Products/Services
product
- Centralized Privileged Identity Management Solution - Privileged Access Manager
- Automated Certificate Management – CyberArk Certificate Manager (formerly Venafi)
- Endpoint Privileged Identity Protection - Endpoint Privilege Manager
- Zero Standing Privilege Solution - Secure Cloud Access/Secure Infrastructure Access

CyberArk
cyber arc
*Zero Standing Privilege: An approach to minimize attack vectors by having privileged IDs not exist on a system and only exist when a user uses them.
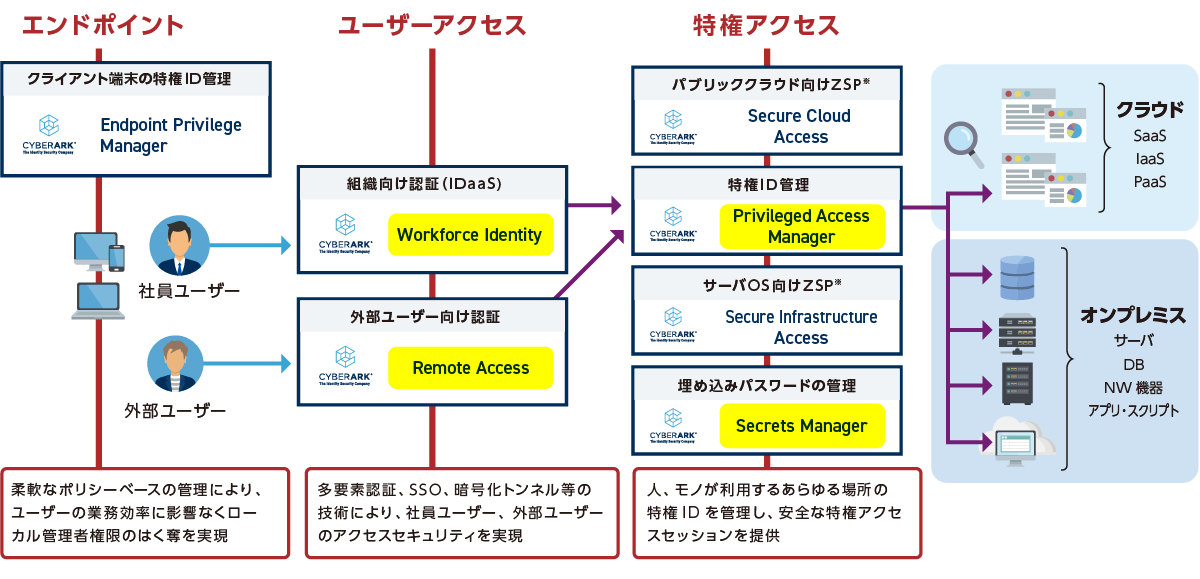
Centralized Privileged Identity Management Solution - Privileged Access Manager
[Point ①] Centralized management of a wide range of managed objects, from on-premise servers to cloud systems
There is a huge range of managed and linked devices, enabling all privileged ID management on a single platform.
On-premise or cloud
Achieve privileged ID management for all products
Achieve privileged ID management for all products
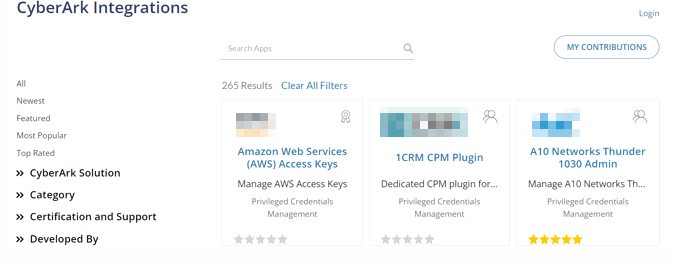
- Representative solutions and connection plug-ins are
Published on CyberArk Market Place
※Reference: https://cyberark-customers.force.com/mplace/s/ - Automatically generate connectors for unsupported devices
Plugin Generation Utility (PGU) is provided free of charge
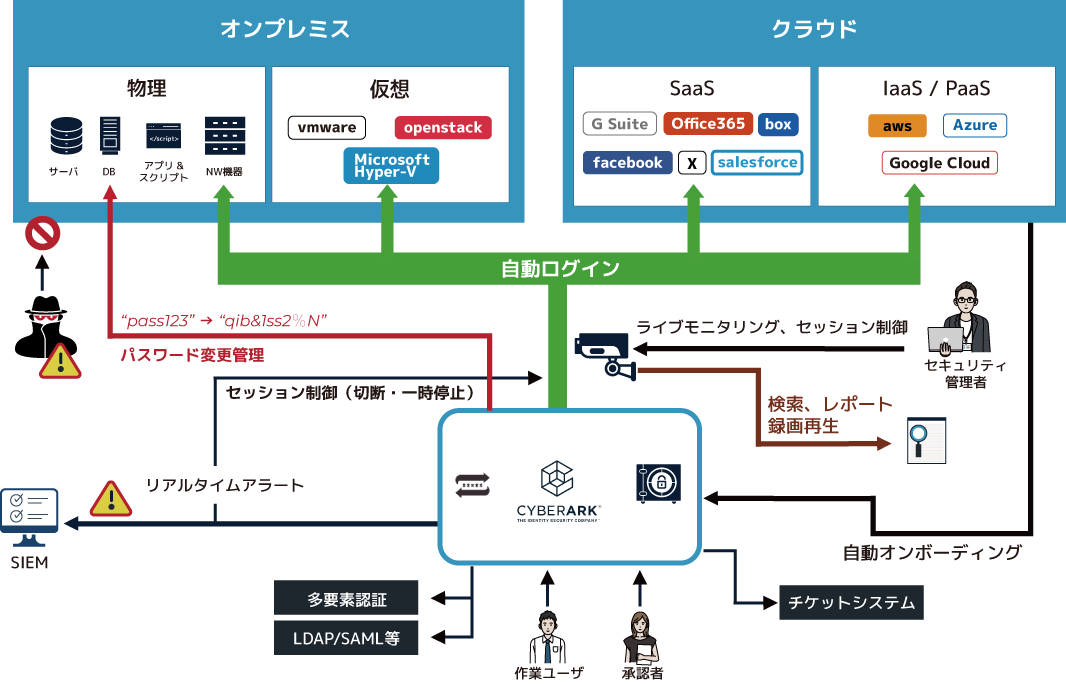
[Point ②] Real-time detection function for unauthorized use of privileges
