
Okta
Octa
I tried to reproduce SSO using Okta's unique authentication method, SWA.
Introduction
Secure Web Authentication (SWA) is Okta's proprietary authentication method that provides single sign-on (SSO) to external web applications that do not support SAML, WS-Federation, or OIDC. By installing the extension function called Okta Browser Plugin in the browser used by the user, Okta Browser Plugin can perform the substitute input of authentication information at the time of authentication and automatically log in.
*SWA-linked automatic login is not supported for login pages that are protected by a system (such as reCAPTCHA) that controls login by bot operation.
In this article, we will introduce automatic login to two types of applications (MobileIron, Box) using Okta's SWA template.
SWA integration with MobileIron
Okta provides templates for various applications not only for SAML and WS-Federation, but also for SWA linkage. This article introduces the settings and actual login behavior for SWA integration using the MobileIron Cloud template below.
・MobileIron Cloud template
Settings and operation
・Login URL setting screen
For integration with MobileIron Cloud templates, the only information required is the Login URL,
Very easy to set up.
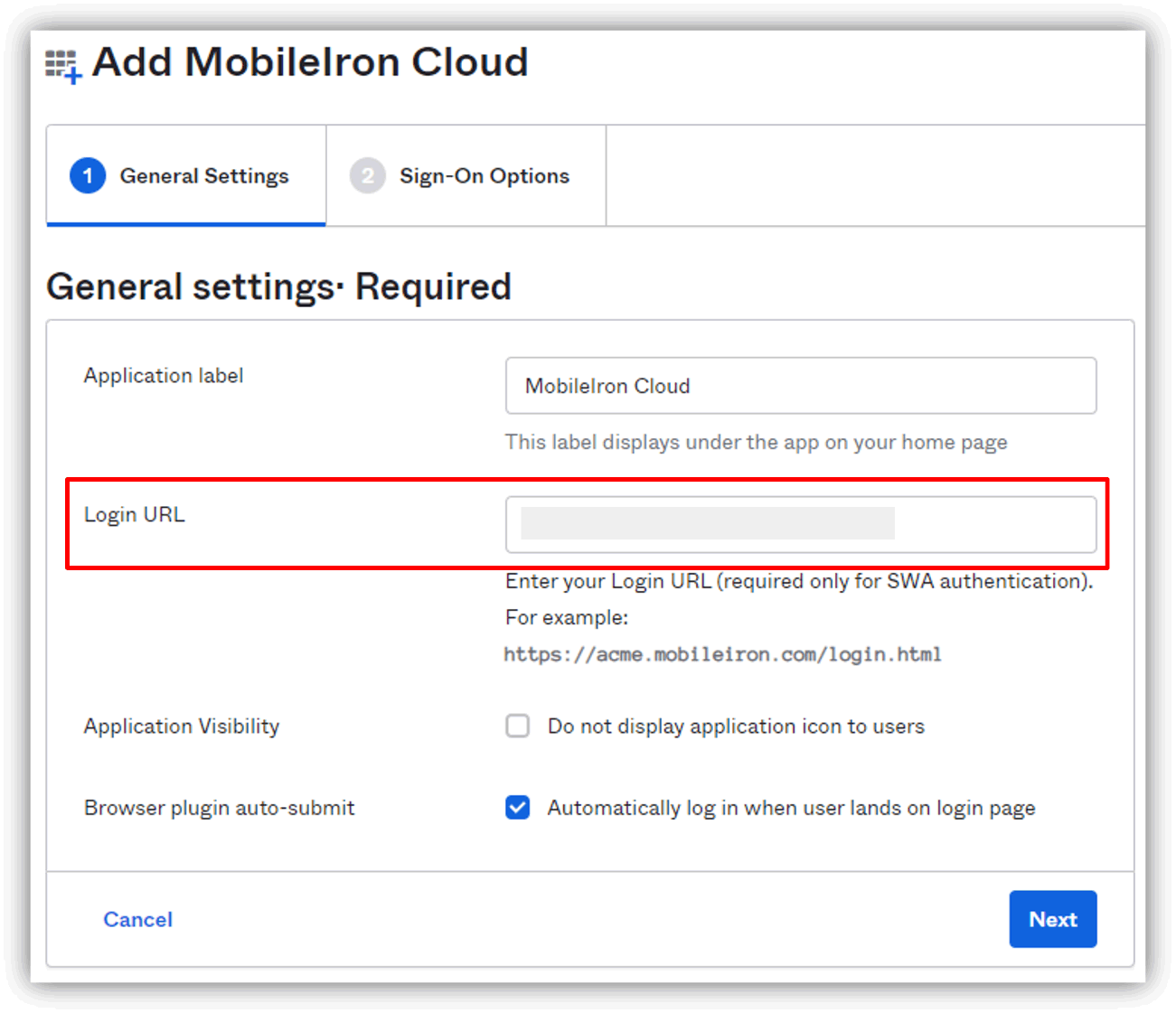
・Setting credentials
With Okta's SWA integration, there are five setting patterns for application credentials (Username, Password), as shown below, which can be set flexibly.
