
Okta
オクタ
はじめに
Auth0導入後も既存の外部IdPを引き続き利用したいなどの理由で、アプリケーション認証で複数のIdPを連携させるケースがあります。Auth0のデフォルト設定では、ログイン画面でユーザが認証先を選択する必要があります。
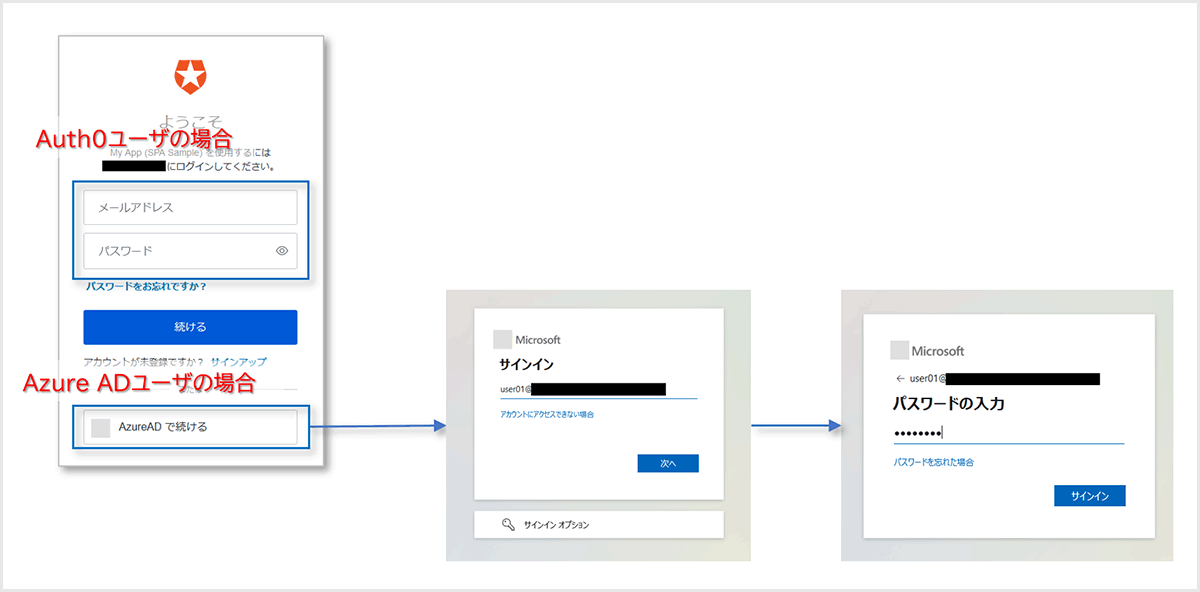
Auth0のAuthentication Profile機能を利用すれば、ユーザ(メールアドレスのドメイン)に応じて自動的に認証先IdPを振り分けることができます。
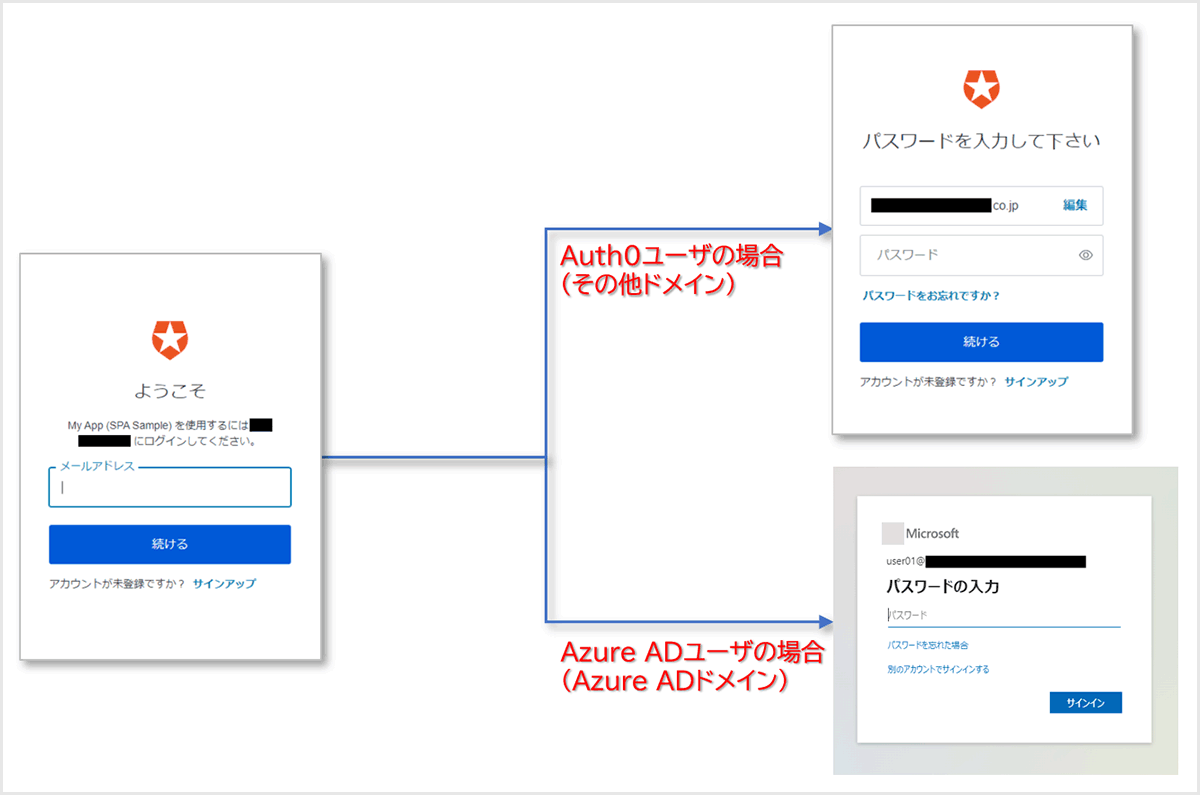
本ページでは、Authentication Profile機能を利用した認証先IdPルーティングの実現について、設定とログイン時の動作例をご紹介します。
前提
本ページ内の設定及びログイン動作例は、以下が準備済の状態を前提とします。
- Auth0連携済のWebアプリケーション
- 当該Webアプリケーションに対して、複数のConnectionsを有効化(今回はAuth0 Database Connection及びEnterprise Connection(Azure AD)を有効化)
