Proofpoint
proof point
Proofpoint Next Generation Email Security
As email attacks such as targeted email attacks and business email fraud become more sophisticated and sophisticated, the environment surrounding corporate email is changing dramatically. Proofpoint offers solutions consisting of three components: Email Protection, Targeted Attack Protection (TAP), and Threat Response Auto Pull (TRAP), as next-generation email security measures that respond to changes in the environment.
- "Email Protection" blocks malicious emails at the gateway
- "Targeted Attack Protection (TAP)" that detects and blocks threats centered on cloud-based Box
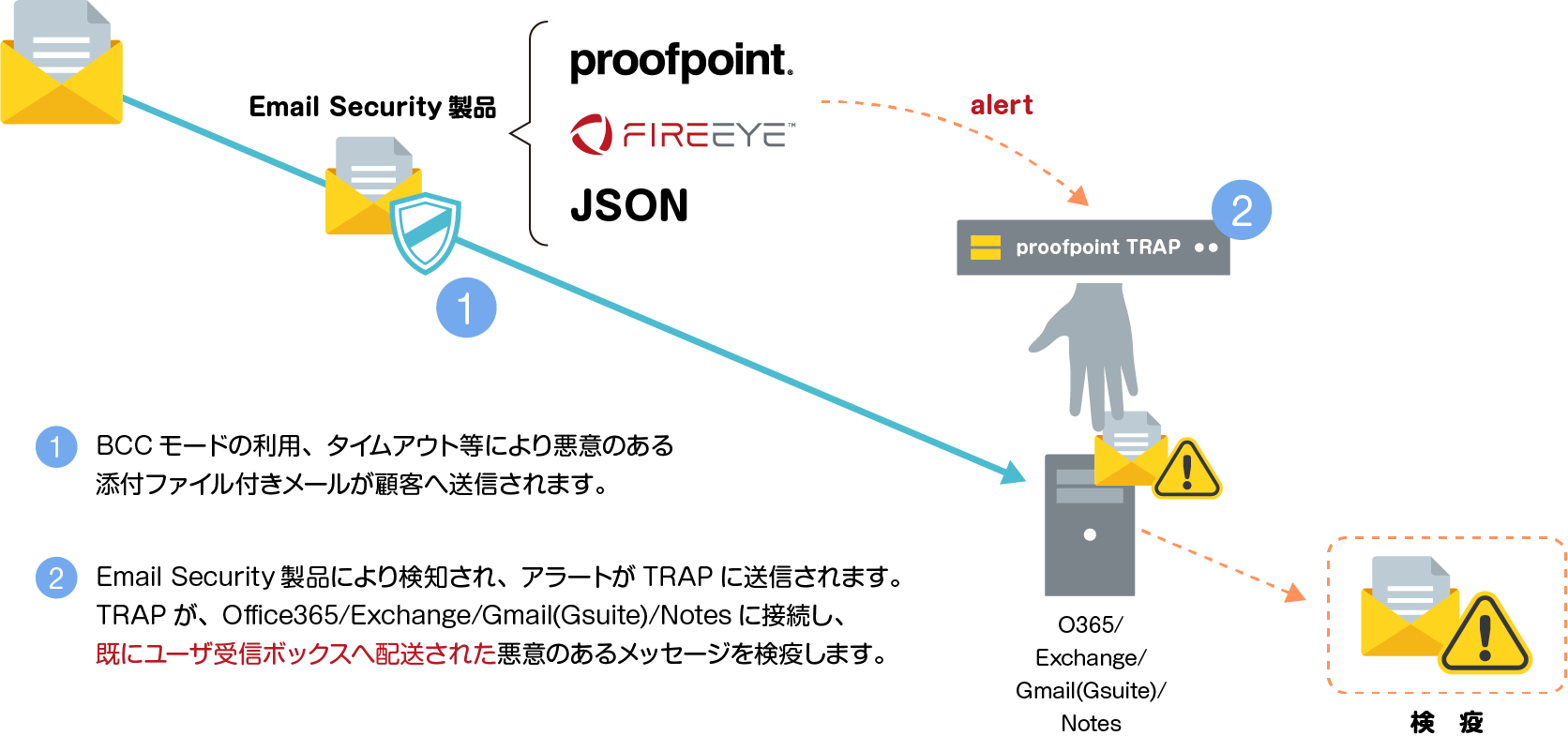
- Threat Response Auto-Pull (TRAP) automates threat containment by auto-quarantining emails
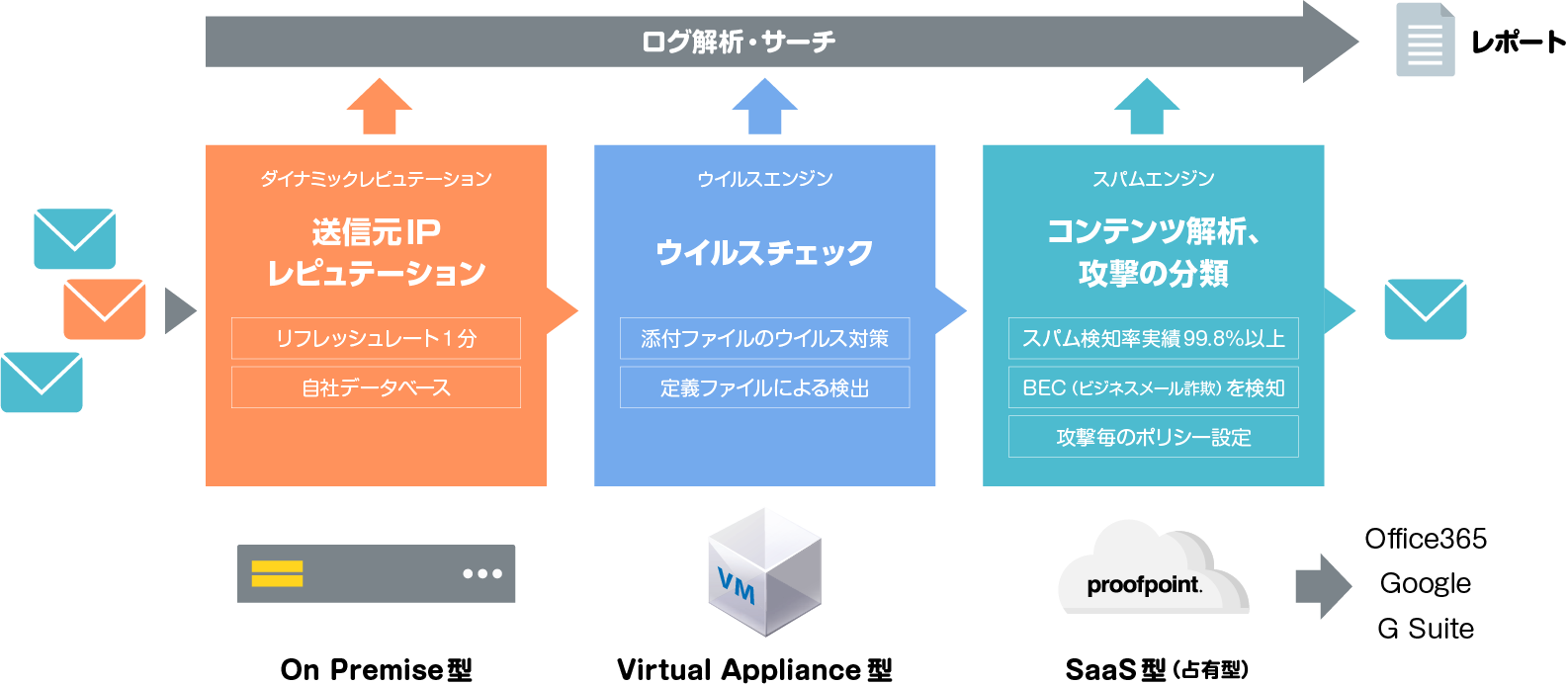
Email Protection: Advanced Email Security Gateway
