
Okta
Octa
I tried managing everything from SSO to authorization with Okta using Okta-AWS integration!
Introduction
According to Okta's annual research report, Businesses at Work 2023, the most popular combination among Okta customers adopting multicloud is Amazon Web Services (AWS) and Google Cloud Platform (GCP). It is mentioned.
Additionally, according to the same report, among the apps used via Okta in 2022, AWS is also the second most used app after Microsoft 365.
Reference source: https://www.okta.com/jp/press-room/press-releases/okta-businesses-at-work2023/
This time, we linked AWS and Okta and verified SSO, ID management, and even AWS account authority management. If you are currently using AWS, we hope that you will find this helpful as a reference when considering implementing IDaaS.
Okta-AWS integration overview
What is AWS IAM Identity Center?
AWS offers a variety of services, but this time we linked AWS IAM Identity Center and Okta.
AWS IAM Identity Center is a service that manages sign-in security for AWS workforce users, allowing you to centrally manage all AWS accounts and applications. (https://aws.amazon.com/jp/iam/identity-center/)
Simply put, it is a service that allows you to manage which resources can be used by which users on AWS.
Therefore, by linking Okta and AWS IAM Identity Center, you can manage access to resources in your AWS account with Okta.
In Okta, when linking provisioning with AWS IAM Identity Center, privileges can be granted/revoked as shown in the diagram below.
*Granting/revoking privileges during provisioning is effective for some SaaS. For other SaaS, if the corresponding API is available, you can use Okta Workflows to manage licenses and permissions in the same way.
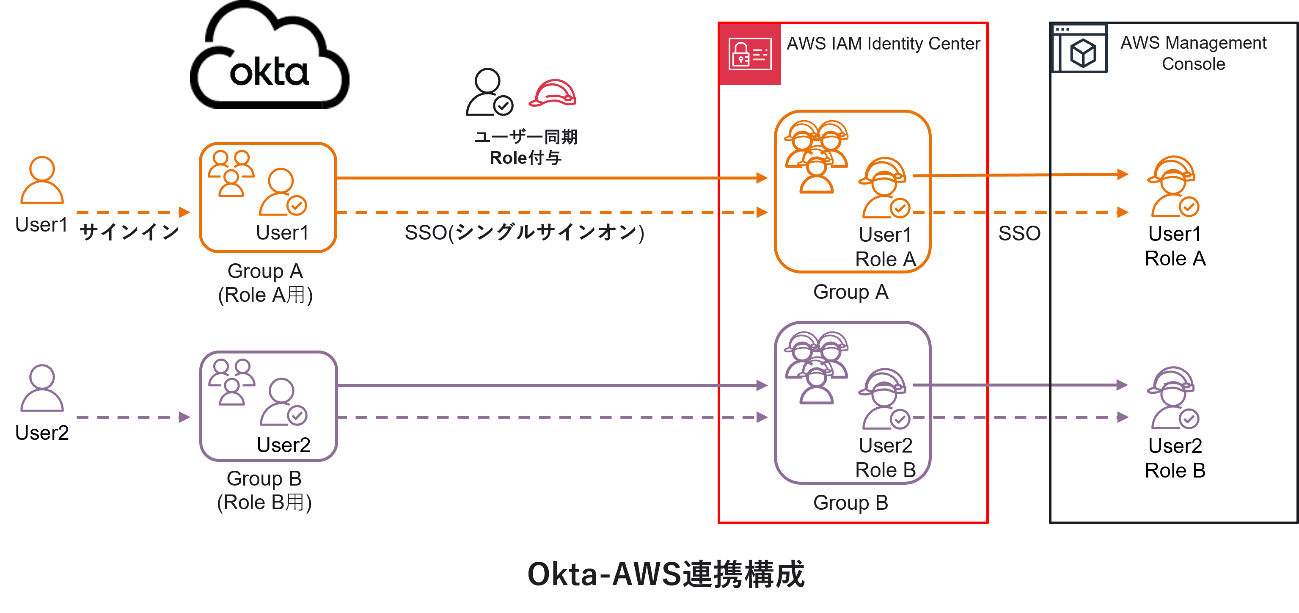
Okta-AWS IAM Identity Center SSO integration
Okta provides a SaaS integration template called OIN, so specify and configure OIN for AWS IAM Identity Center integration.
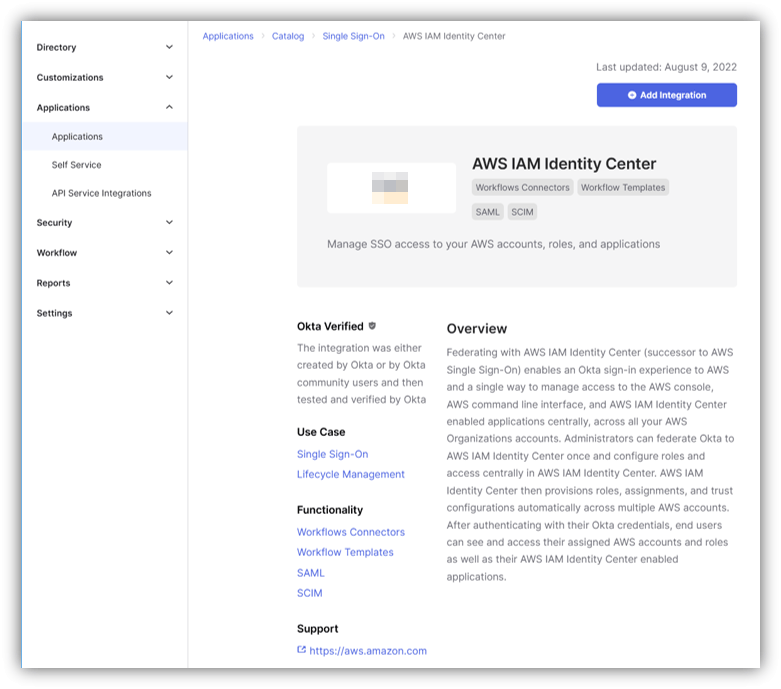
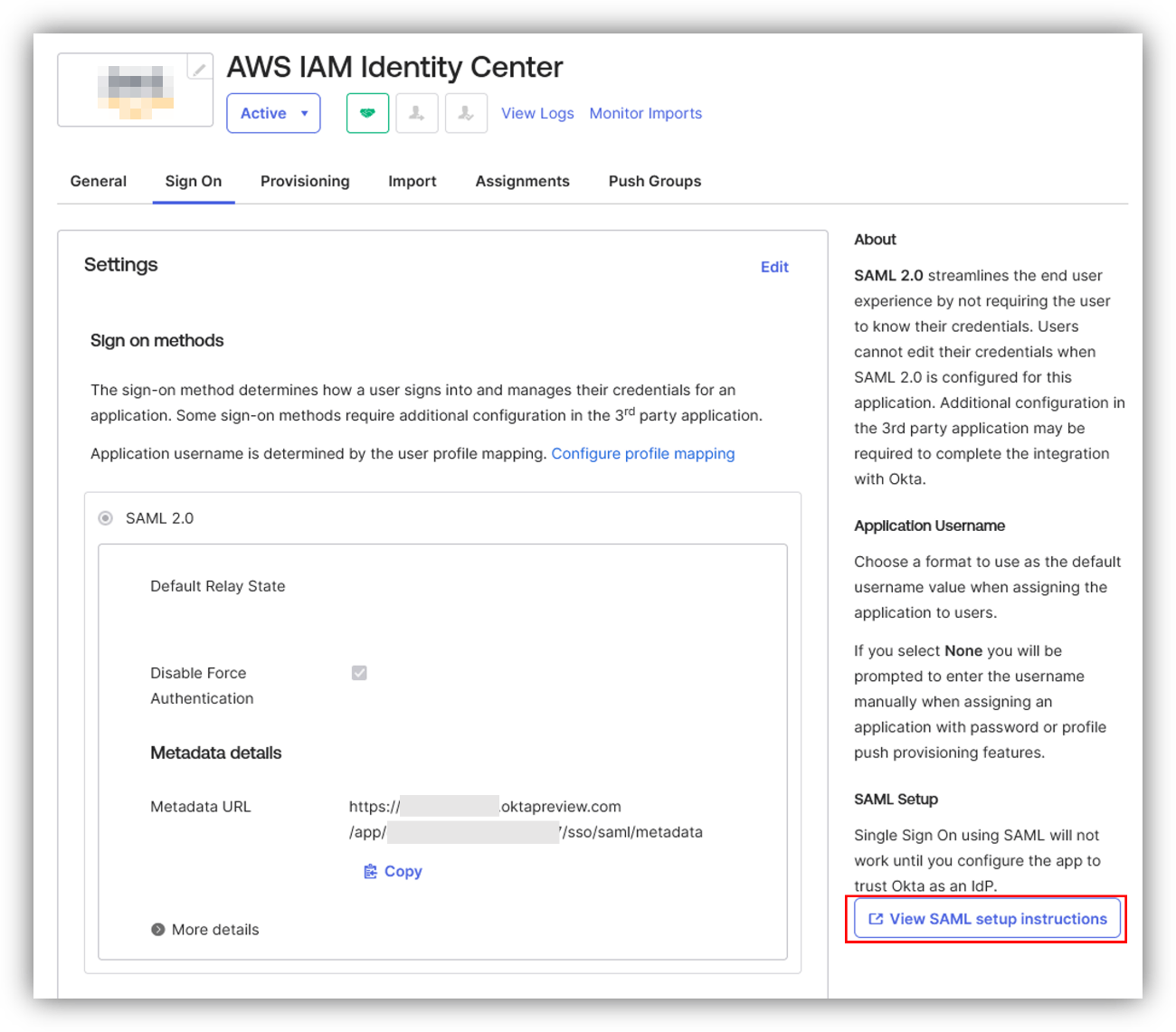
Click View SAML setup instructions in the AWS IAM Identity Center app created on Okta and proceed with the settings according to the instructions.
