
Okta
オクタ
はじめに
Auth0では、Auth0自体のユーザデータベースだけではなく、外部のIdPで管理されているユーザアカウントを利用して、Auth0連携アプリケーションへログインできます。既存のIdPに登録済のユーザアカウント情報を継続して利用でき、最小限の対応作業でAuth0への認証統合を実現できます。
Auth0における外部IdP連携では、Enterprise Connection機能を利用します。本ページでは、外部IdPとしてAzure Active Directory(以下、Azure AD)を対象とし、必要となる設定と実際のログイン動作をご紹介します。
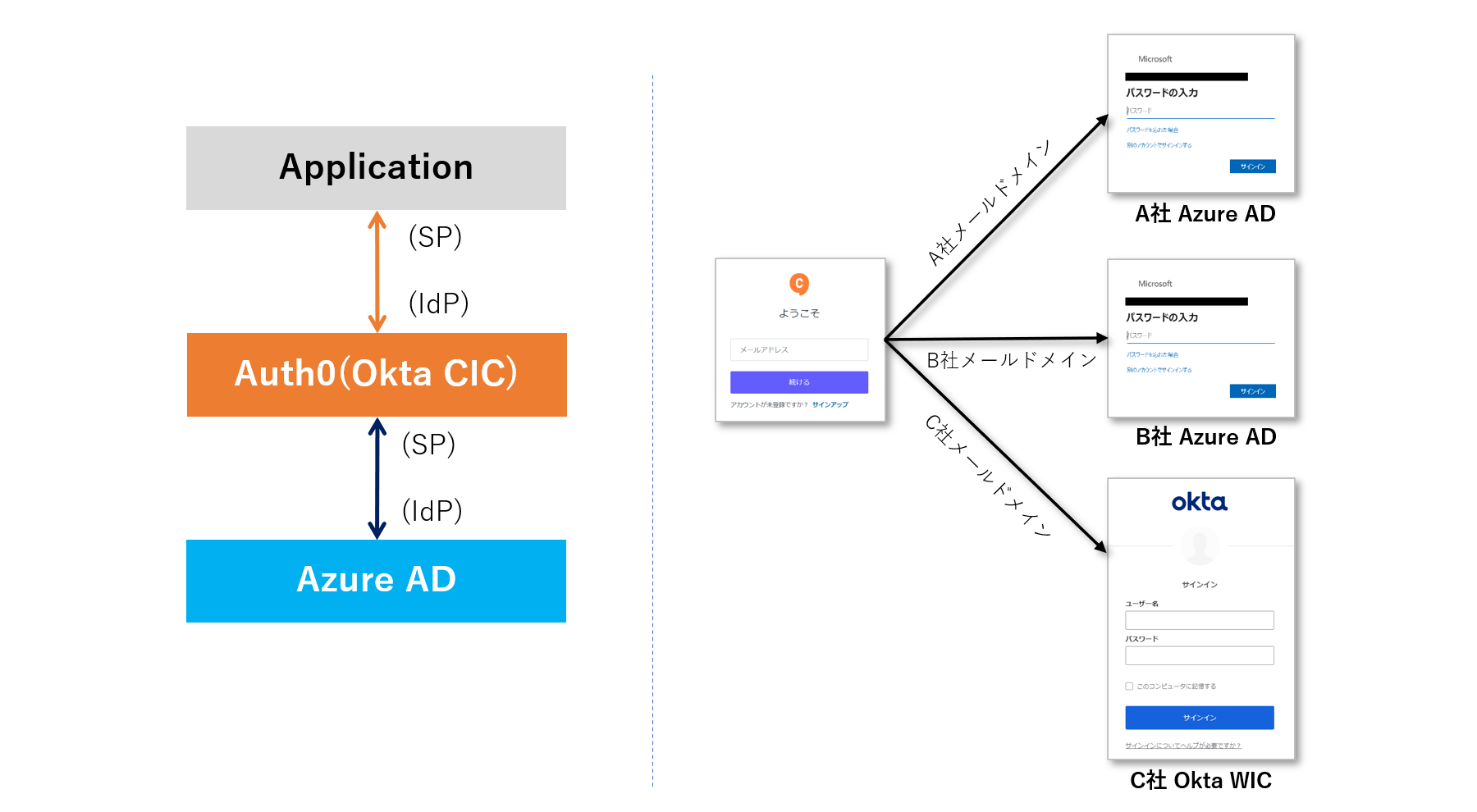
Auth0がサポート対応する外部IdP
Auth0がサポート対応している外部IdPは、以下より確認できます。Okta Workforce Identity、Azure AD等、主要なIdPに対応しています。
https://auth0.com/docs/authenticate/identity-providers/enterprise-identity-providers
前提
本ページ内の設定及び動作例では、以下が準備済の状態を前提とします。
- Auth0連携済のWebアプリケーション
- Azure ADテナント作成
Auth0によるログイン画面機能については、New Universal Loginを利用します。
※後述のConnection Button設定はClassic版非対応
