
Vectra AI
Vectra AI
Instantly detect increasingly sophisticated attacks with network visualization. What is an NDR solution that contributes to solving problems in the manufacturing industry?
Some mid- to large-scale manufacturing companies with more than 1,000 employees must be aware of the security risks of not being able to visualize their networks due to issues unique to the manufacturing industry. In this article, we introduce a case study of solving various security issues by visualizing the entire network using the NDR (Network Detection and Response) solution, which is a next-generation security that is currently attracting attention.
Common themes faced by the manufacturing industry are seen in automobile-related companies
Manufacturing companies of a certain size or larger have common backgrounds and issues in terms of security. The first is having multiple bases. When the number of bases increases due to mergers or grouping, the network environment was originally different, so it is easy to create holes for threats.
The second is the diversification of forms of employment. Employees of various occupations are working from the production site to sales/sales, clerical/administration, and even research departments, and it is common for the security policies to differ from department to department.
And third, this is not limited to the manufacturing industry, but while we handle a lot of confidential data including development information, in recent years we are actively promoting data utilization and IoT introduction, increasing security holes. Doing things. For example, IT assets (all devices connected to the network, such as IoT devices, IP phones, printers, and verification environments) that had insufficient security measures due to platform issues, although they possessed IP, were left untouched. there are many cases.
Under these circumstances, many manufacturing companies have said that since the spring of 2020, they have been attacked frequently since the spring of 2020, as they rapidly built a remote work environment with a VPN in response to the corona disaster. be asked.
What they have in common is that they have not been able to visualize the network. Because it is difficult to centrally understand the security status of the diverse networks that span multiple locations, even if an attack occurs, it cannot be detected immediately, which inevitably leads to delays in response.
Company A, which manufactures automobile-related electrical equipment and precision parts, had exactly this problem. Company A, which has several factories nationwide and over 1,000 employees, has expanded its business in recent years by grouping local companies. Mr. B, who is the manager of the information system department of Company A, describes this situation and related concerns as follows.
“About five years ago, we felt that the network environment, devices used, and installed services differed from company to company, and that we were unable to implement security measures with a sense of unity. Although it did not lead to major damage, it did cause some trouble.In this day and age, being attacked itself is becoming common, so I intend to take countermeasures. However, we failed to notice the attacker's intrusion at an early stage, and it was discovered only after a log investigation after the fact, so it became a problem within the company."
Why is it important to visualize the entire network?
The mainstream of cyber security is shifting from measures to prevent intrusions to methods to detect intrusions and prevent actual damage, as intrusions are a matter of course. For that reason, it is extremely important to constantly monitor the network and visualize the events that occur there.
“the Company also have anti-virus products, so we can detect clearly suspicious behavior. The damage was minor, but if a serious incident were to occur, it would lead to a decline in the company's reputation, so immediate countermeasures were required.As attacks can be quickly noticed from the site, a tool that can broadly control network conditions. There was a growing need for this," said Mr. B. A few years ago, Company A introduced a vendor's tool and tried to visualize the network. However…….
"The tool graphically represents the network status, and the screen is certainly cool, but conversely, the GUI lacks clarity and is difficult to see, making it difficult to investigate cases. , there was a lot of noise (false positives and false positives), and in the end, it put a heavy burden on the SOC.”
Under such circumstances, Company A introduced telework to some departments as part of its work style reforms about a year ago, and the threat of attacks that exploited VPN vulnerabilities became a reality. The company approached Macnica in search of a solution that could visualize the network in an easy-to-understand manner and detect a variety of threats, including lateral movement, even as its base expanded.
Upon receiving the request, Macnica first interviewed Company A. They asked about the issues the company currently faces, such as incidents that have occurred in the past, concerns about the tools currently in use, and how Company A plans to diversify work styles in the future, as well as their outlook for the future. As a result, Macnica proposed and Company A introduced "Vectra AI," an NDR solution that uses AI to visualize the entire network and detect attacks at an early stage.