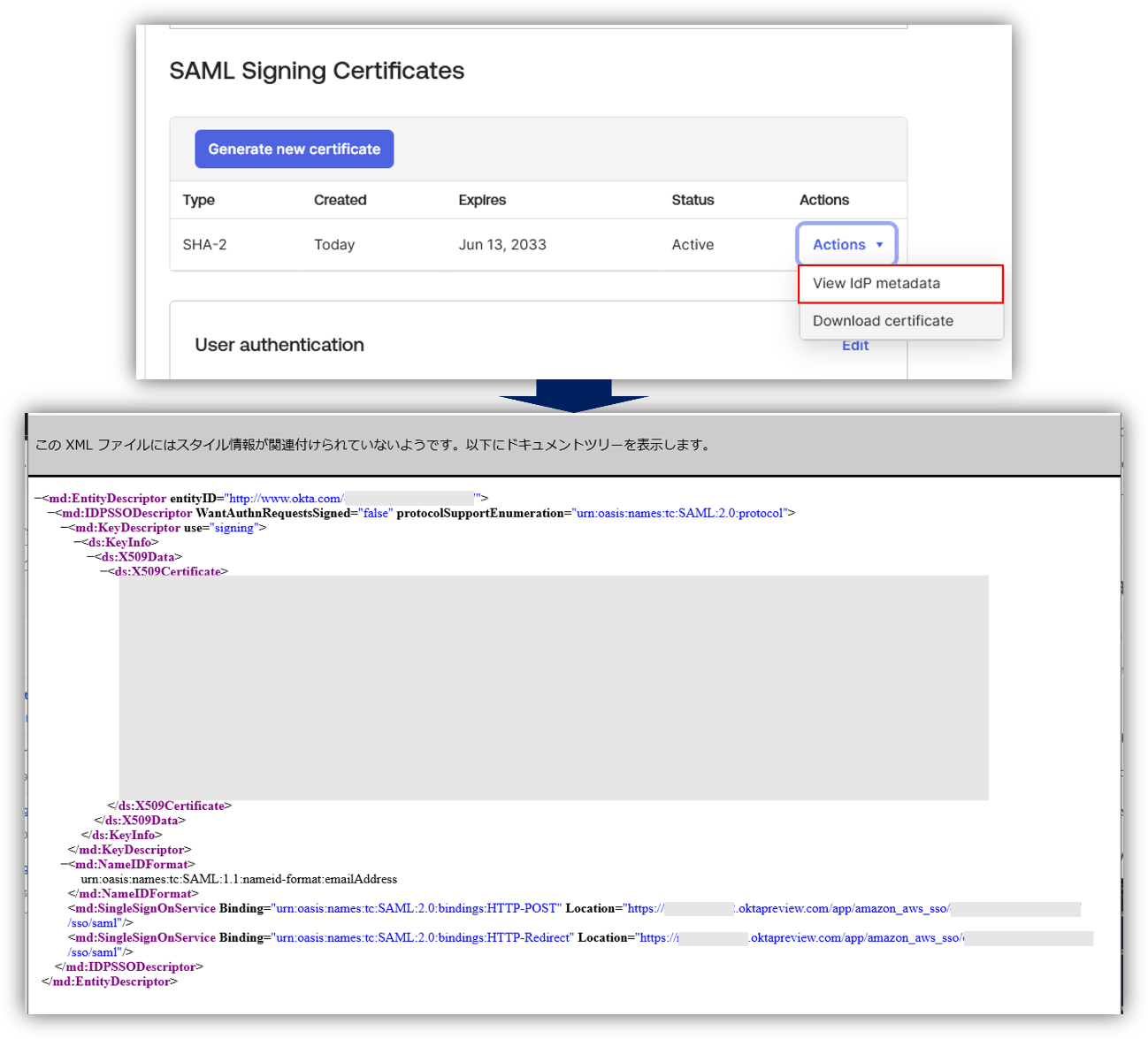
- AWS IAM Identity Center Settings > Identity Source tab, click "Change Identity Source"
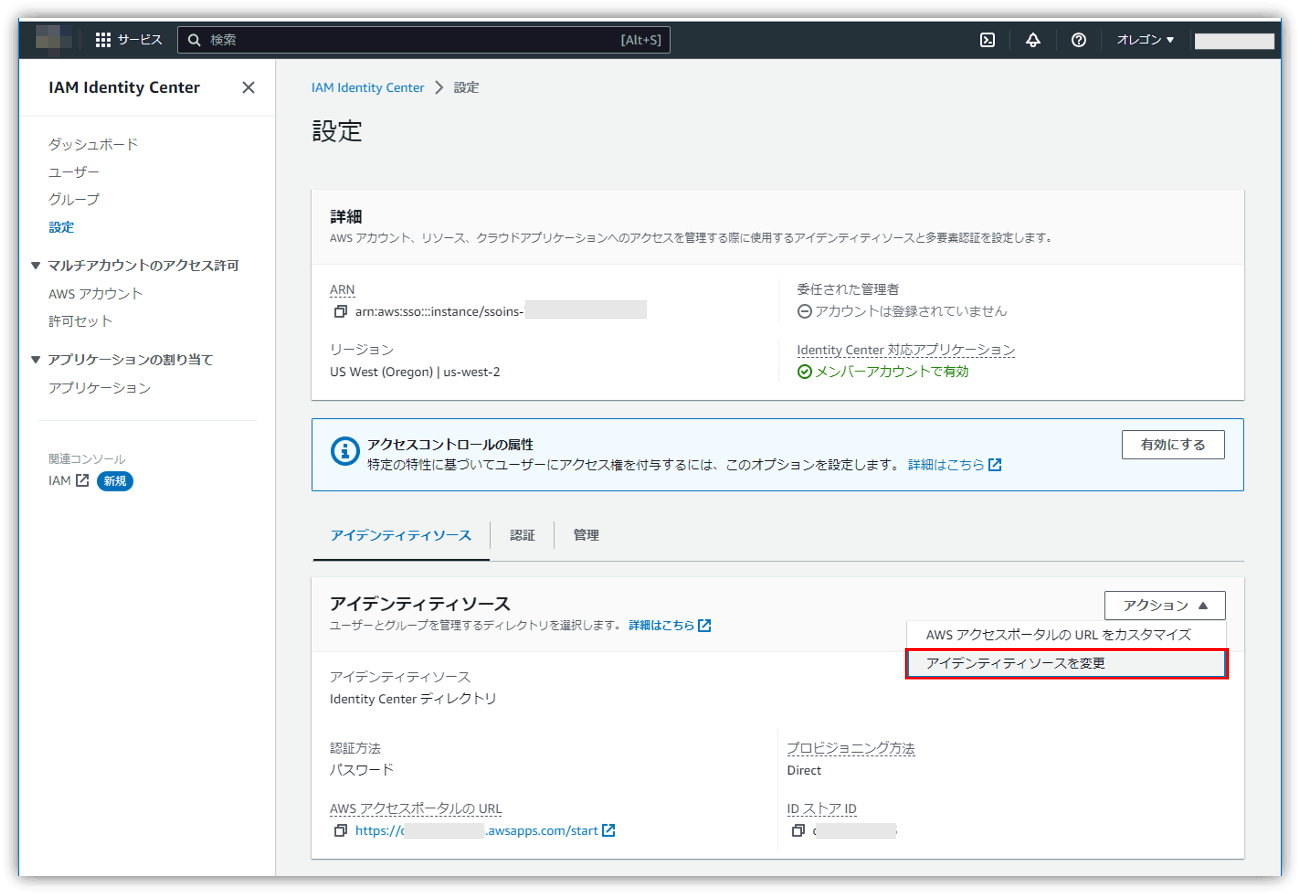
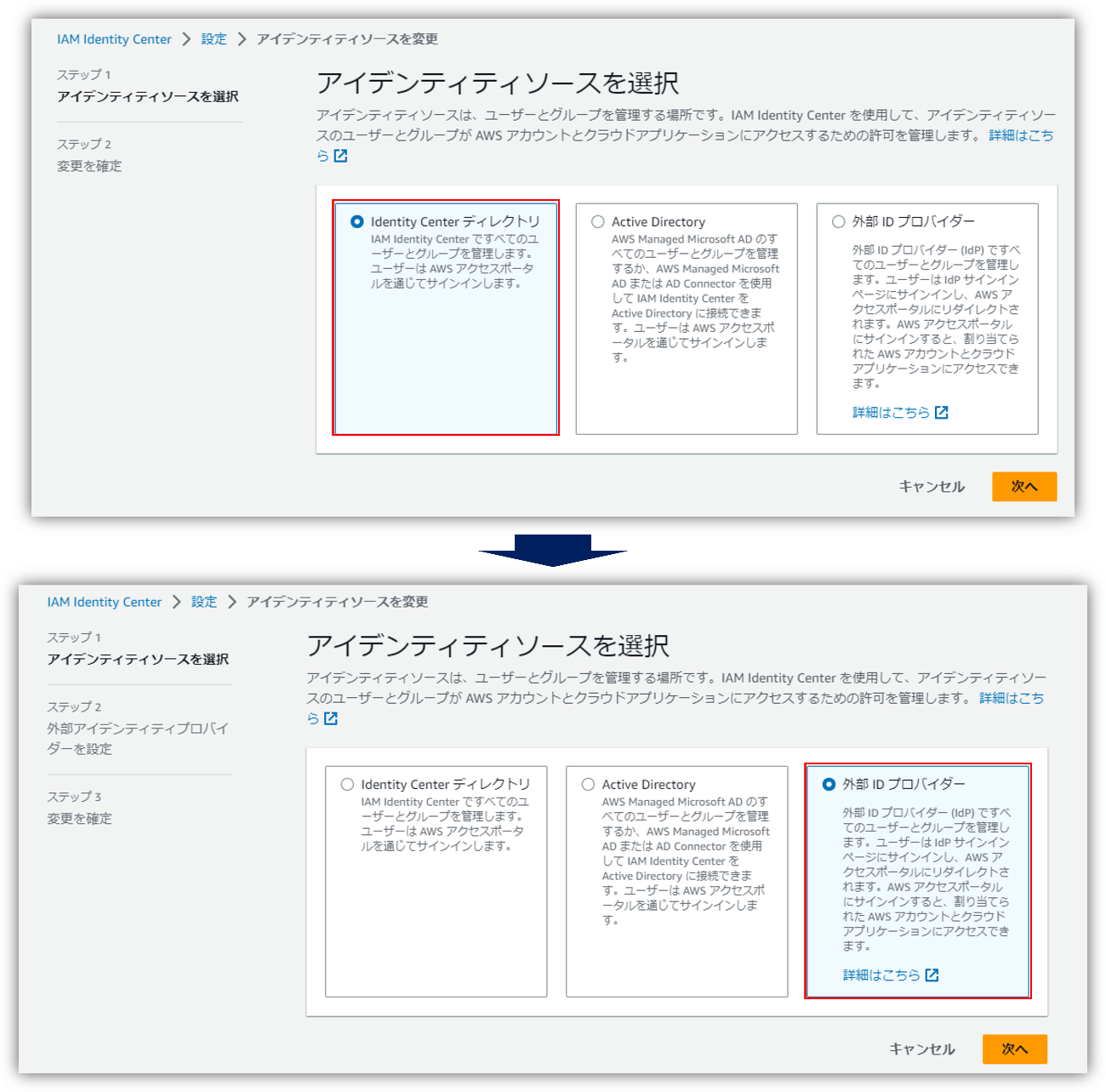
- Select “Identity Center Directory” > “External Identity Provider” as the identity source
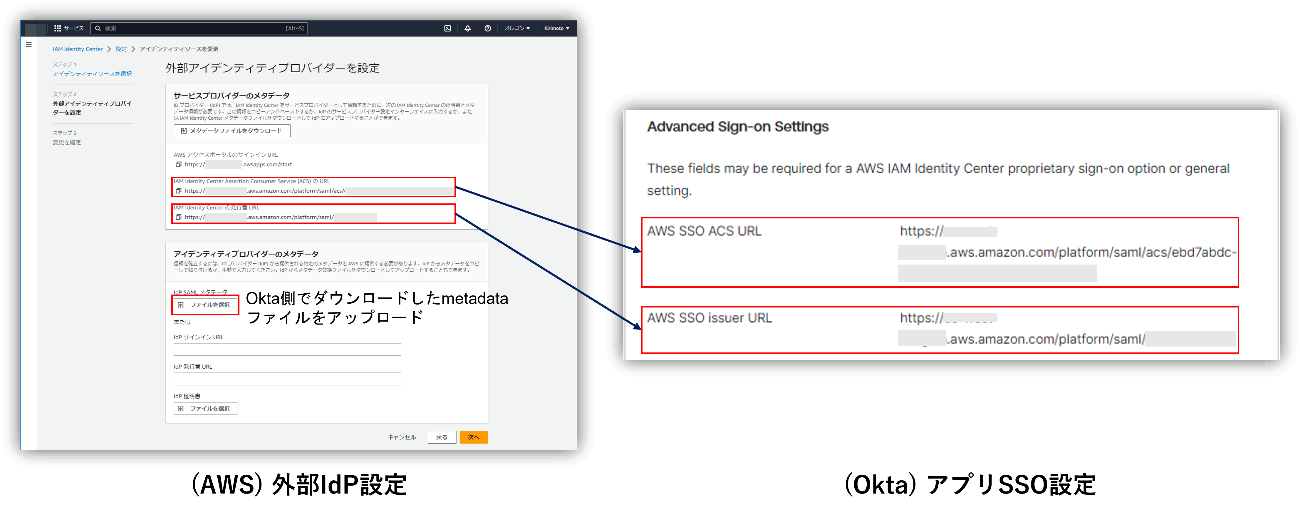