また、本ページに記載する機能及び設定に関する内容は、2022年11月現在の情報となります。
設定概要
Auth0連携済のWebアプリケーションにおいて、Azure ADを外部IdPとする認証統合を実現するにあたり、Auth0・Azure ADそれぞれで必要となる設定は、以下の通りです。
- アプリケーション登録
- クライアントシークレット作成
- Azure AD向けEnterprise Connection設定
- ApplicationにおけるEnterprise Connectionの有効化
ここから、具体的な設定方法とログイン時の動作例をご紹介します。
設定例
- Azure AD設定に必要となるAuth0側情報の整理
Azure AD側の設定にあたり必要となる以下の情報を確認
- Auth0テナントドメイン名:xxxxxx.xx.auth0.com
※Azure AD側の設定の詳細については、Microsoft社の下記ページをご確認ください。
https://learn.microsoft.com/en-us/azure/active-directory/develop/quickstart-register-app
- Azureポータル画面において、[追加] > [アプリの登録]をクリック
![Azureポータル画面において、[追加] > [アプリの登録]をクリック](/business/security/okta/image/okta_tech_auth0_azure_ad_dr01.png)
- アプリケーションの登録において各項目を設定後、[登録]をクリック
- 名前:任意の設定名
- サポートされているアカウントの種類:アクセス範囲の指定
- リダイレクトURL:https://(Auth0テナントドメイン名)/login/callback
![アプリケーションの登録において各項目を設定後、[登録]をクリック](/business/security/okta/image/okta_tech_auth0_azure_ad_dr02.png)
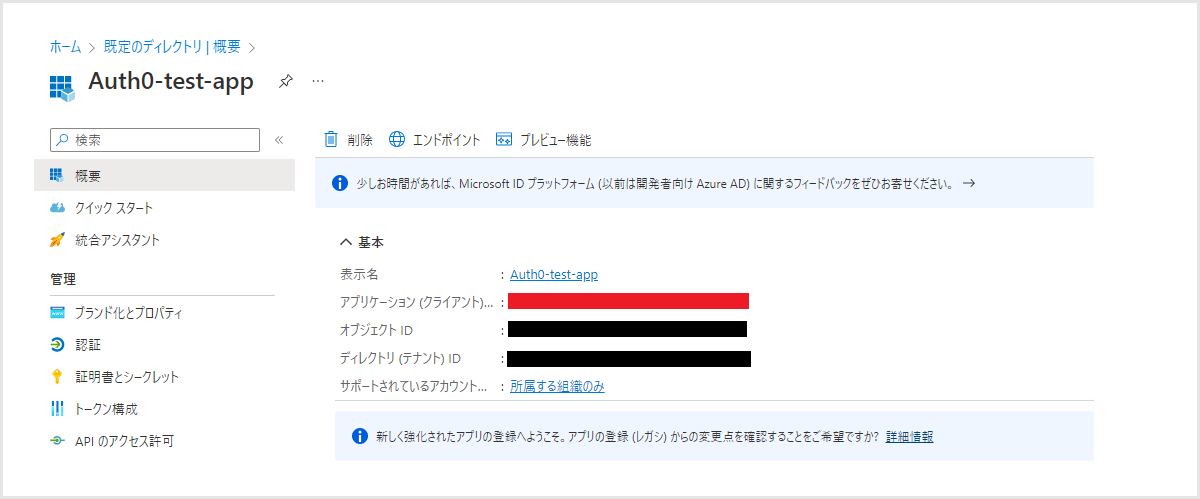
- 登録されたアプリケーションのアプリケーション(クライアント)IDをコピー(3.Auth0設定で利用)
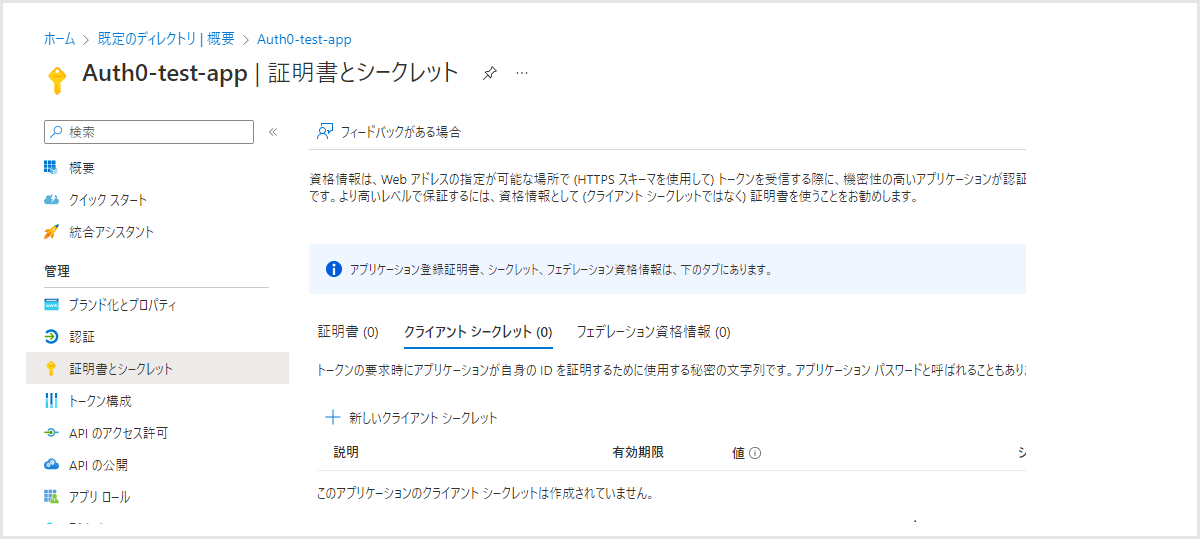
- 左側メニューから[証明書とシークレット]を選択し、[新しいクライアント シークレット]をクリック
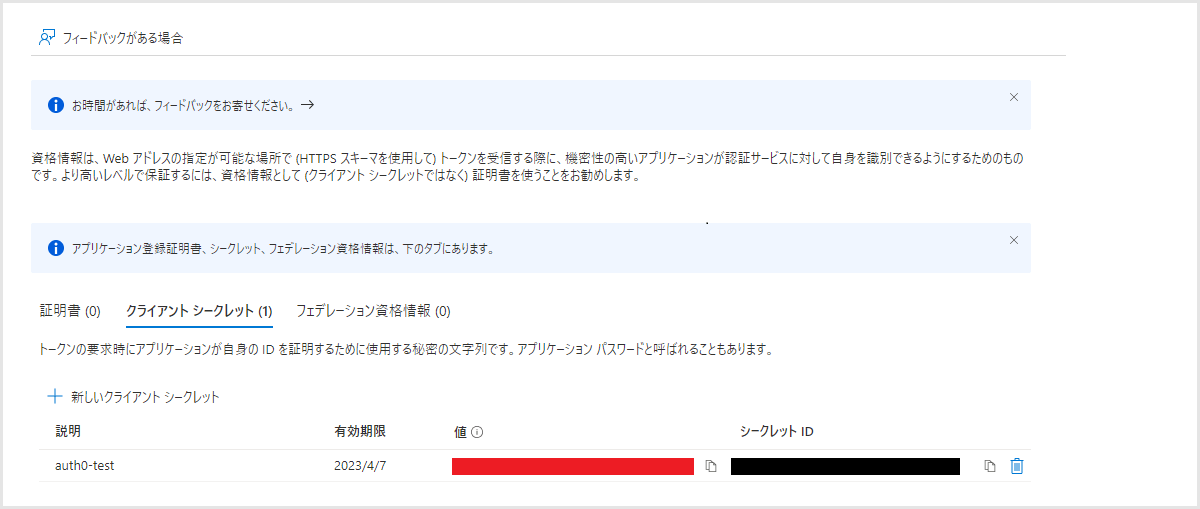
- 任意の説明と有効期限を指定し、[追加]をクリック
![任意の説明と有効期限を指定し、[追加]をクリック](/business/security/okta/image/okta_tech_auth0_azure_ad_dr05.png)
- 発行されたクライアントシークレットの値をコピー(3.Auth0設定にて利用)
- Auth0管理画面で、[Authentication] > [Enterprise]をクリック