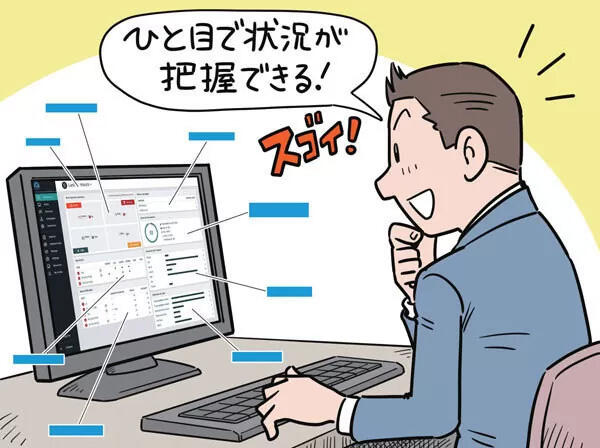
"Vectra AI" enhances security and operability with an easy-to-read screen
NDR is attracting attention as a next-generation security following SIEM and EDR. It is a solution that provides a bird's-eye view.
Among NDR, "Vectra AI" is a popular product for its easy-to-understand GUI, ease of operation, and high AI threat detection rate. The dashboard allows you to check the threat level of the host at a glance, and displays important assets, high-risk terminals, threat detection status, etc. on a single screen, helping to reduce the operational load. For AI, there are global learning (supervised machine learning) that utilizes data from all over the world, and local learning (unsupervised machine learning) that is based on the unique environment and behavior of the company, minimizing false detections and over-detections. You can suppress and detect threats. By combining the results detected by local learning and global learning, the threat level of the detected terminal is automatically evaluated, and the terminals with high threat level can be visualized as a list on the GUI.
“That being said, I had previously felt that the previous tool from another vendor was difficult to use and had detection issues, so even after deciding to use it this time, I was a little worried about its effectiveness. I was also worried about whether we would be able to install it in the appropriate location,” said Mr. B. Regarding the effectiveness, he said he was reassured by the product evaluation through PoC using actual equipment. Regarding the installation, Mr. B said that Macnica 's friendly response and installation support such as settings tuning gave him peace of mind.
“In recent years, there has been an increase in mergers, and it was not possible to immediately visualize the entire network by installing 'Vectra AI' on the core switch. We introduced "AI" and started monitoring for the purpose of countermeasures against threats that occur on internal servers.We confirmed the effect by visualizing important assets, etc., and by expanding the monitoring to other areas, We were able to visualize the entire system.In addition, EDR takes time and effort such as kitting, but Vectra AI has the advantage of being agentless and can be introduced.In addition, even though we own IP, Vectra AI can visualize and detect IT assets (IoT devices, IP phones, all devices in the development environment, etc.) that could not be covered by our security products. It's been extremely helpful."
It took about three months from the decision to use the system to the completion of the introduction, but Mr. B recalls that he did not feel any difficulty in the process itself. As a result, we were able to successfully solve the problem of not being able to notice an attacker's intrusion due to the inability to visualize the network. Not only has it enabled early incident response, but it has also made it possible to capture the overall picture of the network, which was not visible in the past.

“We have received positive feedback from our customers regarding our higher level of security, and our transactions have become more active. I heard that they have begun to consider expanding into the Pacific region,” said Mr. B.
Although NDR alone can be effective in network visualization, combining it with EDR increases security even further. Macnica has a system in place to discuss with customers, propose optimal solutions from multiple portfolios, and provide total support up to the operational phase. If you are a company that wants to improve your security through network visualization, why not take this opportunity to consult Macnica and consider introducing "Vectra AI"?

Contact information
Macnica Co., Ltd.
Vectra AIproduct manager
- TEL:045-476-2010
- E-mail:vectra-ai-sales@macnica.co.jp
Inquiry/Document request
In charge of Macnica Vectra AI
- TEL:045-476-2010
- E-mail:vectra-ai-sales@macnica.co.jp
Weekdays: 9:00-17:00