※Enterprise Connection(Azure AD)の設定は、[Auth0 Enterprise Connection機能による外部IdP連携(Azure AD) ]をご確認ください。
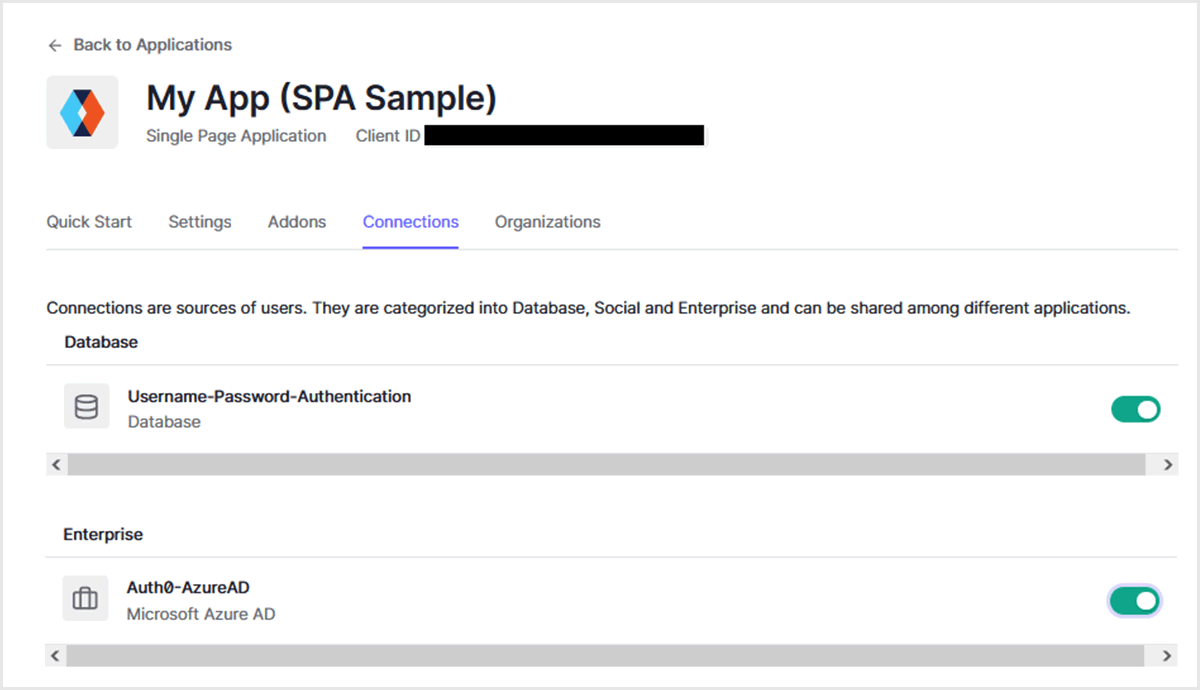
Auth0によるログイン画面機能については、New Universal Loginを利用します。
※Authentication Profile機能はClassic版非対応
また、本ページに記載する機能及び設定に関する内容は、2022年10月現在の情報となります。
設定例
![Auth0管理画面において、[Authentication] > [Authentication Profile]をクリック](/business/security/okta/image/okta_tech_auth0_ap_dr04.png)
[Identifier First]を選択することで、ログイン画面ではメールアドレスの入力のみ要求され、入力されたメールアドレスのドメインに応じて、認証先IdPが提供するパスワード入力画面に遷移します。
![[Identifier First]を選択し、画面右上の[Save]をクリック](/business/security/okta/image/okta_tech_auth0_ap_dr05.png)
