Proofpoint
proof point
ObserveIT Insider Threat Management Insider Threat Prevention
Internal fraud countermeasures by user operation trail recording and UBA
As the threat of cybercrime continues to increase in recent years, crimes by external criminals represented by targeted cyberattacks are becoming more serious, and there is no end to information leaks by internal criminals. There is a high possibility that good users will suddenly act maliciously, and there is also the risk of information leaks due to human error. It can be said that it is a shortcut to reduce risk.
Detection, countermeasures, and education of internal impropriety threats
ObserveIT is an internal fraud countermeasure solution developed by ObserveIT (headquartered in the United States). Record user operations and visualize internal fraud risks with User Behavior Analytics to prevent information leaks caused by human error as well as malicious acts.
identify unsanctioned behavior;
discourage
- Abuse of admin rights
- Bypass security settings
- access you don't need
Intentional information leak risk
eliminate careless behavior
- How to use SaaS apps safely
- How to avoid accidental data leaks
- how to avoid malware
Risk of information leakage due to human error
Observe IT
Features of ObserveIT
- “People”: Focus on “users (people)” instead of conventional internal fraud countermeasures that focus on “data” and monitor the behavior of privileged users, vendors, outsourced contractors, and general employees
- “Detection”: Visualize internal fraud risks by scoring user operations with ObserveIT’s unique analysis algorithm. Early detection of signs of internal improprieties
- "Education": Improve security awareness by notifying users of policies, deter careless operations, and reduce the risk of internal improprieties