- After uploading the metadata file saved in step 2 using the external IdP settings, paste the ACS URL and Issuer URL into the Okta app settings.
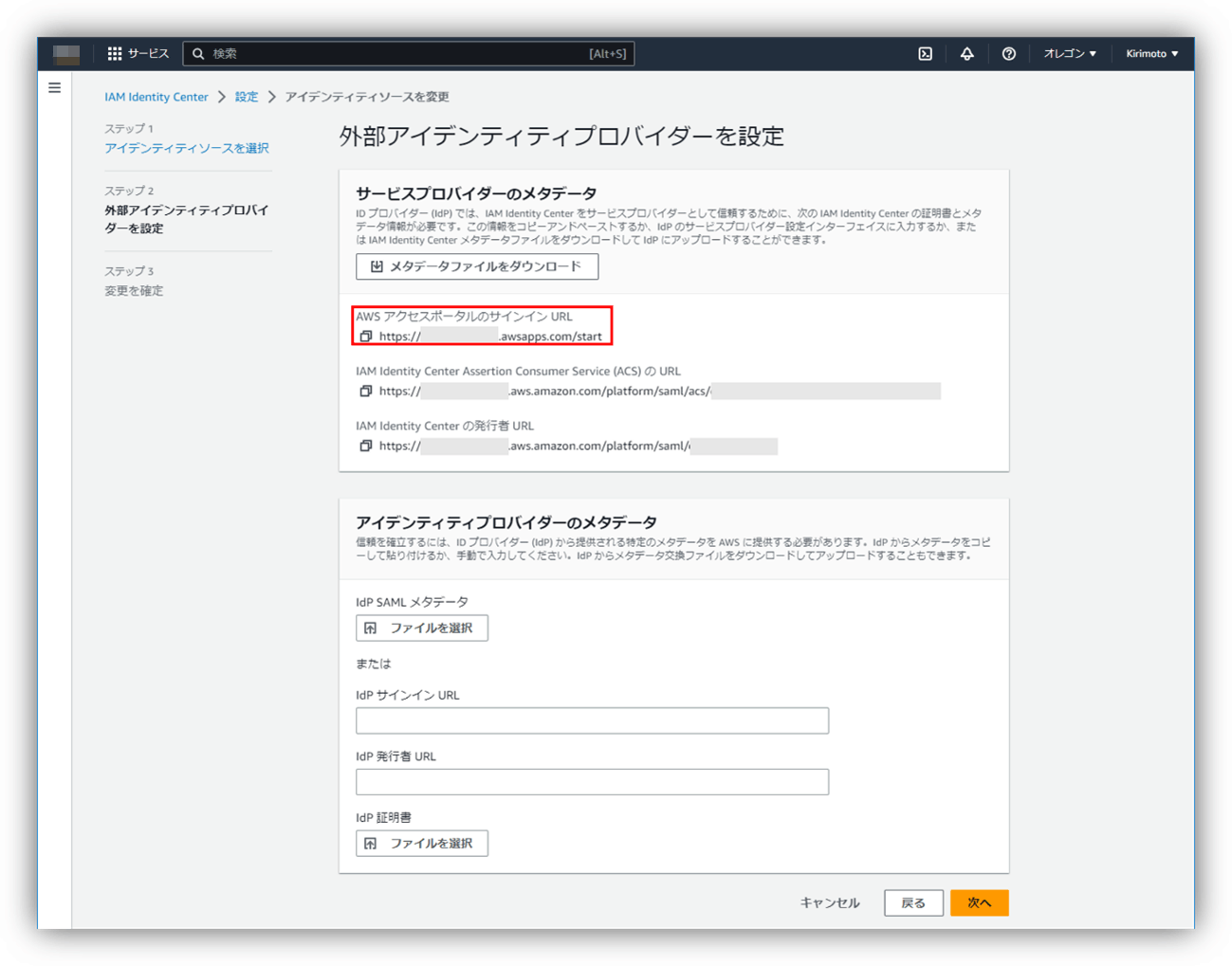
*When actually performing SSO, you will be redirected to Okta by accessing the "AWS access portal sign-in URL" displayed in step 3.
