Proofpoint
proof point
Proofpoint Security Awareness Training Security Awareness Training
Proofpoint Security Awareness Training Security Awareness Training
It is said that more than 90% of cyberattacks target people*, and raising awareness and educating people (=employees) is a very effective means of protecting an organization. Technology alone that detects threats and blocks them before they reach your employees will not stop all threats. When employees receive business email compromise or phishing emails, it is important that they recognize the threat and take appropriate action. Proofpoint Security Awareness Training (PSAT) is a solution that can provide the right training to the right person at the right time, educating employees to prevent cyberattacks.
The PSAT also uses a method of continuous training. It is developed by Wombat Security Technologies (acquired by Proofpoint in March 2018) based on world-renowned Carnegie Mellon University research.
*Verizon: "2019 Data Breach Investigations Report" July 2019
1. diagnose
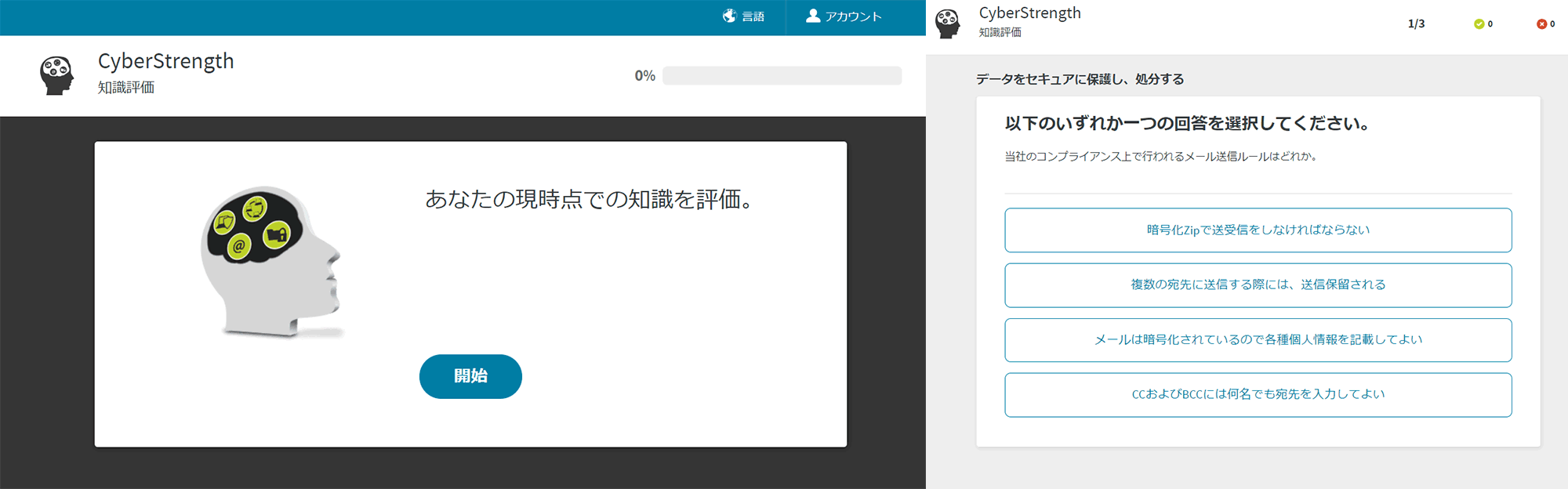
CyberStrength (measurement of understanding of cyberattacks)
- Know your employees' current level of understanding by taking baseline measurements