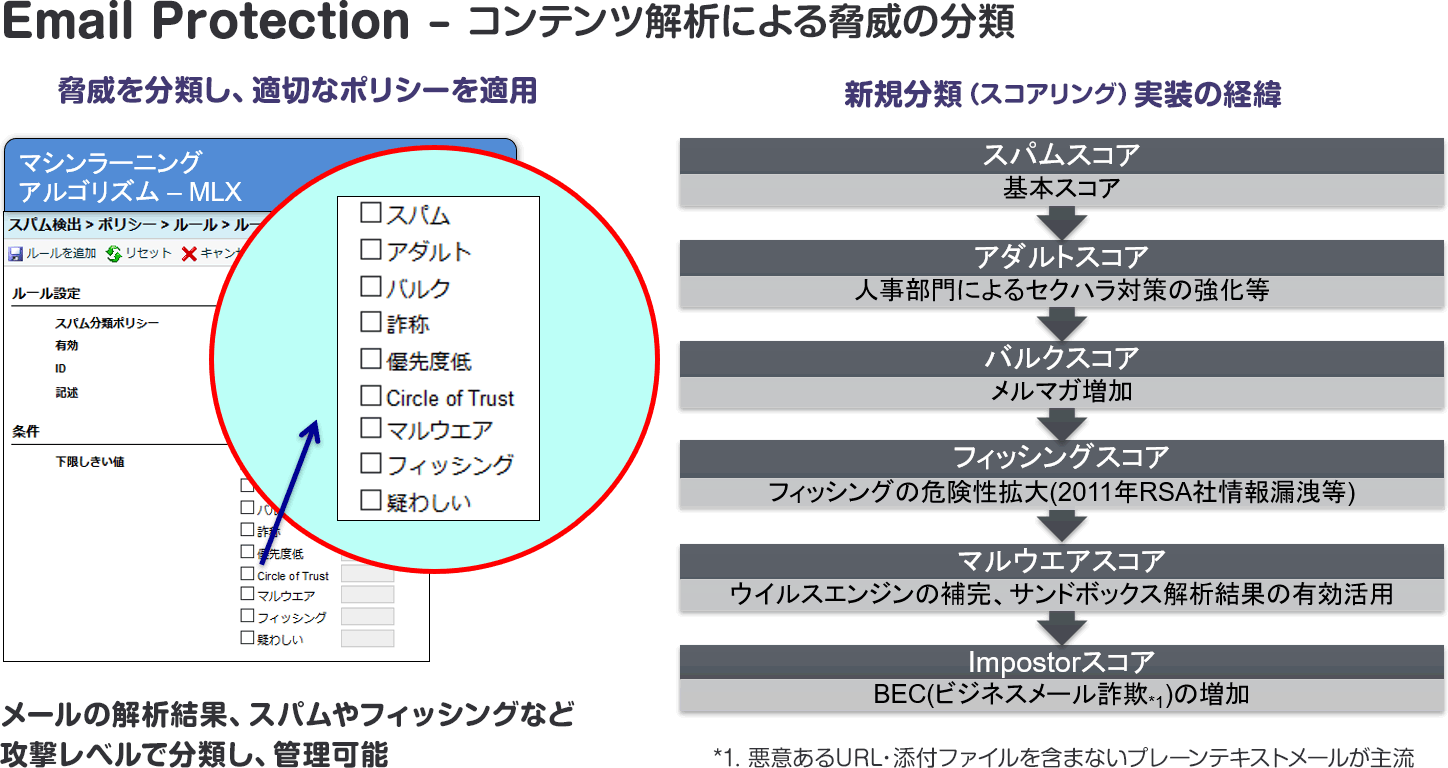
Proofpoint Email Protection is a next-generation email security gateway that provides spam/virus/malware/phishing/BEC protection. It can also be installed as a cloud service or on-premises. In addition to mass distribution of spam and malware, it is possible to classify threats with fine-grained filtering such as adult, phishing, and BEC, and apply and manage appropriate policies according to the attack level.