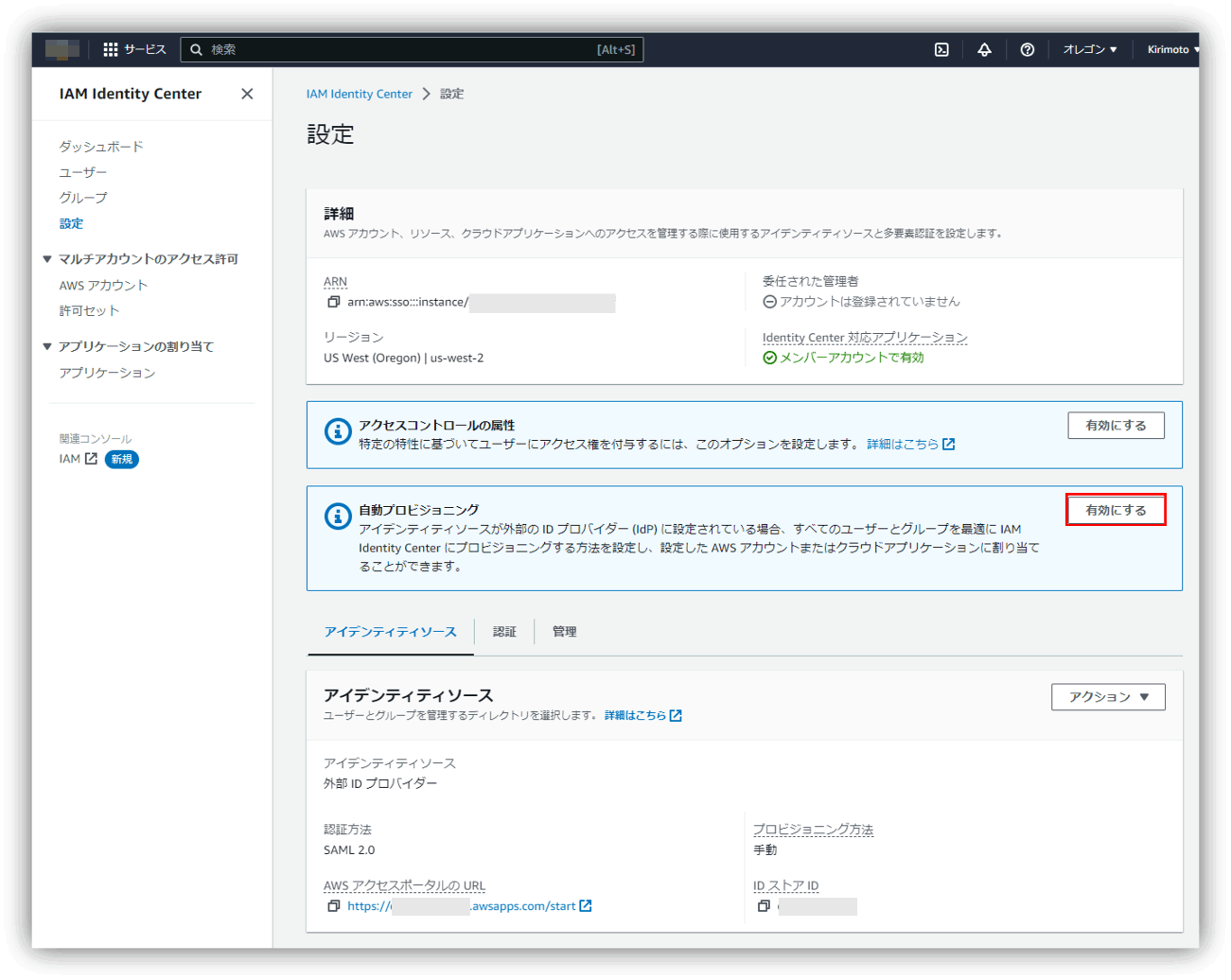
Okta-AWS IAM Identity Center provisioning integration
Okta provides a SaaS integration template called OIN, so specify and configure OIN for AWS IAM Identity Center integration.

Click View SAML setup instructions in the AWS IAM Identity Center app created on Okta and proceed with the settings according to the instructions.


- AWS IAM Identity Center Settings > Identity Source tab, click "Change Identity Source"

- Select “Identity Center Directory” > “External Identity Provider” as the identity source

- After uploading the metadata file saved in step 2 using the external IdP settings, paste the ACS URL and Issuer URL into the Okta app settings.

*When actually performing SSO, you will be redirected to Okta by accessing the "AWS access portal sign-in URL" displayed in step 3.

User group synchronization and authorization
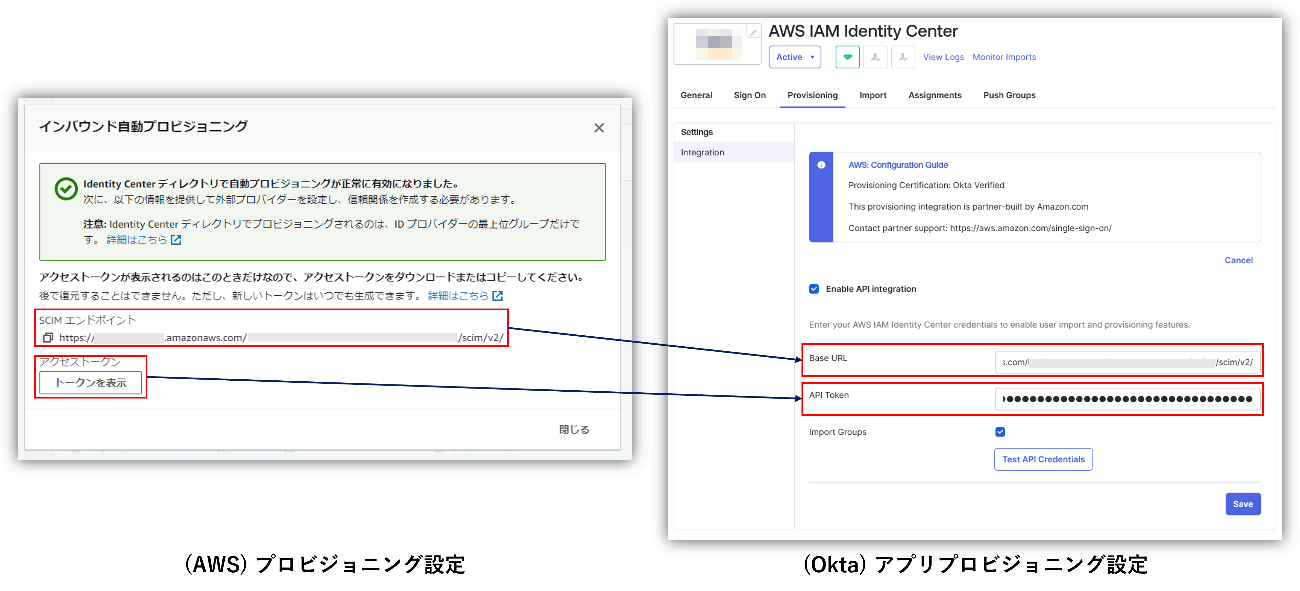
The provisioning linkage is now complete.