- User sets Username, Password
- Administrator sets Username and Password
- Administrator sets Username, User sets Password
- Administrator sets Username. Password uses the user's Okta password.
- Username and Password set by the administrator are shared by all users
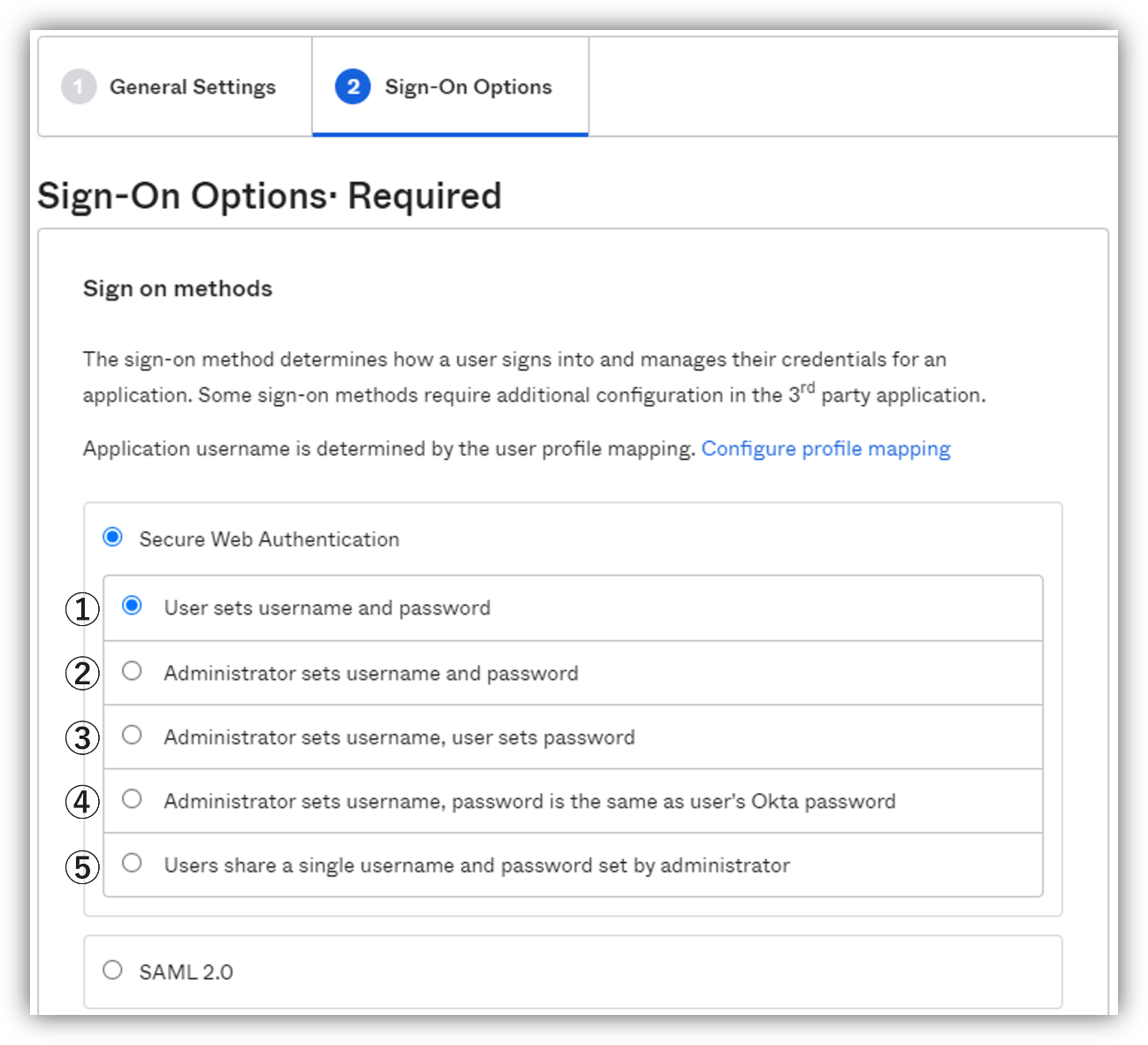
