
Okta
Octa
new function! What is an Access Request in Okta Identity Governance? Actual usage image commentary!
Introduction
This time, we will explain Access Request, one of the new functions added to Okta, "Okta Identity Governance (hereafter OIG)", along with the actual usage image.
I hope this article conveys Okta's flexibility beyond authentication.
What is OIG
OIG is a feature of IGA (Identity Governance and Administration) that is separate from IAM that Okta has covered so far.
IGA emphasizes who has what level of authority over which system.
OIG has three major functions.
- Access Request: application/group usage application and approval (approval workflow)
- Access Certification: Application/Group Inventory
- Reporting: Support for user assignment status/inventory results to applications
This time, we will focus on Access Request and explain it.
Okta Access Request
Okta Access Request provides a familiar approval workflow in Japan.
When a user uses a specific app, they apply within Okta and approve it on the approver side. Authorized users can create a SaaS-side account and start using SaaS immediately with the provisioning features included in Okta's Lifecycle Management license.
Actual usage image
◆ Approval flow according to authority
Since each SaaS has various authorities, defining approval flows according to each authority will lead to stronger governance.
Let's look at the usage image, assuming that the user will apply when using the SaaS A/B account.
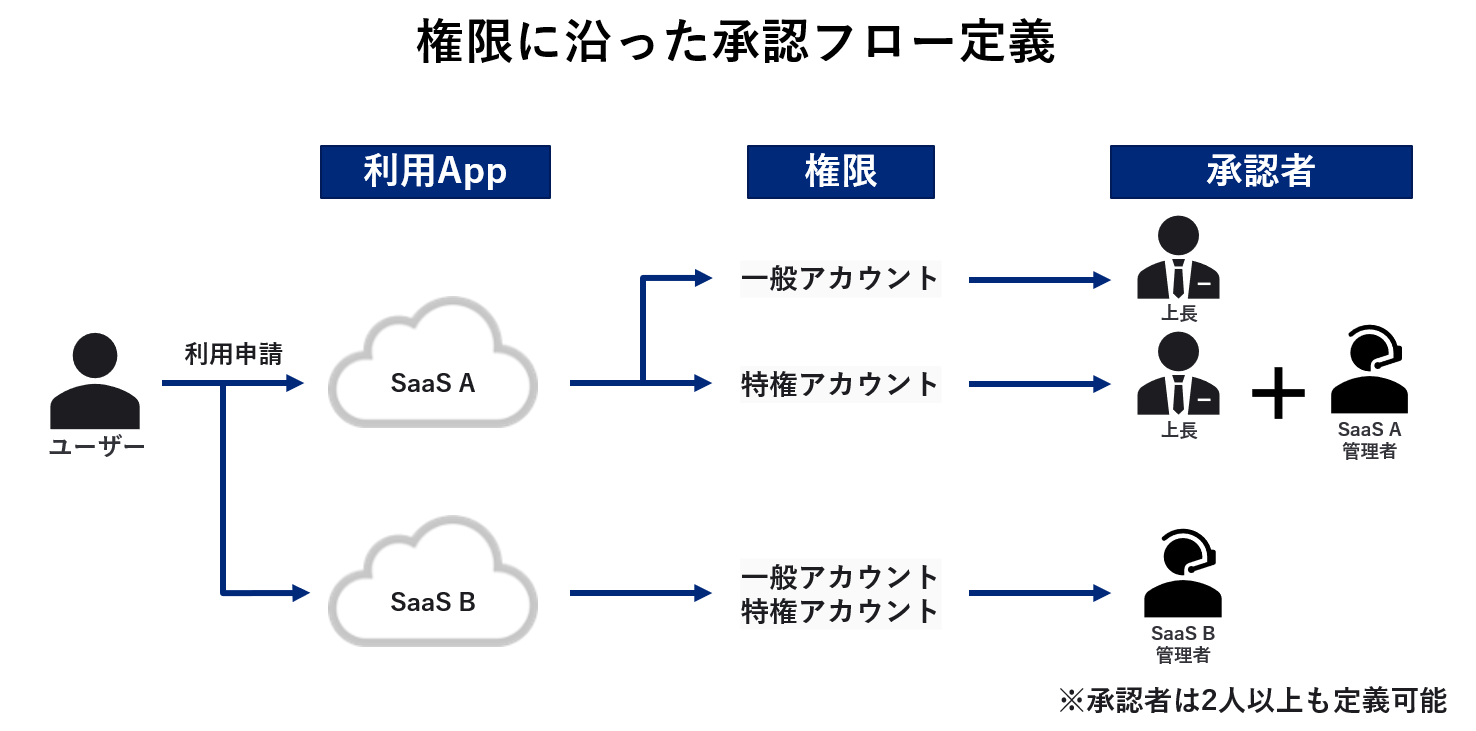
① Application for use of SaaS A
1-1. When applying for a general account
- User applies for SaaS A general account
- Approver: Superior checks validity and approves
- Users can use SaaS A with a general account