- Diagnose the people or topics that need your most attention
- Library of over 185 questions (or create your own)
- Training modules are automatically registered for users below the pass line
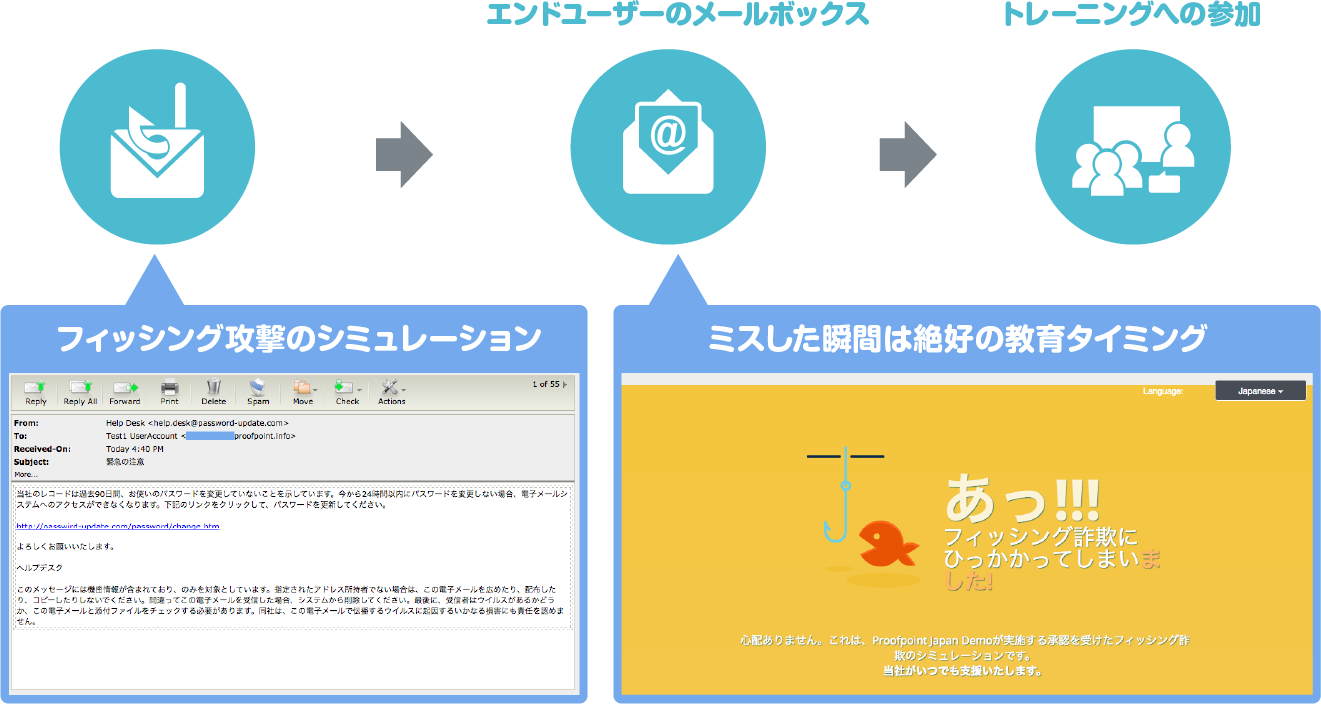
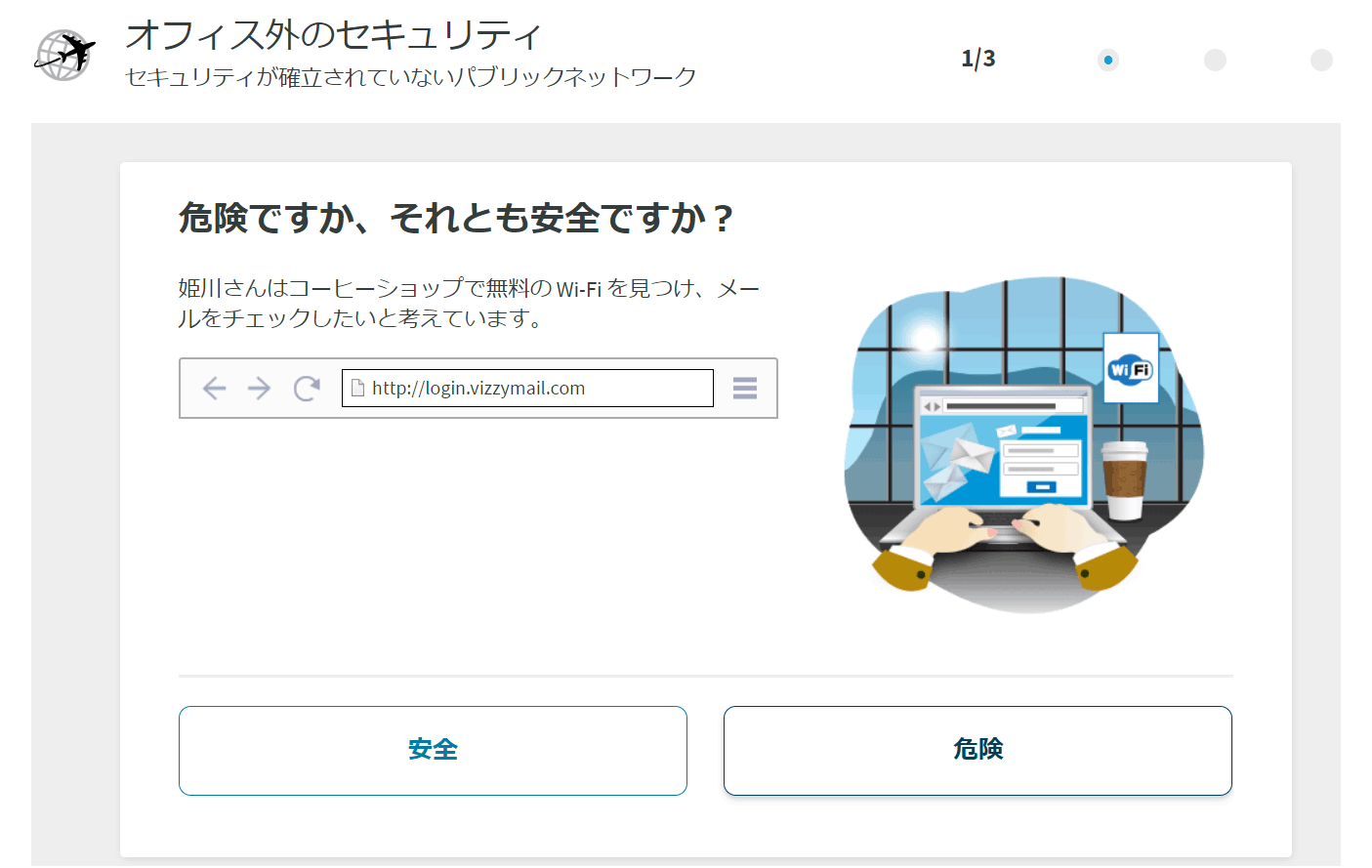
ThreatSim (targeted attack training email)
- Measure users' defenses against phishing attacks with simulated training emails
- Over 1000 “realistic” templates for phishing attacks
- Random email delivery and scheduling possible
- Users who do open it are immediately messaged and automatically enrolled in training modules pre-assigned by the administrator.