・Credential information setting screen (user side)
In this article, we will introduce the setting pattern of ① above.
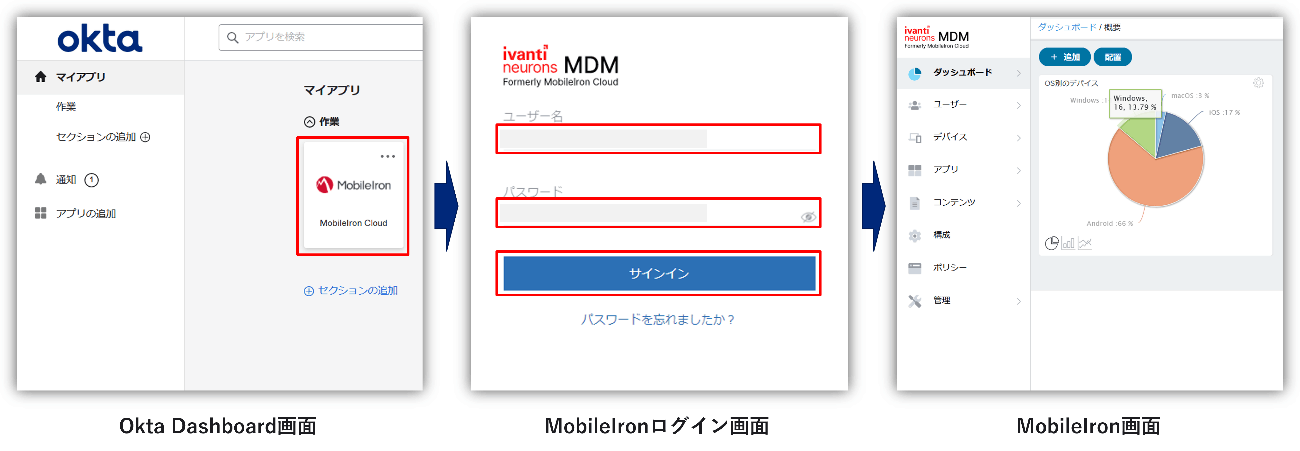
In the user's Okta Dashboard, clicking on the application's icon will
Users can set Username and Password for the application.
