Infoblox
インフォブロックス
クラウド型プロテクティブDNS「BloxOne Threat Degense」
BloxOne Threat Defenseとは?
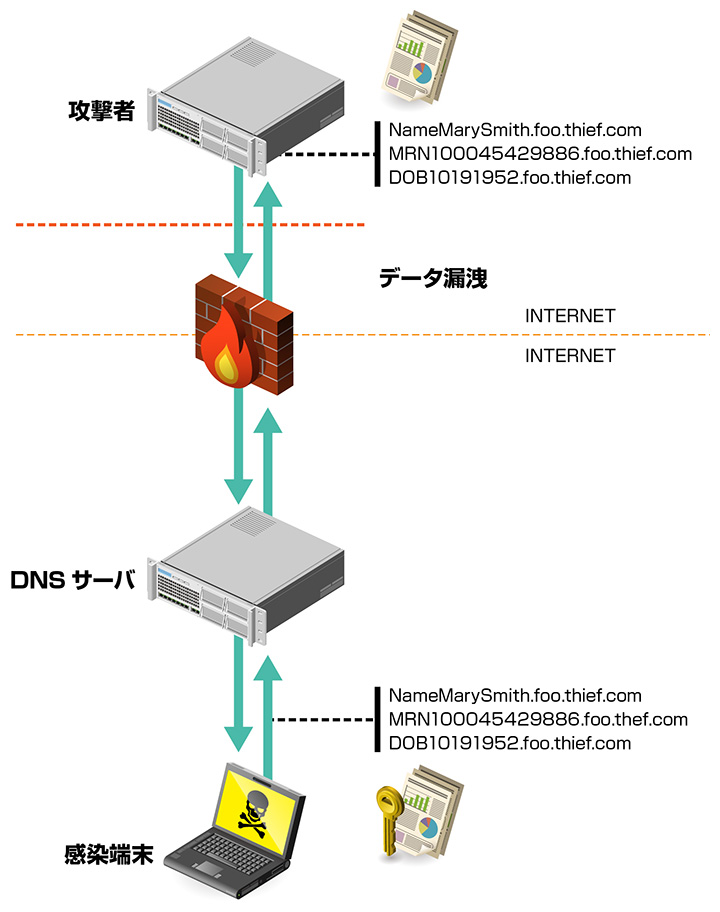
Infoblox社が提供する「DNS Firewall」のクラウドサービスです。マルウェアによるアウトバウンドのDNSベースの通信を遮断することで、ボットネットおよびC&Cサーバとの接続を防ぎます。
BloxOne Threat Defense 主な機能
- 悪意のあるドメインへのDNSクエリの監視・遮断
- 悪意のあるDNSクエリ(DNSトンネリング)を振る舞い検知により遮断
- ユーザ情報として、IPアドレス、MACアドレス、ユーザー名、デバイス情報を取得
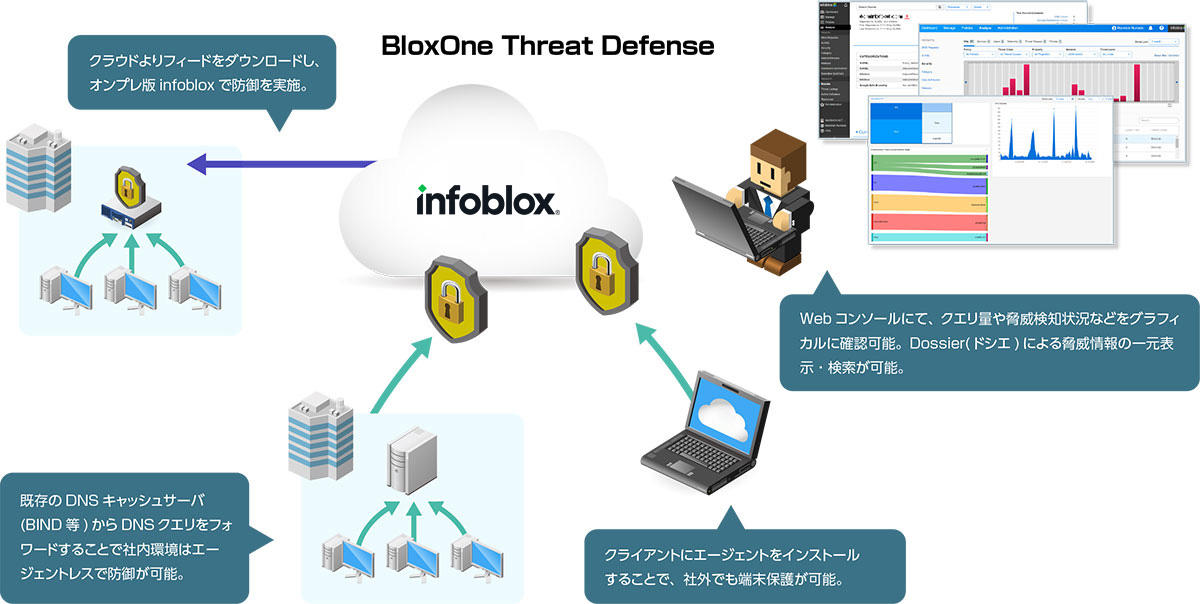
BloxOne Threat Defense導入イメージ
14種類のフィードによる防御
| フィード名 | 詳細 |
|---|---|
| Base (base.rpz.infoblox.local) |
APT、ボットネット、感染したホスト/ドメイン、エクスプロイトキット、悪用されているDNSサーバ、BogonなIPアドレスのシンクホールなど悪意のあるサイトのホスト名(FQDN)によって構成されたブラックリスト |
| AntiMalware (antimalware.rpz.infoblox.local) |
C&Cサーバ、マルウェア配布サイト、現在活動しているフィッシングサイトなど脅威のあるサーバのホスト名(FQDN)によって構成されたブラックリスト |
| Ransomeware (ransomware.rpz.infoblox.local) |
ランサムウェア(身代金マルウェア)の接続先、もしくは配布サイトのホスト名(FQDN)によって構成されたブラックリスト |
| Bogon (bogon.rpz.infoblox.local) |
インターネットの経路制御において、広告可能アドレスとして登録されていないアドレスブロック(IPアドレス/サブネット)によって構成されたブラックリスト*ルーティングテーブルに本来現れるべきではない経路情報を”Bogon経路”と言う。 IANAによる割り振りが行われていない未割り振りIPアドレス、プライベートIPアドレス、 IANAが予約しているIPアドレスなどが含まれています。 |