ログイン時の動作例
- Auth0連携済のWebアプリケーション画面でログイン操作を行い、Auth0が提供するログイン画面に遷移
- メールアドレスの入力だけが求められることを確認
(Auth0ユーザデータベースに登録済のユーザでログインする場合)
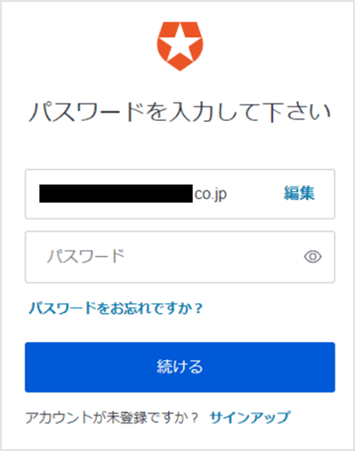
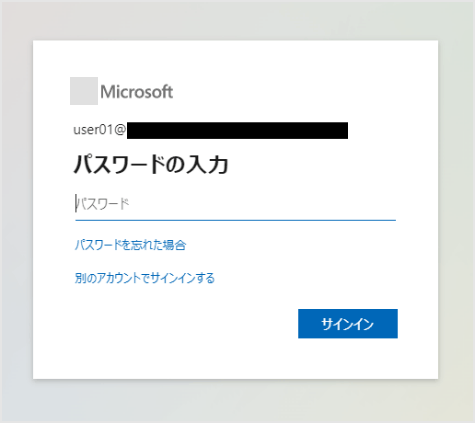
(補足)ドメイン判別設定
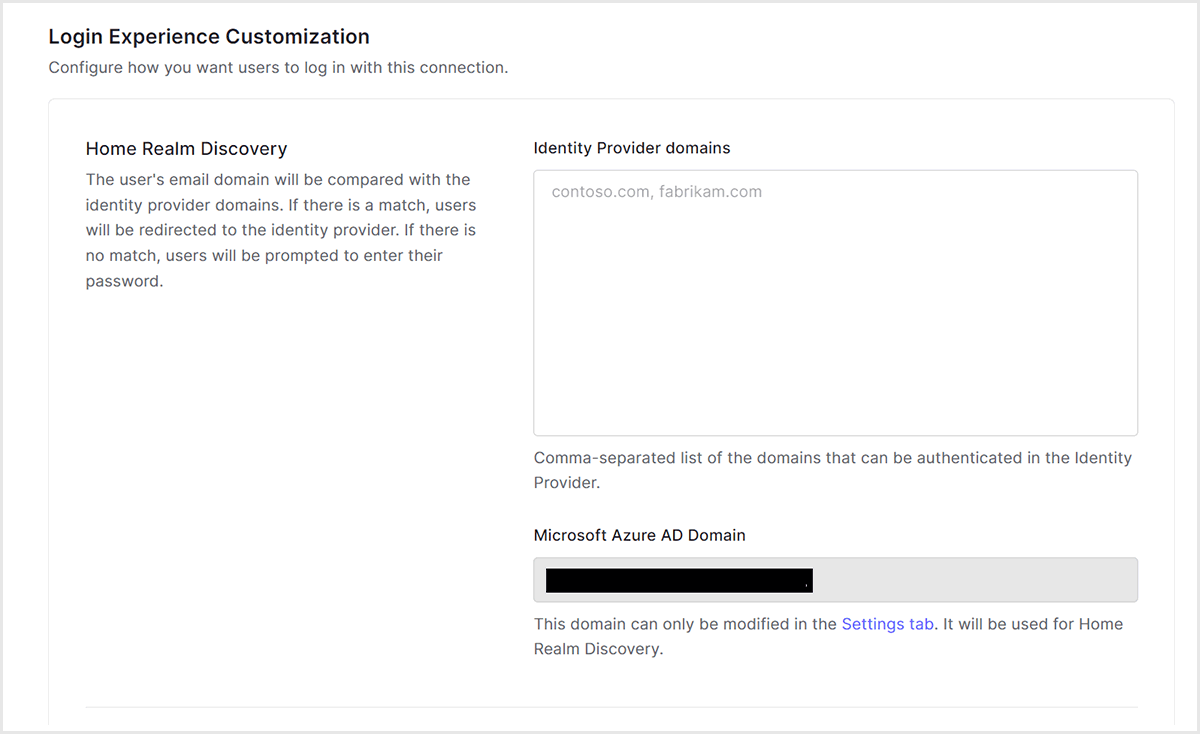
ドメインによる認証先IdPの振り分けは、Enterprise ConnectionにおけるHome Realm Discovery設定に基づきます。本設定に登録されたドメインに合致した場合に、対象IdPへの認証振り分けが行われます。
まとめ
Auth0ではAuthentication Profile機能を利用することで、認証先IdPの振り分けを実現できます。本機能は、無償のAuth0トライアル環境においても利用できますので、是非お試しください。
参考
お問い合わせ・資料請求
株式会社マクニカ Okta 担当
- TEL:045-476-2010
- E-mail:okta@macnica.co.jp
平日 9:00~17:00