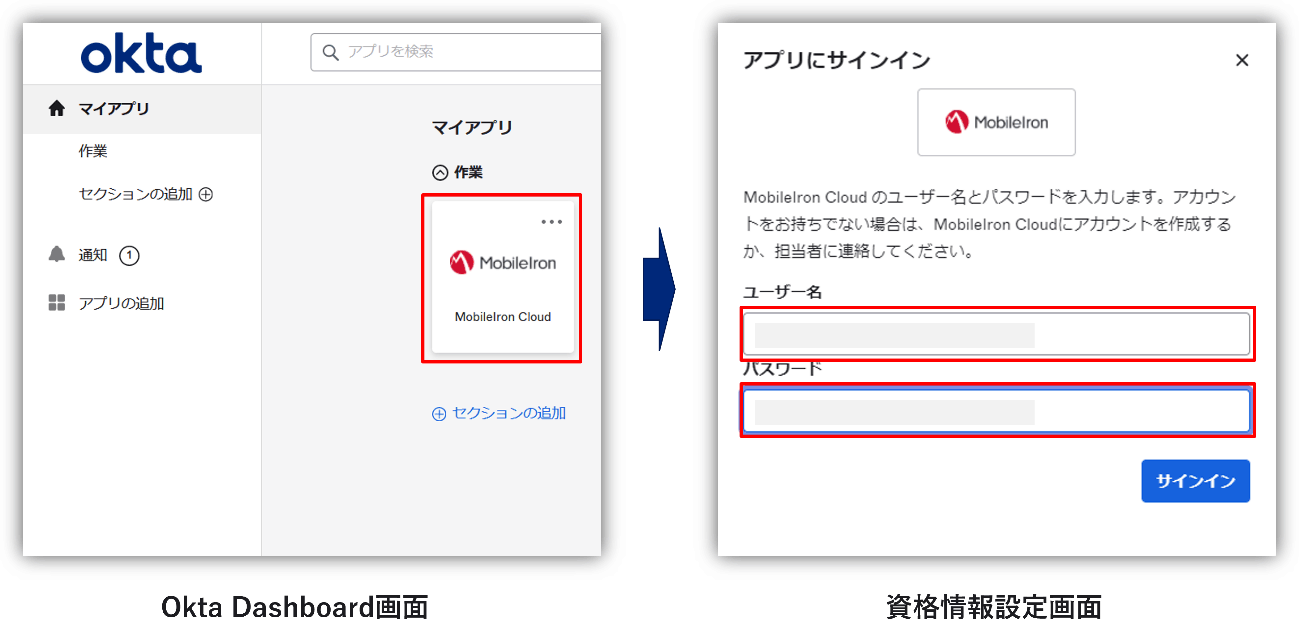
・Actual login operation
When you click the application icon on the Okta Dashboard, you can automatically log in by transitioning to the login screen of the application, automatically entering your Username and Password, and automatically clicking the sign-in button.
