
Skyhigh Security
sky high security
Fukuoka University

Automatically performs cloud service usage visualization and risk assessment.
Realize access control including operation flow design by linking with Proxy.
- Unable to grasp the usage status of cloud services
- There is no way to control even if high-risk cloud services are used
- I want to consider security measures that take into account the operation


- Automatically visualize cloud service usage
- Automated risk assessment of cloud services
- Realize access control including operation flow design by linking with existing proxy products

Fukuoka University Information Technology Center Associate Professor
Mr. Sho Sho Fujimura
User's Voice
As the use of ICT by faculty, staff and students accelerates, cloud security is essential to protect personal information and valuable data. With the introduction of MVISION Cloud, we can easily stop the use of suspicious cloud services, which we believe will be of great help in preventing information leaks.
Issue: Unable to grasp the actual usage of cloud services
Fukuoka University has established a "security zone" and has established operational guidelines to store information that should not be leaked, such as student personal information, "within the zone" under the university's control. In addition to cloud services such as Box and Gmail designated by the university as within compartments and outside cloud services such as Google Drive that are known to be used, what kind of cloud services are used by whom and how much? They had a sense of crisis about not being able to grasp the actual usage situation.
Survey: What are the best solutions for data breach risk preparedness?
Mr. Fujimura and others decided to work on strengthening security measures related to the use of cloud services, starting with the understanding of the actual use of cloud services.
"Information to be protected" refers to information assets owned by the university (personal information of students, research data, etc.), "Who handles that information" refers to faculty and staff members, and "Assumed security incidents (to be prevented)" refers to the use of cloud services. After clarifying that it was an information leak at the time, the solution that attracted attention while collecting information was "Cloud Access SecurityBroke (r hereinafter, CASB)".
Focusing on CASB, Mr. Fujimura first sorted out the necessary functions of CASB for solving the problems of his own studies.
Visualization of cloud service usage
Who is using which cloud service, when and how much (upload and download data volume).
Evaluation of cloud service security
What is the risk of information leakage from the cloud services being used?
For example, does it enforce multi-factor authentication, what happens to the ownership of uploaded data, has there been a security incident with that cloud service in the past?
Developing an environment for safe use of cloud services
Safety and ease of operation. Can you easily stop using high-risk cloud services?
Does the operation work become a burden on the administrator?
Selection: What is the best CASB for self-study problem solving?
In order to select the manufacturer that has the organized necessary functions and is the best, we started to compare multiple manufacturers. As a result, McAfee's MVISION Cloud (MVC) was selected.
Visualization of cloud service usage
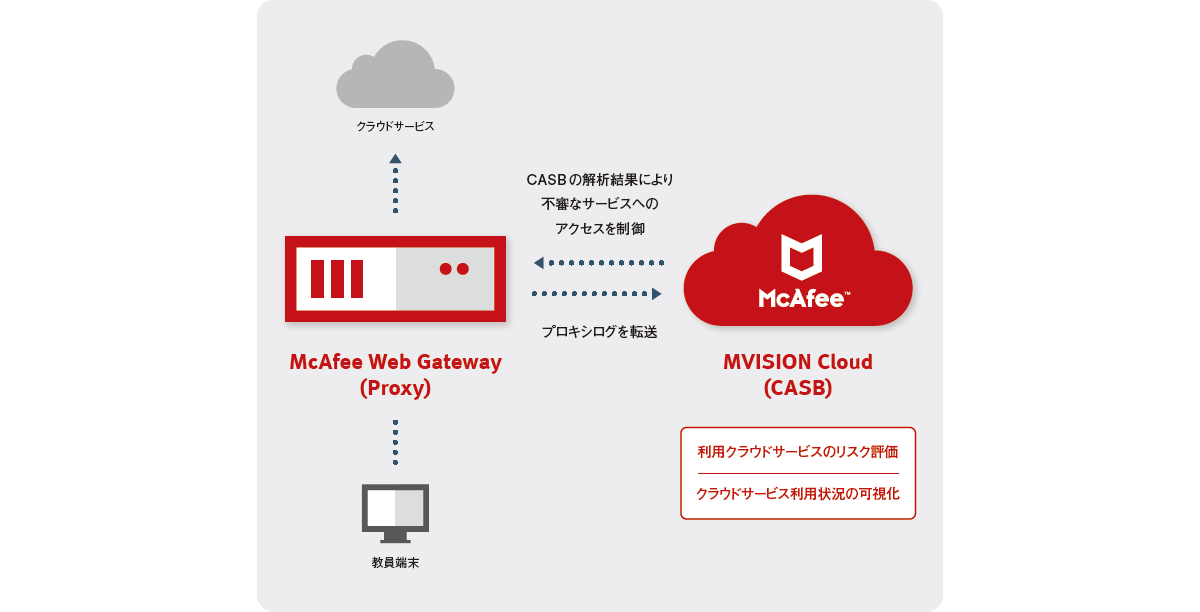
