Ivanti (formerly PulseSecure)
Ivanti
Connect Secure series
connection function
| Available applications | connection function |
|
Supports all TCP/UDP applications
|
Ivanti Secure Client (formerly Pulse Secure Client, formerly NC) |
|
Supports client-server type applications
|
Secure Application Manager (SAM) |
|
Core |
Ivanti Secure Client (formerly Pulse Secure Client, formerly NC)
Tunneling allows you to use all TCP/UDP applications used in LAN, such as e-mail, file sharing, audio/video, and ICMP (for network monitoring such as Ping and traceroute). You can also access client terminals from the center using the tunnel established by Ivanti Secure Client.
In addition, the Connect Secure series automatically selects ESP mode using ESP, which is also used in IPSec, and SSL mode according to the access environment. This greatly improves performance.
Secure Application Manager (SAM)
Client-server type applications can be used by port forwarding. There are two types of SAM, JSAM and WSAM.
- JSAM
JSAM uses Java applets and can take advantage of fixed port TCP applications. Major groupware such as Lotus Notes and Microsoft Exchange, e-mail, etc. can be used.
- WSAM
WSAM uses ActiveX and can be used for fixed/variable port TCP applications and unicast UDP applications.
Core
- Web access
The reverse proxy method allows web applications to be used on a browser basis. You can control access at the URL level.
- file sharing
Browser-based file sharing allows you to upload and download files. You can also control access at the folder and file level.
Security
certification
In addition to basic authentication (user ID/password), you can achieve authentication according to your requirements, such as linking with electronic certificates and one-time password solutions. You can also strengthen authentication with two-factor authentication, which combines basic authentication and electronic certificate authentication.
It supports various authentication platforms such as external authentication such as Active Directory, RADIUS, and LDAP, and local DB (internal DB).
dynamic access control
Based on the group to which the user belongs, you can dynamically assign the internal resources that can be accessed after connecting. For example, sales reps can access mail servers and file servers, while sales managers can access accounting servers in addition to those. In general, access control is performed dynamically using user attributes set in Active Directory, LDAP, etc.
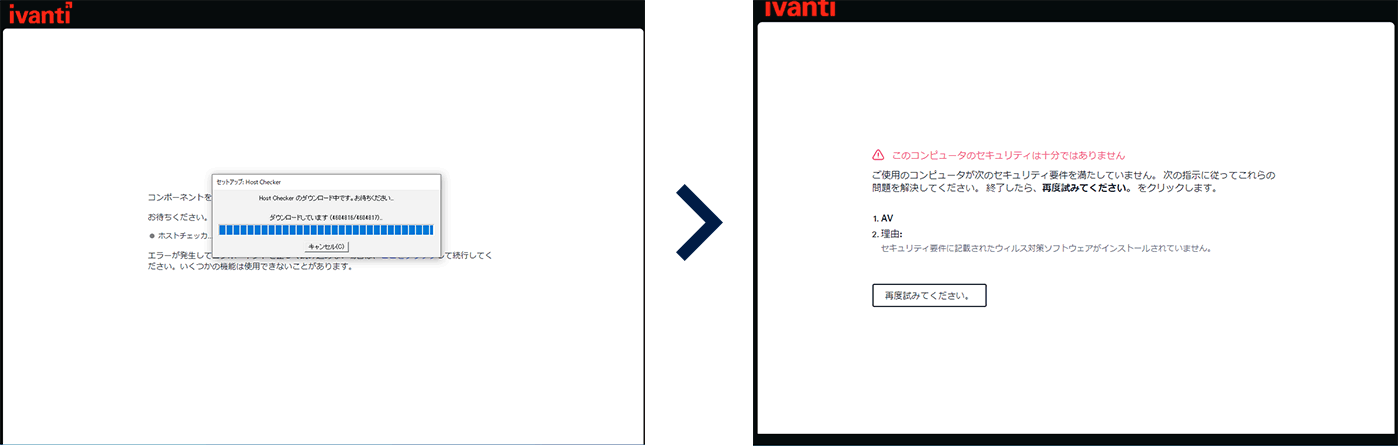
Host Checker (HC)
You can check the status of the client terminal connected to the Connect Secure series and implement simple quarantine. Checks the health of the terminal, such as whether a specific anti-virus software is running or whether the definition file has been updated. You can also prevent connections from unmanaged terminals by starting HDD encryption software and log collection software on client terminals and checking MAC addresses.