| DHS_AIS_IP (dhs-ais-ip.rpz.infoblox.local) |
米国国土安全保障省(DHS)のAIS(Automated Indicator Sharing)プログラムにて、サイバー脅威情報としてプログラム参加パートナーと共有されたIPによって構成されたブラックリスト |
| DHS_AIS_Domain (dhs-ais-domain.rpz.infoblox.local) |
米国国土安全保障省(DHS)のAIS(Automated Indicator Sharing)プログラムにて、サイバー脅威情報としてプログラム参加パートナーと共有されたホスト名(FQDN)によって構成されたブラックリスト |
| AntiMalware_IP (antimalware-ip.rpz.infoblox.local) |
C&Cサーバ、マルウェア配布サイト、現在活動しているフィッシングサイトなど脅威のあるサーバのIPアドレスによって構成されたブラックリスト |
| Bot_IP (bot-ip.rpz.infoblox.local) |
感染を拡大するためにマルウェアが利用するボットのIPアドレスによって構成されたブラックリスト |
| ExploitKit_IP (exploitkit-ip.rpz.infoblox.local) |
感染させるために悪意のあるプログラムを含むマルウェア配布サイトのIPアドレスによって構成されたブラックリスト |
| Malware_DGA (malware-dga.rpz.infoblox.local) |
マルウェアのドメイン生成アルゴリズム(DGA)で生成されるC&Cサーバとして使用できるドメイン名で構成されるブラックリスト |
| TOR_Exit_Node_IP (tor-exit-node-ip.rpz.infoblox.local) |
Tor出口ノードのIPアドレスによって構成されたブラックリスト*Tor出口ノードは、暗号化されたTorトラフィックがインターネットにつながるゲートウェイです。 |
| SURBL_Multi (multi-domain.surbl.rpz.infoblox.local) |
パートナー企業のSURBL社より提供されるアクティブマルウェア、フィッシング、ボットネット、スパムドメインに関する最新の情報を含む悪意のあるドメインのブラックリスト |
| SURBL_Fresh (fresh-domain.surbl.rpz.infoblox.local) |