User group synchronization and authorization
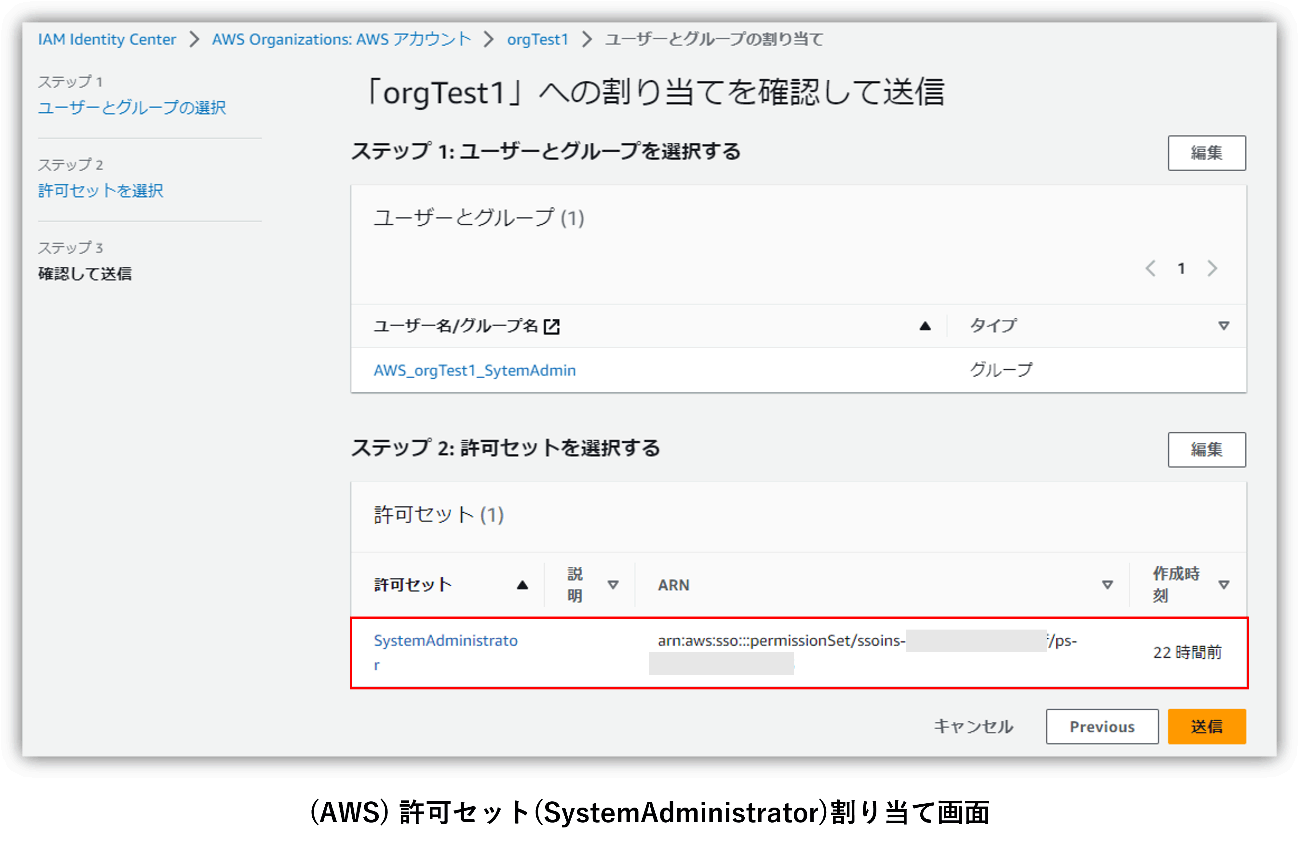
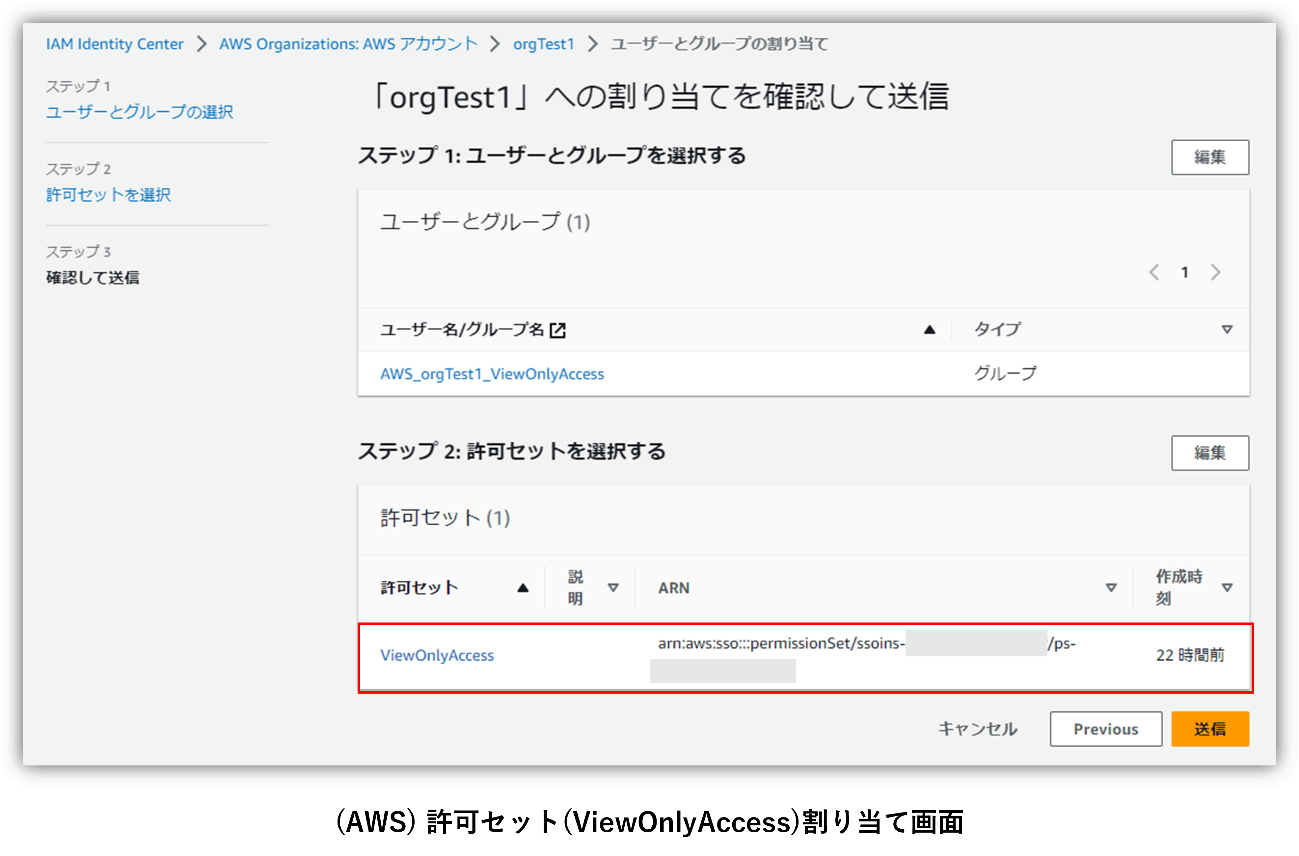
This time, we created a permission set in advance on the AWS IAM Identity Center side. By assigning this permission set to users performing SSO to AWS, the range of privileges available on AWS is specified. Here we have created the following permission set:
- SystemAdministrator: Specify "SystemAdministrator" from the predefined permission set
- ViewOnlyAccess: Specify "ViewOnlyAccess" from the predefined permission set
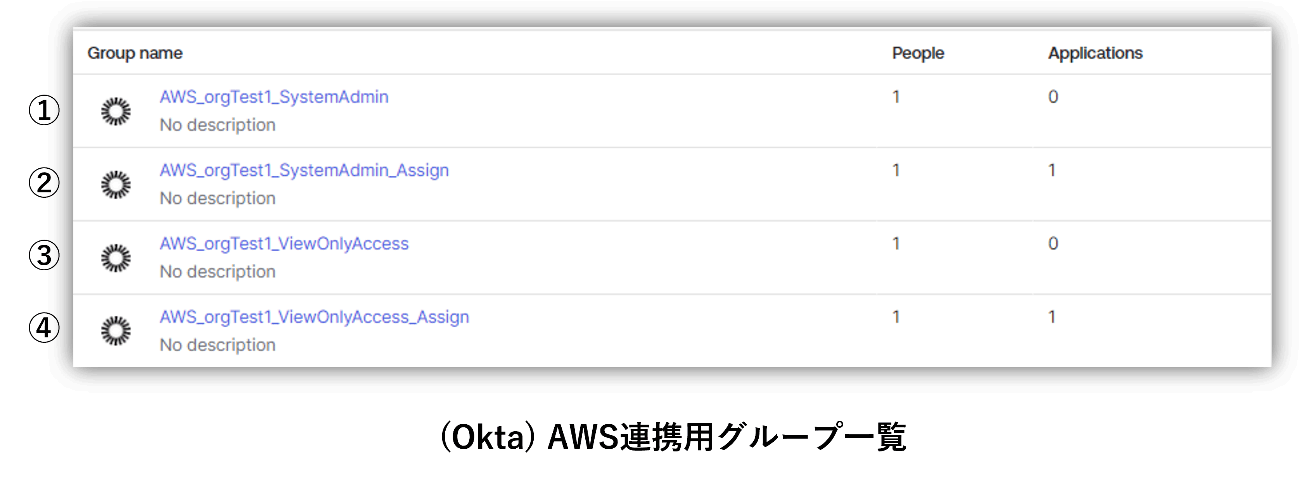
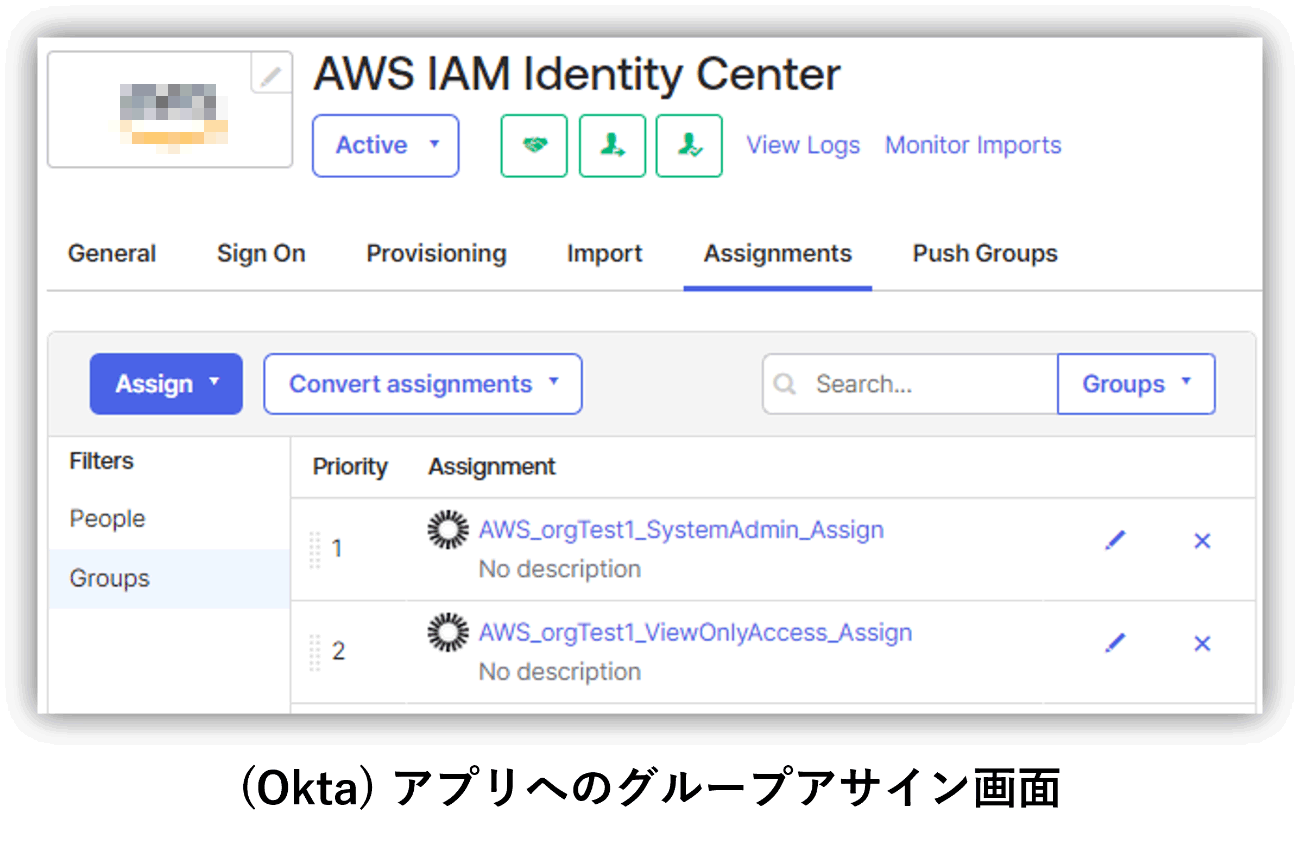
Additionally, on the Okta side, we created groups for each user to whom we would like to grant the above permission set.
