
CyberArk
cyber arc
Public Cloud Entitlement Optimization - Cloud Entitlements Manager
What is Cloud Entitlements Manager (CEM)?
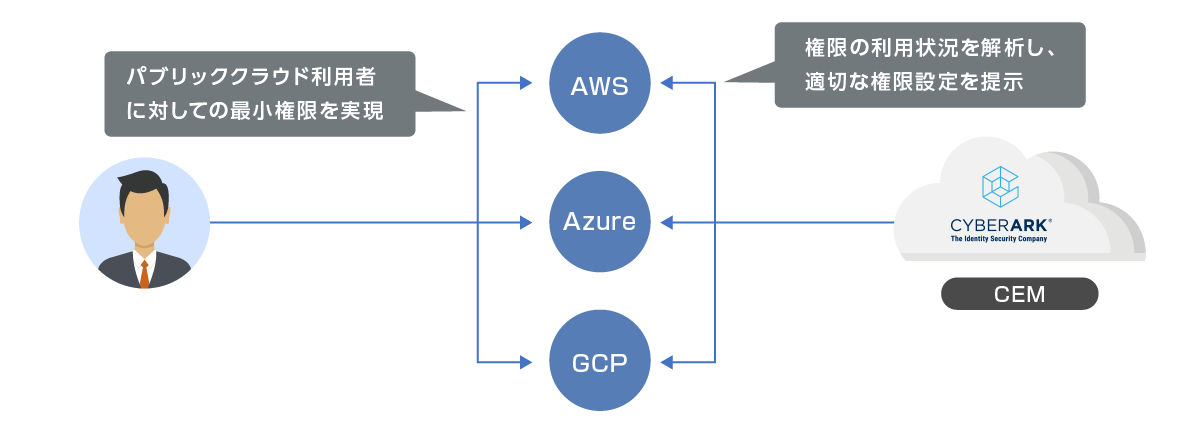
- Cloud Entitlements Manager (CEM) is a product in a category called CIEM that provides "visualization, detection, and correction" of user entitlements in public clouds such as AWS, Azure, and GCP *1.


Visualization
in multi-cloud
Visualize user role permissions


Detection
excessive authority,
Detect Shadow Admin privileges

fix
To achieve least privilege,
Suggestion of desired permission settings
*1 CIEM = Cloud Infrastructure Entitlements Management
Provide the ability to protect the rights management of public cloud environments
Why is CEM necessary?
- Permission issues often occur in public clouds
- The reason for this is that there are a wide variety of permissions and services in the public cloud, so if you try to manage permissions only by human hands, you will end up with inadequate settings to transfer permissions without realizing it.
- Permission issues
- Many problems called "excessive privileges" and "Shadow Admin" occur

A state in which more authority than necessary for business and operation has been granted
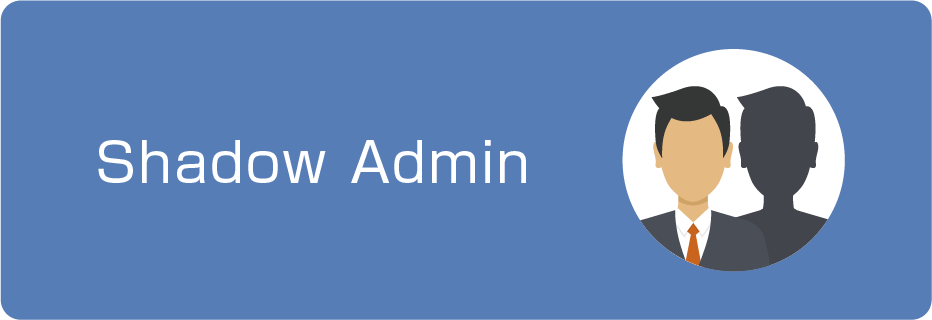
Although it is not explicitly granted administrator privileges, in fact, by using privileges, it is possible to perform operations equivalent to administrators.
Problems Caused by Excessive Privileges and Shadow Admin
- Excessive privilege/Shadow Admin can be abused for both "internal fraud" and "external attack".

・Access to data that should not be accessed
・Bringing out information
・System failures and incidents due to erroneous operations

