
Vectra AI
Vectra AI
Document request
If you would like the following materials, please proceed to the application form.
| Document content | |
| User case | Kintetsu Department Store Co., Ltd. 293KB/2P PDF NEW
VectraAI covers areas that cannot be handled by existing EDR
Covering the entire network and achieving comprehensive monitoring   |
| Document content | |
| Product introduction materials | Network Detection and Response 6.27MB/26P PDF
Capture the entire network from a bird's-eye view and visualize threats that have penetrated inside - Next-Next-Gen Network AI Security
   |
| Microsoft 365 (AzureAD) security enhancement method using Vectra AI991KB /11P PDF
We will introduce the security threats of "Microsoft 365", which is the cornerstone of a company's IT infrastructure, the importance of countermeasures, and countermeasures that do not impose an operational burden.
  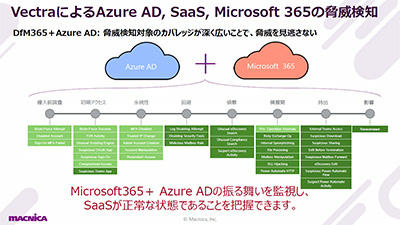 |
|
| white paper | Protecting Azure AD with Vectra AI ITDR - Easy to install and operate! Measures against unauthorized use of authentication information - 745KB/9P PDF
   |
| 3 Reasons Why EDR Is Not Enough and Countermeasures - Comprehensive Countermeasures against Internal Threats with EDR and NDR - 7.75MB/6P PDF
EDR (Endpoint Detection and Response) is attracting attention as an effective solution as it is difficult to completely prevent attackers from intruding. However, it has been confirmed that some attacks cannot be dealt with by EDR alone, which emphasizes endpoint protection. This document introduces effective countermeasures against such attacks.
 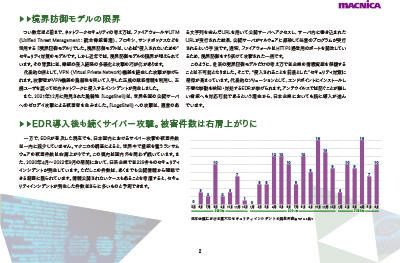  |
|
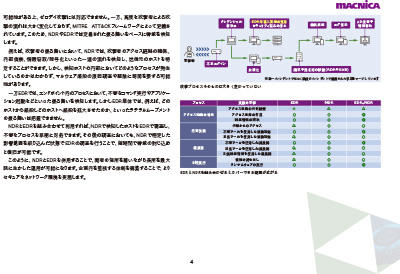
| Limitations of Sandbox Security Measures to Prevent Intrusions - Advantages of NDR assuming Intrusion - 1.84MB/5P PDF
In this document, we will explain the "limitations of security measures using sandboxes" and "the background to the rapid increase in companies considering replacement with NDR products."
   |
|
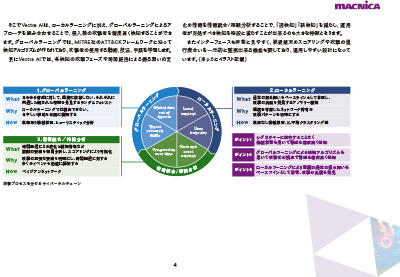
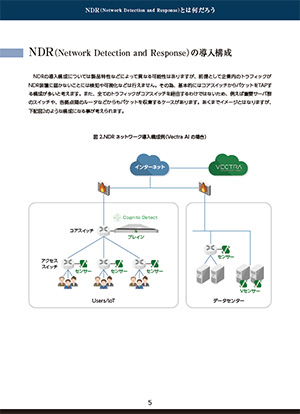
| What is NDR (Network Detection and Response)? 3.67MB/16P PDF
While answering questions such as "What is NDR?" and "How is it different from EDR?"
   |
|
| catalog | What are NDR solutions that contribute to solving problems in the manufacturing industry1.56MB /2P PDF
We will introduce in an easy-to-understand manner, with illustrations, examples of how the network detection and response (NDR) solution, which is currently attracting attention, visualizes the entire network and solves various security issues.
 |
Inquiry
In charge of Macnica Vectra AI
- TEL:045-476-2010
- E-mail:vectra-ai-sales@macnica.co.jp
Weekdays: 9:00-17:00


