
CyberArk
cyber arc
Protecting IDs - From Management to Protection
Portfolio that comprehensively covers identity security
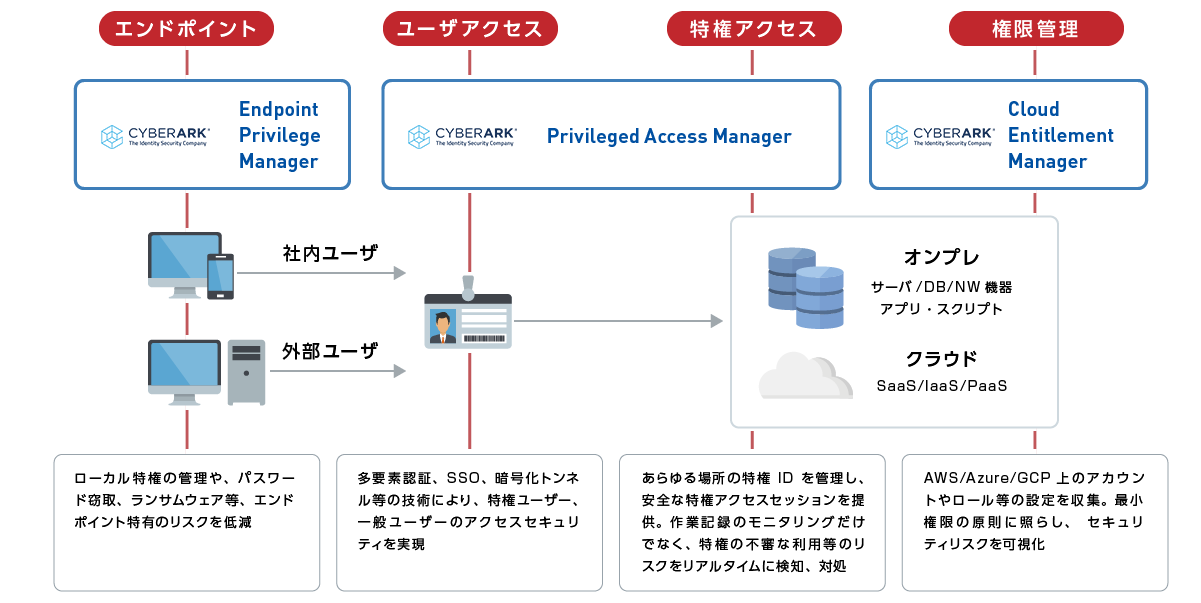
[Product 1] EPM (Endpoint Privilege Manager)
Manage permissions for widely used client terminals.
It controls client terminal privileges that are exploited for lateral movement of cyber attackers, creation of backdoors, disabling of security software, impersonation, and information exploitation. Operation-based management that pursues control that does not impair convenience realizes a secure and free environment.
[Product 2] PAM (Privileged Access Manager)
Manage privileged IDs that have a large business impact if misused or abused.
It provides automatic password updates, secure access sessions, records when, where, who, and what, prepares for audits and incidents, and streamlines management of global privileged identities.
[Product 3] CEM (Cloud Entitlement Manager)
Manage permissions and settings in a huge number of IaaS.
CEM visualizes the granted access rights, assesses risks, and provides practical and recommended policies.
[Product 4] Dynamic Privilege Access (DPA)/Secure Cloud Access (SCA)
Achieve "Zero Standing Privilege", a measure that minimizes attack vectors. Provides temporary access to on-premise systems and public cloud accounts.
Seminar
これから開催 開催終了 {{ item.title }}
{{ item.seminar_start_date__display_1 }} {{ item.seminar_place__display_1 }}
video on demand
company description
| company name | CyberArk Software Inc. |
|---|---|
| Established | January 2017 |
| location | 13F Pacific Century Place, 1-11-1 Marunouchi, Chiyoda-ku, Tokyo 100-6208 |
| representative | President and Executive Officer: Hidenori Kurahashi |
| website | https://www.cyberark.com/japan/ |
Inquiry/Document request
Macnica CyberArk
- TEL:045-476-2010
- E-mail:macnica-cyberark-sales@macnica.co.jp
Mon-Fri 8:45-17:30