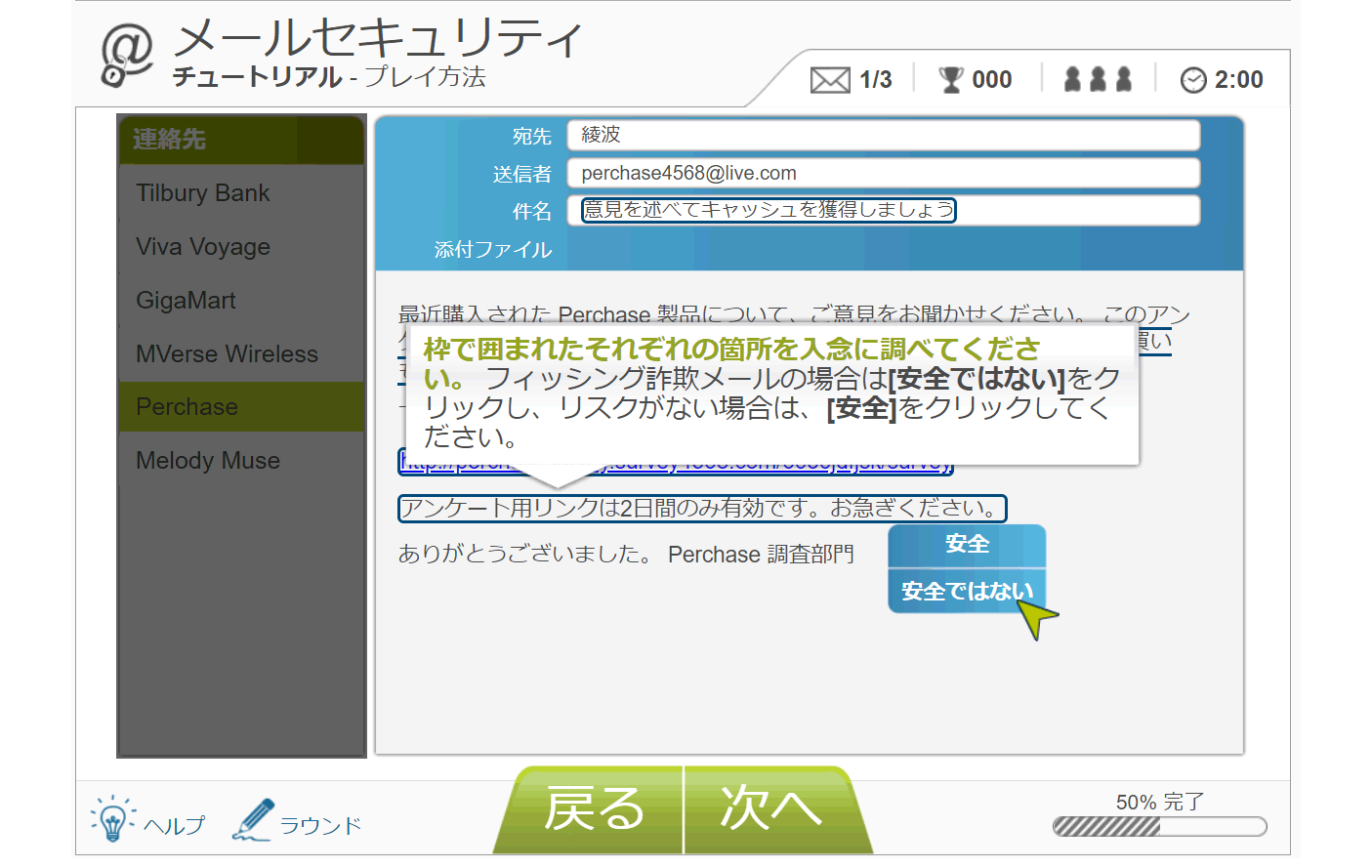
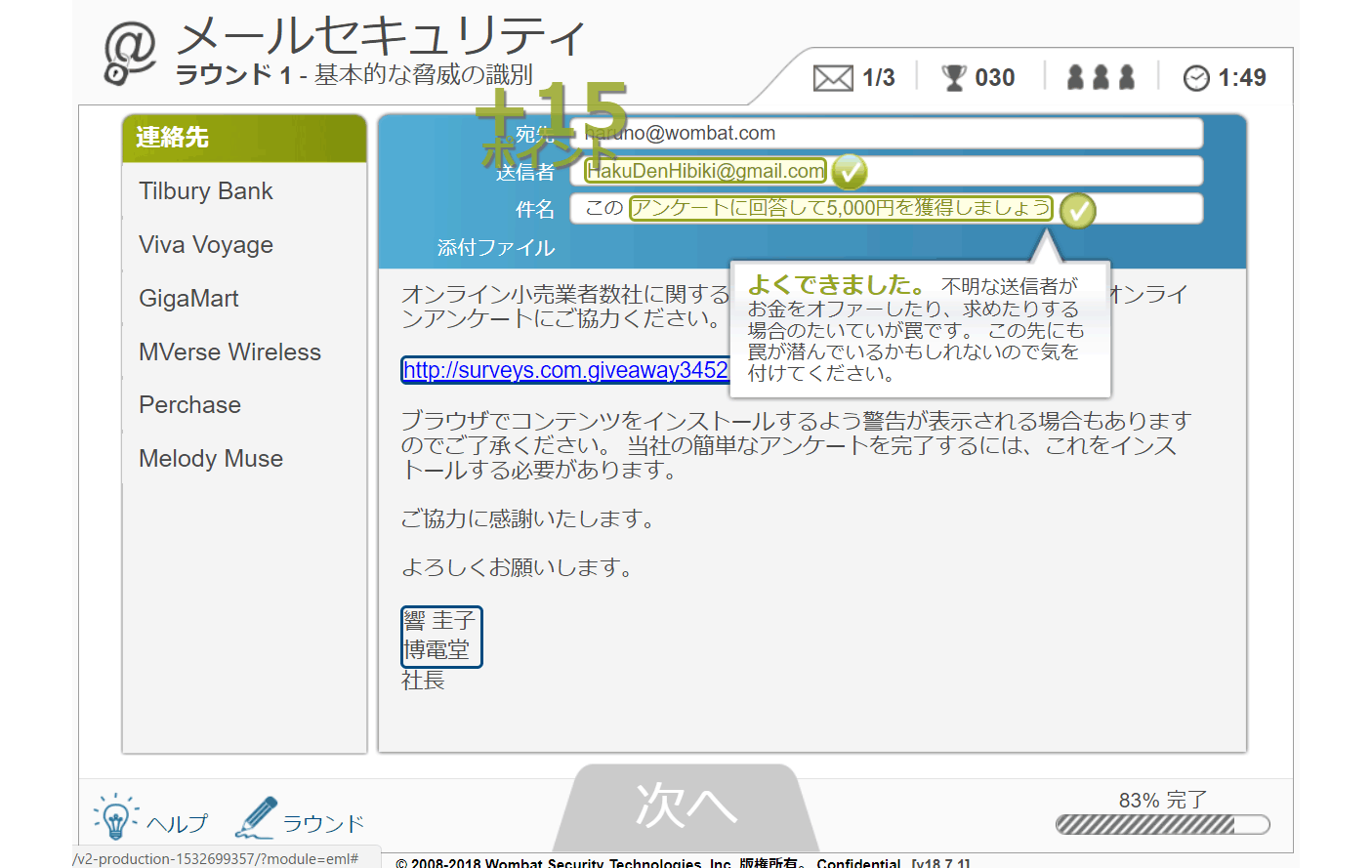
2. education
- About 100 types of training menus that can be taken on demand for about 5 to 15 minutes are provided
- Prepare interactive training using not only text materials but also manga and videos
- Multi-language support to provide consistent training worldwide (supports about 40 languages including Japanese)
- Diverse training modules
Email protection
- foundation series
-
- Introduction to phishing
- data entry phishing
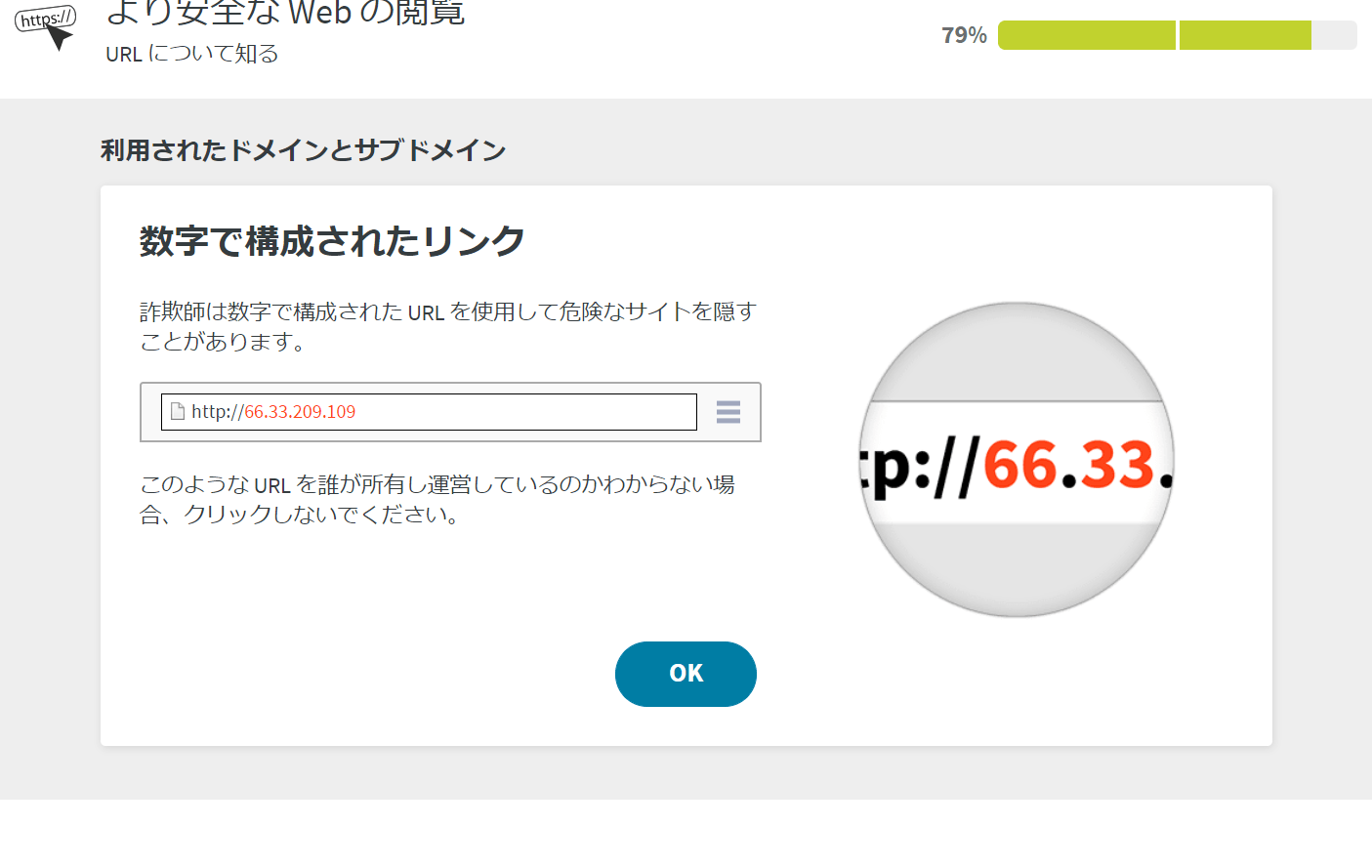
- Avoid dangerous links