MVC can visualize user access status to cloud services via firewalls and proxies used. The point is that the usage status can be visualized without an agent via a log transfer server, and that it can be easily linked with McAfee's Proxy products as well as other companies' products.
Based on the CSA (Cloud Security Alliance) guidelines, MVC classifies cloud services into 50 risk categories into 6 risk categories and judges them according to 9 risk levels. Compared to CASB of other companies, the point is that the basis for cloud service risk judgment is detailed and easy to understand.
Developing an environment for safe use of cloud services
With MVC, if you want to restrict access to high-risk cloud services based on usage, if you have a specific firewall or proxy, the URL list for control is automatically linked to the firewall or proxy. In addition, when combined with McAfee's Proxy, one-stop operation from visualization to control of cloud service usage status and risks is also a point that leads to operational efficiency.
In addition to the essential functions,
- No need to introduce agents to clients
- No network configuration changes required
- Proxy product in use: McAfee Web Gateway
can be operated in combination with
These features that other manufacturers do not have were also reasons for the selection.
“With McAfee, you can manage and operate not only CASB (MVISION Cloud) but also Proxy (Web Gateway) in an integrated manner, so you can expect a significant reduction in management man-hours. We were able to put McAfee products into operation without any problems." (Mr. Fujimura)
Introduction: Reduce the risk of information leakage by introducing CASB with an eye on operations
Fukuoka University decided to introduce MVC.
However, implementing a solution is not the goal. Efficient and optimal operation after introduction will produce the expected effects. After introducing MVC, the operation system of the cloud service became as follows.
The daily cloud usage status is automatically visualized by MVC, and periodic report output is also automated. Based on this report, Fukuoka University and system integrators review it at regular monthly meetings to determine whether there are any dangerous cloud services or suspicious usage situations.
If there is a dangerous cloud service, set a proxy to restrict its use.
“We have created an operational system that allows us to know who is using what cloud service, and to easily stop it in case of emergency. Since the log remains, it is also useful for forensics in the unlikely event that an incident occurs. Information leakage We were able to create an effective operating system for prevention.” (Mr. Fujimura)
User Profile
|
Fukuoka University |
|
|
location |
8-19-1 Nanakuma, Jonan Ward, Fukuoka City, Fukuoka Prefecture |
|
number of students |
about 19,000 |
|
Introduction time |
2020 |
|
Introduced product name |
MVISION Cloud McAfee Web Gateway |
|
URLs |
https://www.fukuoka-u.ac.jp/ |
| Founded in 1934. Under the "Founding Spirit" and "Philosophy of Education and Research", we have 31 departments in 9 faculties and 34 majors in 10 graduate schools. We aim to be a university that makes contributions, adapts to the times, and develops globally. In 1994, we acquired a global IP address and introduced a supercomputer for the on-campus information network system. | |
Inquiry/Document request
In charge of Macnica Skyhigh Security
- TEL:045-476-2010
- E-mail:mfe-info@macnica.co.jp
Weekdays: 9:00-17:00