In this user/group synchronization, the groups are divided as follows.
- AWS_orgTest1_SystemAdmin
SystemAdministrator user group push group - AWS_orgTest1_SystemAdmin_Assign
Group for user synchronization for SystemAdministrator users - AWS_orgTest1_ViewOnlyAccess
ViewOnlyAccess user's group push group - AWS_orgTest1_ViewOnlyAccess_Assign
Group for user synchronization for ViewOnlyAccess users
*Group push is a function that pushes groups and memberships from Okta to partner applications. You can link existing groups between Okta and the application, or create groups on the Okta side as new groups on the application side.
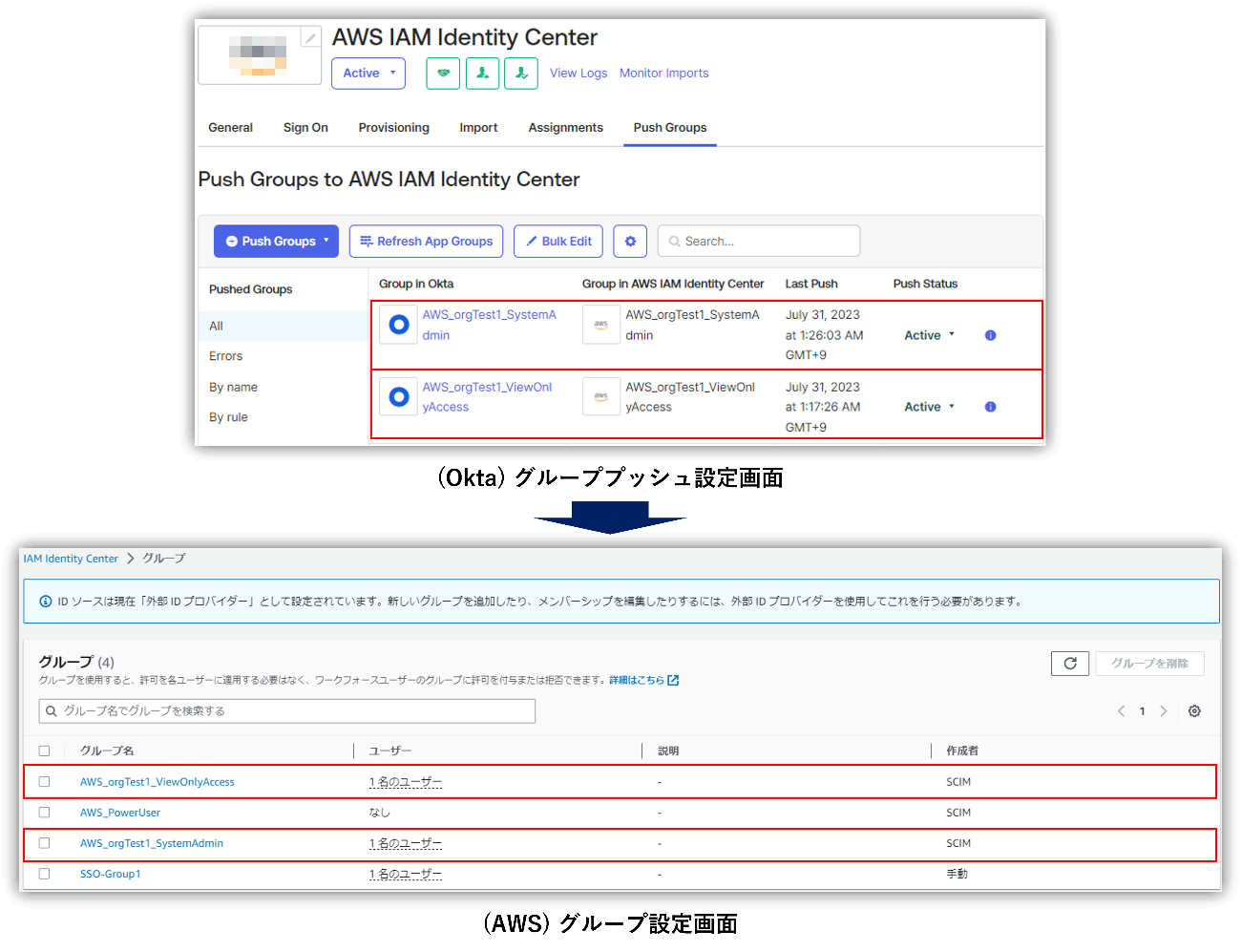
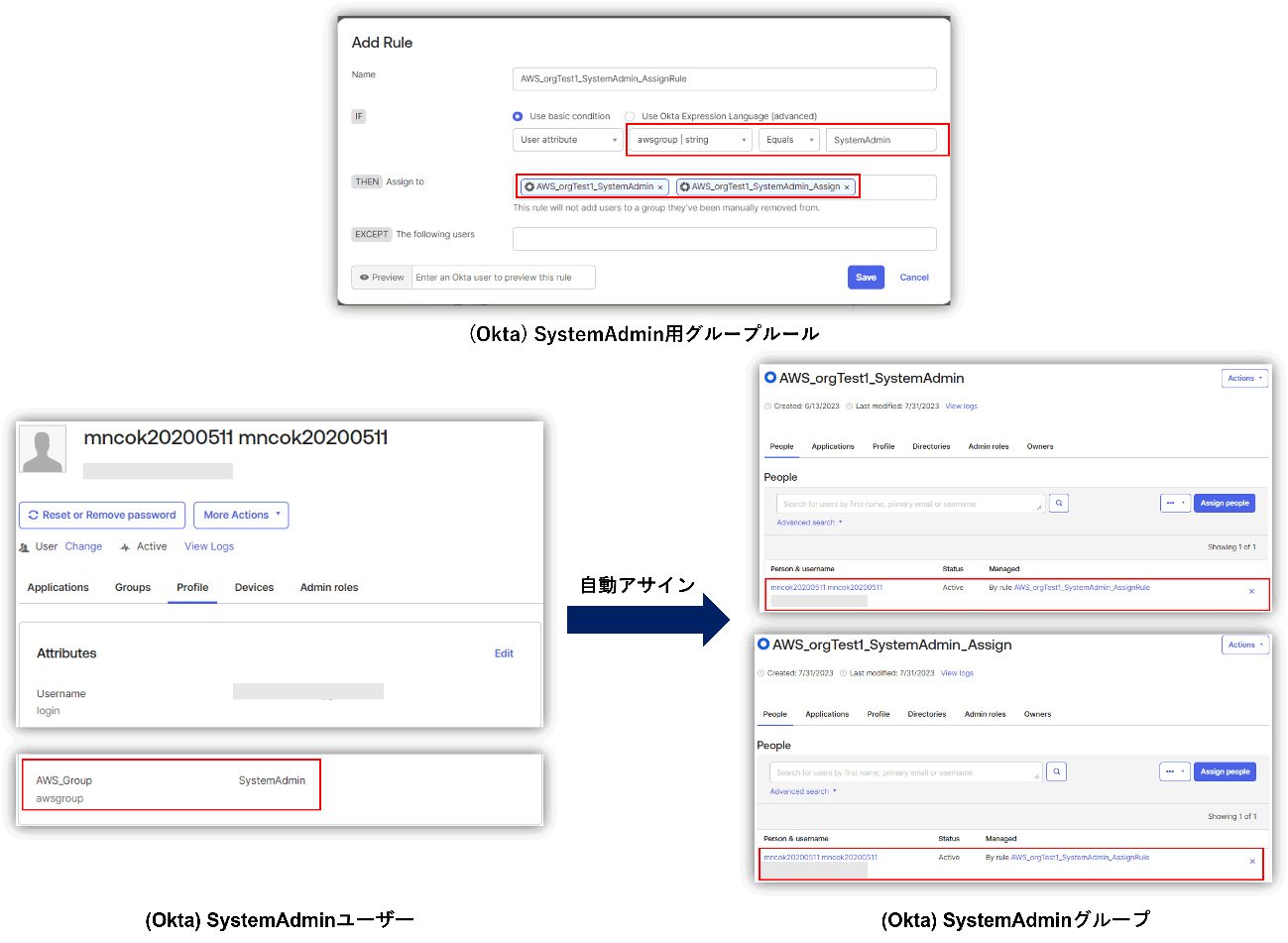
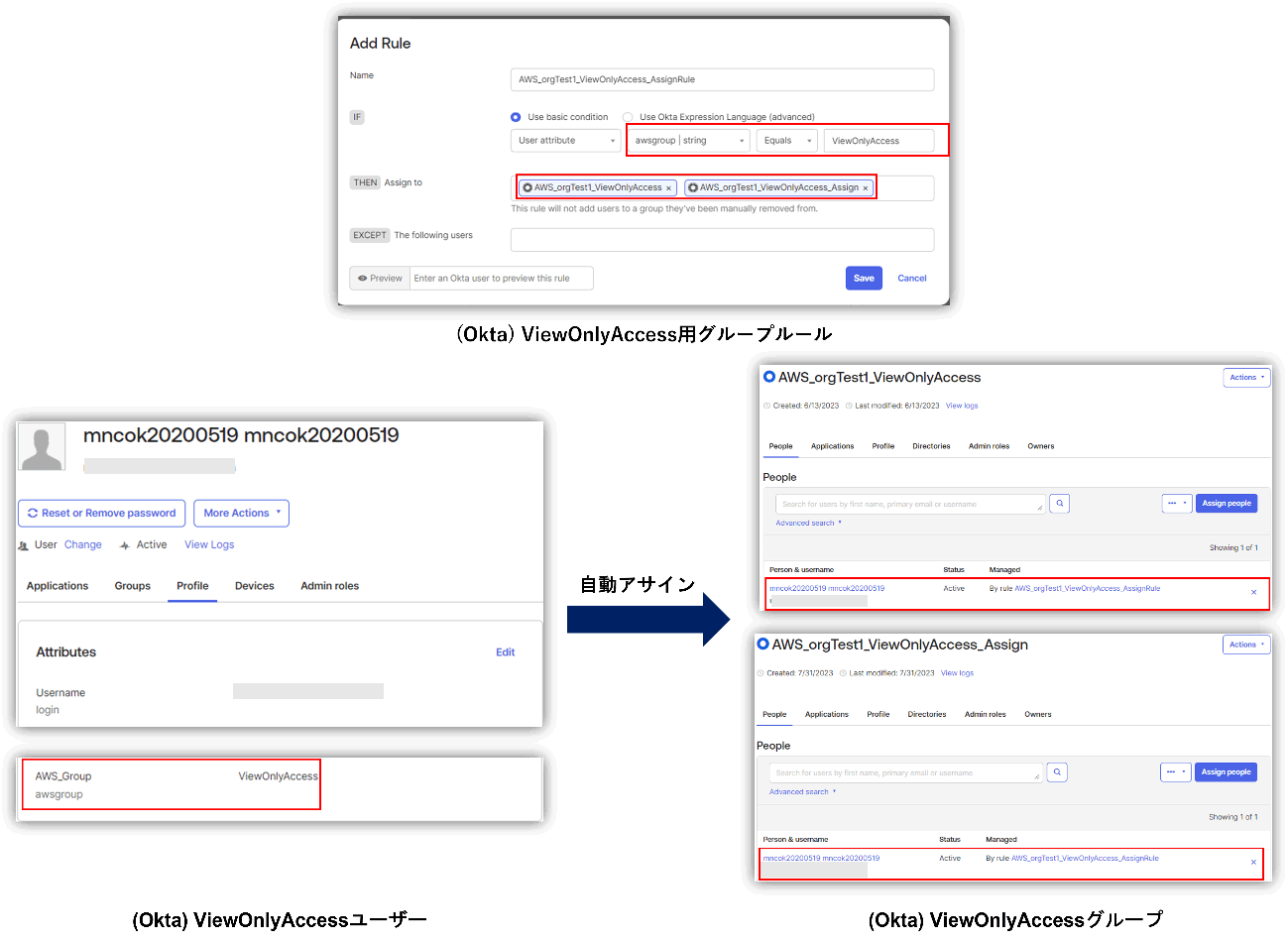