- Avoid dangerous attachments
- Advanced series
-
- Email protection tool
- Email security on mobile devices
- The threat of spear phishing attacks
Insider threat series
- Insider threat overview
- malicious insider threat
- unintentional insider threat
Standard module
- Security essentials
- Security Essentials (For Member of the Board)
- social engineering
- Protection from ransomware
- Data protection and destruction
- USB device safety
- physical security
- secure social networking
- Safe web browsing
- mobile device security
- Security outside the office
- Security while traveling
- Practicing Security Practices in the Workplace
- PHI Protected Health Information
- GDPR overview
- GDPR practice
- Understanding PCI DSS
- OWASP Fundamentals
- FERPA for Higher Ed
PII (personal information)
series
- Basics of personal information
- Personal information protection practices
password protection
series
- password policy
- Password management
- strong password
- 多要素認証
Infringement protection series
- Fewer Compromised Devices
- Account compromised
mobile app
series
- Mobile app permissions
- mobile app security
3. Reinforcement (report)
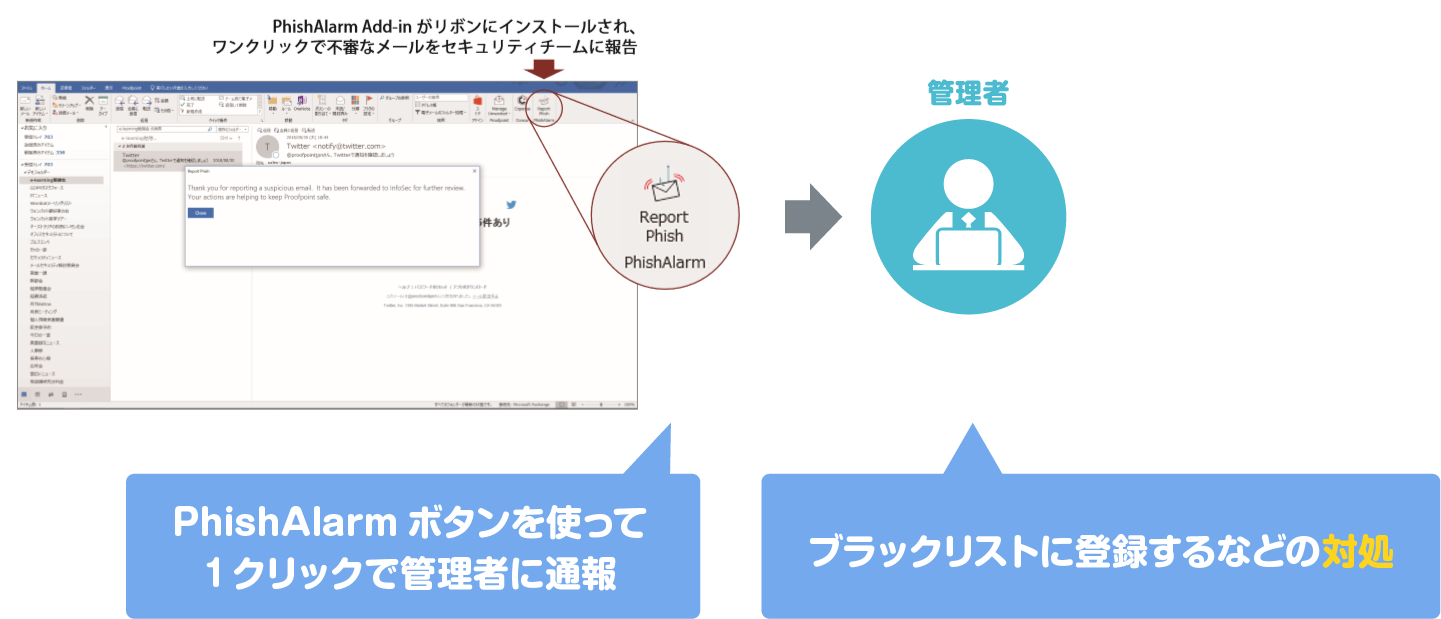
- A reporting tool that can report suspicious phishing emails that arrive in end-user Box to administrators with a single click
- Integrates with major email clients such as Office365 and Gmail
- Display a pop-up message thanking the user who reported it (encourage reporting instead of deleting without reporting as before)
- Not only security personnel but also employees become a force, improving the company's defense capabilities
Four. measurement
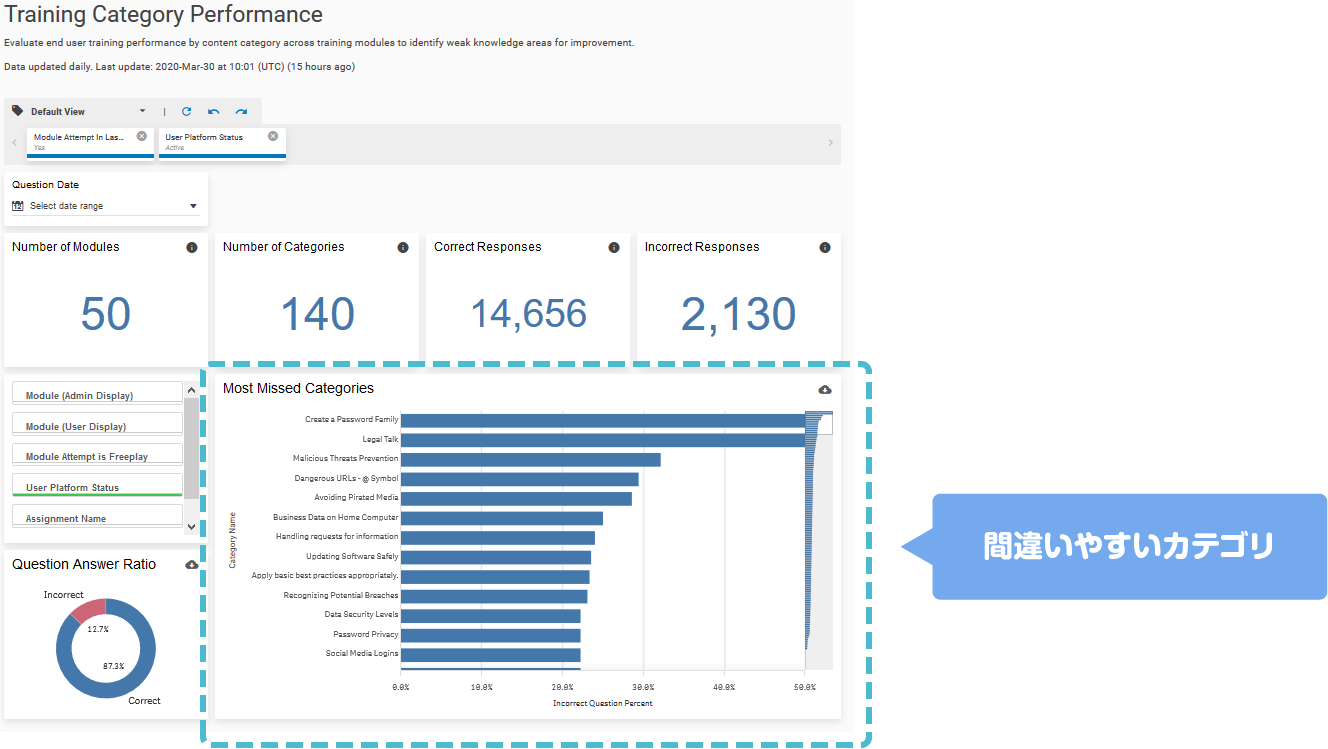
- Real-time visualization of the progress and test results of each module such as CyberStrength, ThreatSim, training modules, and PhishAlarm in the form of a dashboard
- Automatically deliver reports to administrators (exportable to multiple formats (XLS, CSV, PDF, etc.)
- Managers can review employee assessments and training progress, measure ROI, and plan future programs
- Effective employee behavior change is impossible without measurement
Inquiry/Document request
Macnica Proofpoint Co., Ltd. Product Manager
- TEL:045-476-2010
- E-mail:proofpoint-sales@macnica.co.jp
Weekdays: 9:00-17:00