Standard attack countermeasures: Targeted Attack Protection (TAP)
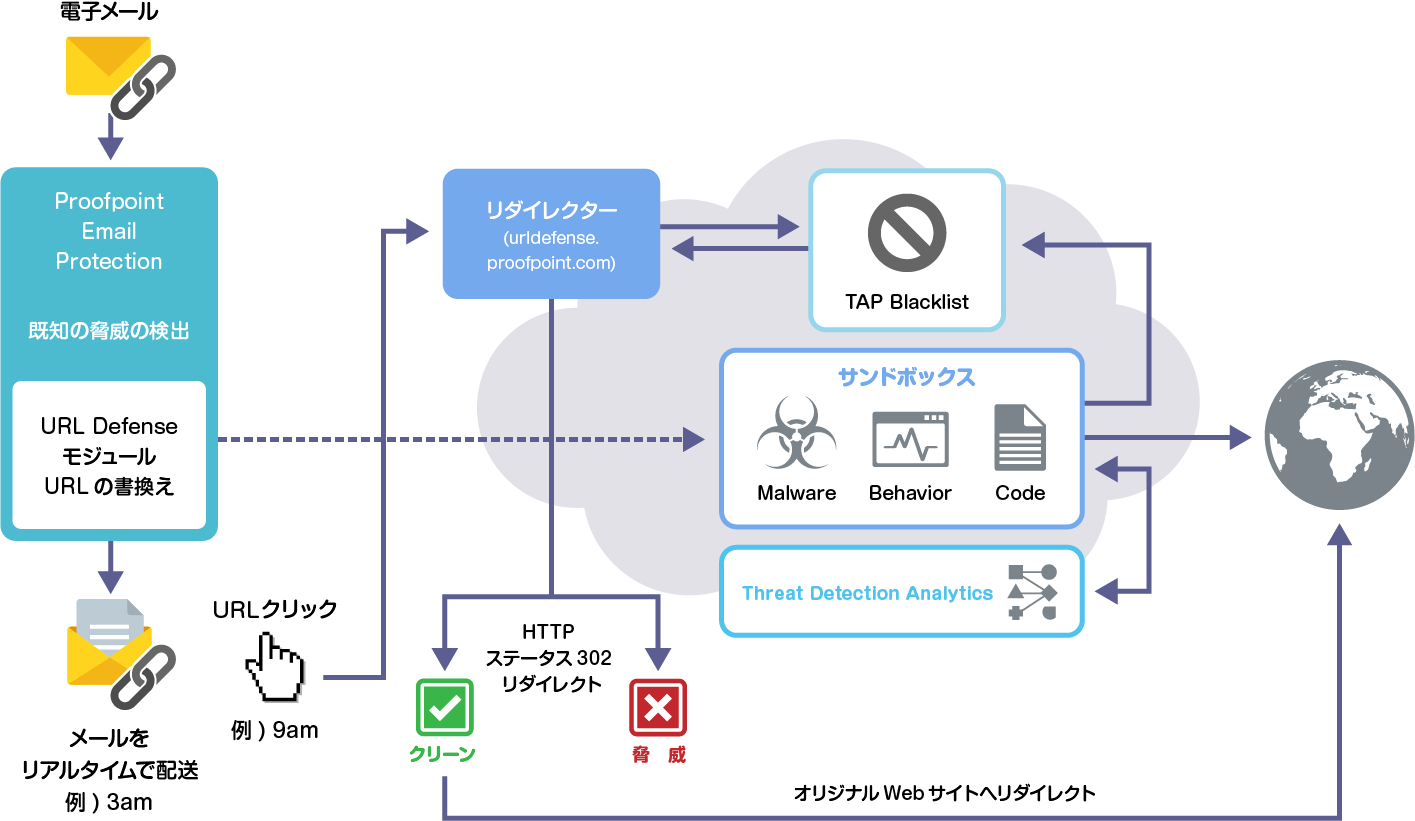
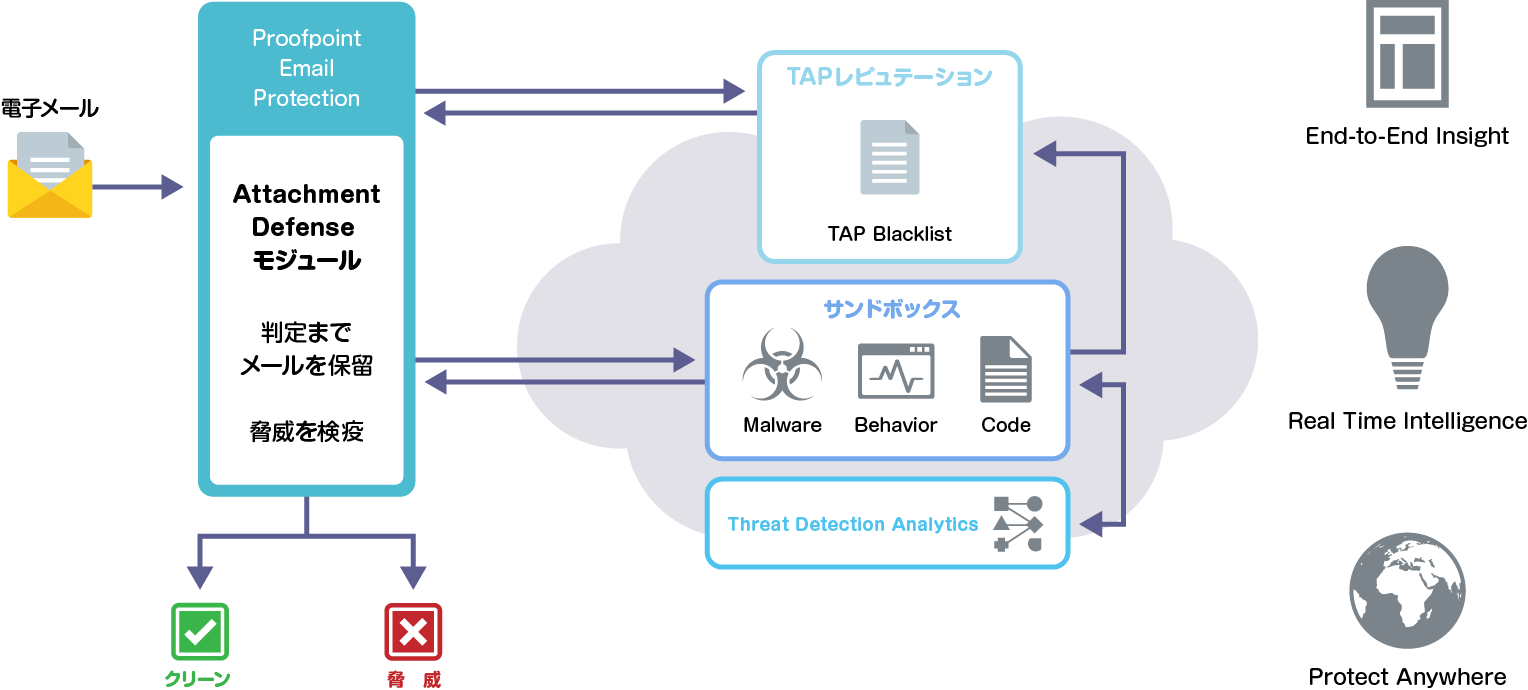
Proofpoint Targeted Attack Protection (TAP) is a service that extends the functionality of the email security gateway "Proofpoint Email Protection". It is a solution that provides a cloud-type Box and analyzes the text and attached files on the cloud. It examines the entire attack chain using multi-stage analysis and combines static/dynamic and protocol analysis techniques to catch even the most advanced ransomware threats. Proofpoint technology doesn't just detect threats. We also apply machine learning to observe the patterns, behaviors and techniques of each threat. As a result, we are always ready to detect new attack tools, techniques and targets. Addresses elusive attack techniques such as virtual machine detection, staggered malware activation, and geo-restricted threats. Our unique predictive analytics predictively identify and Box suspicious URLs based on email traffic patterns. Template-based, reputation-based, and machine-learning detections help you efficiently catch threats like credential phishing attacks that leave no obvious electronic trail. We provide threat intelligence across email, cloud, network, mobile apps and social media as well as threat detection. Our community-based intelligence threat graph uses over 600 billion data points to correlate attack campaigns across industries and geographies. These insights are easily accessible from the TAP Threat Dashboard.
Automatically Quarantine Malicious Emails: Threat Response Auto-Pull (TRAP)
With Proofpoint Threat Response Auto-Pull (TRAP), email and security management teams can streamline the email incident response process. When malicious email is detected, TRAP analyzes the email and automatically quarantines the malicious email. You can also quarantine unwanted mail even after it reaches your users' inboxes. With TRAP, your email and security administration team can save a lot of time cleaning up emails.
Inquiry/Document request
Macnica Proofpoint Co., Ltd. Product Manager
- TEL:045-476-2010
- E-mail:proofpoint-sales@macnica.co.jp
Weekdays: 9:00-17:00