First, create "AWS_Group" as a custom attribute for the user, and specify the permission set (e.g. SystemAdministrator) that you want to assign in AWS IAM Identity Center as the attribute value. Then, create a group rule such as ``Assign users whose AWS_Group attribute value is "SystemAdministrator" to the AWS_SystemAdmin group.''
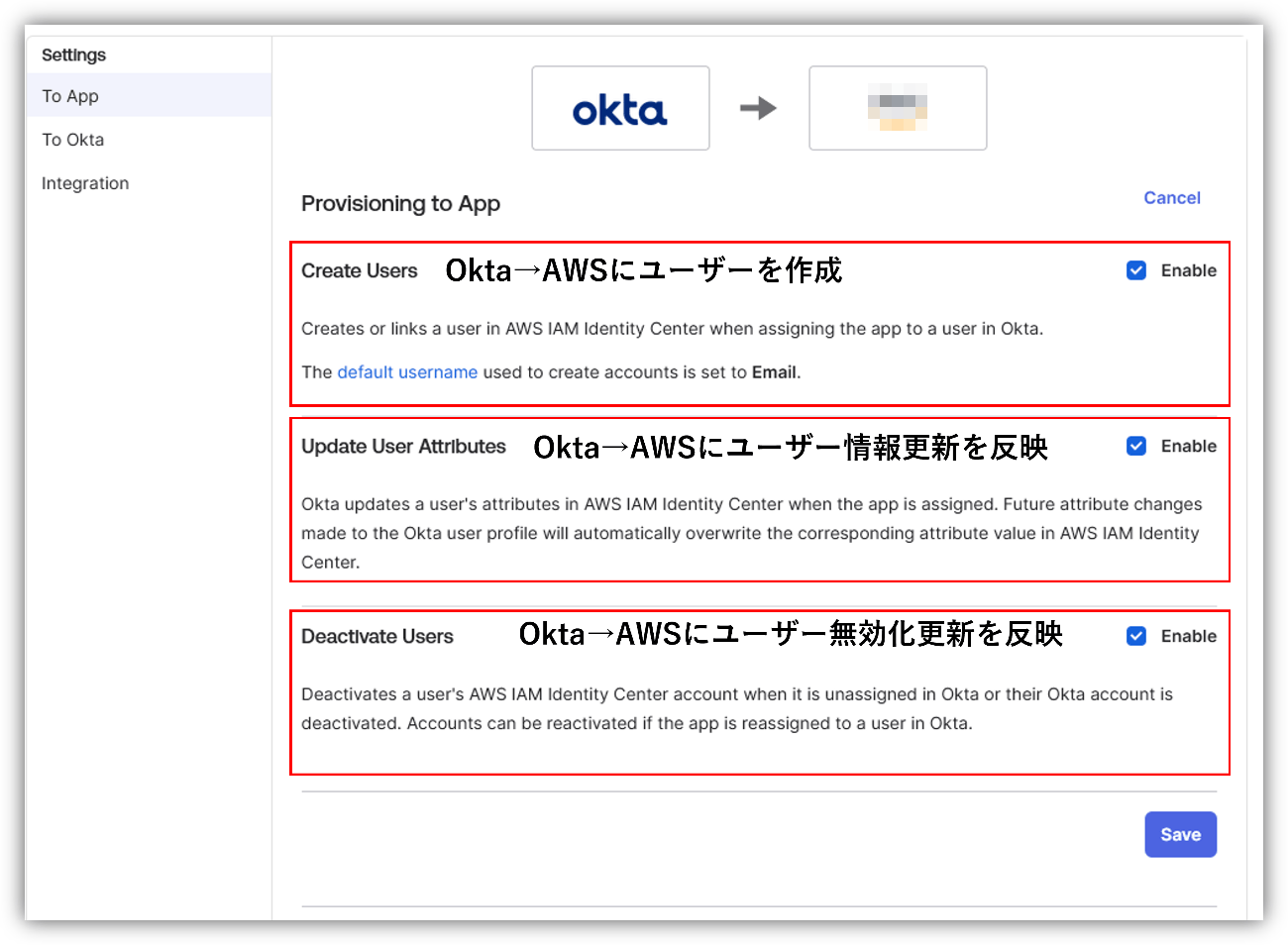
- Okta→Create user to AWS IAM Identity Center
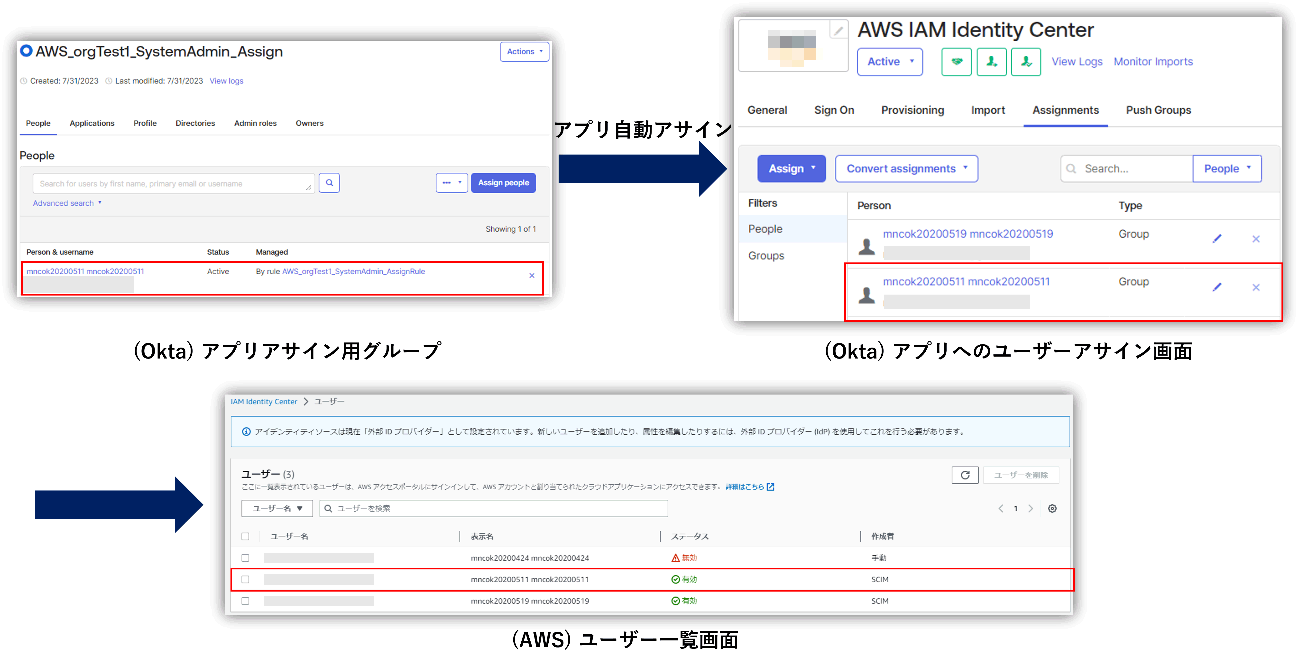
- Assign users to groups created in Okta→AWS IAM Identity Center
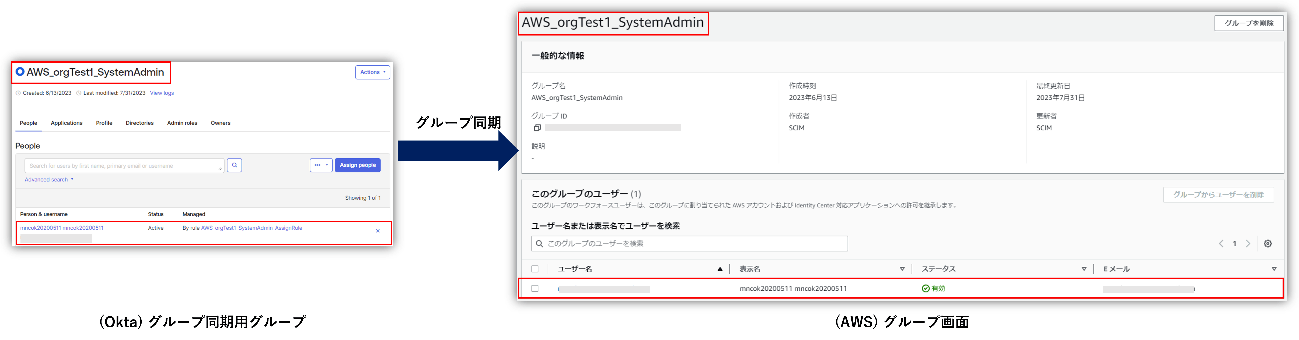
In the above flow, the user is assigned to the group to which the permission set was previously assigned on the AWS IAM Identity Center side, and the permission set is automatically assigned to the user. Therefore, it is possible to manage AWS user privileges by setting groups on the Okta side.