It is possible to monitor the usage of privileged IDs in real time and detect behavior that is a precursor to an incident.
![[Point ②] Real-time detection function for unauthorized use of privileges](/business/security/manufacturers/cyberark/image/cyberark_pam_dr04_2.png)
[Point 3] Managing passwords embedded in applications and scripts
By working with CyberArk, you can safely retrieve passwords when needed, preventing the risk of passwords for managed systems being leaked from the application side.
![[Point 3] Managing passwords embedded in applications and scripts](/business/security/manufacturers/cyberark/image/cyberark_pam_dr05_2.png)
[Point 4] Issuance of privileged accounts for external vendors and remote workers
VPN-less and password-less, you can access it remotely.
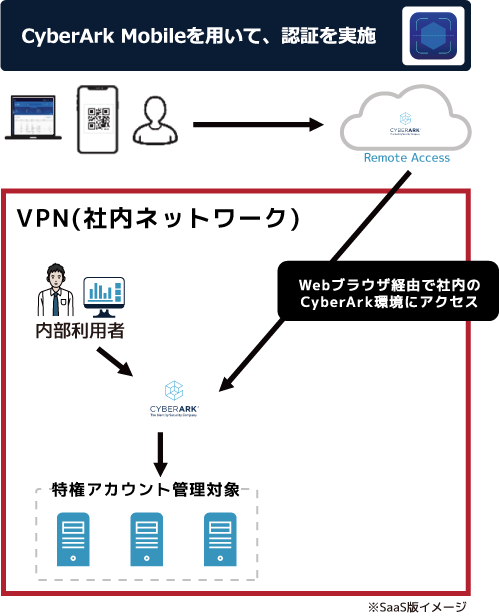
All users need is a browser and a smartphone
- No VPN or special agent software required
- It is safe because the secret (password or hash) is not left on the terminal.
No pre-provisioning required
- Receive an invitation from the administrator and complete biometric registration
- It's OK if you access during the permitted time period
End-to-end encrypted tunnel
- Provides an end-to-end encrypted tunnel environment between the client terminal and the destination
Inquiry/Document request
Macnica CyberArk
- TEL:045-476-2010
- E-mail:macnica-cyberark-sales@macnica.co.jp
Weekdays: 9:00-17:00
