
F5, Inc (Shape Security)
F-Five (Shape Security)
Shape Enterprise Defense
Based on the ID and password information illegally obtained from the dark web and other companies' sites, attackers use automated communication to carry out attacks such as password list attacks and scraping, resulting in unauthorized system operations. Get information. In addition to using real ID and password information, access mimics human behavior, so it is difficult to determine whether communication is normal or malicious with current security measures.
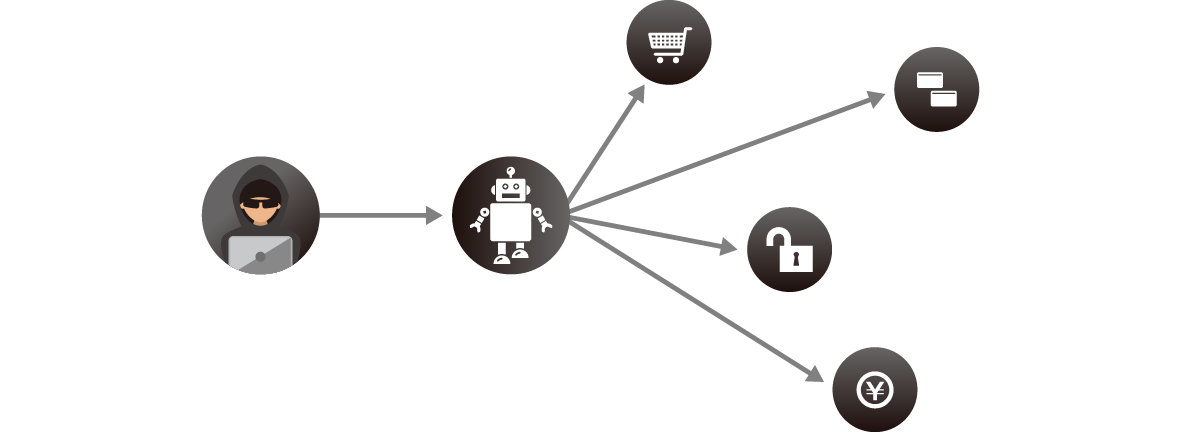
There are various attacks on automated access, as shown below, and they are becoming more sophisticated every day.
OWASP automated attack example
|
Attack method |
explanation |
| Credential Stuffing (OAT-008) | Use a bot to test whether authentication information illegally obtained through dark web, skimming, phishing, etc. can be used on other sites. Also called password list attack. |
| Account Creation (OAT-019) | Using bots to create fake accounts to launder money, disguise information, spread malware, etc. |
| Scraping (OAT-011) | Use bots to collect large amounts of data (product pricing information, hotel room rates, etc.) and reuse it elsewhere. |
| Carding (OAT-001) | Bots are used to execute payment processes in order to identify whether card data obtained illegally through dark web, skimming, phishing, etc. is useful. |
| Scalping (OAT-005) | Bots buy up tickets, exclusive items, hotel reservations, and more. Resell the purchased items at a high price. |
https://owasp.org/www-pdf-archive/Automated-threat-handbook.pdf
Shape Enterprise Defense
Shape Enterprise Defense collects a large amount of information such as mouse operation, key input status, access environment, and terminal information using its own JavaScript, making it possible to determine with a high degree of accuracy whether access is from a person or is automated. is. In addition to continuous machine learning of the obtained information, analysts analyze it in the background, making it possible to detect not only known attacks but also new attack patterns with high accuracy. is.
Features of Shape Security
精度の高い解析が可能
- Browser operation speed
- mouse and keyboard
- attacker's environment
- etc…
- Various attacks are launched against major companies every day, so a huge amount of traffic data flows to Shape
- With this huge amount of data, it is possible to improve the accuracy of machine learning and know various attack patterns
- Alerts when traffic increases/equipment malfunctions
- 24/7 monitoring
- There is no need for the customer to change the settings.
- Dynamically generate your own JavaScript code
Byte-coded for advanced obfuscation
Product line-up
- Individual support for your environment
- Providing a fully managed service
- Providing attack analysis reports
- Embedding JavaScript tags in the web server
- Change routing so that only the target communication goes through Shape
- Common policies recommended by Shape
- Providing managed services
- Change DNS name resolution destination
Inquiry/Document request
In charge of Macnica F5 Co., Ltd.
- TEL:045-476-2010
- E-mail:shape-sales@macnica.co.jp
Mon-Fri 8:45-17:30