SSO to AWS
Actual SSO to AWS works as follows, allowing login with the assigned permission set.
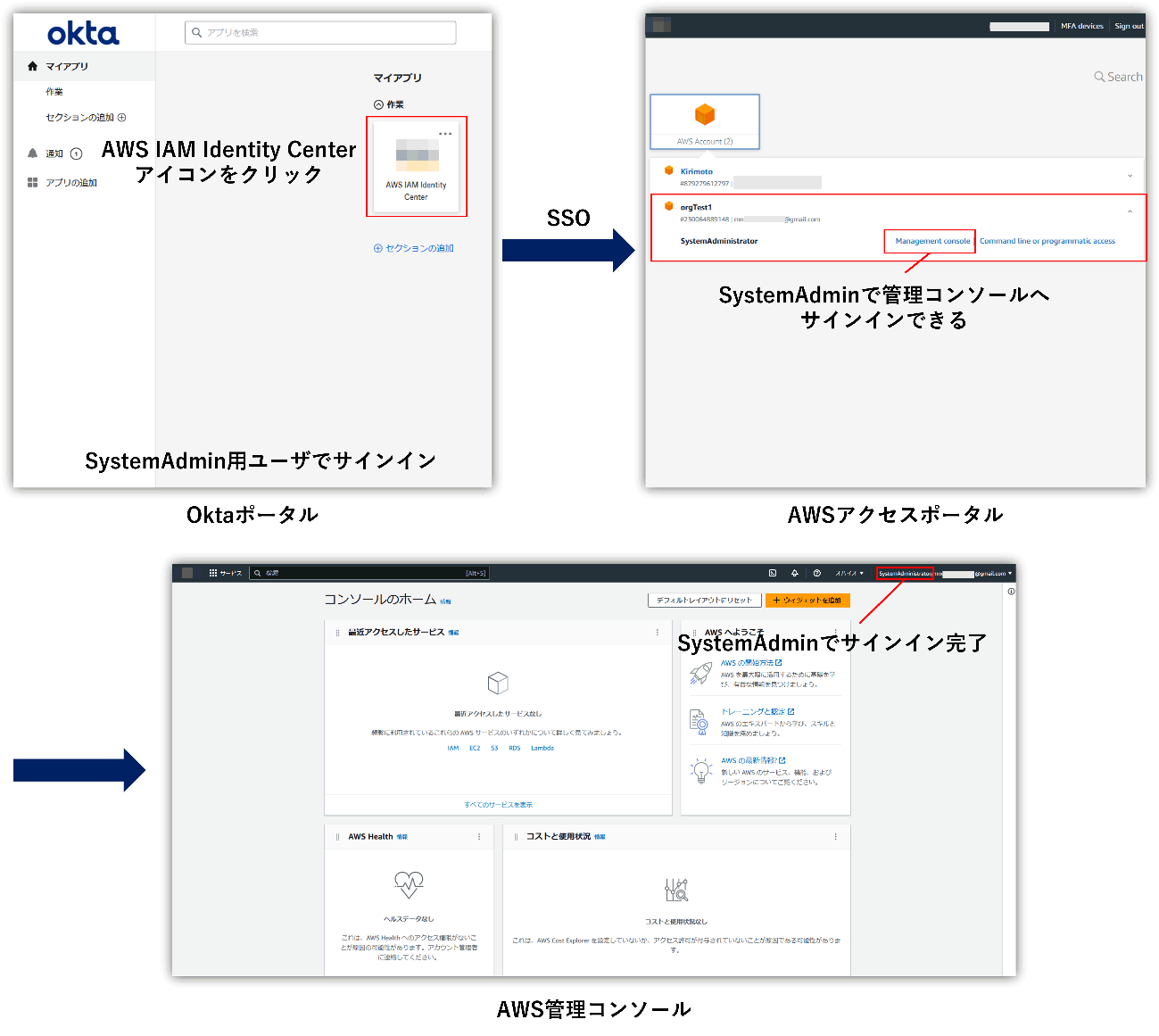
Summary
In this blog, we introduced SSO and provisioning collaboration with AWS IAM Identity Center using OIN (Okta Integration Network). What did you think?
Okta provides OIN that allows you to not only create/update/disable users, but also manage permissions depending on the SaaS, so you can greatly automate access management to SaaS.
If you are interested in integrating with AWS IAM Identity Center or other SaaS, or have any inquiries regarding Okta, please contact us.
Inquiry/Document request
In charge of Macnica Okta Co., Ltd.
- TEL:045-476-2010
- E-mail:okta@macnica.co.jp
Weekdays: 9:00-17:00