![Auth0管理画面で、[Authentication] > [Enterprise]をクリック](/business/security/okta/image/okta_tech_auth0_azure_ad_dr07.png)
- [Microsoft Azure AD]をクリック
![[Microsoft Azure AD]をクリック](/business/security/okta/image/okta_tech_auth0_azure_ad_dr08.png)
- [Create Connection]をクリック
![[Create Connection]をクリック](/business/security/okta/image/okta_tech_auth0_azure_ad_dr09.png)
- 各項目を設定後、ページ末尾の[Create]をクリック
- Connection name:任意の設定名
- Microsoft Azure AD Domain:連携対象とするAzure ADのドメイン(ホーム > Azure Active Directoryより確認可能)
- Client ID:Azure ADアプリケーションのアプリケーション(クライアント)ID
- Client Secret:Azure ADアプリケーションのクライアントシークレット値
- Use common endpoint:無効
- Identity API:Microsoft Identity Platform (v2)
- Extended Attributes:選択なし
- Auth0 APIs:選択なし
- Sync user profile attributes at each login:有効
- Email Verification:Always set email_verified to 'false'
![各項目を設定後、ページ末尾の[Create]をクリック](/business/security/okta/image/okta_tech_auth0_azure_ad_dr10.png)
- Login ExperienceタブにてConnection Button設定を実施し、ページ末尾の[Save]をクリック
- Display connection as a button:チェック(ログイン画面上にAzure ADによるログインボタンを表示)
- Button display name:ボタン表示名称を指定
![Login ExperienceタブにてConnection Button設定を実施し、ページ末尾の[Save]をクリック](/business/security/okta/image/okta_tech_auth0_azure_ad_dr11.png)
- 連携するApplication設定にて、作成したEnterprise Connection設定を有効化
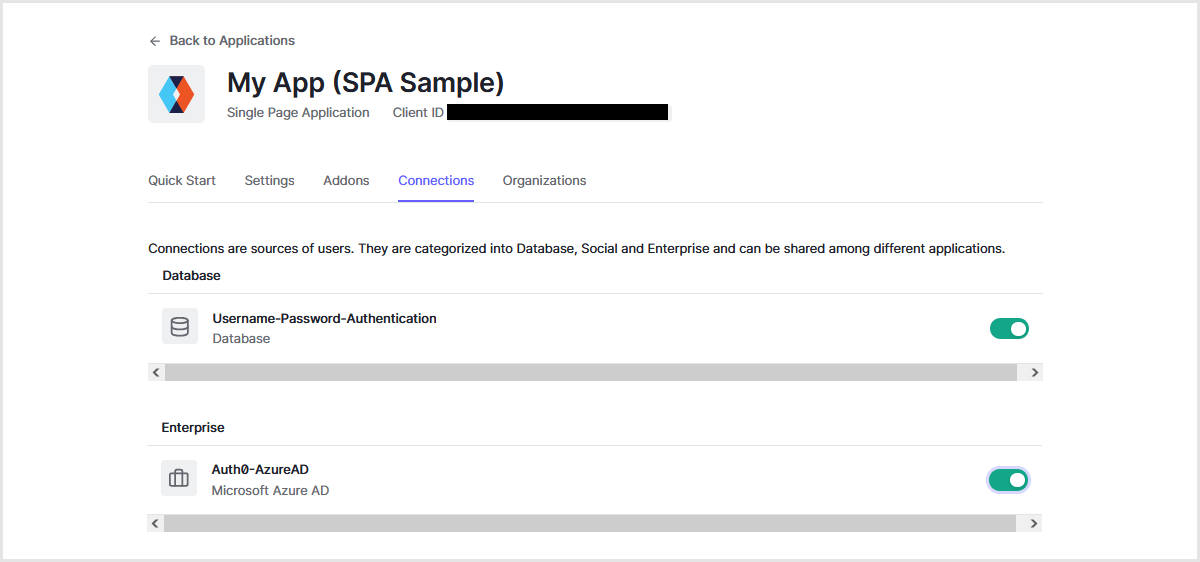
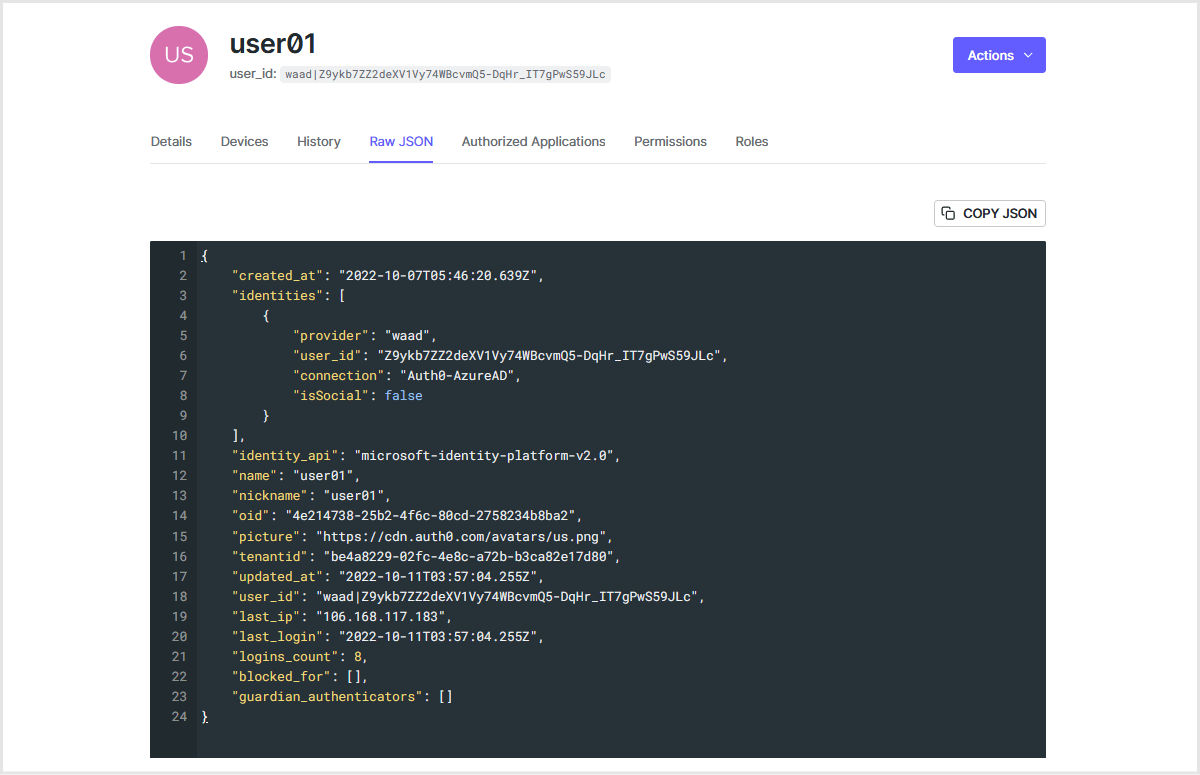