1-2. When applying for a privileged account
- User requests SaaS A privileged account
- Approver (1): Superior checks the validity of the application and approves it
- Approver ②: SaaS A administrator checks the application content and approves it (two-stage approval)
- User can use SaaS A with privileged account
(2) When applying for use of SaaS B
2-1. When applying for a general account/privileged account
- User A applies for either a general account or a privileged account
- Approver: SaaS B administrator checks the validity of the application and approves it
- Users can use SaaS B with general/privileged accounts
*The authorization flow for privileged accounts is only available when Okta can grant authorization to SaaS.
◆ Creating a time-limited account
Okta Access Request goes beyond simply paying out accounts.
You can also allow users to determine their own expiration date, and have their privileges automatically removed after expiration.
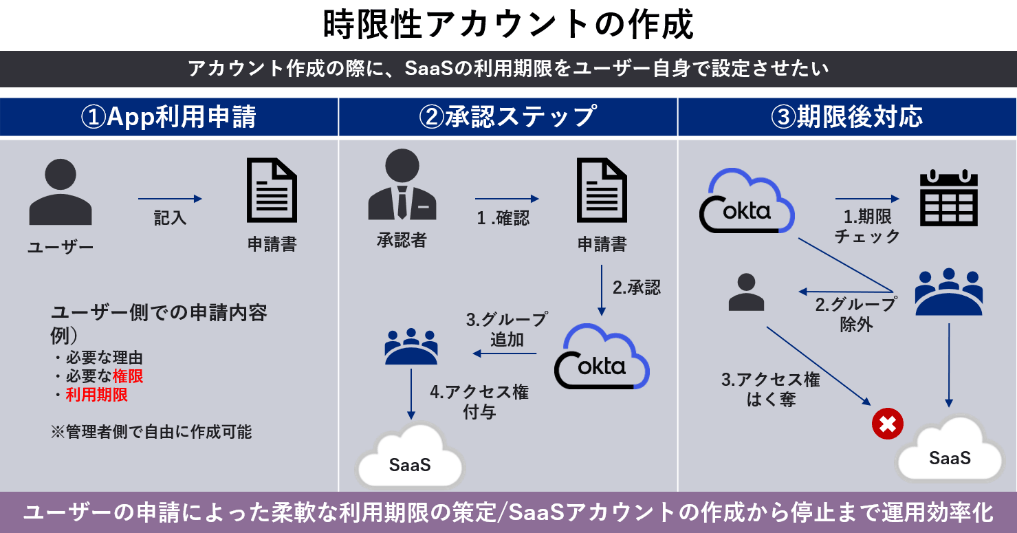
- User requests to use your app
Application details: Reason for use, required authority, expiration date, etc. *Items can be set freely - After confirmation and approval by the approver, the user is added to the application/group on Okta and can be used
- Okta automatically checks deadlines, excludes users from applications/groups, no longer has access
in conclusion
This time, I explained the overview of Okta Access Request.
Next time, I will introduce the procedure for building Access Request, so please look forward to it!
Okta has many features regardless of OIG features, so if you are interested, please contact us.
Inquiry/Document request
In charge of Macnica Okta Co., Ltd.
- TEL:045-476-2010
- E-mail:okta@macnica.co.jp
Weekdays: 9:00-17:00