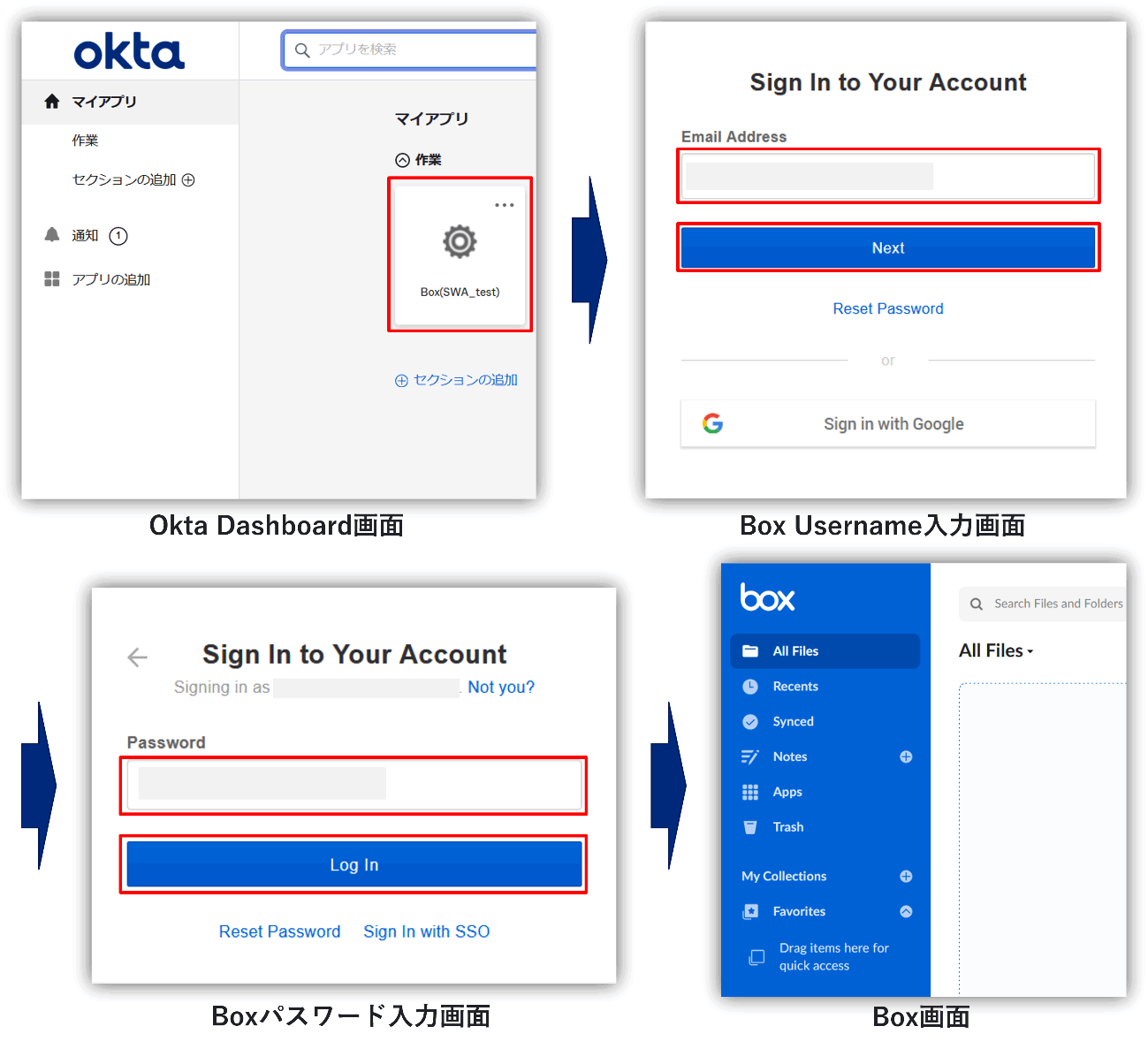
SWA integration with Box
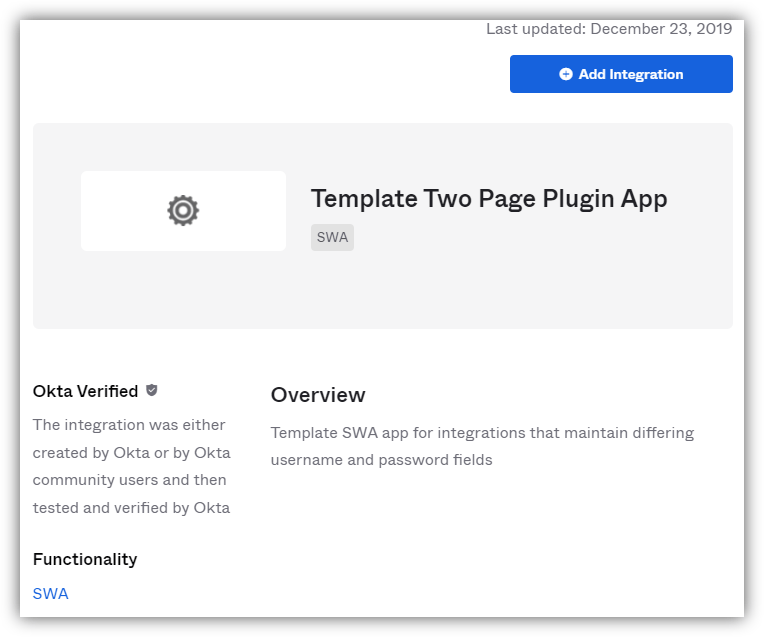
With Okta, even for applications such as Box that have separate Username input screen and Password input screen, you can use the Template Two Page Plugin App below to automatically log in with SWA.