- "Prevention": Identify users at risk of internal fraud, prevent malicious operations before they occur, and block future fraud
- “Investigation”: In conjunction with the operation trail recording function, analysis using metadata enables prompt forensics in the event of an incident.
- More than 1,400 companies worldwide
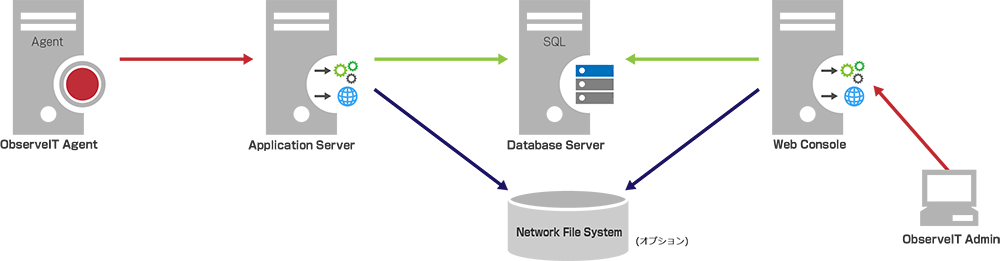
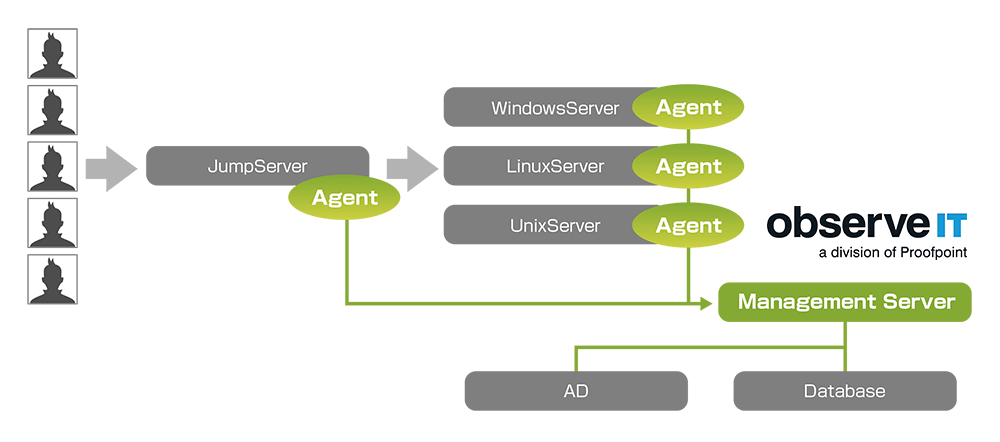
System configuration and required components
ObserveIT Agent
- Windows: Record on-screen operations and send recorded data to Application Server
- Unix/Linux: Record SSH/Telnet sessions and send recorded data to Application Server
Observe IT Management Server
- Application Server (IIS): Collect and manage operation trails from Agent, generate alerts, send recorded data to Database Server
- Web Management Console (IIS): System settings, viewing/searching recorded data, creating reports,
- Database Server(SQL): Stores Config, metadata and recording data
System configuration overview
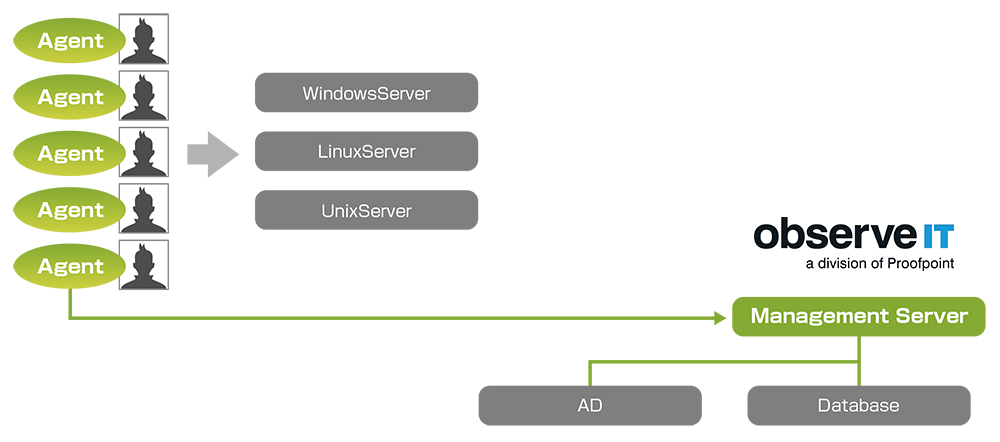
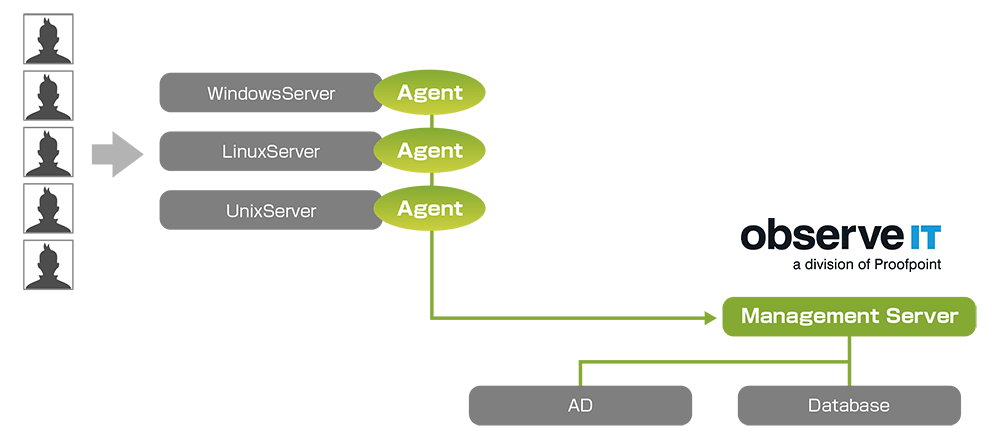
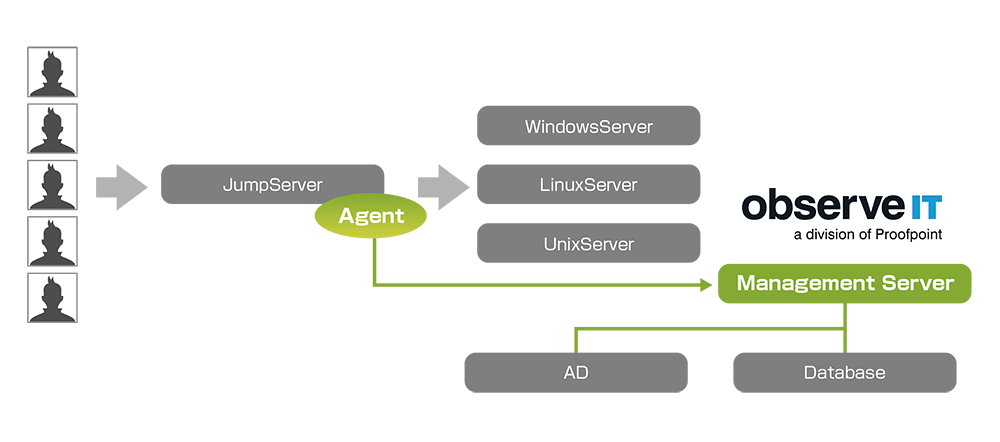
With ObserveIT, you can choose from the following 4 patterns of system configuration according to your application.

(1) Save client operation trail
(2) Save server operation trail
(3) Save jump server operation trail
(4) Jump server + save server operation trail
*Trademarks
- UNIX® is a registered trademark of The Open Group in the United States and other countries.
- Linux® is a registered trademark of Linus Torvalds in Japan and other countries.
- Windows, IIS, and SQL Server are registered trademarks of Microsoft Corporation in the United States and other countries.
Inquiry/Document request
Macnica Proofpoint Co., Ltd. Product Manager
- TEL:045-476-2010
- E-mail:proofpoint-sales@macnica.co.jp
Weekdays: 9:00-17:00