In addition, since it is possible to check not only at the time of login but also periodically after login, it is possible to detect rule violations after connection.
The main items that the host checker can check are: (Example on Windows terminal)
- Antivirus software, firewall, etc.
- OS and Service Pack (SP)
- port
- process
- File
- registry key
- NetBIOS name
- MAC address
Other useful functions
Disaster/pandemic countermeasures (ICE license option)
In the event of an emergency, such as a pandemic (a worldwide epidemic of an infectious or contagious disease such as influenza) or a disaster, in which an organization's operations may be stopped, an ICE (In Case of Emergency) license can be activated to temporarily You can scale the number of concurrent users to the maximum supported by the equipment.
The license is automatically enabled/disabled, so it can be automatically turned on in an emergency.
*Valid for 8 weeks with cumulative use, can be turned ON/OFF at will
Customize multiple URLs and authentication screens
Multiple URLs can be set for one Connect Secure series. Also, different authentication screens can be displayed for each URL. In addition, since the authentication screen and the screen after signing out can be freely customized, it is effective when separating the authentication screen for employees and for group companies, or when using it as an extranet.
【Change before】 |
[After change]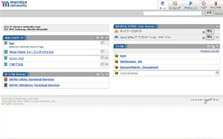 |
LDAP server password management
If the user authentication of Connect Secure series is performed on the LDAP server, passwords can be managed using the policy defined on the LDAP server side. For example, if a user tries to sign in to Connect Secure Series with an LDAP password that is about to expire, the user can be notified through the Connect Secure Series authentication screen and prompted to change it. We have a proven track record with Microsoft's Active Directory and Sun Microsystems' LDAP.
Customizing User Portal Pages
You can freely customize the user's portal page after signing in. As a result, it is possible to change the arrangement to be easy to use for each user.
system dashboard
You can check the status of the Connect Secure series (number of concurrent users, percentage of applications used, CPU/memory usage, throughput, etc.) on the management screen.
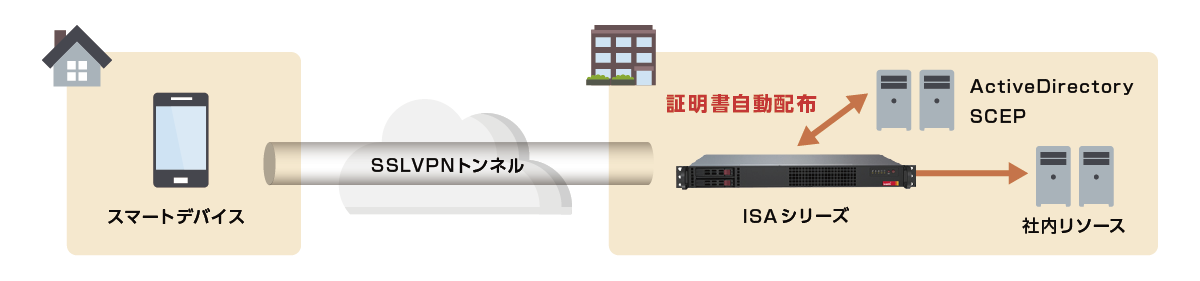
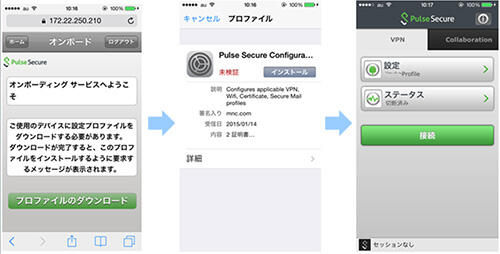
Onboarding features
With the recent spread of smart devices such as iPhone and Android, there is an increasing need for business terminals to use them.
A dedicated application is used when accessing a general SSL-VPN using a smart device.
However, until now, complicated operations such as entering a login URL after installing an application, installing a client certificate to improve security, and setting other detailed parameters were required.
The newly released ISA "onboarding function" solves this problem, and by distributing configuration profiles to smart devices, it is now possible for users to collectively configure settings that they had to manually configure. have become.
In addition, for distribution of client certificates, it is possible to automatically distribute client certificates for each user by cooperating with MSCEP servers represented by ActiveDirectory.
This will further strengthen the linkage between ISA and smart devices, making it possible to use it more smoothly.
Inquiry/Document request
In charge of Macnica Ivanti (Pulse Secure)
- TEL:045-476-2010
- E-mail:pulsesecure-sales@macnica.co.jp
Weekdays: 9:00-17:00