・Access to confidential information by attackers
・Access to other users by exploiting privileges, privilege escalation
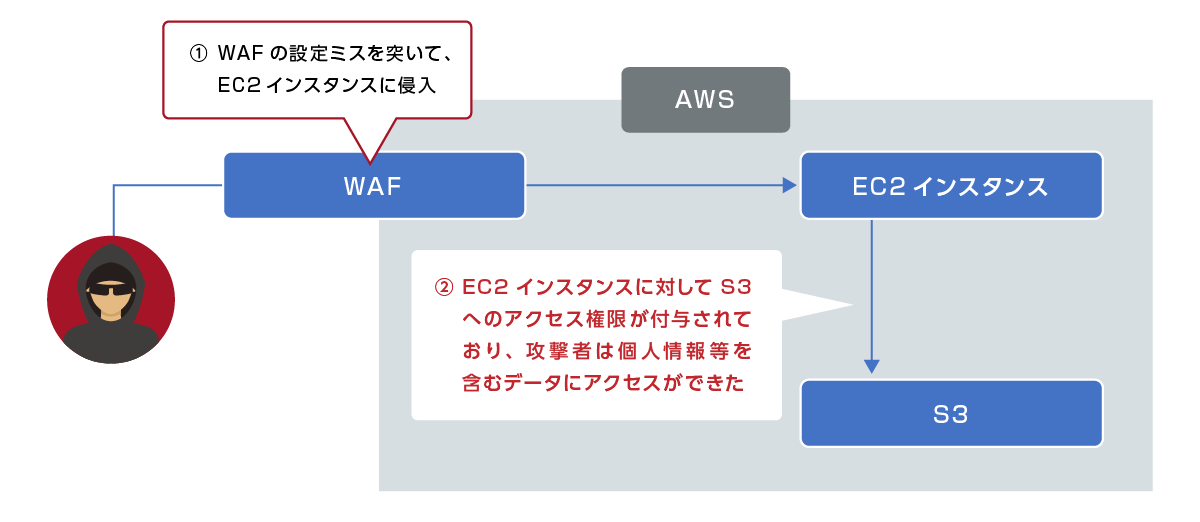
Incident caused by improper setting of authority
- Case of an overseas financial company
- March 2019 Through unauthorized access to the AWS environment, attackers succeeded in stealing bank account numbers, etc. of about 80,000 customers.
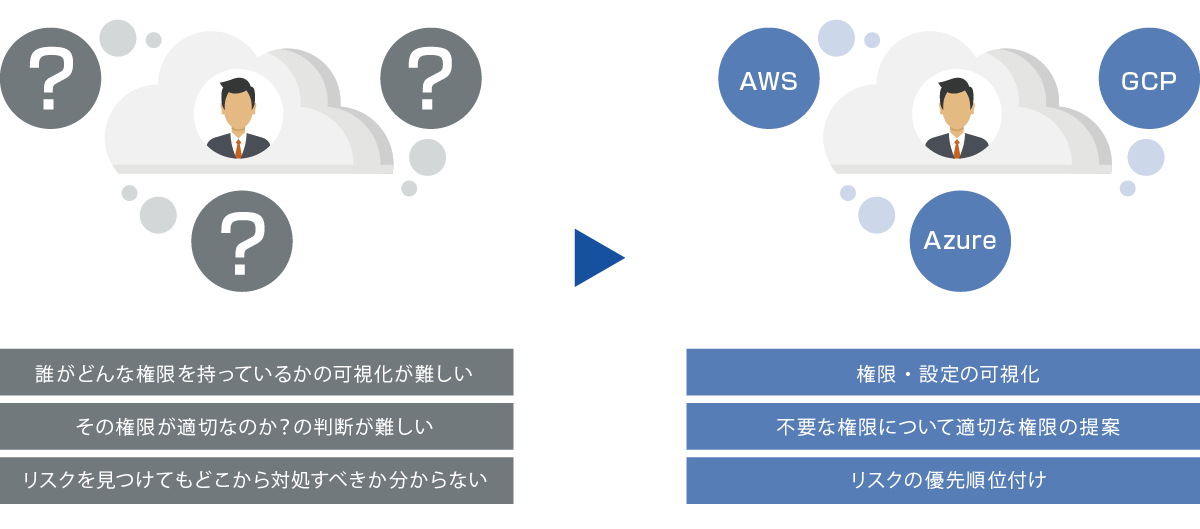
Problems solved by CEM
- Manually dealing with public cloud permissions issues presents a number of challenges. CEM is a solution that comprehensively solves these issues.
CEM's Position in "Zero Trust"
- In order to achieve zero trust, it is necessary to thoroughly implement the “principle of least privilege”.
- CEM is a solution for realizing zero trust in cloud environments by realizing "least privilege" on public clouds.
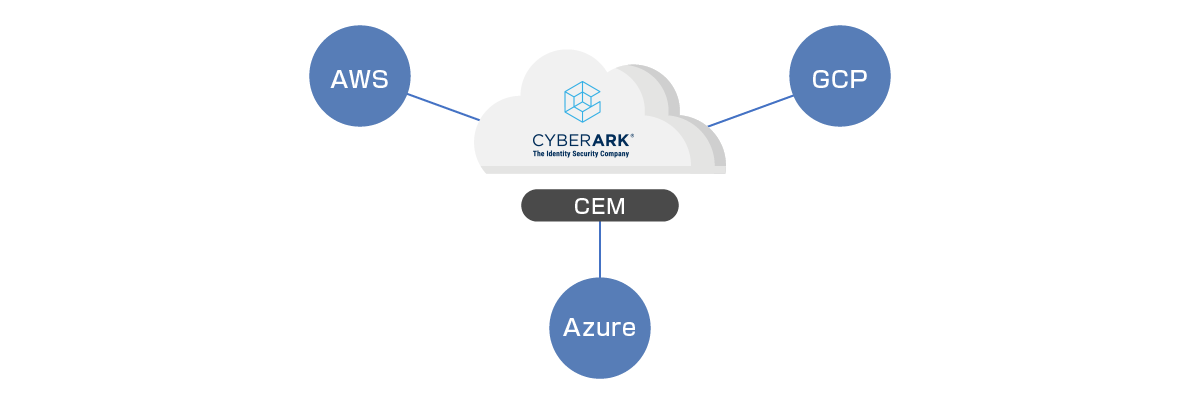
CEM: deployment configuration
- Complete SaaS type solution
- CEM is a SaaS product, so there is no need to prepare a server for the customer environment.
- Deployment can be easily performed by setting up linkage with each public cloud on CEM.
- A free trial is also available. Please contact us if you are interested.
Inquiry/Document request
Macnica CyberArk
- TEL:045-476-2010
- E-mail:macnica-cyberark-sales@macnica.co.jp
Mon-Fri 8:45-17:30