パートナー企業のSURBL社より提供される悪意のある新たに活動が観測されたドメインのブラックリスト |
| SURBL_Multi_Lite (surbl-lite.rpz.infoblox.local) |
SURBL_MultiフィードをLowスペックモデルで利用できるように、最新かつ完全に悪意のあるサイトのみに絞ったブラックリスト |
振る舞い検知機能-Threat Insight-による防御
BloxOne Threat Defenseの特徴
1.DNSを利用したマルウェアをブロック
マルウェアは名前解決を悪用し、DNSキャッシュサーバを踏み台にすることで、既存のセキュリティ対策での多層防御をすり抜けます。これらの攻撃に対し、悪意のあるDNSクエリを遮断することで、標的型攻撃による情報漏えいをDNSベースでブロックすることが可能です。
2.クライアントにエージェントをインストールするだけで即時利用可能
既存のネットワーク構成を変更することなく、サービスをご利用いただけます。また、エージェントをインストールすることで端末特定が可能になり、クライアントのアクティビティをWebのGUI管理画面から一元管理できます。
3.リモートアクセス環境におけるセキュリティ強化
社内でのセキュリティ対策は万全でも、社外の持ち出し端末からのアクセスへの対策は十分出来ていない場合が多くありませんか?BloxOne Threat Defenseはこれまで制御できなかった社外での不正通信を遮断します。
オンプレソリューションとのシームレスな連携
ポリシーの統合マネジメント、可視化、レポーティングと分析
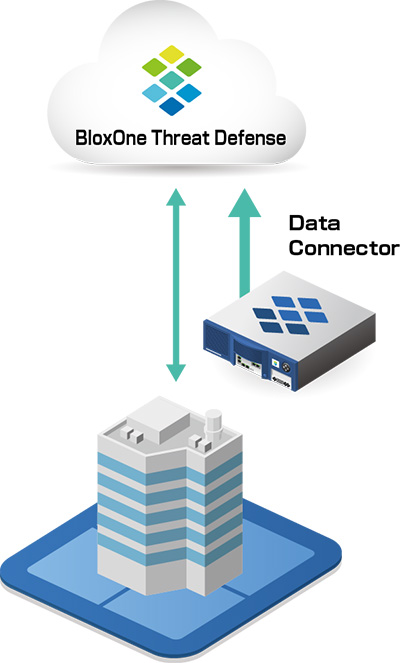
- オンプレ、リモートの各ユーザに対して個別のポリシー、または共通のポリシーが設定可能
- Data Connectorを利用し、オンプレ側のInfobloxのデータをCloudへ送信し、DNSセキュリティの統合分析が可能
- 各ユーザ/デバイスについてオンプレのLAN環境とリモートの環境の往来について、履歴等を確認することが可能
- ユーザ情報として、MACアドレス、デバイス情報、DHCPリース履歴、物理的な位置(建物、拠点)を可視化
お問い合わせ・資料請求
株式会社マクニカ Infoblox 担当
- TEL:045-476-2010
- E-mail:infoblox-sales@macnica.co.jp
平日 9:00~17:00