collect appropriate logs from multiple data sources and make them available for analysis. There is a lot of work to be done, such as developing an API to collect logs from the source. Facilitating such work is one of the important roles of the XDR solution.


In other words, the XDR solution also facilitates the creation or introduction of XDR mechanisms.
that's right. Therefore, by adopting an appropriate XDR solution, the work of adding new data sources (security solutions) and expanding the scope of inspection becomes more efficient.

How does "XDR" work?

Lastly, please tell us about the systematic structure of XDR.
The structure of XDR is simple and can be illustrated in this diagram (Fig. 3).

Figure 3: XDR system configuration
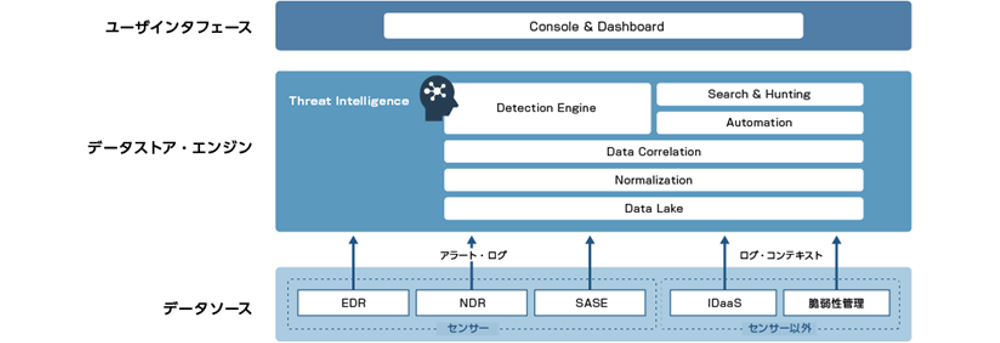
As you can see from this figure, XDR is largely divided into a "data source" part and a "data store & analysis engine" part.


Indeed, in the "data store" part, the various collected logs (formats) are normalized, making comprehensive searches and analysis possible. Structurally, it resembles a system for collecting and analyzing big data.
yes, they are similar


Certainly, the structure of SIEM seems to have a similar structure to this. Are there any structural differences?
No, structurally there is no difference between XDR and SIEM. As you can see from the diagram (Fig. 1) I showed earlier, XDR is a concept that includes SIEM, and it is a solution for expanding the inspection target of SIEM and realizing effective use of SIEM. It is good to remember that the SIEM mechanism is at the heart of data processing and operations.


Is that so.
yes. Also, because it is structurally the same as SIEM, it can be said that the mature technology that has been cultivated in SIEM can be used as it is in XDR solutions.


got it. Thank you for today! If you have any questions about XDR, please feel free to contact us.
roger that!

3 lessons learned
- What is XDR?
A solution that collects information from various sensors (data sources) such as EDR, NDR, and SIEM and analyzes it cross-sectionally to improve the visibility and detection of threats, and improve the ability to deal with and respond to incidents. be. Based on proven and mature technology, not new security technology - What does XDR do better and what can it do?
The introduction of XDR solutions comprehensively solves the issues surrounding the introduction and operation of EDR, NDR, SIEM, etc. The challenges solved by XDR are always faced by companies that are serious about cyber security measures. - How does "XDR" work?
XDR consists of components for collecting information from data sources, searching and analyzing it in an integrated manner. The structure of the system is the same as SIEM, so the mature technology used in SIEM can be used as it is.
Inquiry/Document request
In charge of Macnica XDR Co., Ltd.
- TEL:045-476-2010
- E-mail:XDR@macnica.co.jp
Mon-Fri 8:45-17:30