Templates for Box are also available, but in this article, we will introduce SWA linkage settings and actual login behavior when no application template is available.
・Template Two Page Plugin App
Settings and operation
・Setting screen (administrator side)
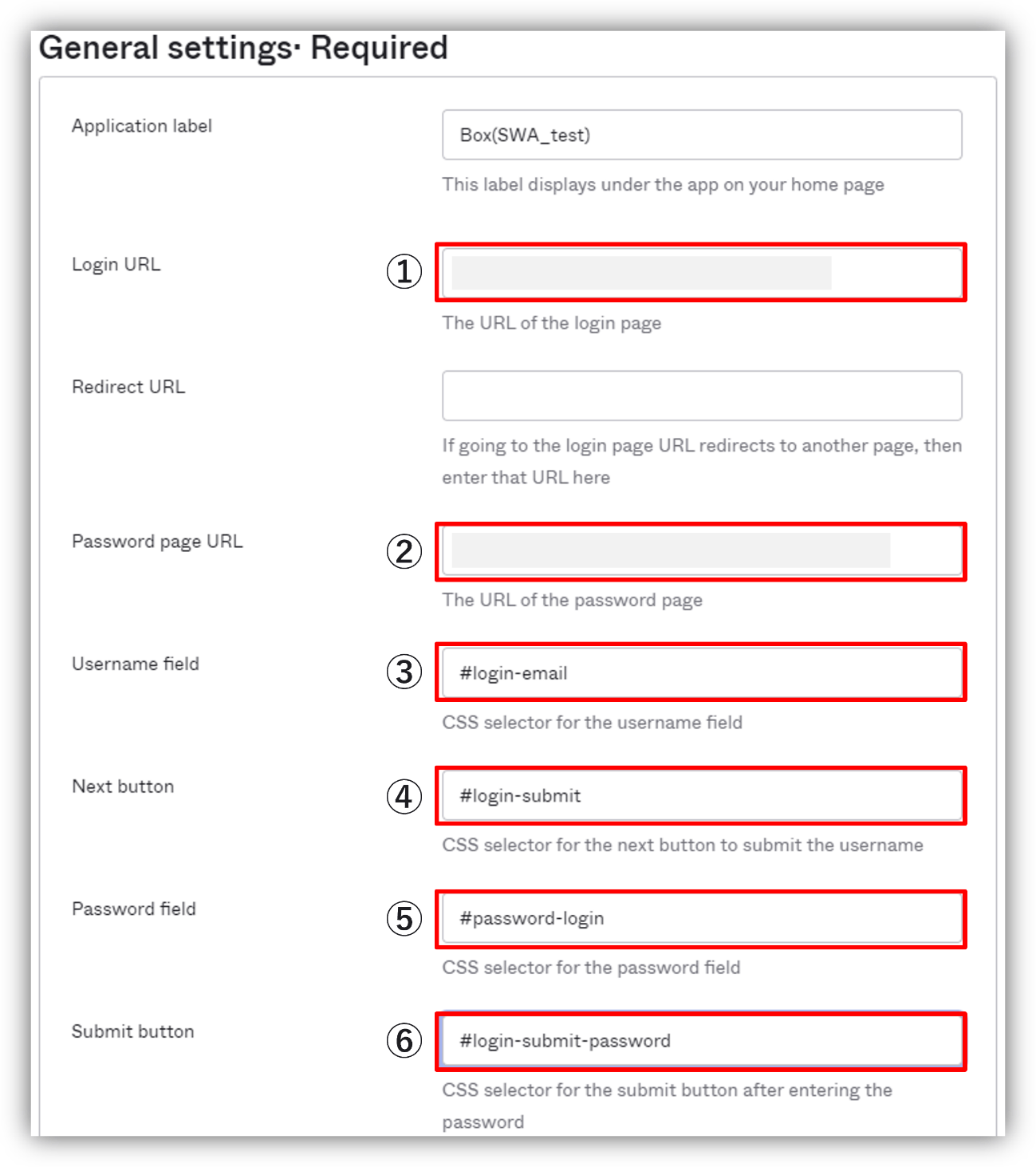
The Template Two Page Plugin App has the following setting items, and you can set items (3) to (6) by copying and pasting CSS selectors for each Field and Button on the login page.