ログイン時の動作例:Azure ADに登録済のユーザによるログイン
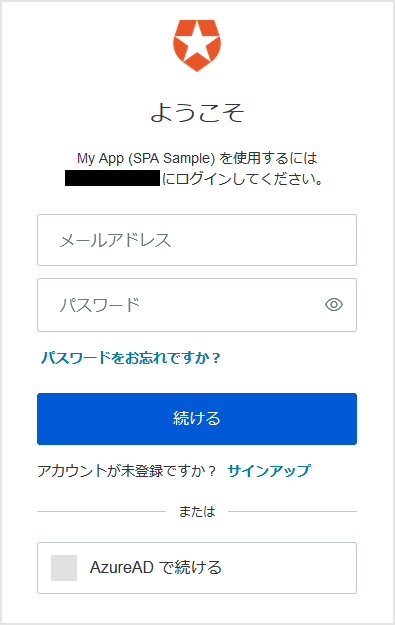
- Auth0連携済のWebアプリケーション画面においてログイン操作を行い、Auth0が提供するログイン画面に遷移
- [Azure ADで続ける]ボタンが表示されていることを確認し、[Azure ADで続ける]ボタンをクリック
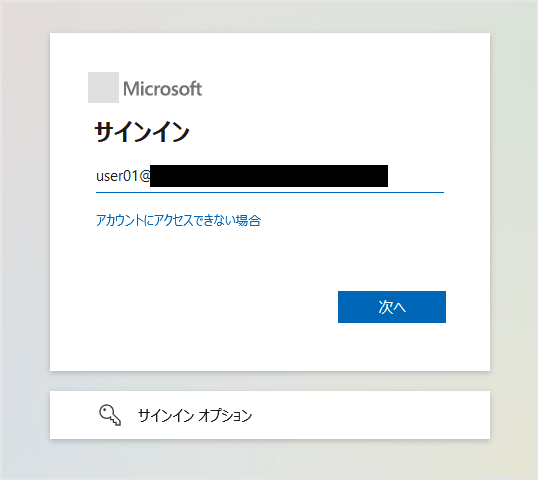
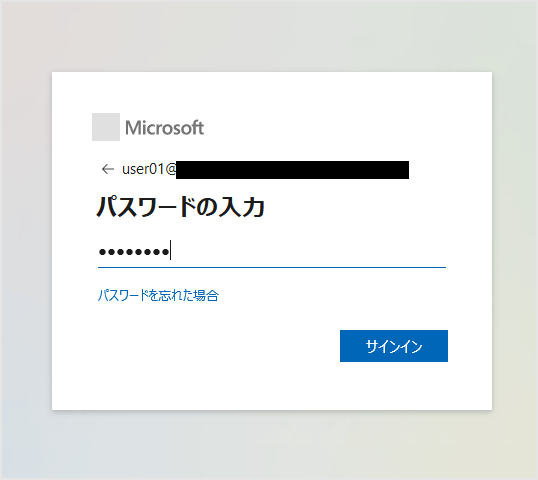
![許可を求めるメッセージ表示において、[承諾]をクリック](/business/security/okta/image/okta_tech_auth0_azure_ad_dr16.png)

まとめ
Auth0では、Enterprise Connection機能を利用することで、外部IdPを用いた認証処理を簡単に実現できます。無償のAuth0トライアル環境においてもEnterprise Connection機能をお試しいただけますので、ぜひ実感してください。
既存のIdPを活用したAuth0への認証統合についてご興味がある方は、是非弊社までお問い合わせください。
参考
お問い合わせ・資料請求
株式会社マクニカ Okta 担当
- TEL:045-476-2010
- E-mail:okta@macnica.co.jp
平日 9:00~17:00