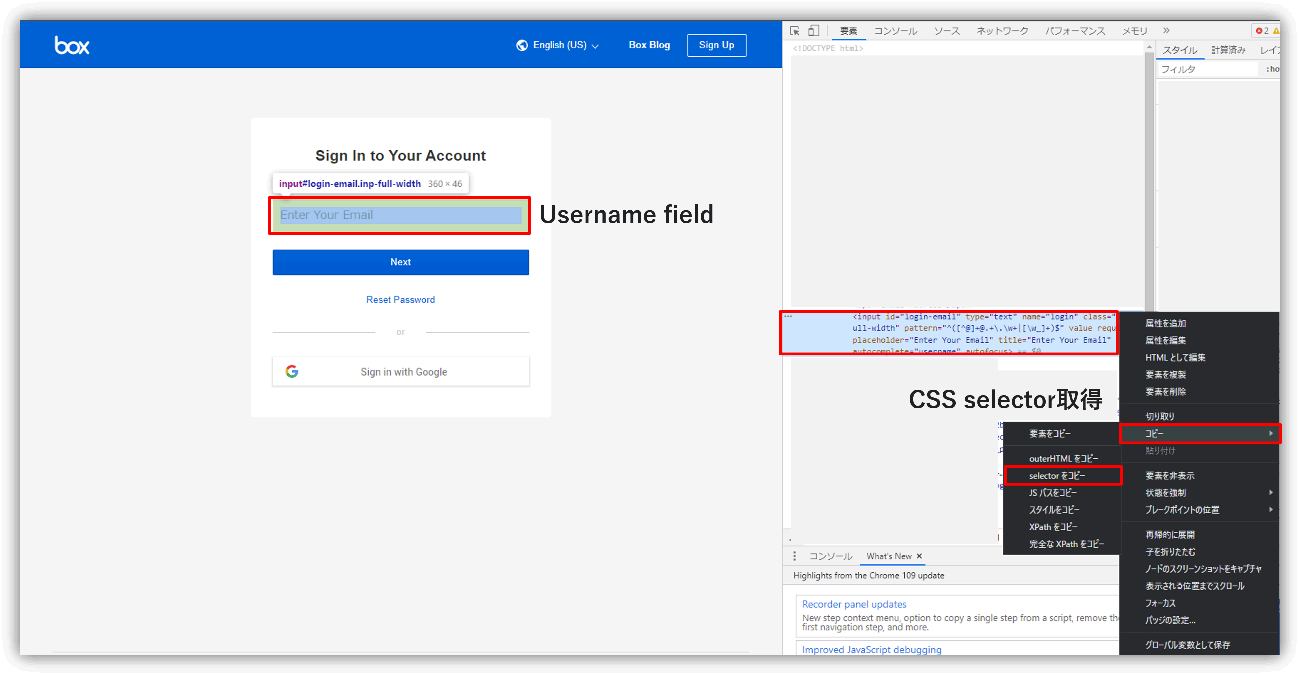
CSS selectors can be obtained using your browser's development tools.
- Login URL
- Password page URL
- Username field
- Next button
- Password field
- Submit button
・CSS selector acquisition screen
・Actual login operation
When logging in, not only can you automatically enter your Username and Password as shown below, but you can also automatically click the Next button, so you can automatically transition from the Username input screen to the Password input screen.
Summary
I hope you have understood the SWA integration in Okta.
With Okta, as mentioned above, applications with irregular login pages, such as those with two separate login pages, can be automatically logged in through SWA linkage.
If you want to perform SSO for applications that do not support SAML, WS-Federation, or OIDC, or if you have any other inquiries about Okta, please contact us.
Inquiry/Document request
In charge of Macnica Okta Co., Ltd.
- TEL:045-476-2010
- E-mail:okta@macnica.co.jp
Weekdays: 9:00-17:00

